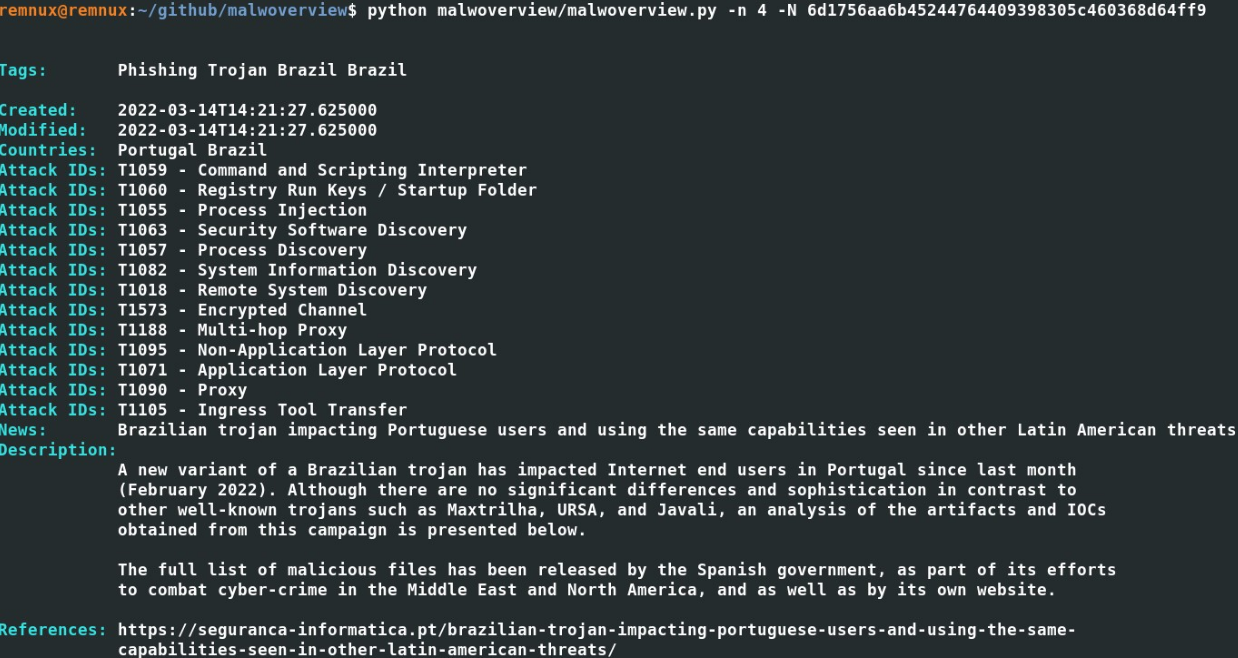
翻译1:
Malwoverview is a first response tool used for threat hunting and offers intel information from Virus Total, Hybrid Analysis, URLHaus, Polyswarm, Malshare, Alien Vault, Malpedia, Malware Bazaar, ThreatFox, Triage and it is able to scan Android devices against VT.
Malwoverview是用于威胁追踪的第一响应工具,提供来自Virus Total、Hybrid Analysis、URLHaus、Polyswarm、Malshare、Alien Vault、Malpedia、Malware Bazaar、ThreatFox、Triage的英特尔信息,并且能够针对VT扫描Android设备。
翻译2:
Copyright (C) 2018-2022 Alexandre Borges <alexandreborges at blackstormsecurity dot com>
This program is free software: you can redistribute it and/or modify
it under the terms of the GNU General Public License as published by
the Free Software Foundation, either version 3 of the License, or
(at your option) any later version.
This program is distributed in the hope that it will be useful,
but WITHOUT ANY WARRANTY; without even the implied warranty of
MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
GNU General Public License for more details.
See GNU Public License on <http://www.gnu.org/licenses/>.
版权所有(C) 2018-2022Alexandre Borges
这个程序是自由软件:你可以重新发布和/或修改它
它遵循由发布的GNU通用公共许可证的条款
自由软件基金会,许可证的第3版,或
(由您选择)任何更高版本。
分发这个程序是希望它有用,
但没有任何保证;甚至没有暗示的保证
适销性或对特定目的的适用性。参见
GNU通用公共许可证。
参见<http://www.gnu.org/licenses/上的GNU公共许可证>。
翻译3:
Current Version: 5.0.3
Important note: Malwoverview does NOT submit samples to any endpoint by default,
so it respects possible Non-Disclosure Agreements (NDAs). There're specific options
that explicitly submit samples, but these options are explained in the help.
