crypto 入门
crypto1
看提示发现密文形式很像flag,加上后面有一个倒序,发现密文倒过来就是flag

crypto2
打开是一段加密文本,先用浏览器的控制台试试,按住F12打开控制台,复制,enter,就有了
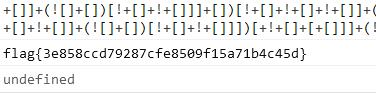
crypto3
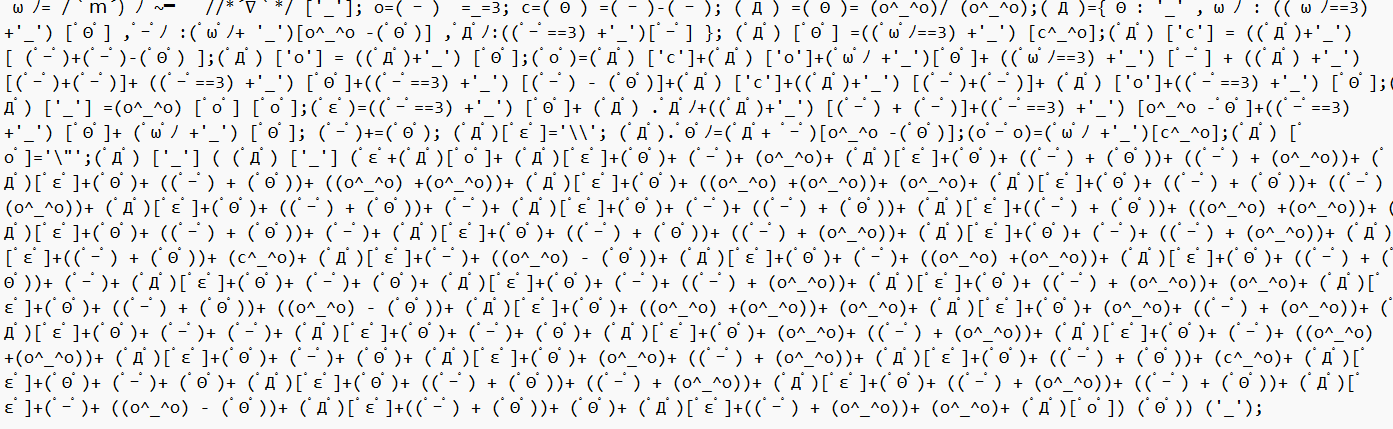
打开是一段颜文字,试试用AAencode解密,
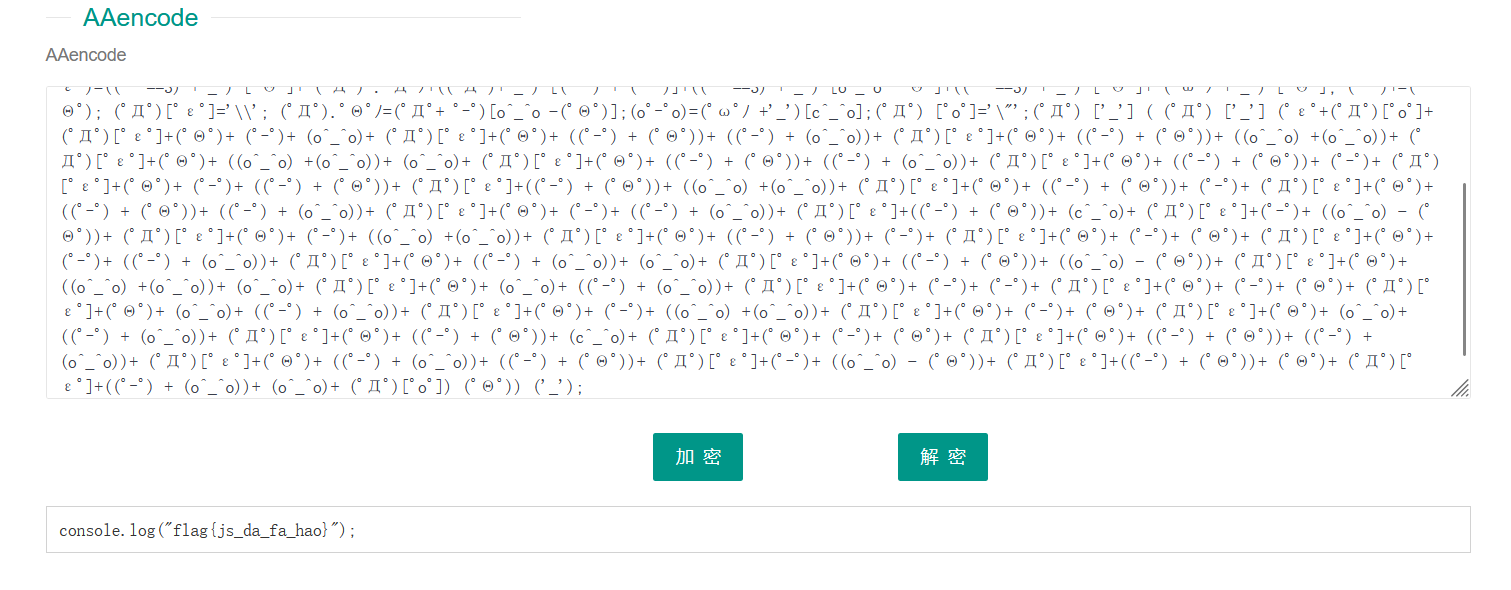
crypto4
题目要求我们计算d的值,根据RSA算法的原理进行计算,利用python脚本
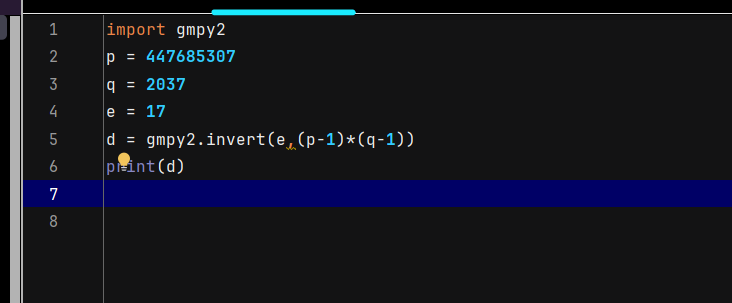
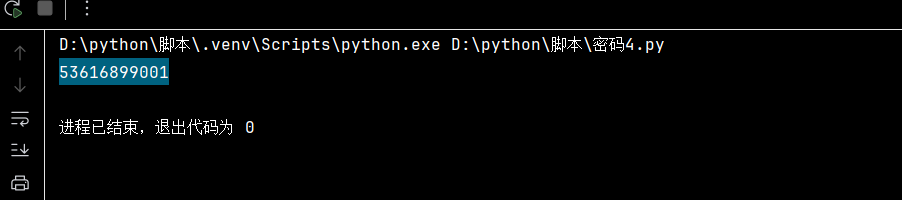
获得d的值
crypto5
同4
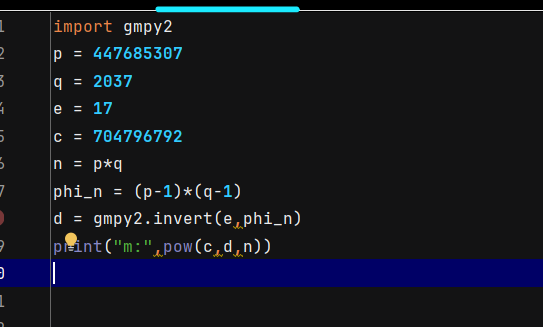
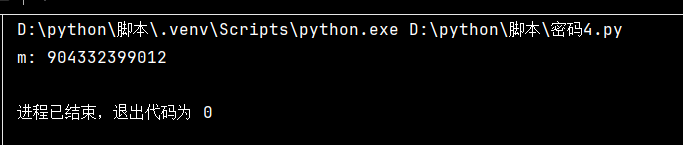
获得m的值
crypto6
打开文件,发现U2FsdGVkX1开头的可能是Rabbit,AES,DES,后面提示密钥和加密方式,应该是Rabbit加密
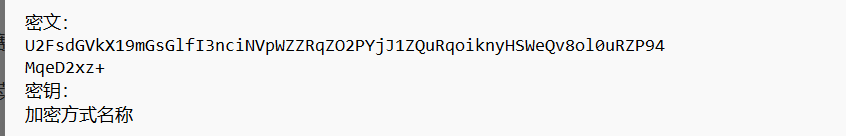
在线解密,获得flag
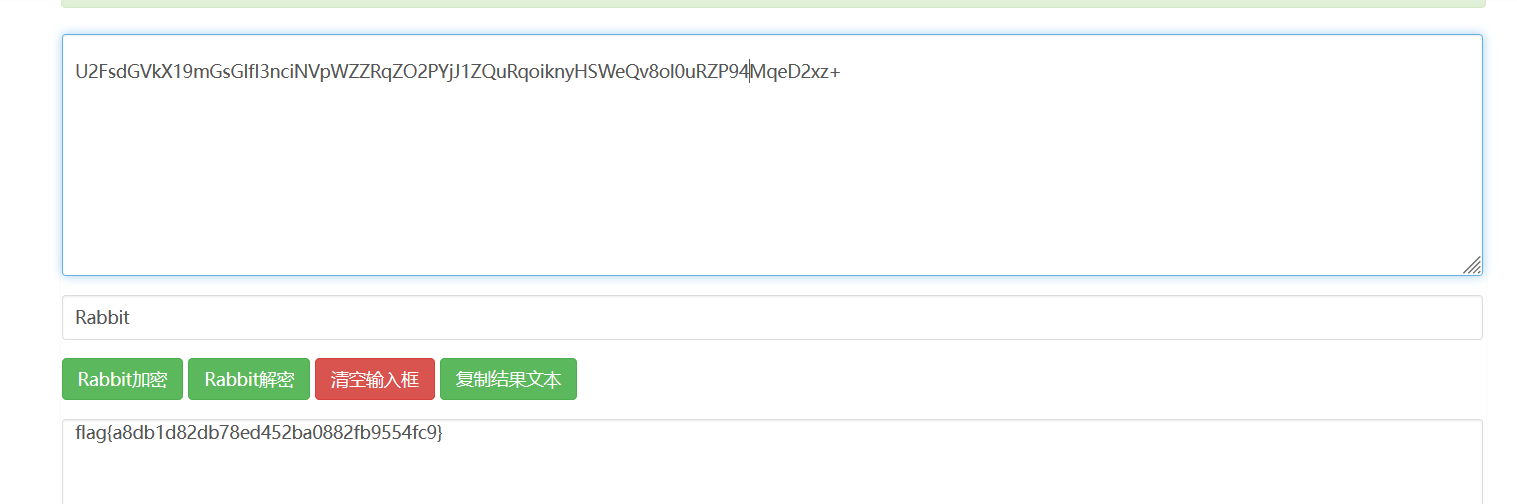
crypto7
打开文本发现,全是ook,ook编码即是BrainFuck编码,用在线解码https://www.splitbrain.org/services/ook
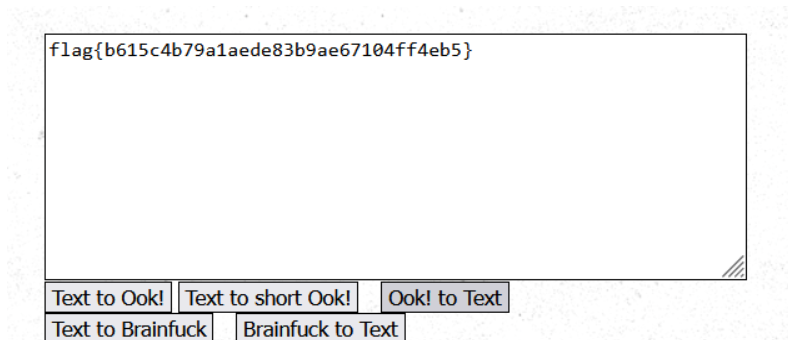
也是OK了
crypto8
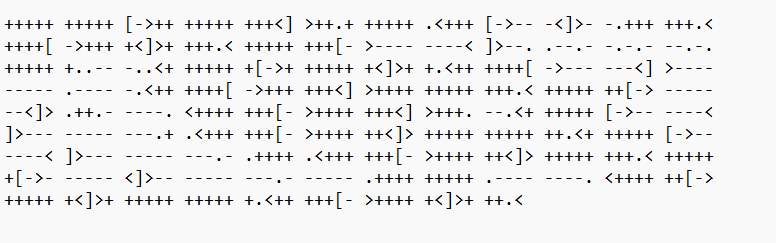

用这个https://www.nayuki.io/page/brainfuck-interpreter-javascript
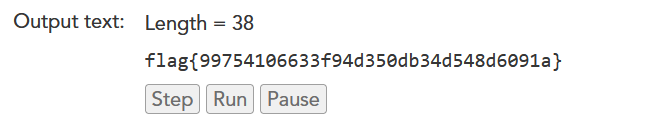
crypto9
解压需要密码,ARCHPR进行爆破

