CTF基础——kail服务器nmap工具
一、nmap主机发现和端口扫描
1、nmap指定源端口eth0发送扫描
┌──(root㉿kali2024)-[~] └─# nmap 192.168.190.110 -e eth0 Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-10 19:56 HKT Nmap scan report for 192.168.190.110 Host is up (0.0018s latency). Not shown: 999 closed tcp ports (reset) PORT STATE SERVICE 22/tcp open ssh MAC Address: 00:0C:29:BF:AE:3B (VMware) Nmap done: 1 IP address (1 host up) scanned in 13.24 seconds
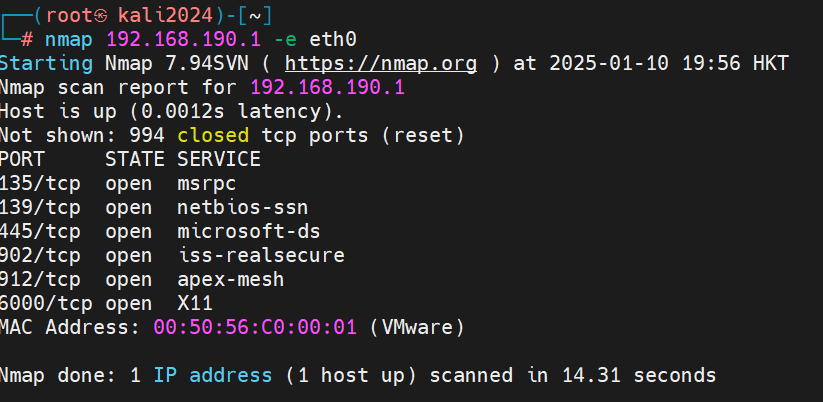
2、nmap指定ip文件
┌──(root㉿kali2024)-[~] └─# nmap -iL ip.txt Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-10 19:55 HKT Nmap scan report for 192.168.190.110 Host is up (0.0024s latency). Not shown: 999 closed tcp ports (reset) PORT STATE SERVICE 22/tcp open ssh MAC Address: 00:0C:29:BF:AE:3B (VMware) Nmap scan report for 192.168.190.1 Host is up (0.0022s latency). Not shown: 994 closed tcp ports (reset) PORT STATE SERVICE 135/tcp open msrpc 139/tcp open netbios-ssn 445/tcp open microsoft-ds 902/tcp open iss-realsecure 912/tcp open apex-mesh 6000/tcp open X11 MAC Address: 00:50:56:C0:00:01 (VMware) Nmap scan report for 192.168.190.129 Host is up (0.0000050s latency). Not shown: 999 closed tcp ports (reset) PORT STATE SERVICE 22/tcp open ssh Nmap done: 7 IP addresses (3 hosts up) scanned in 1.59 seconds

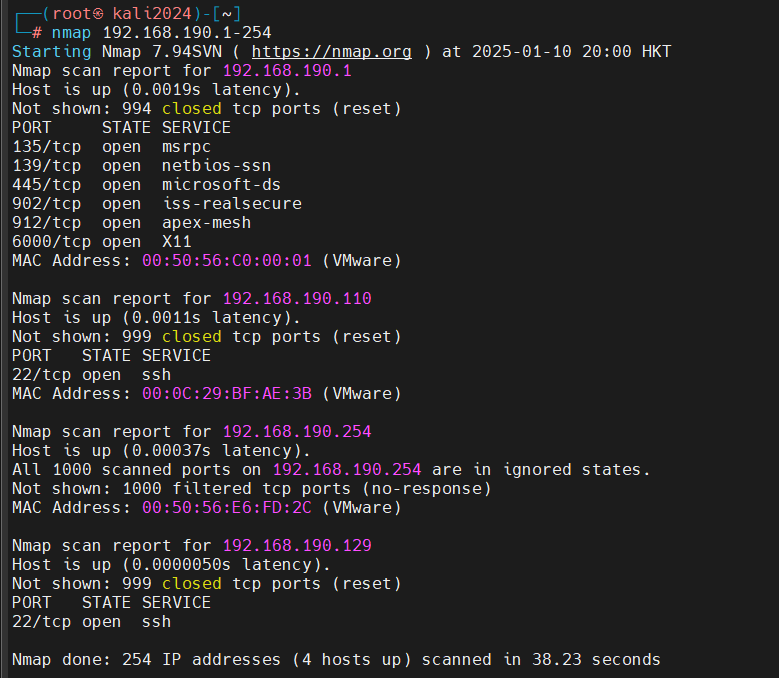
3、nmap指定ip段
┌──(root㉿kali2024)-[~] └─# nmap 192.168.190.1-254 Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-10 20:00 HKT Nmap scan report for 192.168.190.1 Host is up (0.0019s latency). Not shown: 994 closed tcp ports (reset) PORT STATE SERVICE 135/tcp open msrpc 139/tcp open netbios-ssn 445/tcp open microsoft-ds 902/tcp open iss-realsecure 912/tcp open apex-mesh 6000/tcp open X11 MAC Address: 00:50:56:C0:00:01 (VMware) Nmap scan report for 192.168.190.110 Host is up (0.0011s latency). Not shown: 999 closed tcp ports (reset) PORT STATE SERVICE 22/tcp open ssh MAC Address: 00:0C:29:BF:AE:3B (VMware) Nmap scan report for 192.168.190.254 Host is up (0.00037s latency). All 1000 scanned ports on 192.168.190.254 are in ignored states. Not shown: 1000 filtered tcp ports (no-response) MAC Address: 00:50:56:E6:FD:2C (VMware) Nmap scan report for 192.168.190.129 Host is up (0.0000050s latency). Not shown: 999 closed tcp ports (reset) PORT STATE SERVICE 22/tcp open ssh Nmap done: 254 IP addresses (4 hosts up) scanned in 38.23 seconds
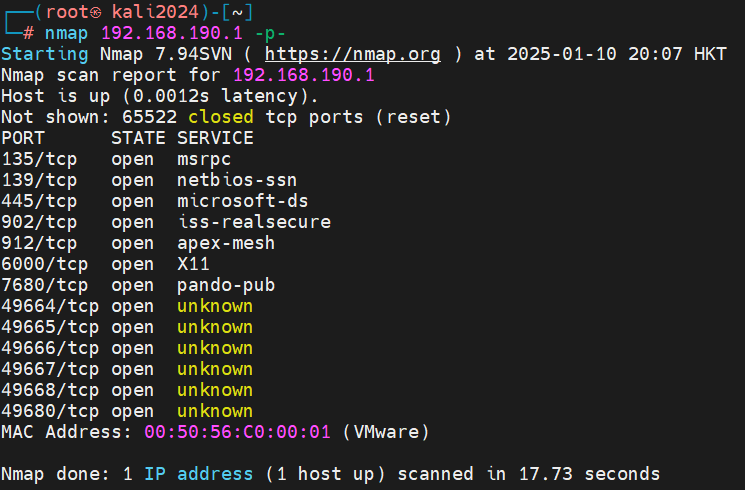
4、nmap扫描主机端口
┌──(root㉿kali2024)-[~] └─# nmap 192.168.190.1 -p- Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-10 20:07 HKT Nmap scan report for 192.168.190.1 Host is up (0.0012s latency). Not shown: 65522 closed tcp ports (reset) PORT STATE SERVICE 135/tcp open msrpc 139/tcp open netbios-ssn 445/tcp open microsoft-ds 902/tcp open iss-realsecure 912/tcp open apex-mesh 6000/tcp open X11 7680/tcp open pando-pub 49664/tcp open unknown 49665/tcp open unknown 49666/tcp open unknown 49667/tcp open unknown 49668/tcp open unknown 49680/tcp open unknown MAC Address: 00:50:56:C0:00:01 (VMware)
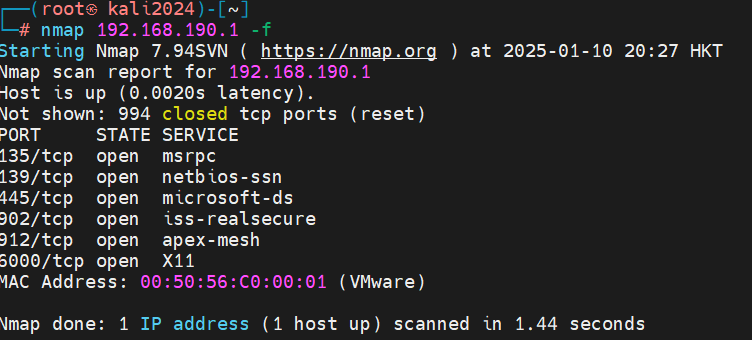
5、nmap扫描避免主机安全机制捕捉
┌──(root㉿kali2024)-[~] └─# nmap 192.168.190.1 -f Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-01-10 20:27 HKT Nmap scan report for 192.168.190.1 Host is up (0.0020s latency). Not shown: 994 closed tcp ports (reset) PORT STATE SERVICE 135/tcp open msrpc 139/tcp open netbios-ssn 445/tcp open microsoft-ds 902/tcp open iss-realsecure 912/tcp open apex-mesh 6000/tcp open X11 MAC Address: 00:50:56:C0:00:01 (VMware) Nmap done: 1 IP address (1 host up) scanned in 1.44 seconds
稳步前行,只争朝夕。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号