重要说明:默认情况下,Malwoverview不会向任何端点提交样本,
所以它尊重可能的保密协议(NDA)。有具体的选择
显式提交示例,但是这些选项在帮助中有解释。
翻译4:
Malwoverview.py is a first response tool for threat hunting, which performs an initial and quick triage of malware samples, URLs, IP addresses, domains, malware families, IOCs and hashes. Additionally, Malwoverview is able to get dynamic and static behavior reports, submit and download samples from several endpoints.
This tool aims to :
Malwoverview.py是用于威胁搜寻的第一个响应工具,它对恶意软件样本、URL、IP地址、域、恶意软件家族、IOC和哈希进行初步和快速的分类。此外,Malwoverview能够获得动态和静态行为报告,从几个端点提交和下载样本。
该工具旨在:
翻译5:
This tool aims to :
Determine similar executable malware samples (PE/PE+) according to the import table (imphash) and group them by different colors (pay attention to the second column from output). Thus, colors matter!
Show hash information on Virus Total, Hybrid Analysis, Malshare, Polyswarm, URLhaus, Alien Vault, Malpedia and ThreatCrowd engines.
Determining whether the malware samples contain overlay and, if you want, extract it.
Check suspect files on Virus Total, Hybrid Analysis and Polyswarm.
Check URLs on Virus Total, Malshare, Polyswarm, URLhaus engines and Alien Vault.
Download malware samples from Hybrid Analysis, Malshare, URLHaus, Polyswarm and Malpedia engines.
Submit malware samples to VirusTotal, Hybrid Analysis and Polyswarm.
List last suspected URLs from URLHaus.
List last payloads from URLHaus.
Search for specific payloads on the Malshare.
Search for similar payloads (PE32/PE32+) on Polyswarm engine.
Classify all files in a directory searching information on Virus Total and Hybrid Analysis.
Make reports about a suspect domain using different engines such as VirusTotal, Malpedia and ThreatCrowd.
Check APK packages directly from Android devices against Hybrid Analysis and Virus Total.
Submit APK packages directly from Android devices to Hybrid Analysis and Virus Total.
Show URLs related to an user provided tag from URLHaus.
Show payloads related to a tag (signature) from URLHaus.
Show information about an IP address from Virus Total, Alien Vault, Malpedia and ThreatCrowd.
Show IP address, domain and URL information from Polyswarm.
Perform meta-search on Polyswarm Network using several criteria: imphash, IPv4, domain, URL and malware family.
Gather threat hunting information from AlienVault using different criteria.
Gather threat hunting information from Malpedia using different criteria.
Gather threat hunting information from Malware Bazaar using different criteria.
Gather IOC information from ThreatFox using different criteria.
Gather threat hunting information from Triage using different criteria.
Get evaluation to hashes from a given file against Virus Total.
Submit large files (>= 32 MB) to Virus Total.
Malwoverview uses Virus Total API v.3, so there isn't longer any option using v.2.
该工具旨在:
根据导入表(imphash)确定相似的可执行恶意软件样本(PE/PE+)并按不同颜色分组(注意从输出数第二列)。因此,颜色很重要!
显示病毒总数、混合分析、Malshare、Polyswarm、URLhaus、Alien Vault、Malpedia和ThreatCrowd引擎的哈希信息。
确定恶意软件样本是否包含覆盖,如果需要,提取它。
检查病毒总量、混合分析和Polyswarm的可疑文件。
检查病毒总数,Malshare,Polyswarm,URLhaus引擎和外国人保险库的网址。
从Hybrid Analysis、Malshare、URLHaus、Polyswarm和Malpedia引擎下载恶意软件样本。
向VirusTotal、Hybrid Analysis和Polyswarm提交恶意软件样本。
列出来自URLHaus的最后一个可疑URL。
列出来自URLHaus的最后有效负载。
在Malshare上搜索特定的有效负载。
在Polyswarm引擎上搜索类似的有效载荷(PE32/PE32+)。
对目录中的所有文件进行分类,搜索关于病毒总量和混合分析的信息。
使用不同的引擎(如VirusTotal、Malpedia和ThreatCrowd)报告可疑域。
检查APK软件包直接从Android设备对混合分析和病毒总数。
直接从Android设备向混合分析和病毒总量提交APK软件包。
显示与URLHaus中用户提供的标签相关的URL。
显示与来自URLHaus的标签(签名)相关的有效负载。
显示来自病毒总数、外星人金库、Malpedia和ThreatCrowd的IP地址信息。
显示来自Polyswarm的IP地址、域和URL信息。
在Polyswarm网络上使用多种标准执行元搜索:imphash、IPv4、域、URL和恶意软件家族。
使用不同的标准从AlienVault收集威胁搜寻信息。
使用不同的标准从Malpedia收集威胁搜寻信息。
使用不同的标准从恶意软件集市收集威胁搜寻信息。
使用不同的标准从ThreatFox收集国际奥委会信息。
使用不同的标准从分类中收集威胁搜寻信息。
根据病毒总数从给定文件中获取哈希评估。
向病毒总数提交大文件(> = 32 MB)。
Malwoverview使用Virus Total API v.3,因此不再有任何使用v.2的选项。
翻译6:
CONTRIBUTORS:
Alexandre Borges (project owner)
Corey Forman (https://github.com/digitalsleuth)
Christian Clauss (https://github.com/cclauss)
INSTALLATION
This tool has been tested on REMnux, Ubuntu, Kali Linux and macOS only. Malwoverview can be installed by executing the following command:
该工具仅在REMnux、Ubuntu、Kali Linux和macOS上进行了测试。Malwoverview可以通过执行以下命令来安装:
* pip3.9 install git+https://github.com/alexandreborges/malwoverview (preferred method)
or...
