东航app研究
东方航空_9.4.34.apk
梆梆加固企业版 去壳反编译 并且 frida
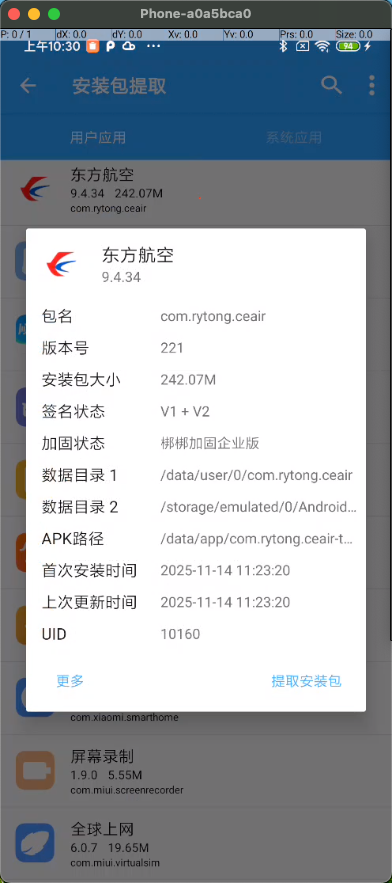
app 有 root\frida hook 等检测 [com.rytong.ceair] frida -U -f com.rytong.ceair -l find_anit_frida_so.js 15:17:52 ____ / _ | Frida 16.7.19 - A world-class dynamic instrumentation toolkit | (_| | > _ | Commands: /_/ |_| help -> Displays the help system . . . . object? -> Display information about 'object' . . . . exit/quit -> Exit . . . . . . . . More info at https://frida.re/docs/home/ . . . . . . . . Connected to Redmi Note 8 (id=a0a5bca0) Spawning `com.rytong.ceair`... addr_android_dlopen_ext 0x7e96592fb8 Spawned `com.rytong.ceair`. Resuming main thread! [Redmi Note 8::com.rytong.ceair ]-> android_dlopen_ext: /system/framework/oat/arm64/org.apache.http.legacy.boot.odex leave! android_dlopen_ext: /data/app/com.rytong.ceair-tSPhvphN2wMbYRbmGthTpQ==/oat/arm64/base.odex leave! android_dlopen_ext: /data/app/com.rytong.ceair-tSPhvphN2wMbYRbmGthTpQ==/lib/arm64/libDexHelper.so leave! Process crashed: Bad access due to invalid address *** *** *** *** *** *** *** *** *** *** *** *** *** *** *** *** *** Build fingerprint: 'xiaomi/ginkgo/ginkgo:9/PKQ1.190616.001/V11.0.8.0.PCOCNXM:user/release-keys' Revision: '0' ABI: 'arm64' pid: 12557, tid: 12582, name: om.rytong.ceair >>> com.rytong.ceair <<< signal 11 (SIGSEGV), code 1 (SEGV_MAPERR), fault addr 0x88c Cause: null pointer dereference x0 0000000000000000 x1 00000000b6a2888e x2 0000000000000fff x3 0000000000000064 x4 0000000000000072 x5 8080800000000000 x6 656e696c6e692d2d x7 646f632d78616d2d x8 00000000b6a2888e x9 000000000000088c x10 00000000b6a2888e