一、WAF 作用
二、luajit安装
wget https://luajit.org/download/LuaJIT-2.0.5.zip --no-check-certificate
unzip LuaJIT-2.0.5.zip && cd LuaJIT-2.0.5
make -j8
make install PREFIX=/usr/local/luajit
三、tengine 一键安装
cat >>install-nginx.sh<<-"EOF"
#!/bin/bash
base_dir=`pwd`
tengine_tar=tengine-2.3.3.tar.gz
yum -y install gcc automake autoconf libtool make
yum install gcc gcc-c++ glibc -y
cd $base_dir
tar -xf openssl-1.1.1g.tar.gz
tar -xf pcre-8.44.tar.gz
tar -xf $tengine_tar
tar -xf zlib-1.2.11.tar.gz
cd $base_dir/tengine-2.3.3 && \
./configure --prefix=/opt/module/tengine-2.3.3 --with-http_ssl_module --with-http_realip_module --with-http_addition_module --with-http_sub_module --with-http_dav_module --with-http_flv_module --with-http_stub_status_module --with-http_gzip_static_module --with-stream --with-pcre=${base_dir}/pcre-8.44 --with-openssl=${base_dir}/openssl-1.1.1g --with-zlib=${base_dir}/zlib-1.2.11 --add-module=./modules/ngx_http_upstream_check_module/ --add-module=./modules/ngx_http_substitutions_filter_module --add-module=./modules/ngx_http_upstream_session_sticky_module --add-module=./modules/ngx_http_concat_module/ --add-module=./modules/ngx_http_sysguard_module/ --with-http_lua_module --with-luajit-lib=/usr/local/luajit/lib/ --with-luajit-inc=/usr/local/luajit/include/luajit-2.0/ --with-ld-opt=-Wl,-rpath,/usr/local/luajit/lib && \
make -j4 && make install
EOF
四、下载ngx_lua_waf并配置
unzip ngx_lua_waf-0.7.2.zip -d /opt/module/tengine/conf
mv ngx_lua_waf-0.7.2 waf
cat /opt/module/tengine/conf/waf/config.lua |head -3
