iptables实现SNAT和DNAT,并对规则持久保存
# 环境检查
[root@PC-1 ~]# hostname -I
192.168.100.11
[root@PC-2 ~]# hostname -I
192.168.100.12
eth1:192.168.100.13
[root@firewall ~]#
eth0:10.0.0.13
eth1:192.168.100.13
[root@Server ~]# hostname -I
10.0.0.14
# 连接检查
[root@PC-1 ~]# ping 192.168.100.13
PING 192.168.100.13 (192.168.100.13) 56(84) bytes of data.
64 bytes from 192.168.100.13: icmp_seq=1 ttl=64 time=0.173 ms
64 bytes from 192.168.100.13: icmp_seq=2 ttl=64 time=0.229 ms
# 测试防火墙连通性
[root@firewall ~]# curl 10.0.0.14
Welcome Server 10.0.0.14
# 检查配置
[root@firewall ~]# iptables -vnL -t nat
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
1 实现SNAT,并保持永久规则
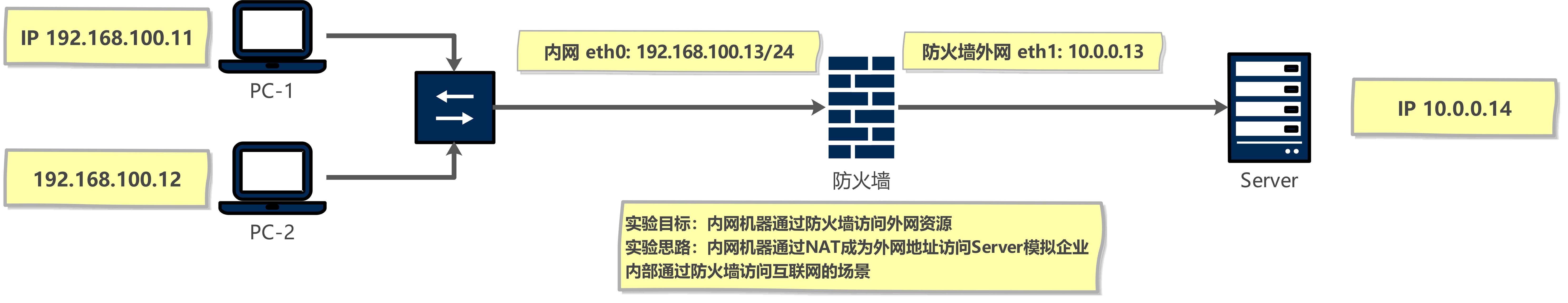
1.1 创建规则
# 启用路由转发
[root@firewall ~]# echo "net.ipv4.ip_forward=1" >> /etc/sysctl.conf
[root@firewall ~]# sysctl -p
net.ipv4.ip_forward = 1
# 配置防火墙
[root@firewall ~]# iptables -t nat -A POSTROUTING -s 192.168.100.0/24 -j SNAT --to-source 10.0.0.13
[root@firewall ~]# iptables -vnL -t nat
Chain PREROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
1 116 SNAT all -- * * 192.168.100.0/24 0.0.0.0/0 to:10.0.0.13
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
# 测试效果 没问题
[root@PC-1 ~]# curl 10.0.0.14
Welcome Server 10.0.0.14
[root@PC-2 ~]# curl 10.0.0.14
Welcome Server 10.0.0.14
# 查看Server访问日志
[root@Server ~]# tail /var/log/nginx/access.log
10.0.0.13 - - [24/Nov/2022:15:27:46 +0800] "GET / HTTP/1.1" 200 26 "-" "curl/7.61.1" "-"
10.0.0.13 - - [24/Nov/2022:15:29:14 +0800] "GET / HTTP/1.1" 200 26 "-" "curl/7.61.1" "-"
# 查看序号(不用操作)
[root@firewall ~]# iptables -vnL -t nat --line-numbers
# 可以删除没用的信息(不用操作)
[root@firewall ~]# iptables -t nat -D POSTROUTING 2
1.2 永久保存
# 安装iptable-services
[root@firewall ~]# yum -y install iptables-services
# 备份配置
[root@firewall ~]# cp /etc/sysconfig/iptables{,.bak}
[root@firewall ~]# ll /etc/sysconfig/iptables*
-rw------- 1 root root 550 Aug 25 2021 /etc/sysconfig/iptables
-rw------- 1 root root 550 Nov 24 19:04 /etc/sysconfig/iptables.bak
-rw-------. 1 root root 2116 Aug 25 2021 /etc/sysconfig/iptables-config
# 查看备份情况
[root@firewall ~]# cat /etc/sysconfig/iptables.bak
# sample configuration for iptables service
# you can edit this manually or use system-config-firewall
# please do not ask us to add additional ports/services to this default configuration
*filter
:INPUT ACCEPT [0:0]
:FORWARD ACCEPT [0:0]
:OUTPUT ACCEPT [0:0]
-A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT
-A INPUT -p icmp -j ACCEPT
-A INPUT -i lo -j ACCEPT
-A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT
-A INPUT -j REJECT --reject-with icmp-host-prohibited
-A FORWARD -j REJECT --reject-with icmp-host-prohibited
COMMIT
# 写入配置
[root@firewall ~]# iptables-save > /etc/sysconfig/iptables
# 设置开机启动
[root@firewall ~]# systemctl enable iptables.service
Created symlink /etc/systemd/system/multi-user.target.wants/iptables.service → /usr/lib/systemd/system/iptables.service.