使用在线解码 :Serpent Encryption – Easily encrypt or decrypt strings or files
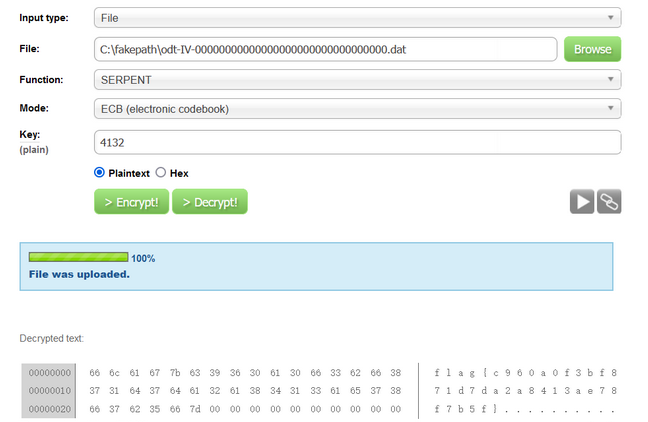
crypto10
提示是明文,打开是这个
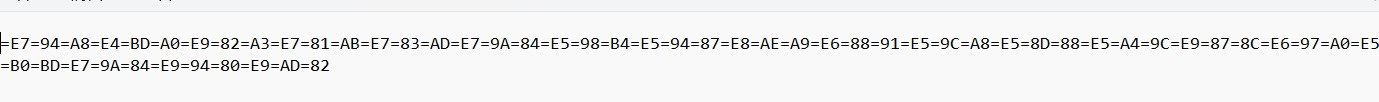
直接复制到浏览器看看啥玩意
crypto11
数了一下只有31位,使用md5解密
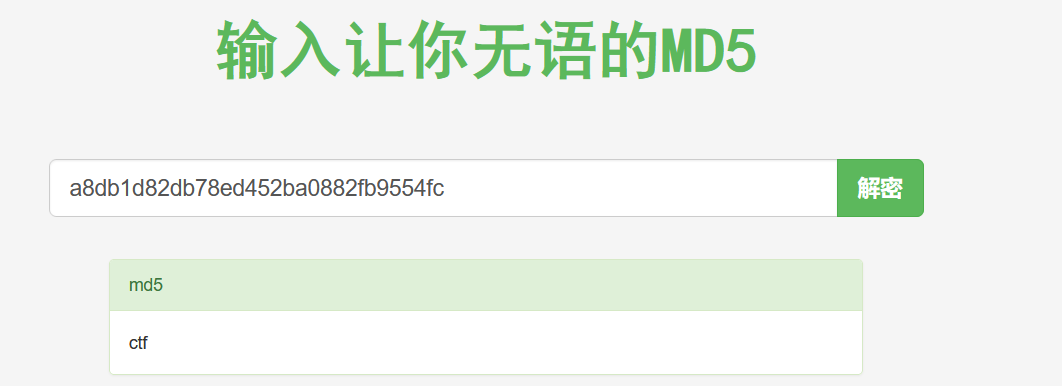
输入发现就是flag
crypto0
第一眼发现这个很像ctf的形式,这里可以联想到凯撒密码,字母发生了偏移,加上我们知道flag的形式,不难看出我们所有字母向前偏移一位就可以获得flag
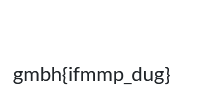
flag{hello_ctf}
crypto12
这一串和凯撒很像,但是发现不能获得flag,那有可能是埃特巴什码,
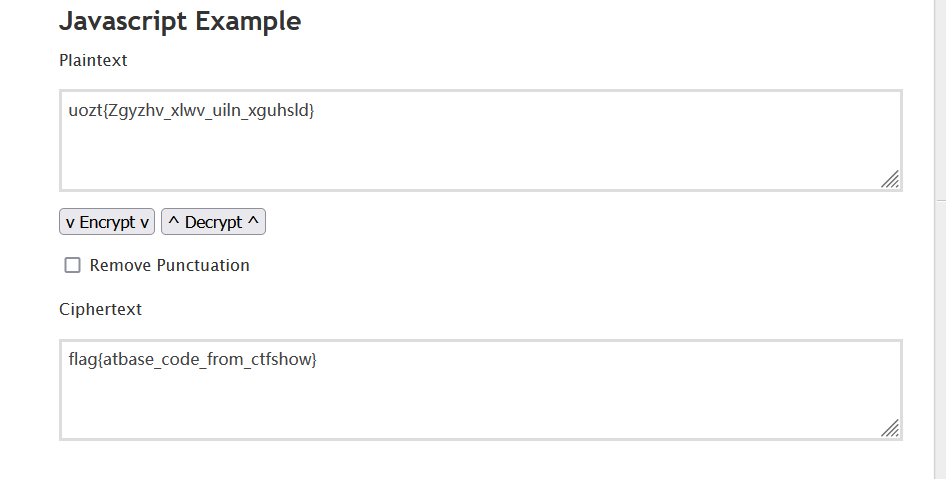
解码获得flag
flag{atbase_code_from_ctfshow}
发现不对,正确的为flag{Atbase_code_from_ctfshow}
crypto13
bace家族,因为我们不知道加密了几次,所以通过python进行暴力破解
import base64
filename = r"C:\Users\lenovo\Desktop\base家族\base家族\base.txt"
with open(filename) as f:
s = f.read()
while True:
try:
s = base64.b16decode(s)
continue
except:
pass
try:
s = base64.b32decode(s)
continue
except:
pass
try:
s = base64.b64decode(s)
continue
except:
pass
break
print(s)
得到结果
b'flag{b4Se_Fami1y_Is_FUn}'
crypto14
一看就是二进制,但是flag一般都尉字符数字型,应该是多层加密,不懂就看wp
