python3 SSLCertVerificationError 研究
WARNING: Retrying (Retry(total=4, connect=None, read=None, redirect=None, status=None)) after connection broken by 'SSLError(SSLCertVerificationError(1, '[SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed: self-signed certificate in certificate chain (_ssl.c:1000)'))': /simple/frida-tools/ WARNING: Retrying (Retry(total=3, connect=None, read=None, redirect=None, status=None)) after connection broken by 'SSLError(SSLCertVerificationError(1, '[SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed: self-signed certificate in certificate chain (_ssl.c:1000)'))': /simple/frida-tools/ WARNING: Retrying (Retry(total=2, connect=None, read=None, redirect=None, status=None)) after connection broken by 'SSLError(SSLCertVerificationError(1, '[SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed: self-signed certificate in certificate chain (_ssl.c:1000)'))': /simple/frida-tools/ WARNING: Retrying (Retry(total=1, connect=None, read=None, redirect=None, status=None)) after connection broken by 'SSLError(SSLCertVerificationError(1, '[SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed: self-signed certificate in certificate chain (_ssl.c:1000)'))': /simple/frida-tools/ WARNING: Retrying (Retry(total=0, connect=None, read=None, redirect=None, status=None)) after connection broken by 'SSLError(SSLCertVerificationError(1, '[SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed: self-signed certificate in certificate chain (_ssl.c:1000)'))': /simple/frida-tools/ Could not fetch URL https://pypi.org/simple/frida-tools/: There was a problem confirming the ssl certificate: HTTPSConnectionPool(host='pypi.org', port=443): Max retries exceeded with url: /simple/frida-tools/ (Caused by SSLError(SSLCertVerificationError(1, '[SSL: CERTIFICATE_VERIFY_FAILED] certificate verify failed: self-signed certificate in certificate chain (_ssl.c:1000)'))) - skippin
python3 ssl验证出错,因为开启了https代理, (启动了charles工具)
我知道怎么解决这个问题, 就是关闭代理工具。但是我想探探它怎么验证的, 因为浏览器可以
以下是我的分析过程: 不想看过程的同学,可以直接看我的另一篇博客,这是完美解决方案: https://www.cnblogs.com/dzqdzq/p/18436545
1. 写了一个nodejs代码做测试, 这个是http, 直接请求, charles并没有抓到包
const axios = require('axios');
