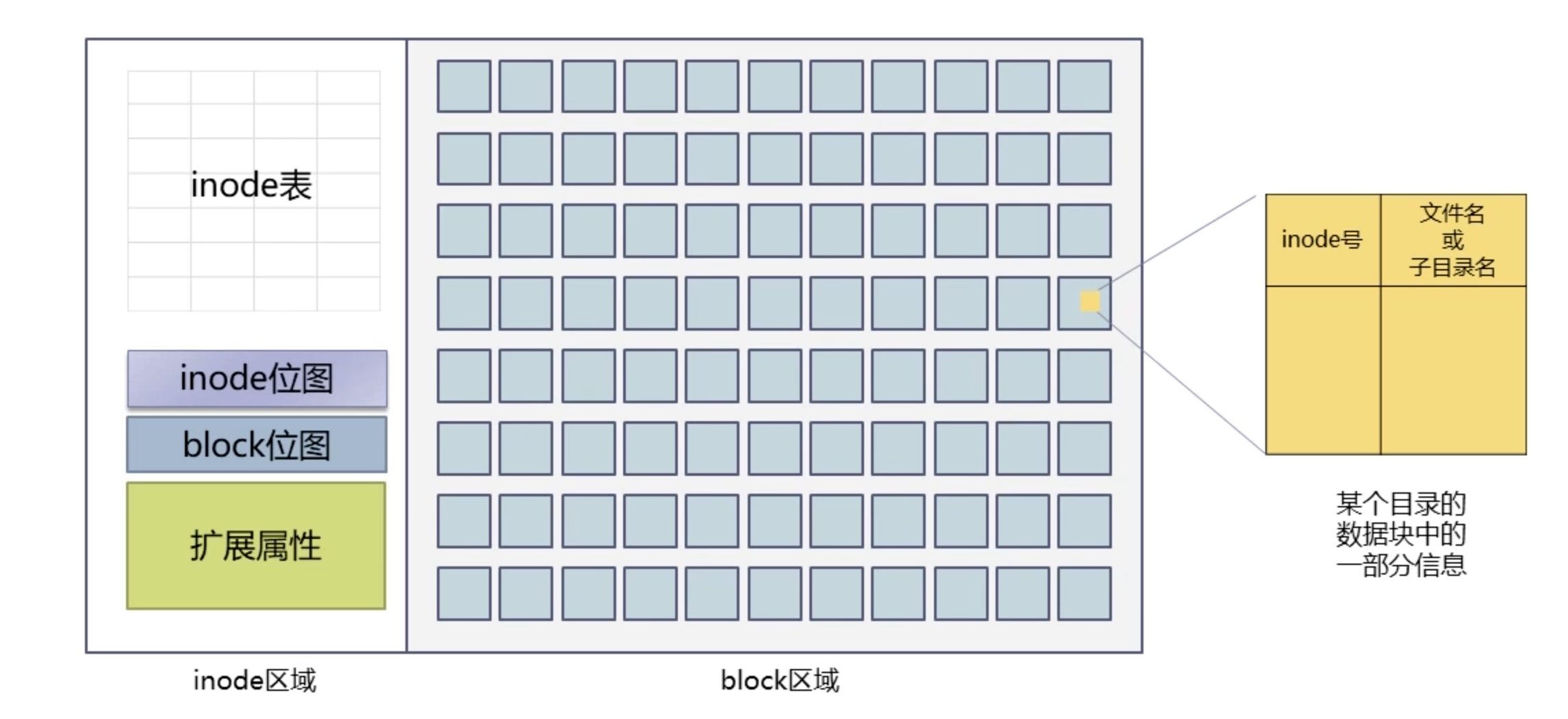
一、访问权限控制
-
U = User(文件主人) G = Group(同组用户) O = Others(剩下的所有人)
-
RWX —— 权限的“动作” R = Read(读/列目录) W = Write(写/删/改/建)
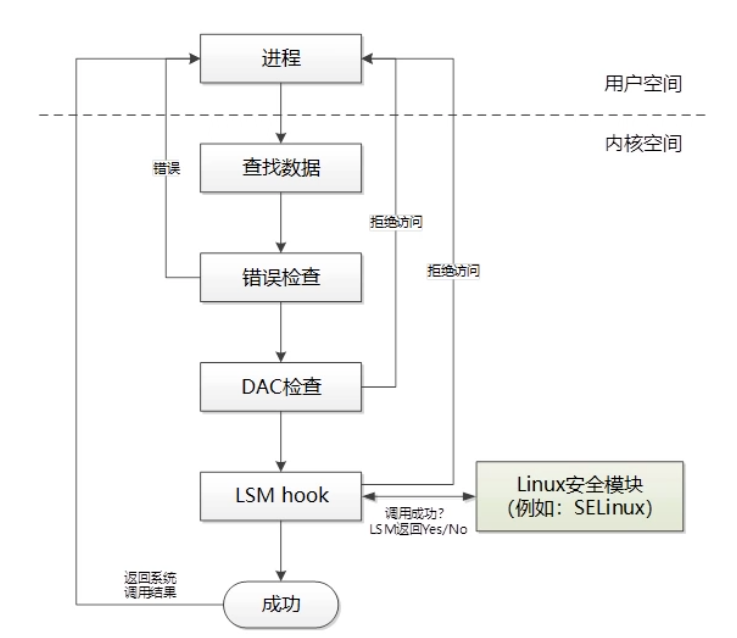
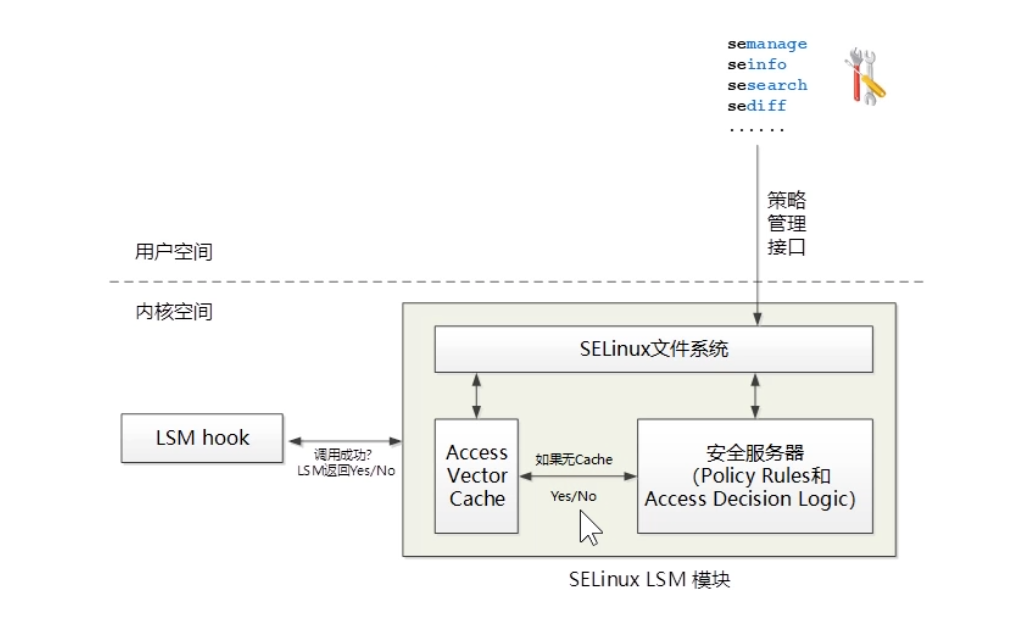
SELinux == Subject(进程) + Object(资源:文件,设备,套接字) + Action
三、SELinux的三种模式
1、查看当前模式
getenforce2、
vim /etc/selinux/config
修改SELINUX=permissive 为 SELINUX=disabled
setenforce 0
vim /etc/selinux/config
设置 SELINUX=permissive宽容模式下查看avc告警信息:
dmesg | grep avc4、
setenforce 1vim /etc/selinux/config
设置 SELINUX=enforcing
1、ubuntu中编译好的规则保存在目录/usr/share/selinux/default,目录中文件名后缀都显示为.bz2
xuanmiao@xuanmiao-SELinux:/usr/share/selinux/default$ pwd
/usr/share/selinux/default
xuanmiao@xuanmiao-SELinux:/usr/share/selinux/default$ ls
accountsd.pp.bz2 chromium.pp.bz2 fcoe.pp.bz2 kismet.pp.bz2 netlabel.pp.bz2 psad.pp.bz2
......2、
xuanmiao@xuanmiao-SELinux:/usr/share/selinux/default$ sesearch -A3、
xuanmiao@xuanmiao-SELinux:/usr/share/selinux/default$ sesearch -A -s crond_t
allow crond_t acct_exec_t:file { execute getattr ioctl map open read };
allow crond_t acct_t:process transition;
allow crond_t acngtool_exec_t:file { execute getattr ioctl map open read };
allow crond_t acngtool_t:process transition;
allow crond_t acpid_exec_t:file { execute getattr ioctl map open read };
allow crond_t acpid_t:process transition;
getsebool -a
sesearch -A -b httpd_enable_homedirs
xuanmiao@xuanmiao-SELinux:~$ sudo semanage boolean -l | grep httpd_enable_homedirs
httpd_enable_homedirs (关,关) Determine whether httpd can traverse user home directories.