x11 000000000000100d x12 000000000000088c x13 00303d7374696e75 x14 ffff000000000000 x15 ffffffffffffffff x16 0000007e94c1e128 x17 0000007e94b2da1c x18 0000000000000010 x19 0000007df75ff10a x20 0000007df75ff588 x21 0000007df75ff0f0 x22 0000007df75ff1d0 x23 0000007df75ff2c0 x24 0000007df75ff08a x25 0000007df7502000 x26 0000007e9a0135e0 x27 0000000000000002 x28 00000000000000be x29 0000007df75ff030 sp 0000000000000000 lr 0000000000000000 pc 000000000000088c backtrace: #00 pc 000000000000088c <unknown> *** [Redmi Note 8::com.rytong.ceair ]-> Thank you for using Frida! 🦉 [com.rytong.ceair] libDexHelper.so 是梆梆企业版 这个也要处理
特征 厂商 libchaosvmp.so 娜迦 libddog.so 娜迦 libfdog.so 娜迦 libedog.so 娜迦企业版 libexec.so 爱加密、腾讯 libexecmain.so 爱加密 ijiami.dat 爱加密 ijiami.ajm 爱加密企业版 libsecexe.so 梆梆免费版 libsecmain.so 梆梆免费版 libSecShell.so 梆梆免费版 libDexHelper.so 梆梆企业版 libDexHelper-x86.so 梆梆企业版 libprotectClass.so 360 libjiagu.so 360 libjiagu_art.so 360 libjiagu_x86.so 360 libegis.so 通付盾 libNSaferOnly.so 通付盾 libnqshield.so 网秦 libbaiduprotect.so 百度 aliprotect.dat 阿里聚安全 libsgmain.so 阿里聚安全 libsgsecuritybody.so 阿里聚安全 libmobisec.so 阿里聚安全 libtup.so 腾讯 libshell.so 腾讯 mix.dex 腾讯 mixz.dex 腾讯 libtosprotection.armeabi.so 腾讯御安全 libtosprotection.armeabi-v7a.so 腾讯御安全 libtosprotection.x86.so 腾讯御安全 libnesec.so 网易易盾 libAPKProtect.so APKProtect libkwscmm.so 几维安全 libkwscr.so 几维安全 libkwslinker.so 几维安全 libx3g.so 顶像科技 libapssec.so 盛大 librsprotect.so 瑞星
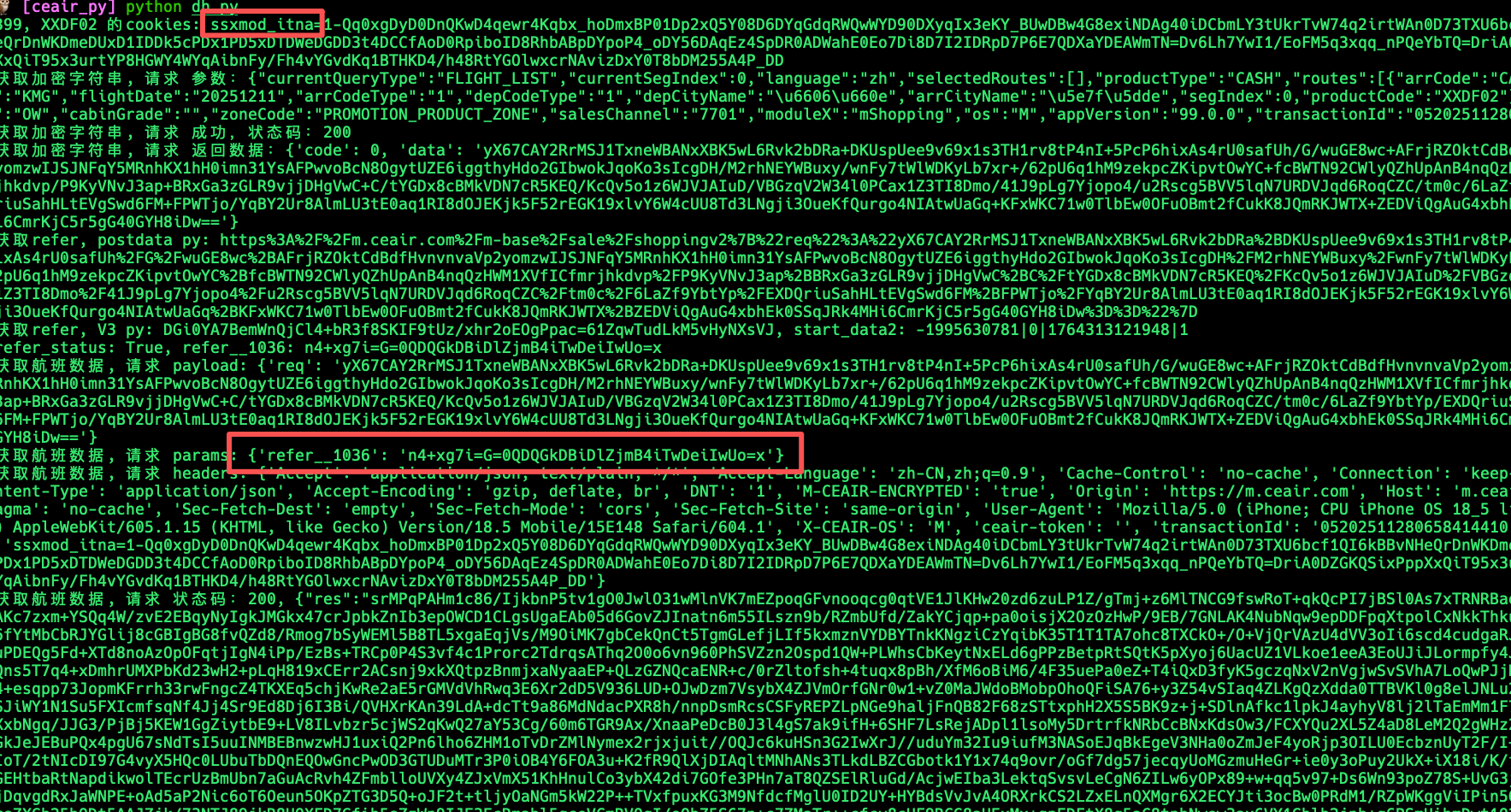
研究后发现 其实不需要 处理 apk 里面嵌的是 html 直接分析 html 发现使用的是阿里 waf sdk 2.3.14d 计算出 refer__1036 和 ssxmod_itna 即可



 浙公网安备 33010602011771号
浙公网安备 33010602011771号