async function requestBaidu() {
try {
const response = await axios.get('http://www.baidu.com');
console.log('Status Code:', response.status);
console.log('Response Headers:', response.headers);
console.log('Response Data:', response.data.substring(0, 100)); // 输出前100个字符
} catch (error) {
console.error('Error requesting Baidu:', error);
}
}
requestBaidu();
我发现了在命令行设置: export HTTP_PROXY="http://127.0.0.1:8888", 再次运行就可以抓到了。
2. 继续探路, 用python试试
import requests # 发起请求 response = requests.get('http://www.baidu.com') # 打印响应内容 print(response.text)
执行结果非常好,Charles能抓包到,
通过1和2,说明了python3默认是走代理的! (后面的步骤说明不是python3默认走代理,而是requests默认走代理)
3. 将1和2的代码,全部改成https
在设置了HTTP(S)_PROXY的终端分别执行js和python脚本: js可以正常访问,能抓包。 python不能正常访问,能抓包
在没有设置HTTP(S)_PROXY的终端分别执行js和python脚本: js可以正常访问,没抓到包。 python不能正常访问,能抓包
通过这些测试发现了一点东西,python默认走系统代码,并且验证比nodejs严格。 nodejs默认不走代理,如果设置了环境变量代理,相当于和浏览器一样了。
4. 这个结论比较有趣, 不过至少可以证明任何程序,走不走代理是app应用自己说了算! 下面的python代码,证明了这个结论:
import http.client # 创建连接 connection = http.client.HTTPConnection('baidu.com') # 发送 GET 请求 connection.request('GET', '/') # 你可以根据需要更改请求路径 # 获取响应 response = connection.getresponse() # 输出状态和内容 print(f'Status: {response.status}, Reason: {response.reason}') print(response.read().decode()) # 关闭连接 connection.close()
使用最原始的请求, 不管有没有设置http_proxy, 它都不会走代理。对它进行改造
我通过断点跟踪,发现requests库默认环境变量和系统代理。 优先获取代理环境变量,然后在获取系统代理。
nodejs axios 仅仅只是获取代理环境变量.
5. 那么现在就只有一个问题: 都走代理的情况下, 为啥nodejs可以,python不行
开启逆向之旅:
错误信息的关键: self-signed certificate
hopper载入:
/usr/local/opt/python@3.12/Frameworks/Python.framework/Versions/3.12/lib/python3.12/lib-dynload/_ssl.cpython-312-darwin.so
没有搜索到,那么查看这个so的依赖:发现了
/usr/local/opt/openssl@3/lib/libssl.3.dylib
hopper 载入它:
还是没有, 我确定它是openssl报出来的, 那么就全局查找吧, 发现了:
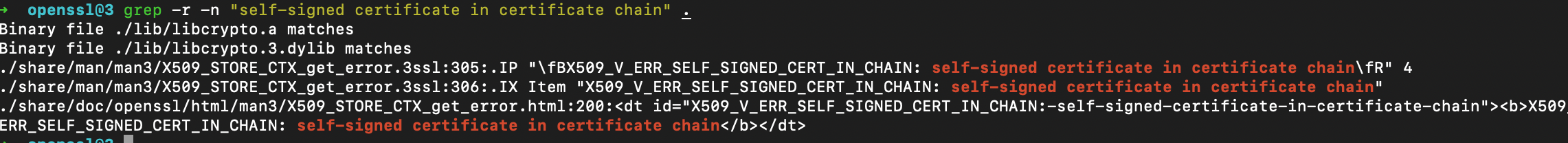
居然在libcrypto.3.dylib里面, 简直不敢相信, 好吧,继续跟踪它:
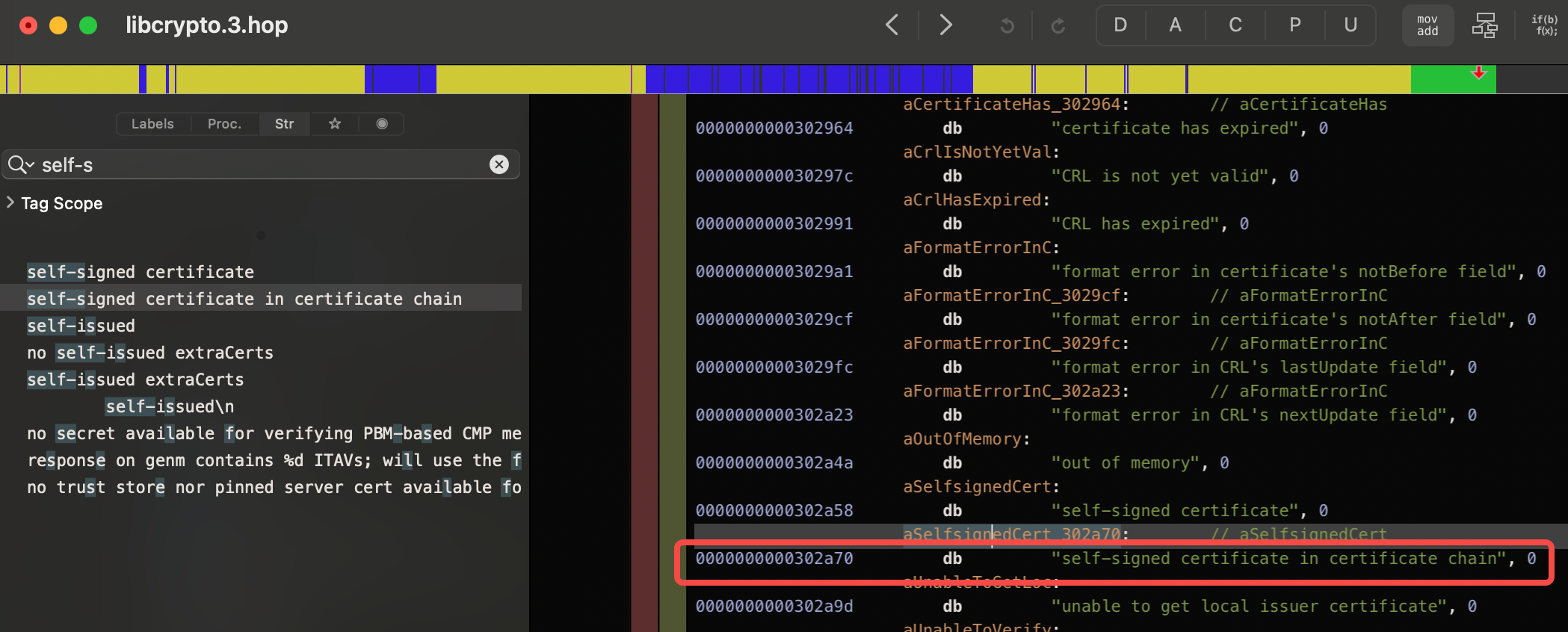
继续跟踪,看下它的触发条件,发现没有任何地方引用它... 那么就在网上拉去openssl源码吧, 它是开源的:
https://openssl-library.org/source/index.html
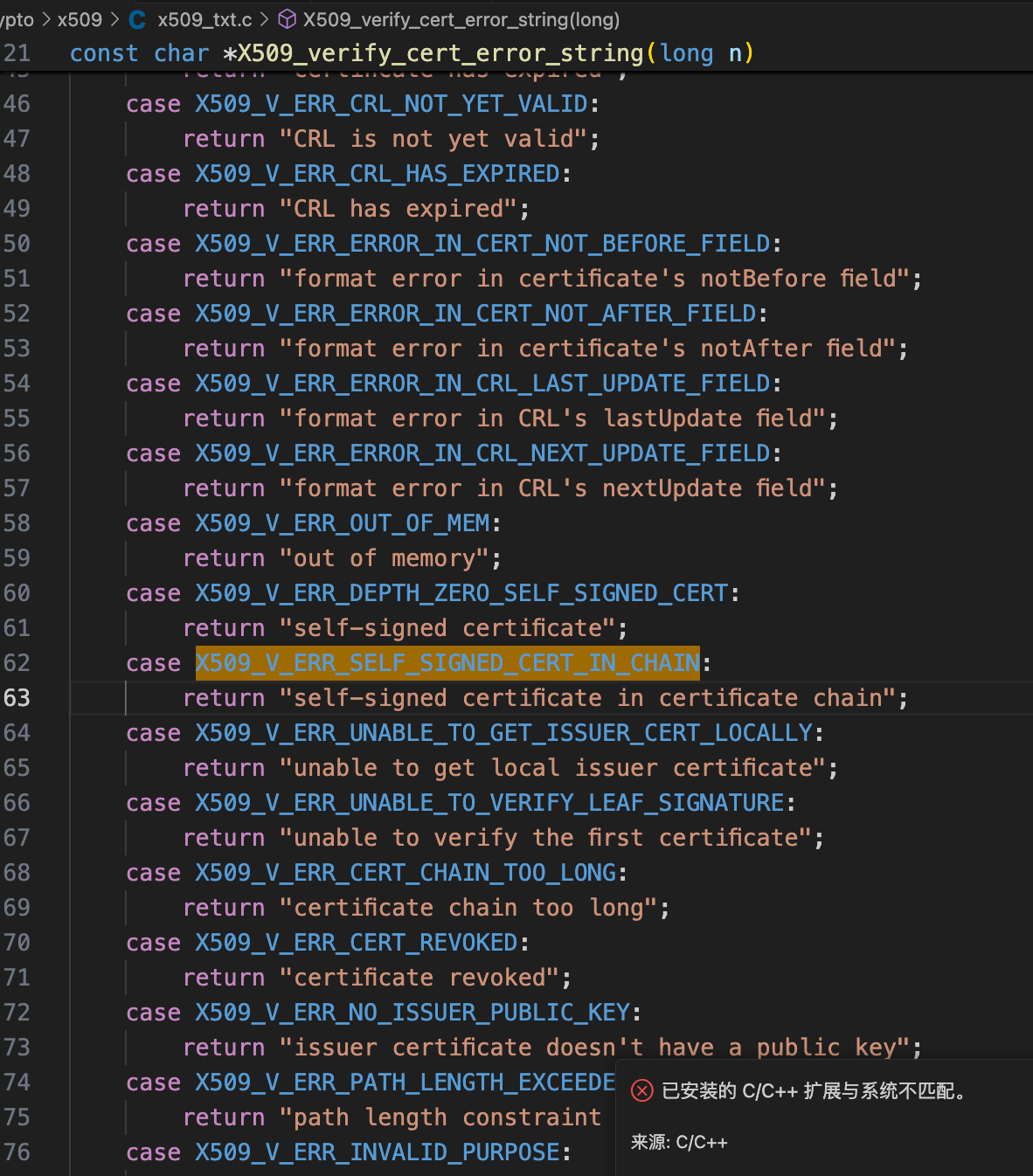
错误编号:X509_V_ERR_SELF_SIGNED_CERT_IN_CHAIN
python里有一个验证选项,如果为true,那么
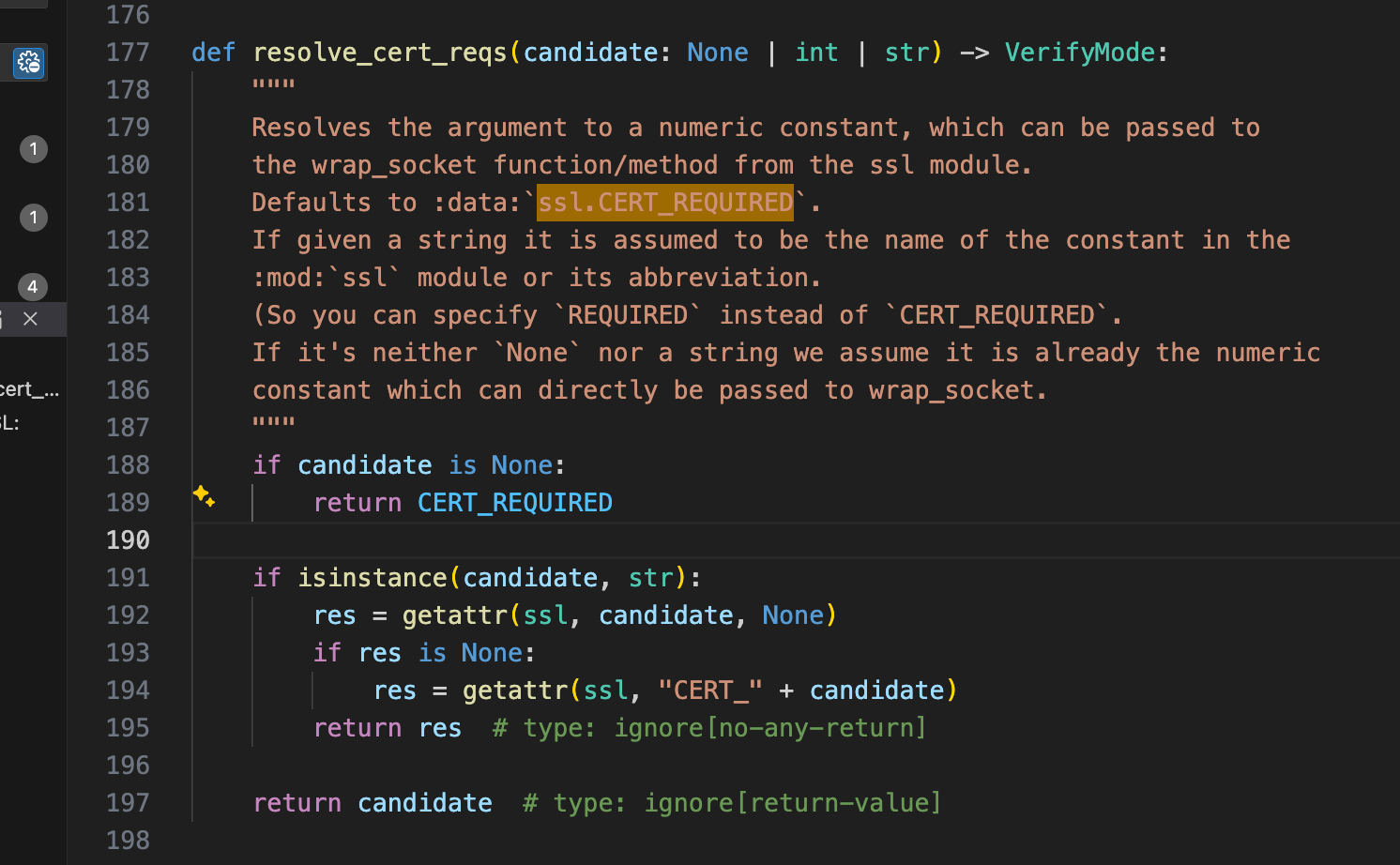
python3 也就是会默认使用VERIFY_PEER 模式,这个模式就是会让openssl库进行证书检查! 看了nodejs相关源码, https默认的模式是VERIFY_NONE, 所以不会进行任何报错!
