7.3系统部署radius与ldap服务器进行客户端认证登陆
一、yum安装更新
yum问题解决清单:证书过期:重新更新证书
wget https://vault.centos.org/6.10/updates/x86_64/Packages/ca-certificates-2020.2.41-65.1.el6_10.noarch.rpm --no-check-certificate
rpm -iU ca-certificates-2020.2.41-65.1.el6_10.noarch.rpm
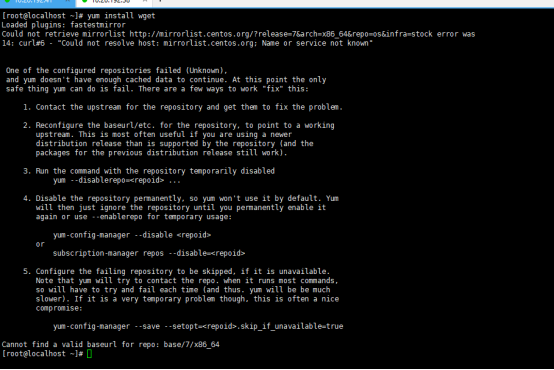
出现这个问题:
解决方法:
mv /etc/yum.repos.d/CentOS-Base.repo /etc/yum.repos.d/CentOS-Base.repo_BAK
wget -O /etc/yum.repos.d/CentOS-Base.repo http://mirrors.aliyun.com/repo/Centos-7.repo
或者
curl -o /etc/yum.repos.d/CentOS-Base.repo http://mirrors.aliyun.com/repo/Centos-7.repo
那么尝试将如下内容追加到 /etc/yum.repos.d/CentOS-Base.repo 中
[centos-sclo-rh]
name=CentOS-7 - SCLo rh
baseurl=http://vault.centos.org/centos/7/sclo/$basearch/rh/
gpgcheck=1
enabled=1
gpgkey=file:///etc/pki/rpm-gpg/RPM-GPG-KEY-CentOS-SIG-SCLo
[centos-sclo-sclo]
name=CentOS-7 - SCLo sclo
baseurl=http://vault.centos.org/centos/7/sclo/$basearch/sclo/
gpgcheck=1
enabled=1
gpgkey=file:///etc/pki/rpm-gpg/RPM-GPG-KEY-CentOS-SIG-SCLo
二、Centos7.3系统Redius服务器认证部署
一、安装radius服务器
yum -y update
yum -y install yum-utils
yum -y install repotrack freeradius
二、配置radius服务器
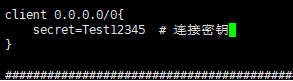
通过配置/etc/raddb/clients.conf ,增加如下字段可以允许任意IP以正确的密钥链接radius。
vi /etc/raddb/clients.conf --这里Test12345是客户端链接radius密钥
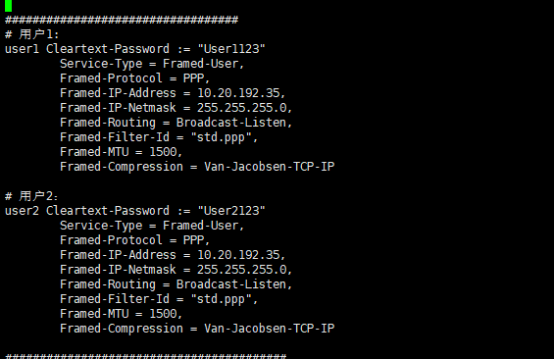
通过配置/etc/raddb/users可以增加、删除用户,以及配置当用户连接时,radius端回复信息。
第一行:设置用户名与秘密;Framed-IP-Address=10.20.192.35限制只有10.20.192.35用户ip连接。
vi /etc/raddb/users