RulePath = "/opt/module/tengine/conf/waf/wafconf/"
attacklog = "on"
logdir = "/data/logs/waf/hack/"
- 修改NGINX http代码段增加
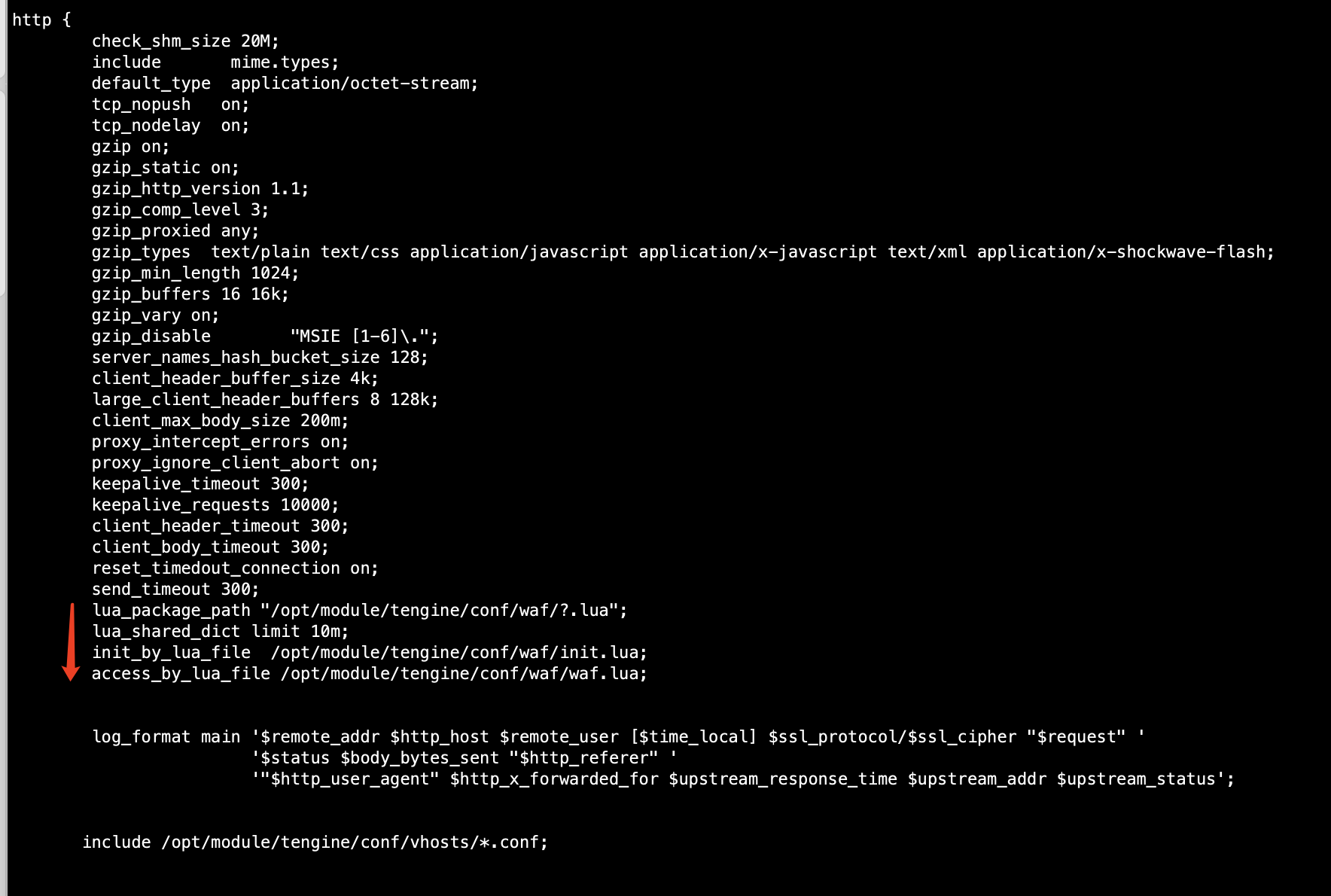
nginx.conf
lua_package_path "/opt/module/tengine/conf/waf/?.lua";
lua_shared_dict limit 10m;
init_by_lua_file /opt/module/tengine/conf/waf/init.lua;
access_by_lua_file /opt/module/tengine/conf/waf/waf.lua;
/opt/module/tengine/sbin/nginx -t
/opt/module/tengine/sbin/nginx
五、验证WAF防护
- sql注入验证
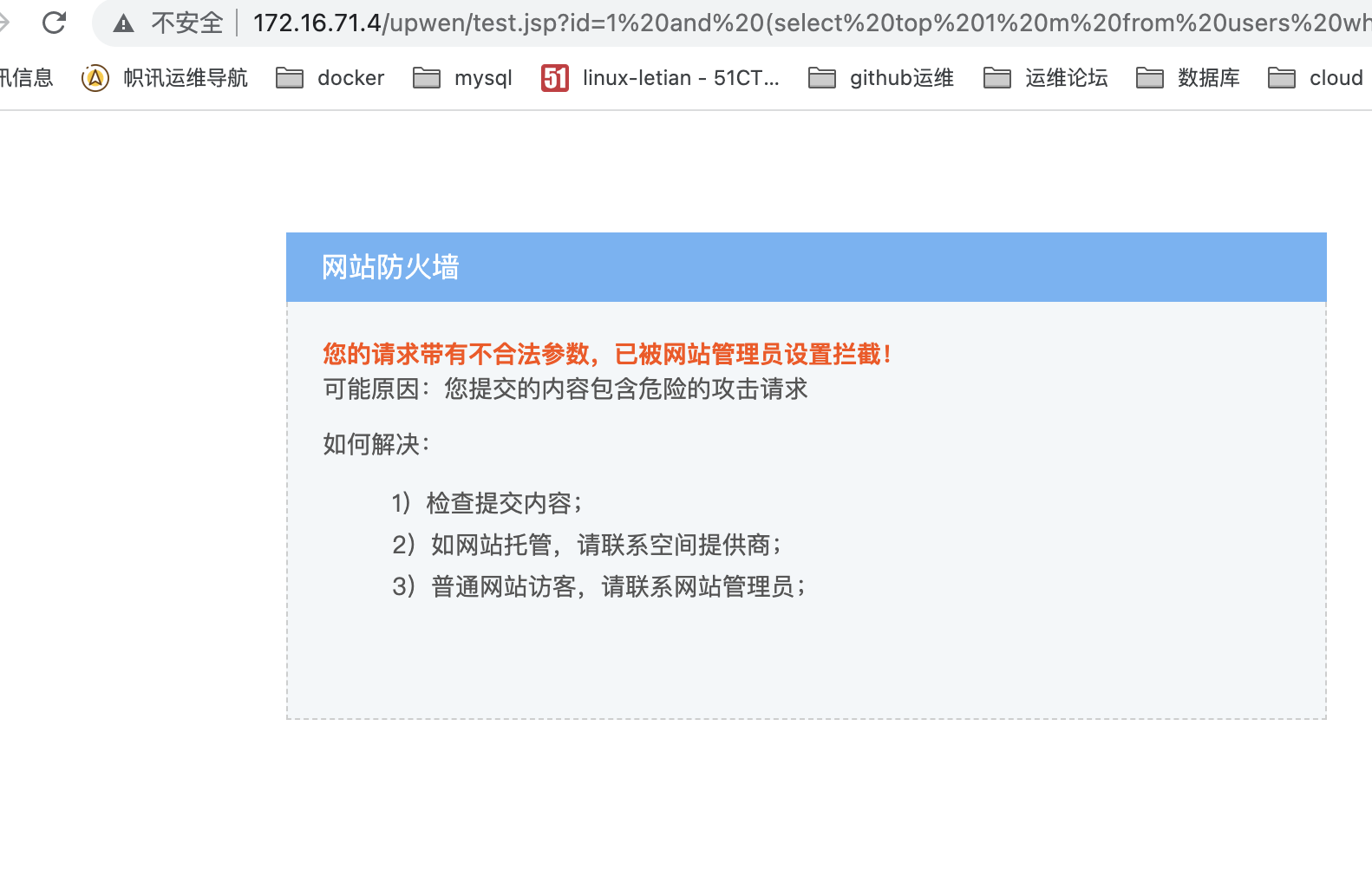
http://172.16.71.4/upwen/test.jsp?id=1 and (select top 1 m from users where d=1 and m not in(select top 0 m from users))>0
- 密码暴力破解
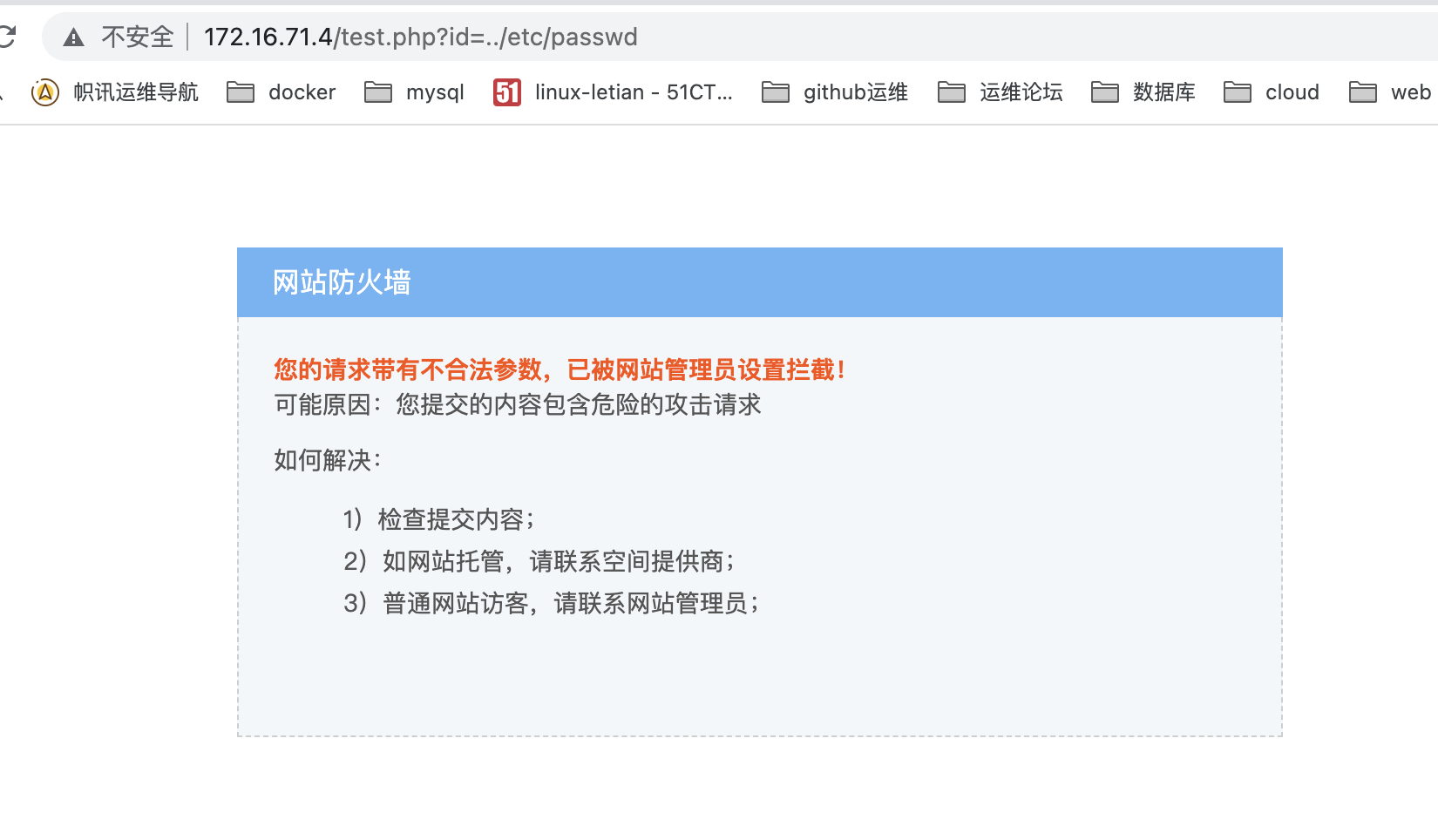
http://172.16.71.4/test.php?id=../etc/passwd





 浙公网安备 33010602011771号
浙公网安备 33010602011771号