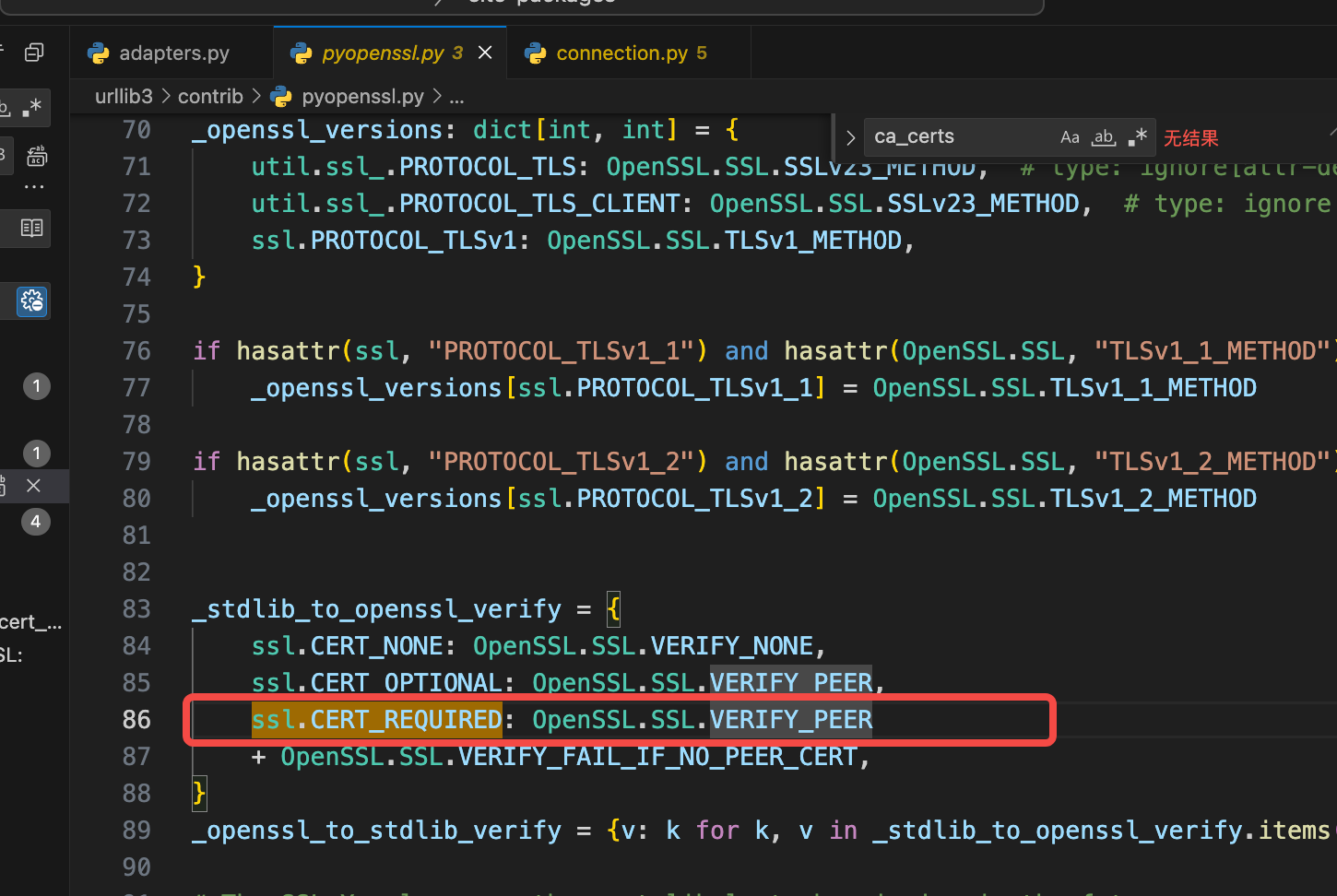
解决方案,证书验证的时候
1. requests.get("httpsUrl", verify=False)
2. 控制台 export REQUESTS_CA_BUNDLE=/path/charles-ssl-proxying-certificate.pem
或者export CURL_CA_BUNDLE=/path/charles-ssl-proxying-certificate.pem
openssl@3 openssl crl2pkcs7 -nocrl -certfile /usr/local/Cellar/python@3.12/3.12.2_1/Frameworks/Python.framework/Versions/3.12/lib/python3.12/site-packages/certifi/cacert.pem | openssl pkcs7 -print_certs -noout subject=C=BE, O=GlobalSign nv-sa, OU=Root CA, CN=GlobalSign Root CA issuer=C=BE, O=GlobalSign nv-sa, OU=Root CA, CN=GlobalSign Root CA subject=O=Entrust.net, OU=www.entrust.net/CPS_2048 incorp. by ref. (limits liab.), OU=(c) 1999 Entrust.net Limited, CN=Entrust.net Certification Authority (2048) issuer=O=Entrust.net, OU=www.entrust.net/CPS_2048 incorp. by ref. (limits liab.), OU=(c) 1999 Entrust.net Limited, CN=Entrust.net Certification Authority (2048) subject=C=IE, O=Baltimore, OU=CyberTrust, CN=Baltimore CyberTrust Root issuer=C=IE, O=Baltimore, OU=CyberTrust, CN=Baltimore CyberTrust Root subject=C=US, O=Entrust, Inc., OU=www.entrust.net/CPS is incorporated by reference, OU=(c) 2006 Entrust, Inc., CN=Entrust Root Certification Authority issuer=C=US, O=Entrust, Inc., OU=www.entrust.net/CPS is incorporated by reference, OU=(c) 2006 Entrust, Inc., CN=Entrust Root Certification Authority subject=C=GB, ST=Greater Manchester, L=Salford, O=Comodo CA Limited, CN=AAA Certificate Services issuer=C=GB, ST=Greater Manchester, L=Salford, O=Comodo CA Limited, CN=AAA Certificate Services subject=C=BM, O=QuoVadis Limited, CN=QuoVadis Root CA 2 issuer=C=BM, O=QuoVadis Limited, CN=QuoVadis Root CA 2 subject=C=BM, O=QuoVadis Limited, CN=QuoVadis Root CA 3 issuer=C=BM, O=QuoVadis Limited, CN=QuoVadis Root CA 3 subject=C=US, OU=www.xrampsecurity.com, O=XRamp Security Services Inc, CN=XRamp Global Certification Authority issuer=C=US, OU=www.xrampsecurity.com, O=XRamp Security Services Inc, CN=XRamp Global Certification Authority subject=C=US, O=The Go Daddy Group, Inc., OU=Go Daddy Class 2 Certification Authority issuer=C=US, O=The Go Daddy Group, Inc., OU=Go Daddy Class 2 Certification Authority subject=C=US, O=Starfield Technologies, Inc., OU=Starfield Class 2 Certification Authority issuer=C=US, O=Starfield Technologies, Inc., OU=Starfield Class 2 Certification Authority subject=C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Assured ID Root CA issuer=C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Assured ID Root CA subject=C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Global Root CA issuer=C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Global Root CA subject=C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert High Assurance EV Root CA issuer=C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert High Assurance EV Root CA subject=C=CH, O=SwissSign AG, CN=SwissSign Gold CA - G2 issuer=C=CH, O=SwissSign AG, CN=SwissSign Gold CA - G2 subject=C=CH, O=SwissSign AG, CN=SwissSign Silver CA - G2 issuer=C=CH, O=SwissSign AG, CN=SwissSign Silver CA - G2 subject=C=US, O=SecureTrust Corporation, CN=SecureTrust CA issuer=C=US, O=SecureTrust Corporation, CN=SecureTrust CA subject=C=US, O=SecureTrust Corporation, CN=Secure Global CA issuer=C=US, O=SecureTrust Corporation, CN=Secure Global CA subject=C=GB, ST=Greater Manchester, L=Salford, O=COMODO CA Limited, CN=COMODO Certification Authority issuer=C=GB, ST=Greater Manchester, L=Salford, O=COMODO CA Limited, CN=COMODO Certification Authority subject=C=GB, ST=Greater Manchester, L=Salford, O=COMODO CA Limited, CN=COMODO ECC Certification Authority issuer=C=GB, ST=Greater Manchester, L=Salford, O=COMODO CA Limited, CN=COMODO ECC Certification Authority subject=C=FR, O=Dhimyotis, CN=Certigna issuer=C=FR, O=Dhimyotis, CN=Certigna subject=C=TW, O=Chunghwa Telecom Co., Ltd., OU=ePKI Root Certification Authority issuer=C=TW, O=Chunghwa Telecom Co., Ltd., OU=ePKI Root Certification Authority subject=C=RO, O=certSIGN, OU=certSIGN ROOT CA issuer=C=RO, O=certSIGN, OU=certSIGN