xuanmiao@xuanmiao-SELinux:~$ ps -eZ | grep systemd
system_u:system_r:init_t:s0 1 ? 00:00:04 systemd
system_u:system_r:syslogd_t:s0 352 ? 00:00:02 systemd-journal
system_u:system_r:udev_t:s0-s0:c0.c1023 408 ? 00:00:02 systemd-udevd
system_u:system_r:initrc_t:s0 745 ? 00:00:25 systemd-oomd
system_u:system_r:systemd_resolved_t:s0 746 ? 00:00:00 systemd-resolve
system_u:system_r:ntpd_t:s0 747 ? 00:00:00 systemd-timesyn
system_u:system_r:systemd_logind_t:s0 804 ? 00:00:00 systemd-logind
sysadm_u:unconfined_r:unconfined_t:s0-s0:c0.c1023 1433 ? 00:00:02 systemd
xuanmiao@xuanmiao-SELinux:~$ ls -dZ /var/www/html
system_u:object_r:httpd_sys_content_t:s0 /var/www/html
xuanmiao@xuanmiao-SELinux:~$ id -Z
unconfined_u:unconfined_r:unconfined_t:s0-s0:c0.c1023
(1)查看SELinux策略定义的SELinux用户
xuanmiao@xuanmiao-SELinux:~$ sudo semanage user -l
Labeling MLS/ MLS/
SELinux User Prefix MCS Level MCS Range SELinux Roles
root sysadm s0 s0-s0:c0.c1023 staff_r sysadm_r system_r
staff_u staff s0 s0-s0:c0.c1023 staff_r sysadm_r
sysadm_u sysadm s0 s0-s0:c0.c1023 sysadm_r
system_u user s0 s0-s0:c0.c1023 system_r
unconfined_u unconfined s0 s0-s0:c0.c1023 system_r unconfined_r
user_u user s0 s0 user_r
xdm user s0 s0 xdm_r
xuanmiao@xuanmiao-SELinux:~$ sudo semanage login -l // 此命令等同于seinfo -u
登录名 SELinux 用户 MLS/MCS 范围 服务
__default__ user_u s0 *
root unconfined_u s0-s0:c0.c1023 *
sddm xdm s0-s0 *
xuanmiao sysadm_u s0-s0:c0.c1023 *
semanage user -a -R staff_r swift_u
xuanmiao@xuanmiao-SELinux:~$ ls -lZ
总计 48
drwxr-xr-x. 2 xuanmiao xuanmiao system_u:object_r:user_home_t:s0 4096 12月 30 10:17 公共的
drwxr-xr-x. 2 xuanmiao xuanmiao system_u:object_r:user_home_t:s0 4096 12月 30 10:17 模板
drwxr-xr-x. 2 xuanmiao xuanmiao system_u:object_r:user_home_t:s0 4096 12月 30 10:17 视频
drwxr-xr-x. 2 xuanmiao xuanmiao system_u:object_r:user_home_t:s0 4096 12月 30 10:17 图片
drwxr-xr-x. 2 xuanmiao xuanmiao system_u:object_r:user_home_t:s0 4096 12月 30 10:17 文档
drwxr-xr-x. 2 xuanmiao xuanmiao system_u:object_r:user_home_t:s0 4096 1月 19 13:48 下载
drwxr-xr-x. 2 xuanmiao xuanmiao system_u:object_r:user_home_t:s0 4096 12月 30 10:17 音乐
drwxr-xr-x. 2 xuanmiao xuanmiao system_u:object_r:user_home_t:s0 4096 12月 30 10:17 桌面
drwx------. 4 xuanmiao xuanmiao system_u:object_r:user_home_t:s0 4096 12月 29 18:13 snap