二进制转换为十六进制,十六进制转化为字符串,发现base64无法解密,用脚本得base64正确编码
修改此处的 s
s = '3EP/3VNFFmNEAnlHD5dCMmVHD5ad9uG'
flag_exp = 'Zmxh' # flag{xxxx...} 开头的字符串的 base64 编码一定是 Zmxh 开头
import base64
base64_table = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/"
def base64_offset(text):
'''
计算 base64 表的偏移量
'''
global base64_table
return base64_table.index(text)
def main():
global base64_table
# 计算偏移量
diff = base64_offset(flag_exp[0]) - base64_offset(s[0])
index = []
for one in s:
index.append(base64_offset(one) + diff)
text = ''
for i in index:
text += base64_table[i]
if len(text)%4!=0:
text = text + "=" * (4-(len(text)%4))
print(f'base64 解码结果:{text}')
print(f'明文:{base64.b64decode(text).decode()}')
if name == 'main':
main()
用大佬脚本获得flag
flag{看我长不长?}
crypto15
全是文字,并带有重复,应该是当铺密码
当铺密码:就是一种将中文和数字进行转化的密码,算法相当简单:当前汉字有多少笔画出头,就是转化成数字几
数他有几个头,由田中 由田井 羊夫 由田人 由中人 羊羊 由由王 由田中 由由大 由田工 由由由 由由羊 由中大
102 108 97 103 99 116 102 115 104 111 119 125
换成16进制
66 6c 61 67 63 74 62 73 68 6f 77 7d
再用HEX解密
