GRE over IPSec-NAT-T
由于IPSec不支持对多播和广播数据包的加密,这样的话,使用IPSec的隧道中,动态路由协议等依靠多播和广播的协议就不能进行正常通告,所以,这时候要配合GRE隧道,GRE隧道会将多播和广播数据包封装到单播包中,再经过IPSec加密。
此外由于GRE建立的是简单的,不进行加密的×××隧道,他通过在物理链路中使用ip地址和路由穿越普通网络。所以很常见的方法就是使用IPSec对GRE进行加密,提供数据安全保证。
再运用到之前练习的IPsec穿越NAT知识,进行综合实验
拓扑图
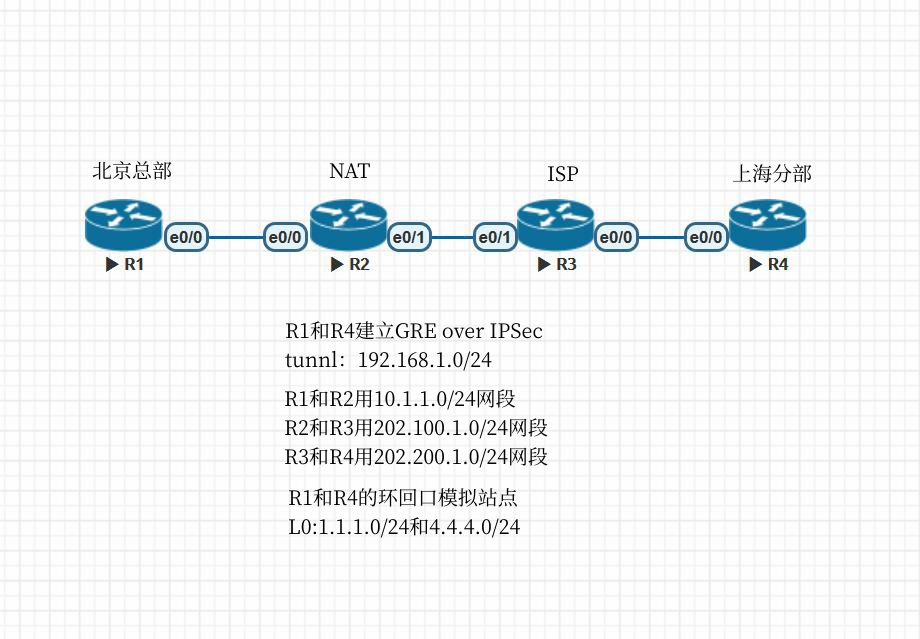
基本配置
R1
interface Loopback0
ip address 1.1.1.1 255.255.255.0
interface Ethernet0/0
ip address 10.1.1.1 255.255.255.0
ip route 0.0.0.0 0.0.0.0 10.1.1.254
R2
interface Ethernet0/0
ip address 10.1.1.254 255.255.255.0
interface Ethernet0/1
ip address 202.100.1.1 255.255.255.0
ip route 0.0.0.0 0.0.0.0 202.100.1.254
R3
interface Ethernet0/0
ip address 202.200.1.254 255.255.255.0
interface Ethernet0/1
ip address 202.100.1.254 255.255.255.0
R4
interface Loopback0
ip address 4.4.4.4 255.255.255.0
interface Ethernet0/0
ip address 202.200.1.1 255.255.255.0
ip route 0.0.0.0 0.0.0.0 202.200.1.254
NAT配置
interface Ethernet0/0
ip address 10.1.1.254 255.255.255.0
ip nat inside
ip virtual-reassembly in
interface Ethernet0/1
ip address 202.100.1.1 255.255.255.0
ip nat outside
ip virtual-reassembly in
access-list 1 permit any
ip nat inside source list 1 interface Ethernet0/1 overloa
配置ipsec
R1
crypto isakmp policy 10
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp key ipsec address 0.0.0.0
crypto ipsec transform-set ipsec esp-3des esp-md5-hmac
mode tunnel
crypto map ipsec 10 ipsec-isakmp
set peer 202.200.1.1
set transform-set ipsec
match address ipsec
ip access-list extended ipsec #此处配置的IPSec保护的感兴趣流量为GRE流量
permit gre any any
R4
crypto isakmp policy 10
encr 3des
hash md5
authentication pre-share
group 2
crypto isakmp key ipsec address 0.0.0.0
crypto ipsec transform-set ipsec esp-3des esp-md5-hmac
mode tunnel
crypto map ipsec 10 ipsec-isakmp
set peer 202.100.1.1
set transform-set ipsec
match address ipsec
ip access-list extended ipsec
permit gre any any
调用map
R1
interface Ethernet0/0
ip address 10.1.1.1 255.255.255.0
crypto map ipsec
R4
interface Ethernet0/0
ip address 202.200.1.1 255.255.255.0
crypto map ipsec
GRE和OSPF配置
R1
interface Tunnel0
ip address 192.168.1.1 255.255.255.0
tunnel source Ethernet0/0
tunnel destination 202.200.1.1
router ospf 100
router-id 1.1.1.1
network 1.1.1.0 0.0.0.255 area 0
network 192.168.1.0 0.0.0.255 area 0
R4
interface Tunnel0
ip address 192.168.1.4 255.255.255.0
tunnel source Ethernet0/0
tunnel destination 10.1.1.1 #这里要目标地址必须是R1的接口地址,GRE被IPSec包裹,如果地址也NAT地址,R1无法识别
router ospf 100
router-id 4.4.4.4
network 4.4.4.0 0.0.0.255 area 0
network 192.168.1.0 0.0.0.255 area 0
############此时应该已经建立ospf邻接
R1#show ip ospf neighbor
Neighbor ID Pri State Dead Time Address Interface
4.4.4.4 0 FULL/ - 00:00:30 192.168.1.4 Tunnel0
可以发现已经建立成功,是通过隧道学习的
R1#show ip route ospf
O 4.4.4.4 [110/1001] via 192.168.1.4, 00:27:00, Tunnel0
在R1上查看ipsec状态,发现端口是4500经过NAT转换
R1#show crypto session
Crypto session current status
Interface: Ethernet0/0
Session status: UP-ACTIVE
Peer: 202.200.1.1 port 4500
IKEv1 SA: local 10.1.1.1/4500 remote 202.200.1.1/4500 Active
IPSEC FLOW: permit 47 0.0.0.0/0.0.0.0 0.0.0.0/0.0.0.0
Active SAs: 2, origin: crypto map
R1#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id status
202.200.1.1 10.1.1.1 QM_IDLE 1004 ACTIVE
测试ping 4.4.4.4 完成实验
R1#ping 4.4.4.4 source l0 repeat 10
Type escape sequence to abort.
Sending 10, 100-byte ICMP Echos to 4.4.4.4, timeout is 2 seconds:
Packet sent with a source address of 1.1.1.1
!!!!!!!!!!
Success rate is 100 percent (10/10), round-trip min/avg/max = 6/6/7 ms
在R2上查看NAT转换
R2#show ip nat translations
Pro Inside global Inside local Outside local Outside global
gre 202.100.1.1:0 10.1.1.1:0 202.200.1.1:0 202.200.1.1:0
udp 202.100.1.1:4500 10.1.1.1:4500 202.200.1.1:4500 202.200.1.1:4500




 浙公网安备 33010602011771号
浙公网安备 33010602011771号