Kubernetes API 身份认证-静态令牌认证 & X509客户端认证【创建多个用户认证到API Server上】-2023.01.10-实验成功
静态令牌认证
静态令牌认证的基础配置
#令牌信息保存于文本文件中
文件格式为CSV,每行定义一个用户,由“令牌、用户名、用户ID和所属的用户组”四个字段组成,用户组为可选字段
格式: token,user,uid,"group1,group2,group3"
#由kube-apiserver在启动时通过--token-auth-file选项加载
#加载完成后的文件变动,仅能通过重启程序进行重载,因此,相关的令牌会长期有效
#客户端在HTTP请求中,通过“Authorization Bearer TOKEN”标头附带令牌令牌以完成认证
配置示例
#生成token,命令: echo "$(openssl rand -hex 3).$(openssl rand hex 8)"
#生成static token文件
#配置kube-apiserver加载该静态令牌文件以启用相应的认证功能
#测试,命令: curl -k -H "Authorization: Bearer TOKEN”-k https://API_SERVER:6443/api/v1/namespaces/default/pods一、生成token,命令: echo "$(openssl rand -hex 3).$(openssl rand hex 8)"
[root@k8s-master01 elk-operator]# echo "$(openssl rand -hex 3).$(openssl rand -hex 8)"
0e34c9.dca86eada7842eb6
[root@k8s-master01 elk-operator]# echo "$(openssl rand -hex 3).$(openssl rand -hex 8)"
5a0738.90a195692c668227二、生成static token文件
[root@k8s-master01 auth]#vim /etc/kubernetes/auth/token.csv
0e34c9.dca86eada7842eb6,ABC,1000,kubeuser
5a0738.90a195692c668227,CBA,1001,kubeadmin三、配置kube-apiserver加载该静态令牌文件以启用相应的认证功能
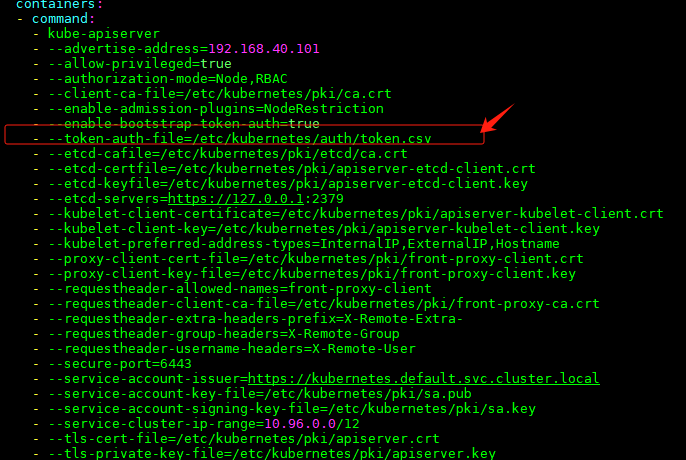
#一定要把kube-apiserver.yaml 移走 否则会有冲突应用不上 配置
[root@k8s-master01 manifests]# cp kube-apiserver.yaml /tmp/kube-apiserver.yaml
[root@k8s-master01 manifests]# vim kube-apiserver.yaml
- --token-auth-file=/etc/kubernetes/auth/token.csv
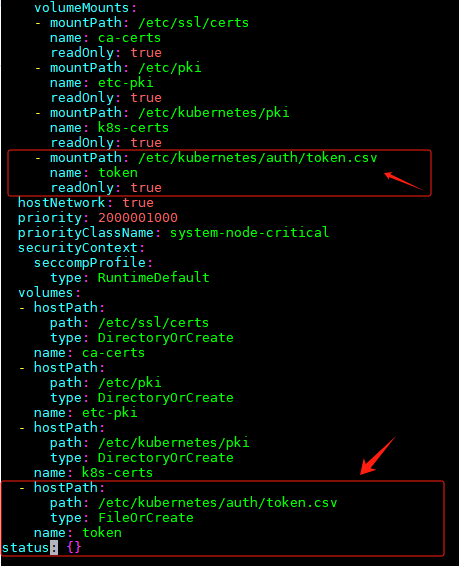
- mountPath: /etc/kubernetes/auth/token.csv
name: token
readOnly: true
- hostPath:
path: /etc/kubernetes/auth/token.csv
type: FileOrCreate
name: token![]()
四、测试,命令
#curl -k -H "Authorization: Bearer $TOKEN”-k https://API_SERVER:6443/api/v1/namespaces/default/pods
#0e34c9.dca86eada7842eb6,ABC,1000,kubeuser
#5a0738.90a195692c668227,CBA,1001,kubeadmin
# 认证成功并获取到了用户ABC。code=403是因为没有给该用户授权
[root@k8s-master01 manifests]# curl -H "Authorization: Bearer 0e34c9.dca86eada7842eb6" -k https://192.168.40.101:6443/api/v1/namespaces/default/pods
{
"kind": "Status",
"apiVersion": "v1",
"metadata": {},
"status": "Failure",
"message": "pods is forbidden: User \"ABC\" cannot list resource \"pods\" in API group \"\" in the namespace \"default\"",
"reason": "Forbidden",
"details": {
"kind": "pods"
},
"code": 403
}
[root@k8s-master01 auth]# curl -H "Authorization: Bearer 5a0738.90a195692c668227" -k https://192.168.40.101:6443/api/v1/namespaces/default/pods
{
"kind": "Status",
"apiVersion": "v1",
"metadata": {},
"status": "Failure",
"message": "pods is forbidden: User \"CBA\" cannot list resource \"pods\" in API group \"\" in the namespace \"default\"",
"reason": "Forbidden",
"details": {
"kind": "pods"
},
"code": 403
}X509客户端认证
1、使用CertificateSigningRequest签发