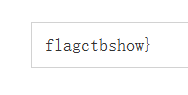
wp中运用脚本的方法更为简单(通解)
s ='田由中人工大王夫井羊'
code=input("请输入当铺密码:")
code = code.split(" ")
w = ''
for i in code:
k=""
for j in i:
k+=str(s.index(j))
w+=chr(int(k))
print(w,end='')
crypto16
贝斯密码,使用工具梭哈,发现不能得到flag,看特征应该是base62,分段解码,只能慢慢试是几段
发现是11位为一段flag,
查看wp能用脚本解决,
import string
import base62
from Crypto.Util.number import *
BASE62 = string.digits + string.ascii_uppercase + string.ascii_lowercase
def groupby(cipher, k):
group_cipher = [cipher[i:i + k] for i in range(0, len(cipher), k)] //分组
return group_cipher
if name == 'main':
cipher = "8nCDq36gzGn8hf4M2HJUsn4aYcYRBSJwj4aE0hbgpzHb4aHcH1zzC9C3IL"
for i in range(4, 21):
try:
cipherg = groupby(cipher, i)
flag = ""
for j in cipherg:
flag += long_to_bytes(base62.decode(j, alphabet=BASE62)).decode()
print(flag)
except Exception as e:
continue
flag
crypto17
审查元素
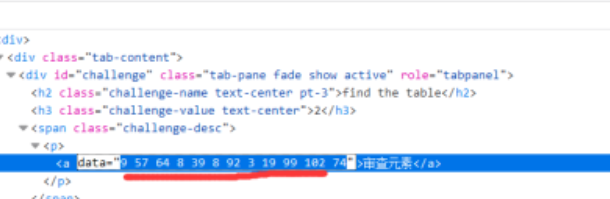
元素嘛,联想到化学元素周期表,进行查询,flag{doyoulikesnow}。
crypto18
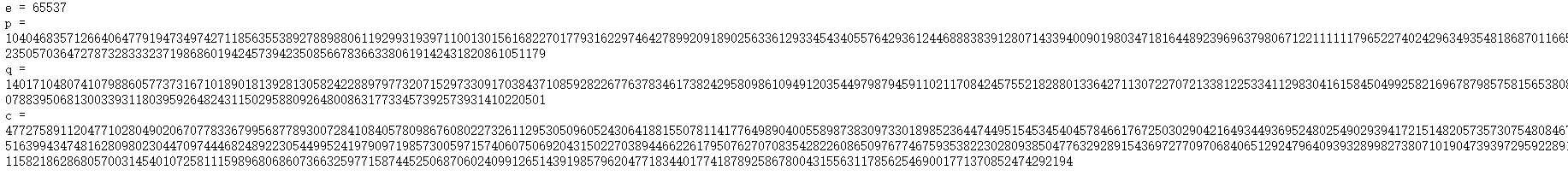