drwxrwxr-x. 2 xuanmiao xuanmiao system_u:object_r:user_home_t:s0 4096 12月 30 10:21 software
drwxrwxr-x. 2 xuanmiao xuanmiao sysadm_u:object_r:user_home_t:s0 4096 1月 19 18:05 Test
drwxr-xr-x. 9 xuanmiao xuanmiao system_u:object_r:user_home_t:s0 4096 12月 29 18:06 vmware-tools-distrib
xuanmiao@xuanmiao-SELinux:~$ cd Test
xuanmiao@xuanmiao-SELinux:~/Test$ ls
xuanmiao@xuanmiao-SELinux:~/Test$ touch test.txt
xuanmiao@xuanmiao-SELinux:~/Test$ ls -lZ
总计 0
-rw-rw-r--. 1 xuanmiao xuanmiao sysadm_u:object_r:user_home_t:s0 0 1月 19 18:06 test.txt
xuanmiao@xuanmiao-SELinux:~/Test$ chcon -t httpd_sys_content_t ./test.txt
xuanmiao@xuanmiao-SELinux:~/Test$ ls -lZ
总计 0
-rw-rw-r--. 1 xuanmiao xuanmiao sysadm_u:object_r:httpd_sys_content_t:s0 0 1月 19 18:06 test.txt
xuanmiao@xuanmiao-SELinux:~$ sudo semanage fcontext -l | grep -E "/var/www/html"
/var/www/html/[^/]*/cgi-bin(/.*)? all files system_u:object_r:httpd_sys_script_exec_t:s0
/var/www/html/[^/]*/sites/default/files(/.*)? all files system_u:object_r:httpd_sys_rw_content_t:s0
/var/www/html/[^/]*/sites/default/settings\.php regular file system_u:object_r:httpd_sys_rw_content_t:s0
/var/www/html/configuration\.php all files system_u:object_r:httpd_sys_rw_content_t:s0
/var/www/html/lightsquid(/.*)? all files system_u:object_r:httpd_lightsquid_content_t:s0
/var/www/html/lightsquid/report(/.*)? all files system_u:object_r:lightsquid_rw_content_t:s0
/var/www/html/munin(/.*)? all files system_u:object_r:httpd_munin_content_t:s0
/var/www/html/munin/cgi(/.*)? all files system_u:object_r:httpd_munin_script_exec_t:s0
/var/www/html/wp-content(/.*)? all files system_u:object_r:httpd_sys_rw_content_t:s0
xuanmiao@xuanmiao-SELinux:~/Test$ pwd
/home/xuanmiao/Test
xuanmiao@xuanmiao-SELinux:~/Test$ ls -lZ
总计 0
-rw-rw-r--. 1 xuanmiao xuanmiao sysadm_u:object_r:httpd_sys_content_t:s0 0 1月 19 18:06 test.txt
xuanmiao@xuanmiao-SELinux:~/Test$
xuanmiao@xuanmiao-SELinux:~/Test$ restorecon -Rv ./test.txt
Relabeled /home/xuanmiao/Test/test.txt from sysadm_u:object_r:httpd_sys_content_t:s0 to sysadm_u:object_r:user_home_t:s0
xuanmiao@xuanmiao-SELinux:~/Test$
xuanmiao@xuanmiao-SELinux:~/Test$
xuanmiao@xuanmiao-SELinux:~/Test$
xuanmiao@xuanmiao-SELinux:~/Test$ ls -lZ
总计 0
-rw-rw-r--. 1 xuanmiao xuanmiao sysadm_u:object_r:user_home_t:s0 0 1月 19 18:06 test.txt


 浙公网安备 33010602011771号
浙公网安备 33010602011771号