ROOT CA subject=C=HU, L=Budapest, O=NetLock Kft., OU=Tanúsítványkiadók (Certification Services), CN=NetLock Arany (Class Gold) Főtanúsítvány issuer=C=HU, L=Budapest, O=NetLock Kft., OU=Tanúsítványkiadók (Certification Services), CN=NetLock Arany (Class Gold) Főtanúsítvány subject=C=JP, O=Japan Certification Services, Inc., CN=SecureSign RootCA11 issuer=C=JP, O=Japan Certification Services, Inc., CN=SecureSign RootCA11 subject=C=HU, L=Budapest, O=Microsec Ltd., CN=Microsec e-Szigno Root CA 2009, emailAddress=info@e-szigno.hu issuer=C=HU, L=Budapest, O=Microsec Ltd., CN=Microsec e-Szigno Root CA 2009, emailAddress=info@e-szigno.hu subject=OU=GlobalSign Root CA - R3, O=GlobalSign, CN=GlobalSign issuer=OU=GlobalSign Root CA - R3, O=GlobalSign, CN=GlobalSign subject=C=ES, O=IZENPE S.A., CN=Izenpe.com issuer=C=ES, O=IZENPE S.A., CN=Izenpe.com subject=C=US, ST=Arizona, L=Scottsdale, O=GoDaddy.com, Inc., CN=Go Daddy Root Certificate Authority - G2 issuer=C=US, ST=Arizona, L=Scottsdale, O=GoDaddy.com, Inc., CN=Go Daddy Root Certificate Authority - G2 subject=C=US, ST=Arizona, L=Scottsdale, O=Starfield Technologies, Inc., CN=Starfield Root Certificate Authority - G2 issuer=C=US, ST=Arizona, L=Scottsdale, O=Starfield Technologies, Inc., CN=Starfield Root Certificate Authority - G2 subject=C=US, ST=Arizona, L=Scottsdale, O=Starfield Technologies, Inc., CN=Starfield Services Root Certificate Authority - G2 issuer=C=US, ST=Arizona, L=Scottsdale, O=Starfield Technologies, Inc., CN=Starfield Services Root Certificate Authority - G2 subject=C=US, O=AffirmTrust, CN=AffirmTrust Commercial issuer=C=US, O=AffirmTrust, CN=AffirmTrust Commercial subject=C=US, O=AffirmTrust, CN=AffirmTrust Networking issuer=C=US, O=AffirmTrust, CN=AffirmTrust Networking subject=C=US, O=AffirmTrust, CN=AffirmTrust Premium issuer=C=US, O=AffirmTrust, CN=AffirmTrust Premium subject=C=US, O=AffirmTrust, CN=AffirmTrust Premium ECC issuer=C=US, O=AffirmTrust, CN=AffirmTrust Premium ECC subject=C=PL, O=Unizeto Technologies S.A., OU=Certum Certification Authority, CN=Certum Trusted Network CA issuer=C=PL, O=Unizeto Technologies S.A., OU=Certum Certification Authority, CN=Certum Trusted Network CA subject=C=TW, O=TAIWAN-CA, OU=Root CA, CN=TWCA Root Certification Authority issuer=C=TW, O=TAIWAN-CA, OU=Root CA, CN=TWCA Root Certification Authority subject=C=JP, O=SECOM Trust Systems CO.,LTD., OU=Security Communication RootCA2 issuer=C=JP, O=SECOM Trust Systems CO.,LTD., OU=Security Communication RootCA2 subject=C=IT, L=Milan, O=Actalis S.p.A./03358520967, CN=Actalis Authentication Root CA issuer=C=IT, L=Milan, O=Actalis S.p.A./03358520967, CN=Actalis Authentication Root CA subject=C=NO, O=Buypass AS-983163327, CN=Buypass Class 2 Root CA issuer=C=NO, O=Buypass AS-983163327, CN=Buypass Class 2 Root CA subject=C=NO, O=Buypass AS-983163327, CN=Buypass Class 3 Root CA issuer=C=NO, O=Buypass AS-983163327, CN=Buypass Class 3 Root CA subject=C=DE, O=T-Systems Enterprise Services GmbH, OU=T-Systems Trust Center, CN=T-TeleSec GlobalRoot Class 3 issuer=C=DE, O=T-Systems Enterprise Services GmbH, OU=T-Systems Trust Center, CN=T-TeleSec GlobalRoot Class 3 subject=C=DE, O=D-Trust GmbH, CN=D-TRUST Root Class 3 CA 2 2009 issuer=C=DE, O=D-Trust GmbH, CN=D-TRUST Root Class 3 CA 2 2009 subject=C=DE, O=D-Trust GmbH, CN=D-TRUST Root Class 3 CA 2 EV 2009 issuer=C=DE, O=D-Trust GmbH, CN=D-TRUST Root Class 3 CA 2 EV 2009 subject=C=SK, L=Bratislava, O=Disig a.s., CN=CA Disig Root R2 issuer=C=SK, L=Bratislava, O=Disig a.s., CN=CA Disig Root R2 subject=CN=ACCVRAIZ1, OU=PKIACCV, O=ACCV, C=ES issuer=CN=ACCVRAIZ1, OU=PKIACCV, O=ACCV, C=ES subject=C=TW, O=TAIWAN-CA, OU=Root CA, CN=TWCA Global Root CA issuer=C=TW, O=TAIWAN-CA, OU=Root CA, CN=TWCA Global Root CA subject=O=TeliaSonera, CN=TeliaSonera Root CA v1 issuer=O=TeliaSonera, CN=TeliaSonera Root CA v1 subject=C=DE, O=T-Systems Enterprise Services GmbH, OU=T-Systems Trust Center, CN=T-TeleSec GlobalRoot Class 2 issuer=C=DE, O=T-Systems Enterprise Services GmbH, OU=T-Systems