Portainer学习笔记2
使用portainer添加docker swarm集群,然后部署redis主从集群
docker swarm集群部署参考:https://blog.csdn.net/backtwo/article/details/143334089
需要提前在swarm 的manage节点上生成TLS证书,用来加密开启docker远程连接协议。
[root@park2-0006 uniapply]# mkdir /etc/docker/certs [root@park2-0006 uniapply]# cd /etc/docker/certs [root@park2-0006 certs]# vim gen-TLS.sh [root@park2-0006 certs]# chmod +x gen-TLS.sh [root@park2-0006 certs]# ./gen-TLS.sh 当前目录:/etc/docker/certs/ 证书文件将保存在此文件夹下 请输入证书使用的 IP 地址或者 HOST: 192.168.0.100 您输入的是:192.168.0.100 证书只能在这个 IP 或者 HOST 下使用,证书密码和输入的一致 Generating RSA private key, 4096 bit long modulus ...................................................................++ ................++ e is 65537 (0x10001) Generating RSA private key, 4096 bit long modulus ......................++ ..................................++ e is 65537 (0x10001) Signature ok subject=/CN=10.9.102.61 Getting CA Private Key Generating RSA private key, 4096 bit long modulus .......................................................................................................................................++ .................................................................................++ e is 65537 (0x10001) Signature ok subject=/CN=client Getting CA Private Key 证书生成完成 客户端使用文件:key.pem ca.pem cert.pem Docker 端使用文件:ca.pem server-cert.pem server-key.pem Docker 推荐配置内容:-H tcp://0.0.0.0:2375 --tlsverify --tlscacert=/etc/docker/certs/ca.pem --tlscert=/etc/docker/certs/server-cert.pem --tlskey=/etc/docker/certs/server-key.pem
脚本内容如下:
#!/bin/bash # # ------------------------------------------------------------- # 自动创建 Docker TLS 证书 # wget https://gitee.com/dromara/Jpom/raw/master/script/docker-tls.sh # curl -fsSL https://get.docker.com | bash -s docker --mirror Aliyun # systemctl daemon-reload && systemctl restart docker # ------------------------------------------------------------- # 以下是配置信息 # --[BEGIN]------------------------------ NOW_PATH=$( cd "$(dirname "$0")" || exit pwd )"/" echo "当前目录:${NOW_PATH} 证书文件将保存在此文件夹下" read -p "请输入证书使用的 IP 地址或者 HOST: " HOST # echo "您输入的是:${HOST} 证书只能在这个 IP 或者 HOST 下使用,证书密码和输入的一致" # --[INIT PARAMETER]------------------------------ PASSWORD="$HOST" COUNTRY="CN" STATE="$HOST" CITY="$HOST" ORGANIZATION="$HOST" ORGANIZATIONAL_UNIT="Dev" COMMON_NAME="$HOST" EMAIL="$HOST@docker-tls.com" # --[END]-- # Generate CA key openssl genrsa -aes256 -passout "pass:$PASSWORD" -out "ca-key.pem" 4096 # Generate CA openssl req -new -x509 -days 365 -key "ca-key.pem" -sha256 -out "ca.pem" -passin "pass:$PASSWORD" -subj "/C=$COUNTRY/ST=$STATE/L=$CITY/O=$ORGANIZATION/OU=$ORGANIZATIONAL_UNIT/CN=$COMMON_NAME/emailAddress=$EMAIL" # Generate Server key openssl genrsa -out "server-key.pem" 4096 # Generate Server Certs. openssl req -subj "/CN=$COMMON_NAME" -sha256 -new -key "server-key.pem" -out server.csr rm -f extfile.cnf echo "subjectAltName = DNS.1:$HOST,IP.1:127.0.0.1,IP.2:$HOST" >>extfile.cnf echo "extendedKeyUsage = serverAuth" >>extfile.cnf openssl x509 -req -days 365 -sha256 -in server.csr -passin "pass:$PASSWORD" -CA "ca.pem" -CAkey "ca-key.pem" -CAcreateserial -out "server-cert.pem" -extfile extfile.cnf # Generate Client Certs. rm -f extfile.cnf openssl genrsa -out "key.pem" 4096 openssl req -subj '/CN=client' -new -key "key.pem" -out client.csr echo "extendedKeyUsage = clientAuth" >>extfile.cnf openssl x509 -req -days 365 -sha256 -in client.csr -passin "pass:$PASSWORD" -CA "ca.pem" -CAkey "ca-key.pem" -CAcreateserial -out "cert.pem" -extfile extfile.cnf rm -f client.csr server.csr ca.srl extfile.cnf # check if [ -f "${NOW_PATH}key.pem" -a -f "${NOW_PATH}ca.pem" -a -f "${NOW_PATH}ca-key.pem" -a -f "${NOW_PATH}server-cert.pem" -a -f "${NOW_PATH}server-key.pem" ]; then echo "证书生成完成" echo "客户端使用文件:key.pem ca.pem cert.pem" echo "Docker 端使用文件:ca.pem server-cert.pem server-key.pem" echo "Docker 推荐配置内容:-H tcp://0.0.0.0:2375 --tlsverify --tlscacert=${NOW_PATH}ca.pem --tlscert=${NOW_PATH}server-cert.pem --tlskey=${NOW_PATH}server-key.pem" else echo "证书生成不完成,请检查配置和根据错误日志排查" fi