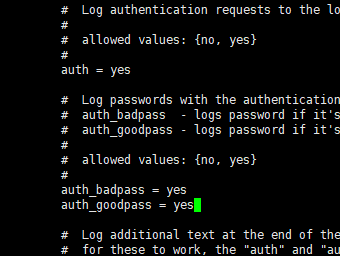
修改/etc/raddb/radiusd.conf文件启用radius日志功能
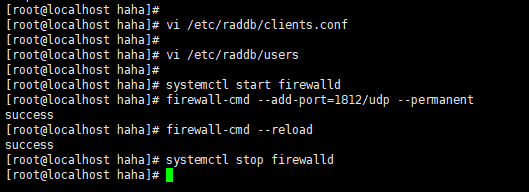
三、开放服务器端口启用radius服务器
systemctl start firewalld
firewall-cmd --add-port=1812/udp --permanent
firewall-cmd --add-port=1812/tcp --permanent
firewall-cmd --reload
systemctl stop firewalld
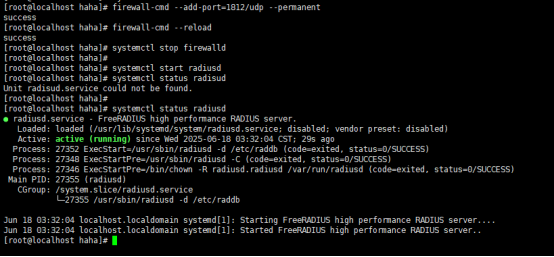
systemctl start radiusd
systemctl status radiusd
四、waf上面启用radius认证功能进行登陆验证
Waf上面配置:
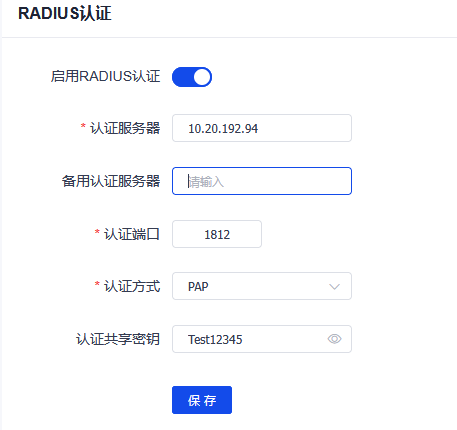
创建用户:user1 认证方式raidus认证
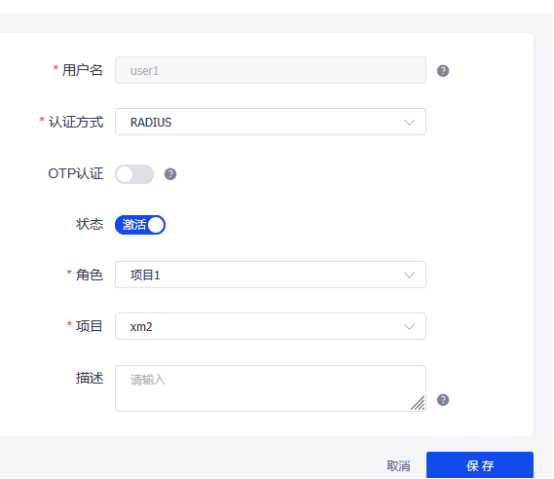
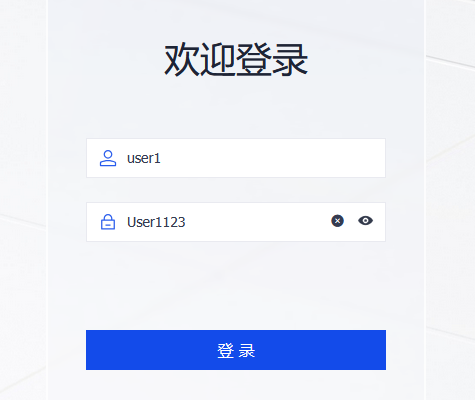
五、登陆
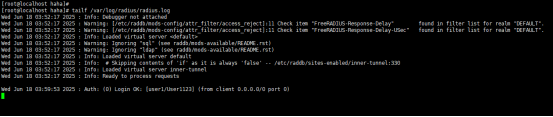
Radius服务器查看日志:
tailf /var/log/radius/radius.log
三、Cetnos 7.3系统部署ldap进行登陆 认证
一、安装ldap服务
yum install -y openldap-servers openldap-clients
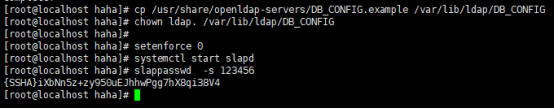
cp /usr/share/openldap-servers/DB_CONFIG.example /var/lib/ldap/DB_CONFIG
chown ldap. /var/lib/ldap/DB_CONFIG
setenforce 0
systemctl start slapd
二、配置ldap服务
[root@localhost haha]# slappasswd -s 123456
{SSHA}iXbNn5z+zy950uEJhhwPgg7hX8qi38V4
[root@localhost haha]#
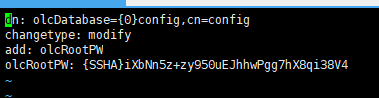
[root@dlp ~]# vi chrootpw.ldif
# specify the password generated above for "olcRootPW" section
dn: olcDatabase={0}config,cn=config
changetype: modify
add: olcRootPW
olcRootPW: {SSHA}iXbNn5z+zy950uEJhhwPgg7hX8qi38V4
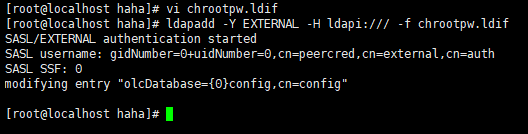
ldapadd -Y EXTERNAL -H ldapi:/// -f chrootpw.ldif
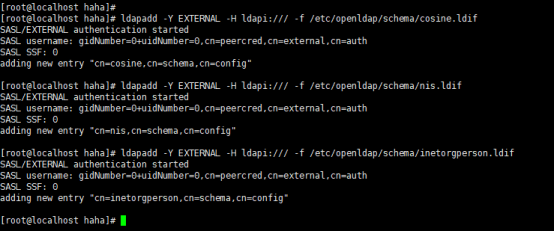
三、导入基本模式