* python -m pip install -U malwoverview
or...
* git clone https://github.com/alexandreborges/malwoverview
如果您使用的是macOS,那么您应该在安装Malwoverview之前安装libmagic:
* brew install libmagic
* pip3.9 install -U malwoverview
翻译7:
To use Malwoverview you should insert VirusTotal, Hybrid Analysis, URLHaus, Malshare, Polyswarm, Alien Vault, Malpedia and Triage into the .malwapi.conf configuration file (the default one at the home directory (/home/[username] or /root) -- if the file doesn't exist, so you should create it) or you could create a custom configuration file and indicate it by using the -c option.
Nonetheless, starting on version 4.4.2, it isn't longer necessary to insert all APIs into .malwapi.conf before using Malwoverview. Therefore, users can only insert few APIs and use the respective options to these APIs.
要使用Malwoverview,您应该将VirusTotal、Hybrid Analysis、URLHaus、Malshare、Polyswarm、Alien Vault、Malpedia和Triage插入. malwapi.conf配置文件(主目录(/home/[username]或/root)中的默认文件,如果该文件不存在,您应该创建它),或者您可以创建一个自定义配置文件,并使用-c选项指定它。
尽管如此,从版本4.4.2开始,不再需要在使用Malwoverview之前将所有api插入. malwapi.conf。因此,用户只能插入几个API,并使用这些API各自的选项。
翻译8:
A special note about the Alien Vault: it is necessary to subscribe to pulses on Alien Vault website before using -n 1 option.
The .malwapi.conf configuration file (from the the home directory -- /home/[username] or /root) has the following format:
关于Alien Vault的特别说明:在使用-n 1选项之前,需要在外星人金库网站上订阅pulses。
. malwapi.conf配置文件(来自主目录-/home/[用户名]或/root)具有以下格式:
[VIRUSTOTAL]
VTAPI =
[HYBRID-ANALYSIS]
HAAPI =
[MALSHARE]
MALSHAREAPI =
[HAUSSUBMIT]
HAUSSUBMITAPI =
[POLYSWARM]
POLYAPI =
[ALIENVAULT]
ALIENAPI =
[MALPEDIA]
MALPEDIAAPI =
[TRIAGE]
TRIAGEAPI =
The APIs can be requested on the respective service websites:
可以在相应的服务网站上申请API:
Virus Total (community and paid API): https://www.virustotal.com/gui/join-us
Hybrid Analysis: https://www.hybrid-analysis.com/signup
Malshare: https://malshare.com/doc.php
URLHaus: https://urlhaus.abuse.ch/api/#account
Polyswarm: https://docs.polyswarm.io/consumers
Alien Vault: https://otx.alienvault.com/api
Malpedia: It doesn't offer open registration, but you can request an user account directly through Twitter (DM) or feedback e-email. The Malpedia Twitter handle is @malpedia.
Malware Bazaar: It isn't necessary an API.
ThreatFox: It isn't necessary an API.
Triage: https://tria.ge/signup.
翻译9:
A special note about API requests to the MALPEDIA:
The service and acceptance is based on the community vetting. Thus, it's recommended you send a request for an API from your business e-mail address and NOT public/free one (Gmail, Outlook and so on). Additionally, it'd be great whether you provided further information about you (LinkedIn account, Twitter and so on) because it would make simpler to proof your identity, professional profile and legitimacy, so making quicker the approval of your request.