RSA非对称加密,直接上脚本
import libnum
from Crypto.Util.number import long_to_bytes,bytes_to_long
e = 65537
p = 104046835712664064779194734974271185635538927889880611929931939711001301561682270177931622974642789920918902563361293345434055764293612446888383912807143394009019803471816448923969637980671221111117965227402429634935481868701166522350570364727873283332371986860194245739423508566783663380619142431820861051179
q = 140171048074107988605773731671018901813928130582422889797732071529733091703843710859282267763783461738242958098610949120354497987945911021170842457552182880133642711307227072133812253341129830416158450499258216967879857581565380890788395068130033931180395926482431150295880926480086317733457392573931410220501
c = 4772758911204771028049020670778336799568778930072841084057809867608022732611295305096052430641881550781141776498904005589873830973301898523644744951545345404578466176725030290421649344936952480254902939417215148205735730754808467351639943474816280980230447097444682489223054499524197909719857300597157406075069204315022703894466226179507627070835428226086509767746759353822302809385047763292891543697277097068406512924796409393289982738071019047393972959228919115821862868057003145401072581115989680686073663259771587445250687060240991265143919857962047718344017741878925867800431556311785625469001771370852474292194
n=pq
phi=(p-1)(q-1)
d = libnum.invmod(e,phi)
m = pow(c, d, n)
flag=long_to_bytes(m)
print(m)
print(flag)#转字节
crypto19
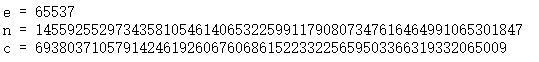
没有q和p.
在线分离n的值,然后用上一题的代码获得flag。
http://factordb.com/index.php
crypto20
给了两串数据
题目中e相同,n,c不同。对于rsa而言,同一个e同一个m,因此n之间可能是共享素数。求出n1与n2的最大公因数即为p,之后就可以得到q和d,从而求解m.
import gmpy2
import binascii
import RSAwienerHacker
e = 284100478693161642327695712452505468891794410301906465434604643365855064101922252698327584524956955373553355814138784402605517536436009073372339264422522610010012877243630454889127160056358637599704871937659443985644871453345576728414422489075791739731547285138648307770775155312545928721094602949588237119345