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/cosine.ldif
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/nis.ldif
ldapadd -Y EXTERNAL -H ldapi:/// -f /etc/openldap/schema/inetorgperson.ldif
四、在ldap的DB中设置域名
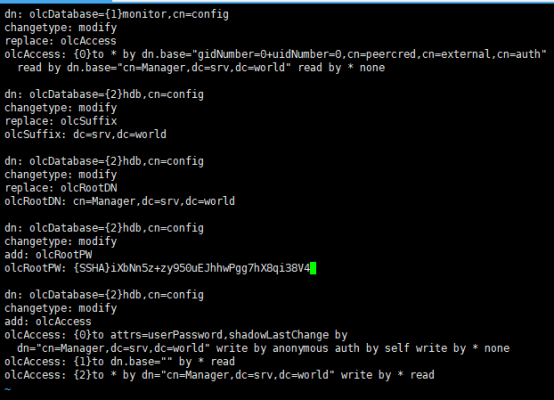
[root@dlp ~]# vi chdomain.ldif
dn: olcDatabase={1}monitor,cn=config
changetype: modify
replace: olcAccess
olcAccess: {0}to * by dn.base="gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth"
read by dn.base="cn=Manager,dc=srv,dc=world" read by * none
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcSuffix
olcSuffix: dc=srv,dc=world
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcRootDN
olcRootDN: cn=Manager,dc=srv,dc=world
dn: olcDatabase={2}hdb,cn=config
changetype: modify
add: olcRootPW
olcRootPW: {SSHA}iXbNn5z+zy950uEJhhwPgg7hX8qi38V4
dn: olcDatabase={2}hdb,cn=config
changetype: modify
add: olcAccess
olcAccess: {0}to attrs=userPassword,shadowLastChange by
dn="cn=Manager,dc=srv,dc=world" write by anonymous auth by self write by * none
olcAccess: {1}to dn.base="" by * read
olcAccess: {2}to * by dn="cn=Manager,dc=srv,dc=world" write by * read
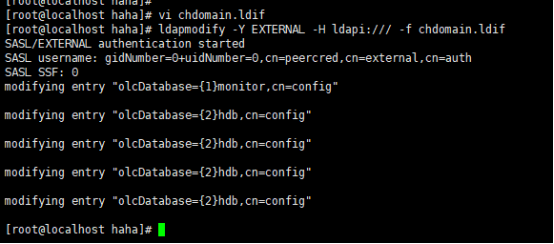
[root@dlp ~]# ldapmodify -Y EXTERNAL -H ldapi:/// -f chdomain.ldif
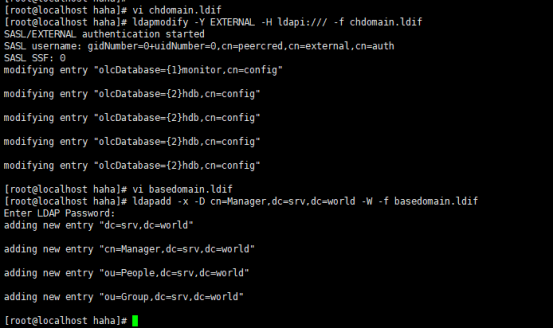
ldapadd -x -D cn=Manager,dc=srv,dc=world -w ‘123456’ -f basedomain.ldif
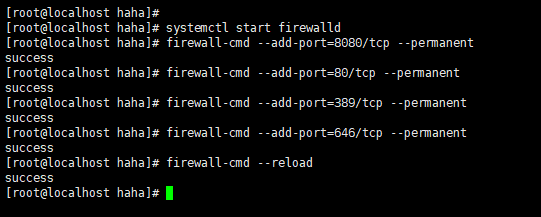
五、开放端口
[root@localhost haha]#
[root@localhost haha]# systemctl start firewalld