服务和接受是基于社区审查。因此,建议您从您的业务电子邮件地址而不是公共/免费电子邮件地址(Gmail、Outlook等)发送API请求。此外,如果您能提供更多关于您的信息(LinkedIn帐户、Twitter等)就更好了,因为这样可以更容易地证明您的身份、职业资料和合法性,从而更快地批准您的请求。
翻译10:
Every Triage operation is based on the Triage ID of each artifact, so you need to use the "-x 1 -X <attribute>:<value>" to look for the correct ID of the artifact, so use this ID information with the remaining Triage options (-x [2-7]) for getting further threat hunting information from Triage endpoint.
Malwoverview has been written to produce outputs to dark background terminal. However, there's the -o option, which changes and adapts output's colors to light background.
每个类选操作都基于每个工件的类选ID,因此您需要使用“-x 1 -X <属性>:<值>”来查找工件的正确ID,因此使用这个ID信息和剩余的类选选项(-x [2-7])来从类选端点获取进一步的威胁搜索信息。
Malwoverview已被编写为向暗背景终端产生输出。但是,有一个-o选项,它可以改变输出的颜色,使其适应浅色背景。
翻译11:
On Linux systems, create the .malwapi.conf file within /home/[username] directory (Linux home user directory -- /home/[username] or /root).
Just in case you install it on Windows systems, you should create the .malwapi.conf file in the C:\Users\[username] directory (Windows home user directory).
To check the installation, execute:
在Linux系统上,在/home/[用户名]目录(Linux主用户目录-/home/[用户名]或/root)中创建. malwapi.conf文件。
为了防止在Windows系统上安装它,您应该在C:\Users\[username]目录(Windows home用户目录)中创建. malwapi.conf文件。
要检查安装,请执行:
malwoverview.py --help
翻译12:
Further information is available on:
(PYPI.org repository) https://pypi.org/project/malwoverview/
(Github) https://github.com/alexandreborges/malwoverview
如果要执行手动步骤(通常,这是不必要的),那么应该执行几个步骤:
翻译13:
Python version 3.8 or later (Only Python 3.x !!! It does NOT work using Python 2.7)
$ apt-get install python3.9 (for example)
Python-magic.
To install python-magic package you can execute the following command:
$ pip3.9 install python-magic
Or compiling it from the github repository:
$ git clone https://github.com/ahupp/python-magic
$ cd python-magic/
$ python3.9 setup.py build
$ python3.9 setup.py install
As there are serious problems about existing two versions of python-magic package, my recommendation is to install it from github (second procedure above) and copy the magic.py file to the SAME directory of malwoverview tool.
Install several Python packages:
$ pip3.9 install -r requirements.txt
OR
$ pip3.9 install -U pefile
$ pip3.9 install -U colorama
$ pip3.9 install -U simplejson
$ pip3.9 install -U python-magic
$ pip3.9 install -U requests
$ pip3.9 install -U validators
$ pip3.9 install -U geocoder
$ pip3.9 install -U polyswarm-api
$ pip3.9 install -U pathlib
$ pip3.9 install -U configparser
To check an Android mobile you need to install the "adb" program by executing the following command:
# apt get install adb
PS: before trying Android's options, check:
* If the adb program is listed in the PATH environment variable.
* If the system has authorized access to the device by using "adb devices -l"
Python 3.x版或更高版本(仅限Python 3.x!!!它在Python 2.7中不工作)
Python-magic。
要安装python-magic包,您可以执行以下命令:
或者从github库编译它:
由于现有的两个版本的python-magic package存在严重的问题,我的建议是从github安装它(上面的第二个过程),并将magic.py文件复制到malwoverview工具的同一个目录中。
安装几个Python包:
要检查Android手机,您需要通过执行以下命令来安装“adb”程序:
PS:在尝试Android的选项之前,请检查:
*如果adb程序列在PATH环境变量中。
*如果系统已授权使用“adb设备-l”访问设备
翻译14:
Malwoverview is a tool to perform a first triage of malware samples in a directory and group them
according to their import functions (imphash) using colors. This version:
* Shows the imphash information classified by color.
* Checks whether malware samples are packed.
* Checks whether malware samples have overlay.
* Shows the entropy of the malware samples.
Malwoverview是一个工具,用于对目录中的恶意软件样本进行第一次分类,并对它们进行分组
根据它们的导入函数(imphash)使用颜色。此版本:
*显示按颜色分类的imphash信息。
*检查恶意软件样本是否打包。
*检查恶意软件样本是否有覆盖。
*显示恶意软件样本的熵。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号