执行此脚本会提升让输入IP,此IP为你开启远程docker权限的IP,被管理的远程docker的IP
脚本执行结果如下
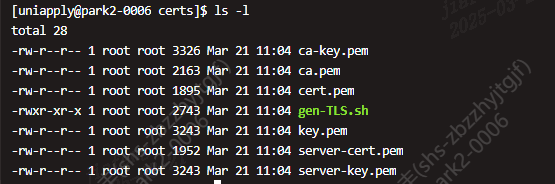
修改swarm manage节点的docker daemon配置,重启开启远程服务
# vim /usr/lib/systemd/system/docker.service ... [Service] Type=notify # the default is not to use systemd for cgroups because the delegate issues still # exists and systemd currently does not support the cgroup feature set required # for containers run by docker ExecStart=/usr/bin/dockerd -H fd:// --containerd=/run/containerd/containerd.sock -H tcp://0.0.0.0:2375 --tlsverify --tlscacert=/etc/docker/certs/ca.pem --tlscert=/etc/docker/certs/server-cert.pem --tlskey=/etc/docker/certs/server-key.pem ... # 推出保存,重启dokcer systemctl daemon-reload systemctl restart docker
回到Portainer页面添加环境
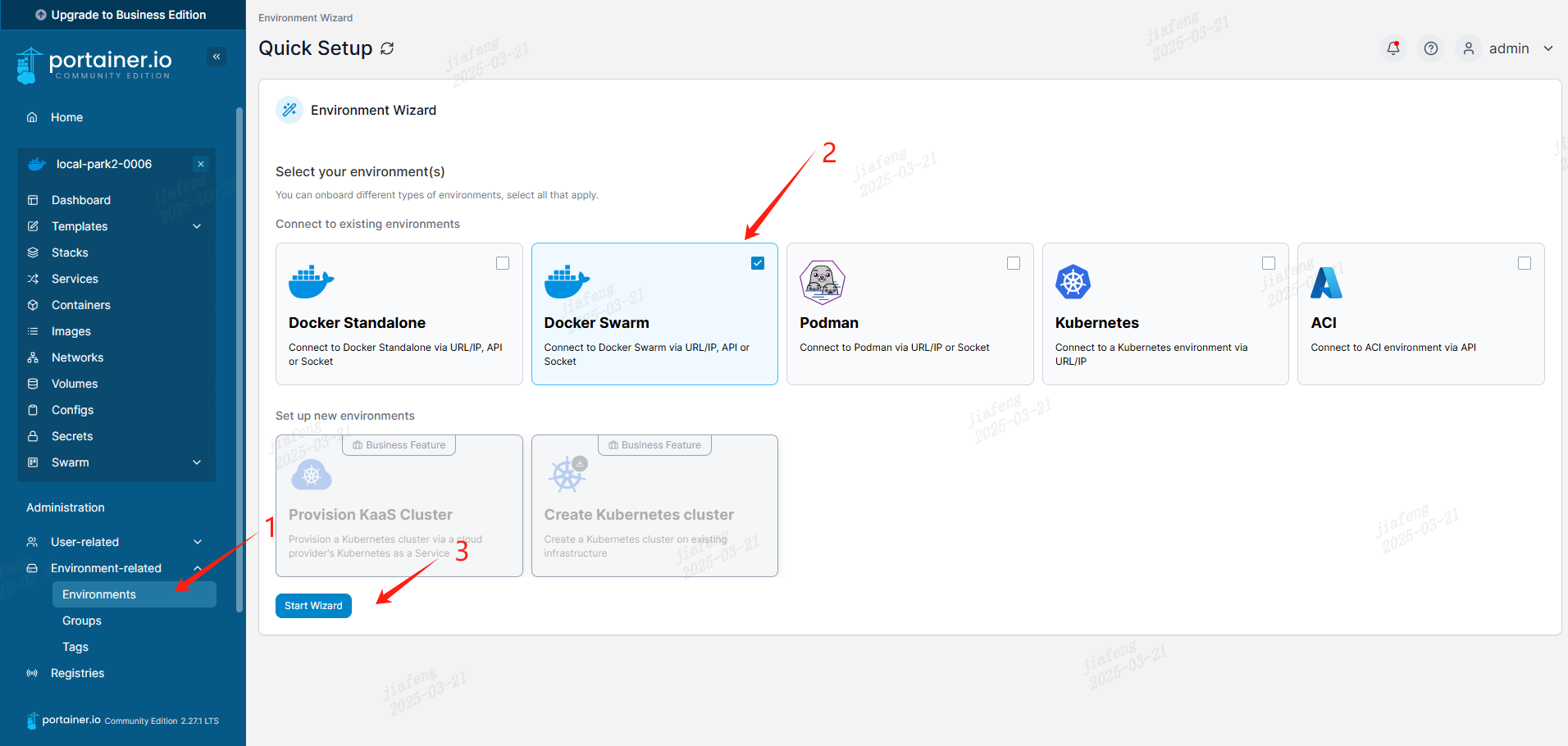
选择API的方式,输入swarm manage节点的ip和证书信息

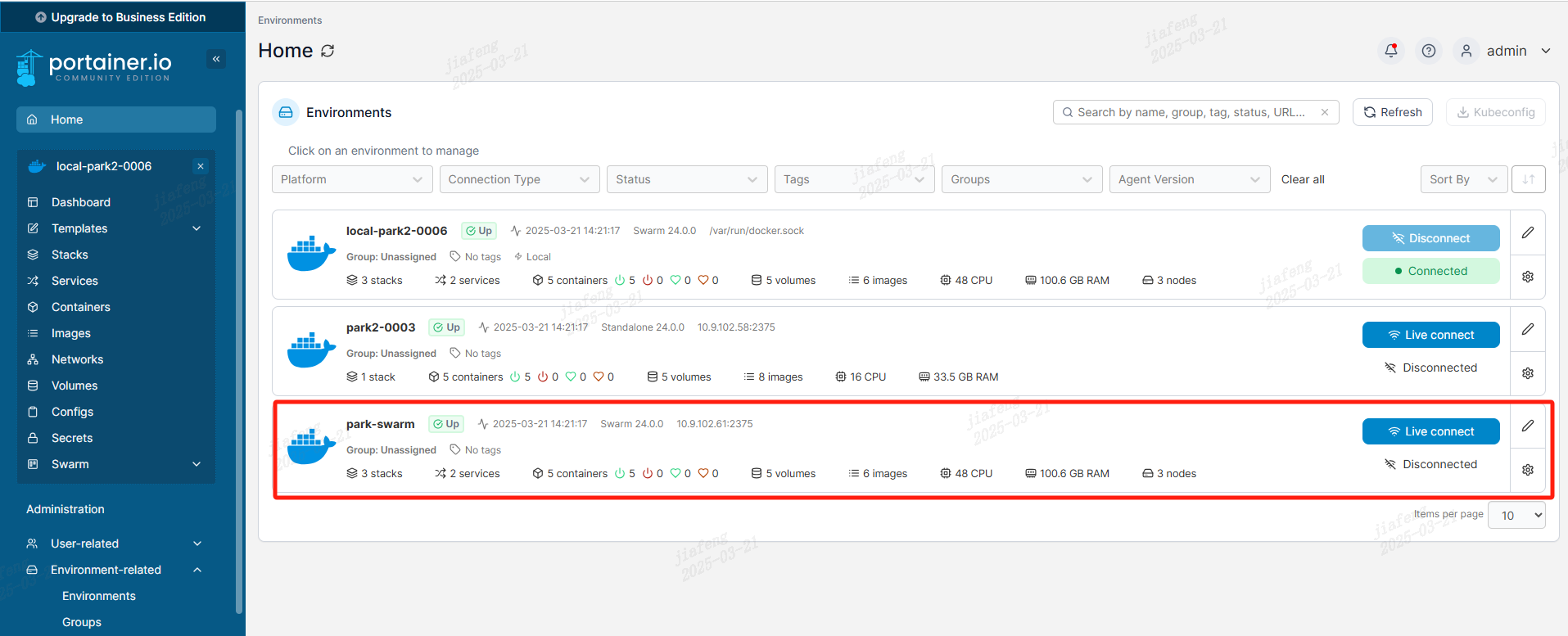
添加完成之后如下所示
选择Stacks,Web Editer方式输入docker-compose内容
version: '3' services: # Redis 主节点 redis-master: image: swr.cn-north-4.myhuaweicloud.com/ddn-k8s/docker.io/redis:5.0.14 ports: - "6379:6379" command: redis-server --requirepass aTPTF6An*jX5 volumes: - redis-master-data:/data deploy: replicas: 1 placement: constraints: - node.hostname == park2-0007.novalocal restart_policy: condition: on-failure networks: - swarm-overlay # Redis 从节点 1 redis-slave: image: swr.cn-north-4.myhuaweicloud.com/ddn-k8s/docker.io/redis:5.0.14 ports: - "6380:6379" # 修改为不同的宿主机端口 command: redis-server --slaveof redis-master 6379 --requirepass aTPTF6An*jX5 --masterauth aTPTF6An*jX5 volumes: - redis-slave-data:/data deploy: replicas: 1 placement: constraints: - node.hostname == park2-0008.novalocal restart_policy: condition: on-failure networks: - swarm-overlay volumes: redis-master-data: driver: local redis-slave-data: driver: local networks: swarm-overlay: driver: overlay
部署验证
# 连接到主节点 redis-cli -h <主节点 IP> -p 6379 -a aTPTF6An*jX5 # 设置键值对 set mykey "Hello, Redis!" # 连接到从节点 redis-cli -h <从节点 IP> -p 6380 -a aTPTF6An*jX5 # 获取键值对 get mykey



 浙公网安备 33010602011771号
浙公网安备 33010602011771号