n = 468459887279781789188886188573017406548524570309663876064881031936564733341508945283407498306248145591559137207097347130203582813352382018491852922849186827279111555223982032271701972642438224730082216672110316142528108239708171781850491578433309964093293907697072741538649347894863899103340030347858867705231
c = 350429162418561525458539070186062788413426454598897326594935655762503536409897624028778814302849485850451243934994919418665502401195173255808119461832488053305530748068788500746791135053620550583421369214031040191188956888321397450005528879987036183922578645840167009612661903399312419253694928377398939392827
d = RSAwienerHacker.hack_RSA(e,n)
m = gmpy2.powmod(c,d,n)
print(d)
print(binascii.unhexlify(hex(m)[2:]))
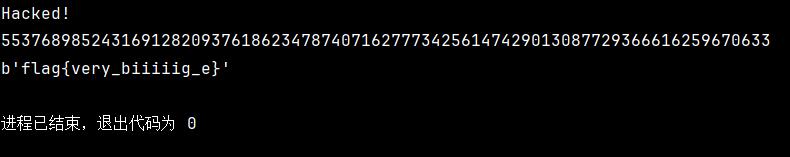
crypto21
crypto
crypto
crypto
crypto
crypto
crypto
crypto
crypto
crypto
crypto
crypto
crypto
crypto
crypto


 浙公网安备 33010602011771号
浙公网安备 33010602011771号