[ACTF2020]fungame
无壳,使用IDA打开
0x02 分析主要函数的内容
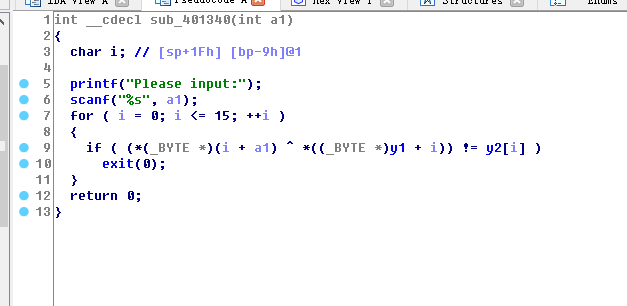
通过异或得到前面的16个字符
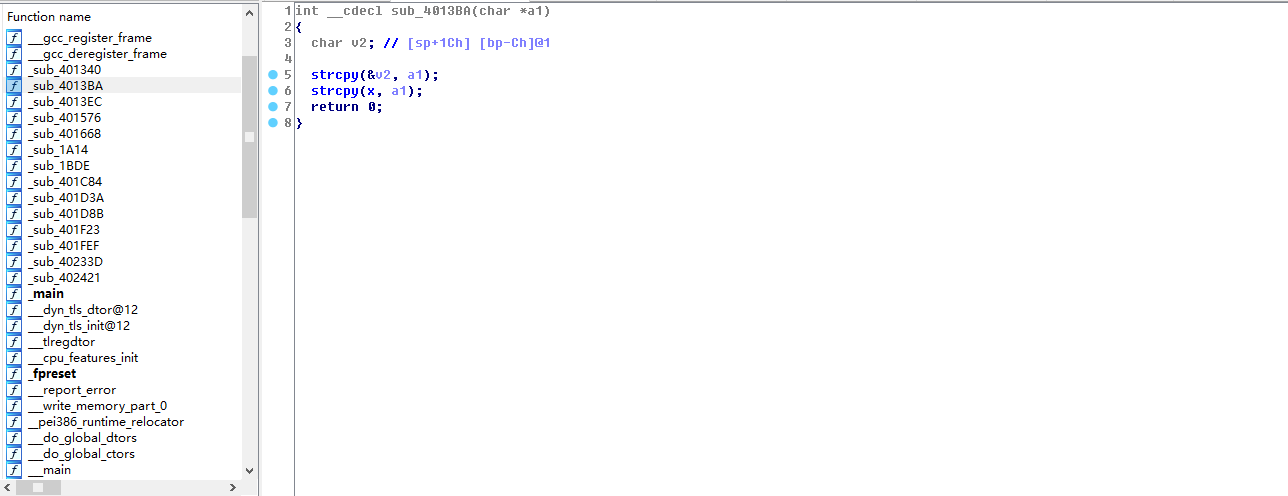
发现是栈溢出,函数先把flag复制到只能容纳12个字节的Destination,发生溢出,第二次复制进入X
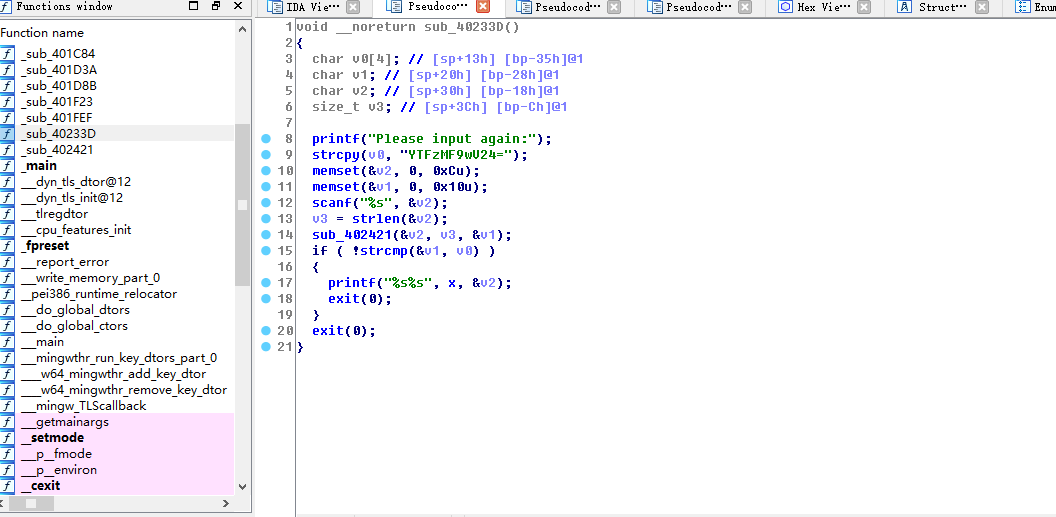
白给的溢出
1 import base64 2 y1=[0x23,0x61,0x3E,0x69,0x54,0x41,0x18,0x4D,0x6E,0x3B,0x65,0x53,0x30,0x79,0x45,0x5B] 3 y2=[0x71,0x04,0x61,0x58,0x27,0x1E,0x4B,0x22,0x5E,0x64,0x3,0x26,0x5E,0x17,0x3C,0x7A] 4 flag='flag{' 5 for i in range(len(y1)): 6 flag+=chr(y1[i]^y2[i]) 7 flag+=chr(0x40)+chr(0x23)+chr(0x3D)+str(base64.b64decode('YTFzMF9wV24='),encoding = "utf-8") #bytes转str 8 print(flag+'}')
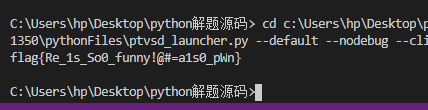
flag{Re_1s_So0_funny!@#=a1s0_pWn}
未亡人



 浙公网安备 33010602011771号
浙公网安备 33010602011771号