Trust Center, CN=T-TeleSec GlobalRoot Class 2 subject=CN=Atos TrustedRoot 2011, O=Atos, C=DE issuer=CN=Atos TrustedRoot 2011, O=Atos, C=DE subject=C=BM, O=QuoVadis Limited, CN=QuoVadis Root CA 1 G3 issuer=C=BM, O=QuoVadis Limited, CN=QuoVadis Root CA 1 G3 subject=C=BM, O=QuoVadis Limited, CN=QuoVadis Root CA 2 G3 issuer=C=BM, O=QuoVadis Limited, CN=QuoVadis Root CA 2 G3 subject=C=BM, O=QuoVadis Limited, CN=QuoVadis Root CA 3 G3 issuer=C=BM, O=QuoVadis Limited, CN=QuoVadis Root CA 3 G3 subject=C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Assured ID Root G2 issuer=C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Assured ID Root G2 subject=C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Assured ID Root G3 issuer=C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Assured ID Root G3 subject=C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Global Root G2 issuer=C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Global Root G2 subject=C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Global Root G3 issuer=C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Global Root G3 subject=C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Trusted Root G4 issuer=C=US, O=DigiCert Inc, OU=www.digicert.com, CN=DigiCert Trusted Root G4 subject=C=GB, ST=Greater Manchester, L=Salford, O=COMODO CA Limited, CN=COMODO RSA Certification Authority issuer=C=GB, ST=Greater Manchester, L=Salford, O=COMODO CA Limited, CN=COMODO RSA Certification Authority subject=C=US, ST=New Jersey, L=Jersey City, O=The USERTRUST Network, CN=USERTrust RSA Certification Authority issuer=C=US, ST=New Jersey, L=Jersey City, O=The USERTRUST Network, CN=USERTrust RSA Certification Authority subject=C=US, ST=New Jersey, L=Jersey City, O=The USERTRUST Network, CN=USERTrust ECC Certification Authority issuer=C=US, ST=New Jersey, L=Jersey City, O=The USERTRUST Network, CN=USERTrust ECC Certification Authority subject=OU=GlobalSign ECC Root CA - R5, O=GlobalSign, CN=GlobalSign issuer=OU=GlobalSign ECC Root CA - R5, O=GlobalSign, CN=GlobalSign subject=C=US, O=IdenTrust, CN=IdenTrust Commercial Root CA 1 issuer=C=US, O=IdenTrust, CN=IdenTrust Commercial Root CA 1 subject=C=US, O=IdenTrust, CN=IdenTrust Public Sector Root CA 1 issuer=C=US, O=IdenTrust, CN=IdenTrust Public Sector Root CA 1 subject=C=US, O=Entrust, Inc., OU=See www.entrust.net/legal-terms, OU=(c) 2009 Entrust, Inc. - for authorized use only, CN=Entrust Root Certification Authority - G2 issuer=C=US, O=Entrust, Inc., OU=See www.entrust.net/legal-terms, OU=(c) 2009 Entrust, Inc. - for authorized use only, CN=Entrust Root Certification Authority - G2 subject=C=US, O=Entrust, Inc., OU=See www.entrust.net/legal-terms, OU=(c) 2012 Entrust, Inc. - for authorized use only, CN=Entrust Root Certification Authority - EC1 issuer=C=US, O=Entrust, Inc., OU=See www.entrust.net/legal-terms, OU=(c) 2012 Entrust, Inc. - for authorized use only, CN=Entrust Root Certification Authority - EC1 subject=C=CN, O=China Financial Certification Authority, CN=CFCA EV ROOT issuer=C=CN, O=China Financial Certification Authority, CN=CFCA EV ROOT subject=C=CH, O=WISeKey, OU=OISTE Foundation Endorsed, CN=OISTE WISeKey Global Root GB CA issuer=C=CH, O=WISeKey, OU=OISTE Foundation Endorsed, CN=OISTE WISeKey Global Root GB CA subject=C=PL, O=Krajowa Izba Rozliczeniowa S.A., CN=SZAFIR ROOT CA2 issuer=C=PL, O=Krajowa Izba Rozliczeniowa S.A., CN=SZAFIR ROOT CA2 subject=C=PL, O=Unizeto Technologies S.A., OU=Certum Certification Authority, CN=Certum Trusted Network CA 2 issuer=C=PL, O=Unizeto Technologies S.A., OU=Certum Certification Authority, CN=Certum Trusted Network CA 2 subject=C=GR, L=Athens, O=Hellenic Academic and Research Institutions Cert. Authority, CN=Hellenic Academic and Research Institutions RootCA 2015 issuer=C=GR, L=Athens, O=Hellenic Academic and Research Institutions Cert. Authority, CN=Hellenic Academic and Research Institutions RootCA 2015 subject=C=GR, L=Athens, O=Hellenic Academic and Research Institutions Cert. Authority, CN=Hellenic