X-CTF(REVERSE高级) APK-逆向2
1.查壳。c#文件,无壳,提示使用relector编译

2.反编译。请求本地接口传数据
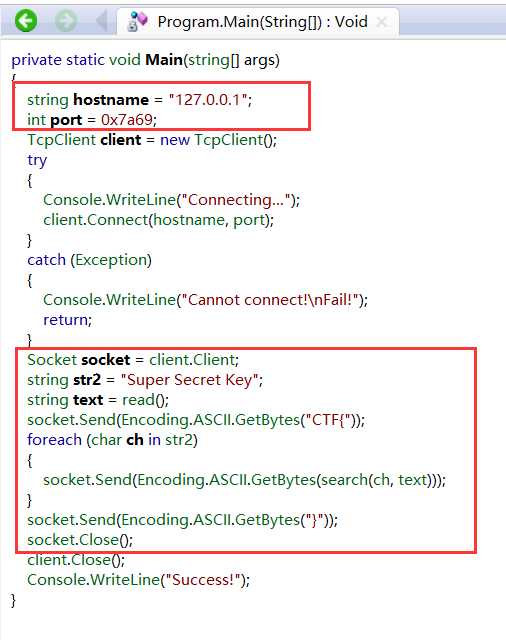
3.使用python代码搭建socket接口
import http.server
server_address = ('127.0.0.1', 31337)
handler_class = http.server.BaseHTTPRequestHandler
httpd = http.server.HTTPServer(server_address, handler_class)
httpd.serve_forever()
4.双击运行程序

得到flag
CTF{7eb67b0bb4427e0b43b40b6042670b55}
relector破解方法及工具:
https://www.52pojie.cn/thread-311707-1-1.html



 浙公网安备 33010602011771号
浙公网安备 33010602011771号