# 重启后查看配置生效情况
[root@firewall ~]# reboot
[root@firewall ~]# iptables -nvL -t nat
Chain PREROUTING (policy ACCEPT 1 packets, 52 bytes)
pkts bytes target prot opt in out source destination
Chain INPUT (policy ACCEPT 1 packets, 52 bytes)
pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
0 0 SNAT all -- * * 192.168.100.0/24 0.0.0.0/0 to:10.0.0.13
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
pkts bytes target prot opt in out source destination
2 实现DNAT,并保持永久规则
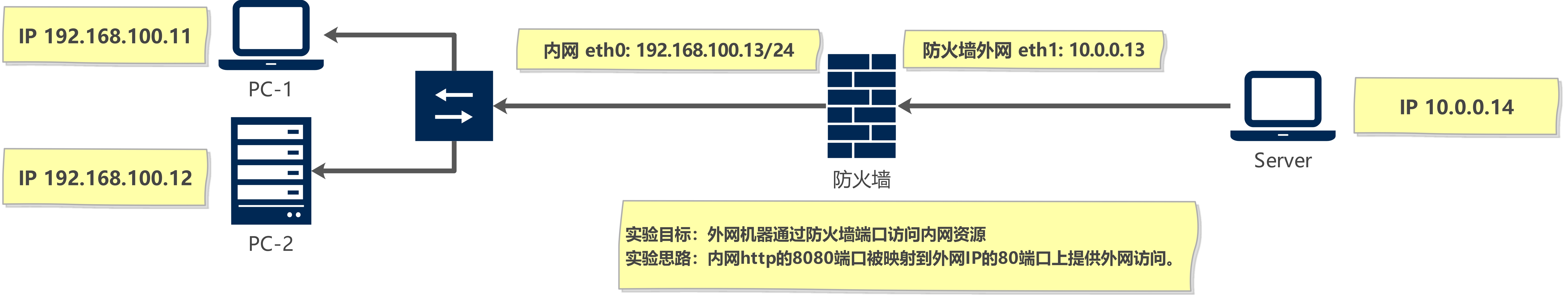
2.1 DNAT实现
# 内网服务器搭建过程省略,直接测试
[root@firewall ~]# curl 192.168.100.12:8080
Welcome 192.168.100.12
# 未配置前测试不通
[root@Server ~]# curl 10.0.0.13:80
curl: (7) Failed to connect to 10.0.0.13 port 80: Connection refused
# 配置iptables
[root@firewall ~]# iptables -t nat -A PREROUTING -d 10.0.0.13 -p tcp --dport 80 -j DNAT --to-destination 192.168.100.12:8080
# 查看配置
[root@firewall ~]# iptables -vnL -t nat --line-numbers
Chain PREROUTING (policy ACCEPT 54 packets, 5812 bytes)
num pkts bytes target prot opt in out source destination
1 2 120 DNAT tcp -- * * 0.0.0.0/0 10.0.0.13 tcp dpt:80 to:192.168.100.12:8080
Chain INPUT (policy ACCEPT 15 packets, 2210 bytes)
num pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 2 packets, 120 bytes)
num pkts bytes target prot opt in out source destination
1 26 1604 SNAT all -- * * 192.168.100.0/24 0.0.0.0/0 to:10.0.0.13
Chain OUTPUT (policy ACCEPT 6 packets, 360 bytes)
num pkts bytes target prot opt in out source destination
# 测试连通性
[root@node4 ~]# curl 10.0.0.13
Welcome 192.168.100.12
# 查看日志
[root@PC-2 ~]# tail -f /var/log/nginx/access.log
10.0.0.14 - - [24/Nov/2022:20:31:43 +0800] "GET / HTTP/1.1" 200 23 "-" "curl/7.61.1" "-"
10.0.0.14 - - [24/Nov/2022:20:41:05 +0800] "GET / HTTP/1.1" 200 23 "-" "curl/7.61.1" "-"
2.2 永久保存
# 写入配置 重启
[root@firewall ~]# iptables-save > /etc/sysconfig/iptables
[root@firewall ~]# reboot
# 查看效果 重新启动后配置都在
[root@firewall ~]# iptables -vnL -t nat --line-numbers
Chain PREROUTING (policy ACCEPT 11 packets, 672 bytes)
num pkts bytes target prot opt in out source destination
1 0 0 DNAT tcp -- * * 0.0.0.0/0 10.0.0.13 tcp dpt:80 to:192.168.100.12:8080
Chain INPUT (policy ACCEPT 1 packets, 52 bytes)
num pkts bytes target prot opt in out source destination
Chain POSTROUTING (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination
1 10 620 SNAT all -- * * 192.168.100.0/24 0.0.0.0/0 to:10.0.0.13
Chain OUTPUT (policy ACCEPT 0 packets, 0 bytes)
num pkts bytes target prot opt in out source destination



 浙公网安备 33010602011771号
浙公网安备 33010602011771号