Academic and Research Institutions ECC RootCA 2015 issuer=C=GR, L=Athens, O=Hellenic Academic and Research Institutions Cert. Authority, CN=Hellenic Academic and Research Institutions ECC RootCA 2015 subject=C=US, O=Internet Security Research Group, CN=ISRG Root X1 issuer=C=US, O=Internet Security Research Group, CN=ISRG Root X1 subject=C=ES, O=FNMT-RCM, OU=AC RAIZ FNMT-RCM issuer=C=ES, O=FNMT-RCM, OU=AC RAIZ FNMT-RCM subject=C=US, O=Amazon, CN=Amazon Root CA 1 issuer=C=US, O=Amazon, CN=Amazon Root CA 1 subject=C=US, O=Amazon, CN=Amazon Root CA 2 issuer=C=US, O=Amazon, CN=Amazon Root CA 2 subject=C=US, O=Amazon, CN=Amazon Root CA 3 issuer=C=US, O=Amazon, CN=Amazon Root CA 3 subject=C=US, O=Amazon, CN=Amazon Root CA 4 issuer=C=US, O=Amazon, CN=Amazon Root CA 4 subject=C=TR, L=Gebze - Kocaeli, O=Turkiye Bilimsel ve Teknolojik Arastirma Kurumu - TUBITAK, OU=Kamu Sertifikasyon Merkezi - Kamu SM, CN=TUBITAK Kamu SM SSL Kok Sertifikasi - Surum 1 issuer=C=TR, L=Gebze - Kocaeli, O=Turkiye Bilimsel ve Teknolojik Arastirma Kurumu - TUBITAK, OU=Kamu Sertifikasyon Merkezi - Kamu SM, CN=TUBITAK Kamu SM SSL Kok Sertifikasi - Surum 1 subject=C=CN, O=GUANG DONG CERTIFICATE AUTHORITY CO.,LTD., CN=GDCA TrustAUTH R5 ROOT issuer=C=CN, O=GUANG DONG CERTIFICATE AUTHORITY CO.,LTD., CN=GDCA TrustAUTH R5 ROOT subject=C=US, ST=Texas, L=Houston, O=SSL Corporation, CN=SSL.com Root Certification Authority RSA issuer=C=US, ST=Texas, L=Houston, O=SSL Corporation, CN=SSL.com Root Certification Authority RSA subject=C=US, ST=Texas, L=Houston, O=SSL Corporation, CN=SSL.com Root Certification Authority ECC issuer=C=US, ST=Texas, L=Houston, O=SSL Corporation, CN=SSL.com Root Certification Authority ECC subject=C=US, ST=Texas, L=Houston, O=SSL Corporation, CN=SSL.com EV Root Certification Authority RSA R2 issuer=C=US, ST=Texas, L=Houston, O=SSL Corporation, CN=SSL.com EV Root Certification Authority RSA R2 subject=C=US, ST=Texas, L=Houston, O=SSL Corporation, CN=SSL.com EV Root Certification Authority ECC issuer=C=US, ST=Texas, L=Houston, O=SSL Corporation, CN=SSL.com EV Root Certification Authority ECC subject=OU=GlobalSign Root CA - R6, O=GlobalSign, CN=GlobalSign issuer=OU=GlobalSign Root CA - R6, O=GlobalSign, CN=GlobalSign subject=C=CH, O=WISeKey, OU=OISTE Foundation Endorsed, CN=OISTE WISeKey Global Root GC CA issuer=C=CH, O=WISeKey, OU=OISTE Foundation Endorsed, CN=OISTE WISeKey Global Root GC CA subject=C=CN, O=UniTrust, CN=UCA Global G2 Root issuer=C=CN, O=UniTrust, CN=UCA Global G2 Root subject=C=CN, O=UniTrust, CN=UCA Extended Validation Root issuer=C=CN, O=UniTrust, CN=UCA Extended Validation Root subject=C=FR, O=Dhimyotis, OU=0002 48146308100036, CN=Certigna Root CA issuer=C=FR, O=Dhimyotis, OU=0002 48146308100036, CN=Certigna Root CA subject=C=IN, OU=emSign PKI, O=eMudhra Technologies Limited, CN=emSign Root CA - G1 issuer=C=IN, OU=emSign PKI, O=eMudhra Technologies Limited, CN=emSign Root CA - G1 subject=C=IN, OU=emSign PKI, O=eMudhra Technologies Limited, CN=emSign ECC Root CA - G3 issuer=C=IN, OU=emSign PKI, O=eMudhra Technologies Limited, CN=emSign ECC Root CA - G3 subject=C=US, OU=emSign PKI, O=eMudhra Inc, CN=emSign Root CA - C1 issuer=C=US, OU=emSign PKI, O=eMudhra Inc, CN=emSign Root CA - C1 subject=C=US, OU=emSign PKI, O=eMudhra Inc, CN=emSign ECC Root CA - C3 issuer=C=US, OU=emSign PKI, O=eMudhra Inc, CN=emSign ECC Root CA - C3 subject=C=HK, ST=Hong Kong, L=Hong Kong, O=Hongkong Post, CN=Hongkong Post Root CA 3 issuer=C=HK, ST=Hong Kong, L=Hong Kong, O=Hongkong Post, CN=Hongkong Post Root CA 3 subject=C=US, O=Entrust, Inc., OU=See www.entrust.net/legal-terms, OU=(c) 2015 Entrust, Inc. - for authorized use only, CN=Entrust Root Certification Authority - G4 issuer=C=US, O=Entrust, Inc., OU=See www.entrust.net/legal-terms, OU=(c) 2015 Entrust, Inc. - for authorized use only, CN=Entrust Root Certification Authority - G4 subject=C=US, O=Microsoft Corporation, CN=Microsoft ECC Root Certificate Authority 2017 issuer=C=US, O=Microsoft Corporation, CN=Microsoft ECC Root