[root@localhost haha]# firewall-cmd --add-port=8080/tcp --permanent
success
[root@localhost haha]# firewall-cmd --add-port=80/tcp --permanent
success
[root@localhost haha]# firewall-cmd --add-port=389/tcp --permanent
success
[root@localhost haha]# firewall-cmd --add-port=646/tcp --permanent
success
[root@localhost haha]# firewall-cmd --reload
success
[root@localhost haha]# systemctl stop firewalld
[root@localhost haha]#
六、安装phpLDAPadmin来web配置LDAP
yum -y install httpd
rm -f /etc/httpd/conf.d/welcome.conf
vi /etc/httpd/conf/httpd.conf
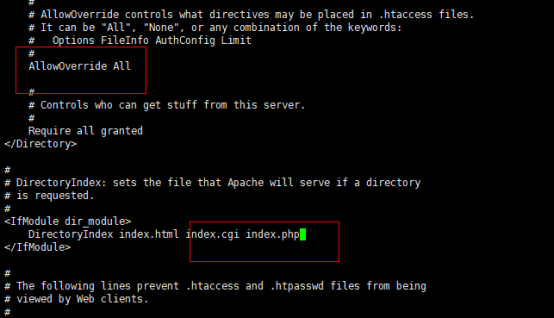
末尾添加:
ServerTokens Prod
KeepAlive On
systemctl start httpd
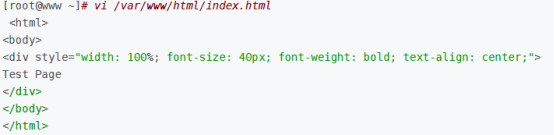
vi /var/www/html/index.html
七、安装php
yum -y install php php-mbstring php-pear
vi /etc/php.ini
date.timezone = "Asia/Shanghai"
systemctl restart httpd
八、安装phpLDAP admin
yum localinstall http://rpms.famillecollet.com/enterprise/remi-release-7.rpm
yum --enablerepo=epel -y install phpldapadmin
vi /etc/phpldapadmin/config.php
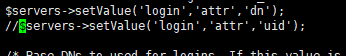
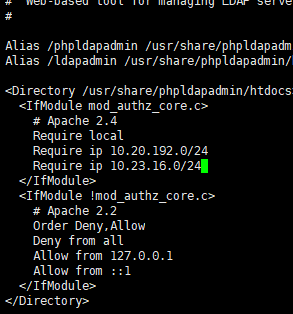
vi /etc/httpd/conf.d/phpldapadmin.conf
八、浏览器访问:http://10.20.192.94/ldapadmin/
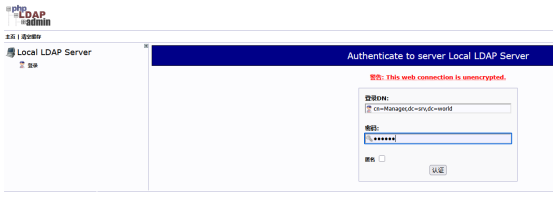
登陆:
用户名:cn=Manager,dc=srv,dc=world
密码: 123456
九、waf中启用ldap认证登陆
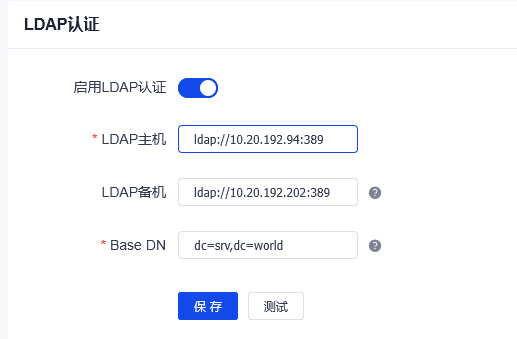
创建用户Manger---必须是ldap中的用户名
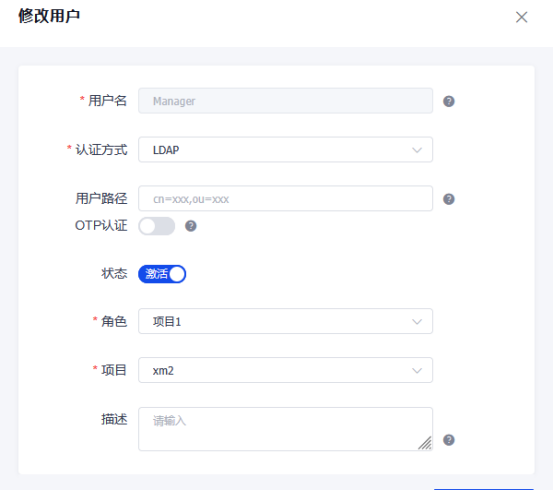
使用ldap中用户名与秘密登陆

登陆成功


 浙公网安备 33010602011771号
浙公网安备 33010602011771号