Certificate Authority 2017 subject=C=US, O=Microsoft Corporation, CN=Microsoft RSA Root Certificate Authority 2017 issuer=C=US, O=Microsoft Corporation, CN=Microsoft RSA Root Certificate Authority 2017 subject=C=HU, L=Budapest, O=Microsec Ltd., organizationIdentifier=VATHU-23584497, CN=e-Szigno Root CA 2017 issuer=C=HU, L=Budapest, O=Microsec Ltd., organizationIdentifier=VATHU-23584497, CN=e-Szigno Root CA 2017 subject=C=RO, O=CERTSIGN SA, OU=certSIGN ROOT CA G2 issuer=C=RO, O=CERTSIGN SA, OU=certSIGN ROOT CA G2 subject=C=US, ST=Illinois, L=Chicago, O=Trustwave Holdings, Inc., CN=Trustwave Global Certification Authority issuer=C=US, ST=Illinois, L=Chicago, O=Trustwave Holdings, Inc., CN=Trustwave Global Certification Authority subject=C=US, ST=Illinois, L=Chicago, O=Trustwave Holdings, Inc., CN=Trustwave Global ECC P256 Certification Authority issuer=C=US, ST=Illinois, L=Chicago, O=Trustwave Holdings, Inc., CN=Trustwave Global ECC P256 Certification Authority subject=C=US, ST=Illinois, L=Chicago, O=Trustwave Holdings, Inc., CN=Trustwave Global ECC P384 Certification Authority issuer=C=US, ST=Illinois, L=Chicago, O=Trustwave Holdings, Inc., CN=Trustwave Global ECC P384 Certification Authority subject=C=KR, O=NAVER BUSINESS PLATFORM Corp., CN=NAVER Global Root Certification Authority issuer=C=KR, O=NAVER BUSINESS PLATFORM Corp., CN=NAVER Global Root Certification Authority subject=C=ES, O=FNMT-RCM, OU=Ceres, organizationIdentifier=VATES-Q2826004J, CN=AC RAIZ FNMT-RCM SERVIDORES SEGUROS issuer=C=ES, O=FNMT-RCM, OU=Ceres, organizationIdentifier=VATES-Q2826004J, CN=AC RAIZ FNMT-RCM SERVIDORES SEGUROS subject=C=BE, O=GlobalSign nv-sa, CN=GlobalSign Root R46 issuer=C=BE, O=GlobalSign nv-sa, CN=GlobalSign Root R46 subject=C=BE, O=GlobalSign nv-sa, CN=GlobalSign Root E46 issuer=C=BE, O=GlobalSign nv-sa, CN=GlobalSign Root E46 subject=C=AT, O=e-commerce monitoring GmbH, CN=GLOBALTRUST 2020 issuer=C=AT, O=e-commerce monitoring GmbH, CN=GLOBALTRUST 2020 subject=serialNumber=G63287510, C=ES, O=ANF Autoridad de Certificacion, OU=ANF CA Raiz, CN=ANF Secure Server Root CA issuer=serialNumber=G63287510, C=ES, O=ANF Autoridad de Certificacion, OU=ANF CA Raiz, CN=ANF Secure Server Root CA subject=C=PL, O=Asseco Data Systems S.A., OU=Certum Certification Authority, CN=Certum EC-384 CA issuer=C=PL, O=Asseco Data Systems S.A., OU=Certum Certification Authority, CN=Certum EC-384 CA subject=C=PL, O=Asseco Data Systems S.A., OU=Certum Certification Authority, CN=Certum Trusted Root CA issuer=C=PL, O=Asseco Data Systems S.A., OU=Certum Certification Authority, CN=Certum Trusted Root CA subject=C=TN, O=Agence Nationale de Certification Electronique, CN=TunTrust Root CA issuer=C=TN, O=Agence Nationale de Certification Electronique, CN=TunTrust Root CA subject=C=GR, O=Hellenic Academic and Research Institutions CA, CN=HARICA TLS RSA Root CA 2021 issuer=C=GR, O=Hellenic Academic and Research Institutions CA, CN=HARICA TLS RSA Root CA 2021 subject=C=GR, O=Hellenic Academic and Research Institutions CA, CN=HARICA TLS ECC Root CA 2021 issuer=C=GR, O=Hellenic Academic and Research Institutions CA, CN=HARICA TLS ECC Root CA 2021 subject=C=ES, CN=Autoridad de Certificacion Firmaprofesional CIF A62634068 issuer=C=ES, CN=Autoridad de Certificacion Firmaprofesional CIF A62634068 subject=C=CN, O=iTrusChina Co.,Ltd., CN=vTrus ECC Root CA issuer=C=CN, O=iTrusChina Co.,Ltd., CN=vTrus ECC Root CA subject=C=CN, O=iTrusChina Co.,Ltd., CN=vTrus Root CA issuer=C=CN, O=iTrusChina Co.,Ltd., CN=vTrus Root CA subject=C=US, O=Internet Security Research Group, CN=ISRG Root X2 issuer=C=US, O=Internet Security Research Group, CN=ISRG Root X2 subject=C=TW, O=Chunghwa Telecom Co., Ltd., CN=HiPKI Root CA - G1 issuer=C=TW, O=Chunghwa Telecom Co., Ltd., CN=HiPKI Root CA - G1 subject=OU=GlobalSign ECC Root CA - R4, O=GlobalSign, CN=GlobalSign issuer=OU=GlobalSign ECC Root CA - R4, O=GlobalSign, CN=GlobalSign subject=C=US, O=Google Trust Services LLC, CN=GTS Root R1 issuer=C=US, O=Google Trust Services LLC, CN=GTS Root R1 subject=C=US, O=Google Trust Services LLC, CN=GTS Root R2 issuer=C=US, O=Google Trust Services LLC, CN=GTS Root R2 subject=C=US, O=Google Trust Services LLC, CN=GTS Root R3 issuer=C=US, O=Google Trust Services LLC, CN=GTS Root R3 subject=C=US, O=Google Trust Services LLC, CN=GTS Root R4 issuer=C=US, O=Google Trust Services LLC, CN=GTS Root R4 subject=C=FI, O=Telia Finland Oyj, CN=Telia Root CA v2 issuer=C=FI, O=Telia Finland Oyj, CN=Telia Root CA v2 subject=C=DE, O=D-Trust GmbH, CN=D-TRUST BR Root CA 1 2020 issuer=C=DE, O=D-Trust GmbH, CN=D-TRUST BR Root CA 1 2020 subject=C=DE, O=D-Trust GmbH, CN=D-TRUST EV Root CA 1 2020 issuer=C=DE, O=D-Trust GmbH, CN=D-TRUST EV Root CA 1 2020 subject=C=US, O=DigiCert, Inc., CN=DigiCert TLS ECC P384 Root G5 issuer=C=US, O=DigiCert, Inc., CN=DigiCert TLS ECC P384 Root G5 subject=C=US, O=DigiCert, Inc., CN=DigiCert TLS RSA4096 Root G5 issuer=C=US, O=DigiCert, Inc., CN=DigiCert TLS RSA4096 Root G5 subject=C=US, O=Certainly, CN=Certainly Root R1 issuer=C=US, O=Certainly, CN=Certainly Root R1 subject=C=US, O=Certainly, CN=Certainly Root E1 issuer=C=US, O=Certainly, CN=Certainly Root E1 subject=C=JP, O=SECOM Trust Systems CO.,LTD., CN=Security Communication RootCA3 issuer=C=JP, O=SECOM Trust Systems CO.,LTD., CN=Security Communication RootCA3 subject=C=JP, O=SECOM Trust Systems CO.,LTD., CN=Security Communication ECC RootCA1 issuer=C=JP, O=SECOM Trust Systems CO.,LTD., CN=Security Communication ECC RootCA1 subject=C=CN, O=BEIJING CERTIFICATE AUTHORITY, CN=BJCA Global Root CA1 issuer=C=CN, O=BEIJING CERTIFICATE AUTHORITY, CN=BJCA Global Root CA1 subject=C=CN, O=BEIJING CERTIFICATE AUTHORITY, CN=BJCA Global Root CA2 issuer=C=CN, O=BEIJING CERTIFICATE AUTHORITY, CN=BJCA Global Root CA2 subject=C=GB, O=Sectigo Limited, CN=Sectigo Public Server Authentication Root E46 issuer=C=GB, O=Sectigo Limited, CN=Sectigo Public Server Authentication Root E46 subject=C=GB, O=Sectigo Limited, CN=Sectigo Public Server Authentication Root R46 issuer=C=GB, O=Sectigo Limited, CN=Sectigo Public Server Authentication Root R46 subject=C=US, O=SSL Corporation, CN=SSL.com TLS RSA Root CA 2022 issuer=C=US, O=SSL Corporation, CN=SSL.com TLS RSA Root CA 2022 subject=C=US, O=SSL Corporation, CN=SSL.com TLS ECC Root CA 2022 issuer=C=US, O=SSL Corporation, CN=SSL.com TLS ECC Root CA 2022 subject=CN=Atos TrustedRoot Root CA ECC TLS 2021, O=Atos, C=DE issuer=CN=Atos TrustedRoot Root CA ECC TLS 2021, O=Atos, C=DE subject=CN=Atos TrustedRoot Root CA RSA TLS 2021, O=Atos, C=DE issuer=CN=Atos TrustedRoot Root CA RSA TLS 2021, O=Atos, C=DE subject=C=CN, O=TrustAsia Technologies, Inc., CN=TrustAsia Global Root CA G3 issuer=C=CN, O=TrustAsia Technologies, Inc., CN=TrustAsia Global Root CA G3 subject=C=CN, O=TrustAsia Technologies, Inc., CN=TrustAsia Global Root CA G4 issuer=C=CN, O=TrustAsia Technologies, Inc., CN=TrustAsia Global Root CA G4 subject=C=US, O=CommScope, CN=CommScope Public Trust ECC Root-01 issuer=C=US, O=CommScope, CN=CommScope Public Trust ECC Root-01 subject=C=US, O=CommScope, CN=CommScope Public Trust ECC Root-02 issuer=C=US, O=CommScope, CN=CommScope Public Trust ECC Root-02 subject=C=US, O=CommScope, CN=CommScope Public Trust RSA Root-01 issuer=C=US, O=CommScope, CN=CommScope Public Trust RSA Root-01 subject=C=US, O=CommScope, CN=CommScope Public Trust RSA Root-02 issuer=C=US, O=CommScope, CN=CommScope Public Trust RSA Root-02 subject=C=DE, O=Deutsche Telekom Security GmbH, CN=Telekom Security TLS ECC Root 2020 issuer=C=DE, O=Deutsche Telekom Security GmbH, CN=Telekom Security TLS ECC Root 2020 subject=C=DE, O=Deutsche Telekom Security GmbH, CN=Telekom Security TLS RSA Root 2023 issuer=C=DE, O=Deutsche Telekom Security GmbH, CN=Telekom Security TLS RSA Root 2023
python里支持以上这些机构的颁发的证书,请求的网站证书如果不在这个里面,那么就握手失败,请求不了
看下了pythons底层代码:
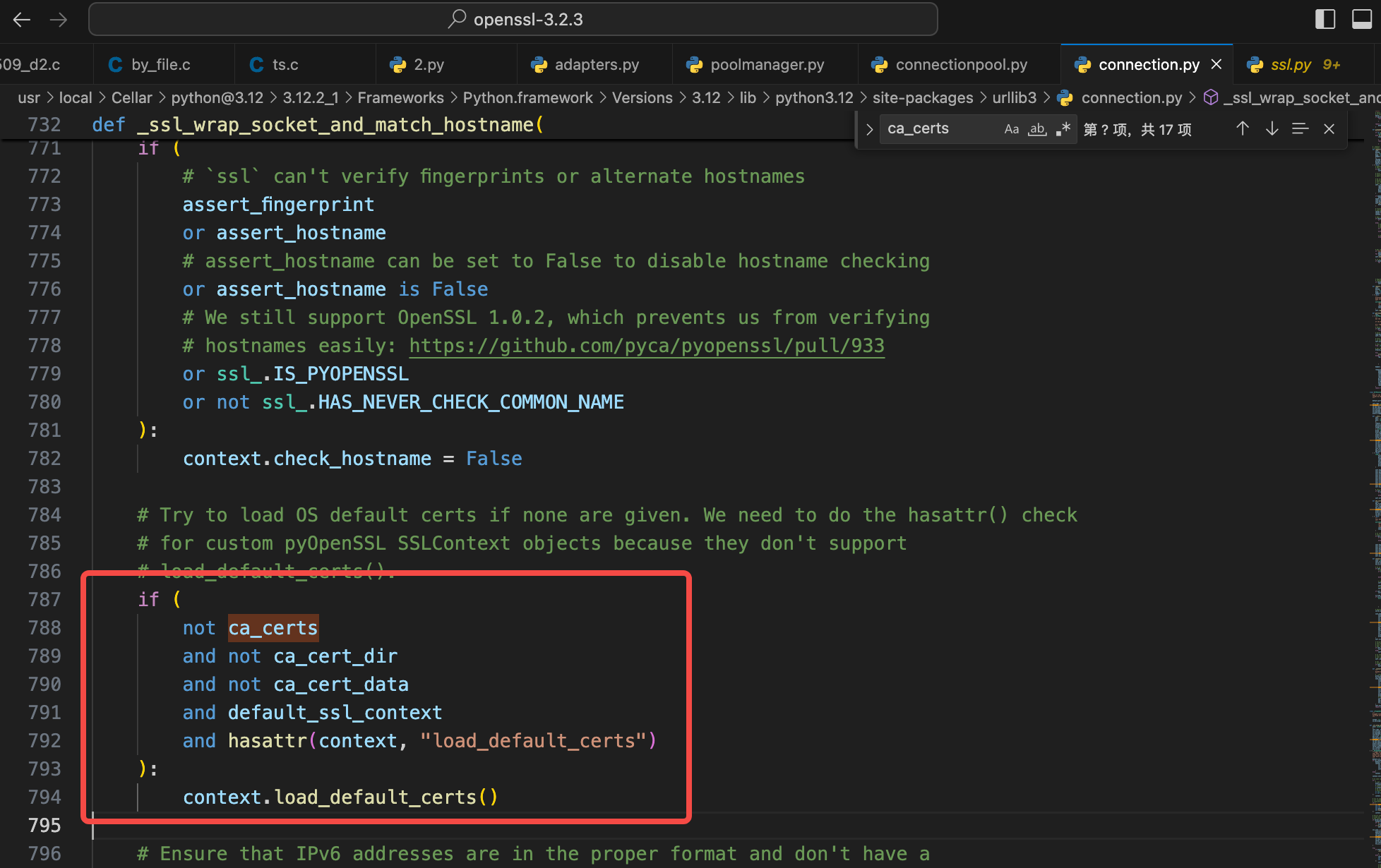
资源ca_certs ca_cert_dir无值的时候,才会加载默认的证书。 requests就默认会验证:
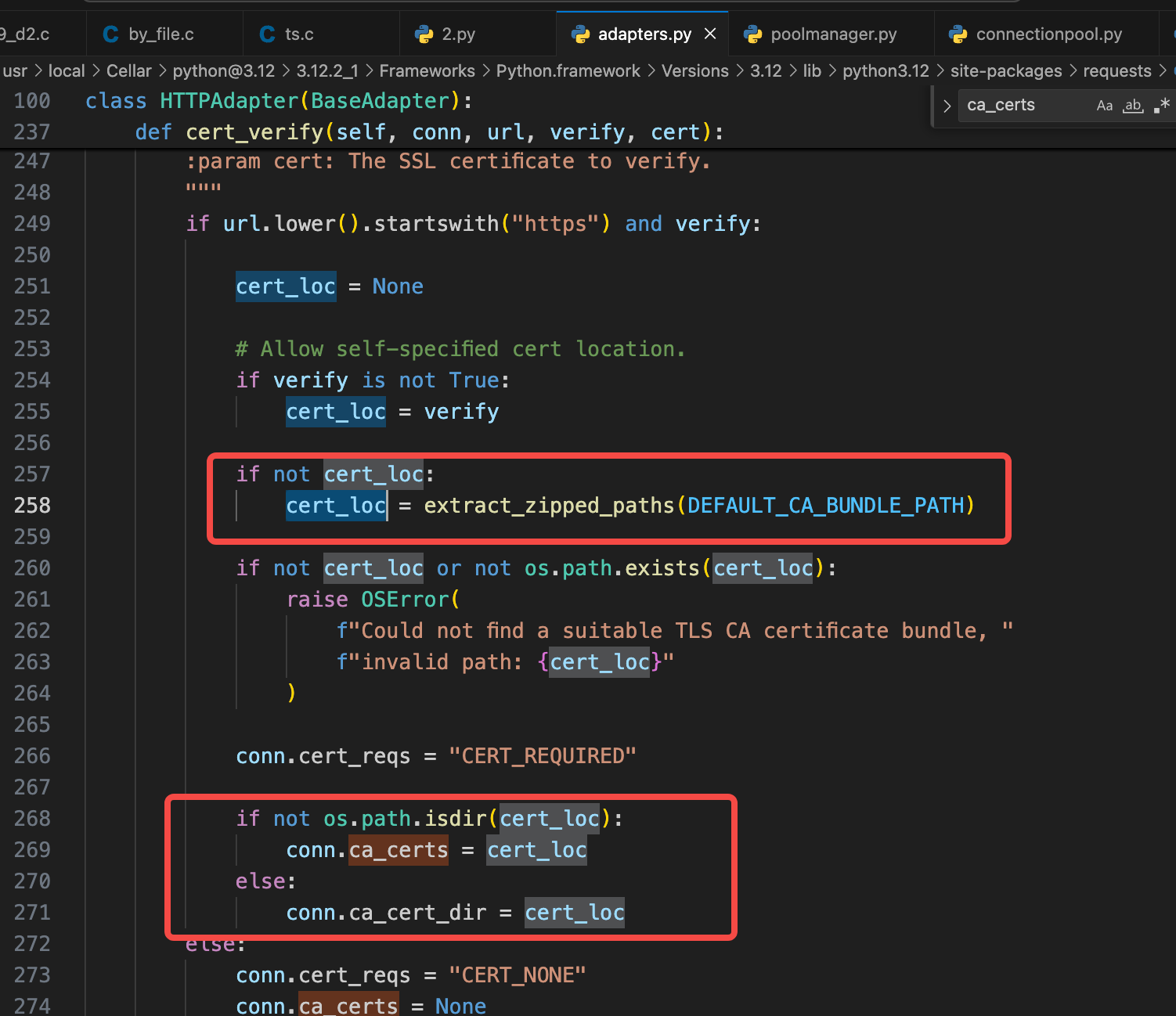
分析到这里, 已经把所有点了解通透了。 心里的疙瘩总算没了。



 浙公网安备 33010602011771号
浙公网安备 33010602011771号