1.1 创建证书认证请求
[root@k8s-master01 ~]# mkdir x509cert
[root@k8s-master01 ~]# cd x509cert/
[root@k8s-master01 x509cert]# openssl genrsa -out winnie.key 2048
Generating RSA private key, 2048 bit long modulus
.................................................................+++
..................+++
e is 65537 (0x10001)
[root@k8s-master01 x509cert]# ll
total 4
-rw-r--r-- 1 root root 1679 Jan 9 16:12 winnie.key
[root@k8s-master01 x509cert]# openssl req -new -key winnie.key -out winnie.csr -subj "/CN=winnie/O=developers"
[root@k8s-master01 x509cert]# ll
total 8
-rw-r--r-- 1 root root 915 Jan 9 16:12 winnie.csr
-rw-r--r-- 1 root root 1679 Jan 9 16:12 winnie.key1.2 创建CertificateSigningRequest资源
#request 替换为 自己csr base64数据
vim certificatesignrequest-winnie.yaml
apiVersion: certificates.k8s.io/v1
kind: CertificateSigningRequest
metadata:
name: winnie
spec:
request: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURSBSRVFVRVNULS0tLS0KTUlJQ2F6Q0NBVk1DQVFBd0pqRVBNQTBHQTFVRUF3d0dkMmx1Ym1sbE1STXdFUVlEVlFRS0RBcGtaWFpsYkc5dwpaWEp6TUlJQklqQU5CZ2txaGtpRzl3MEJBUUVGQUFPQ0FROEFNSUlCQ2dLQ0FRRUFxNGk2Q3JDU1A3VzRwYVpOCjNSRlcySnJSWFlRZEhrQkZ1V2krV0tVb250c1VlaSsrR05BR3Nhcm9rRFF5alpKYXByeUpwTjd6dERzVUxBRDUKbzVGQ24vVWxSVmxGM3hUTzVFQ1FTM243WUw3U3BSNHNnZ2tFdCtMQnB2bzdZVlQrVVk0L1FkRnJ4WmtpZHJmdwpXRlhsSllIampZSEhzaTVWY2V0bERaTkpoVmkreUxCTHRJWktPdTI5d1llRjhEU3R1M0Y2djFib2o4RFdvZWM0CmNVVU9UeWdCM05qbDY2a3ovamxxNXhoK1l6a3BhSkhTVFlqbkdjbnF4TFJHZngxQWJ2TTVyc3FZaFpZZkY2WkoKdkI2RVJKelhXeVZZekZDOTNoMGFXZUZ2VEtwMkF3OFovRHRZTHROTkZXVXE0am1URmd3UGxwQkdNOVFwaDZiTApkS3pjZFFJREFRQUJvQUF3RFFZSktvWklodmNOQVFFTEJRQURnZ0VCQUdCMWRsb2JDK2diSHRxYUE1TE03Sm1SCjVBV0s0eFBySmNKNHZDbVhkclJHeTN6MFBEMDgwZWZ5Rk9ZMzVqVVkwYVY1U21HZ0xSMFZNNkJtU29EWVovdTQKRzd3Z1htQU1aQkRydS9uZ3NlRElad0syMlhjN0pMd25HR21MdGpGRzZyNDRoYUZGZmFlMy9WRjRKR2RQR2gxNgpSalJhZmhjS0IvMUVFMU5vc3d4TDJDV1QzTkRvcWVkOGtXRHlHQ2Z3bjNNTmdEYTlWTEFKSTY0eUFqcmF0bUs5CnE2cmkyTk01NXcvWWNuNG1mQTZSRjgzeFFjQk15ZDNtbmdDYnIrMzI2VkZ4UmU4L3JYcTN6SnNMeERFUU8zd1YKa29aY0lWUlVFUnJ6YU9nYnJ6eU56Y2x0RXowbXNDbUg3TFJFc0J5dDRzVDkxZ1FBOXpxeS9EN3dzOFI4Rno0PQotLS0tLUVORCBDRVJUSUZJQ0FURSBSRVFVRVNULS0tLS0K
signerName: kubernetes.io/kube-apiserver-client
expirationSeconds: 864000 # ten days
usages:
- client auth
[root@k8s-master01 x509cert]# cat winnie.csr | base64 | tr -d '\n'
LS0tLS1CRUdJTiBDRVJUSUZJQ0FURSBSRVFVRVNULS0tLS0KTUlJQ2F6Q0NBVk1DQVFBd0pqRVBNQTBHQTFVRUF3d0dkMmx1Ym1sbE1STXdFUVlEVlFRS0RBcGtaWFpsYkc5dwpaWEp6TUlJQklqQU5CZ2txaGtpRzl3MEJBUUVGQUFPQ0FROEFNSUlCQ2dLQ0FRRUFxNGk2Q3JDU1A3VzRwYVpOCjNSRlcySnJSWFlRZEhrQkZ1V2krV0tVb250c1VlaSsrR05BR3Nhcm9rRFF5alpKYXByeUpwTjd6dERzVUxBRDUKbzVGQ24vVWxSVmxGM3hUTzVFQ1FTM243WUw3U3BSNHNnZ2tFdCtMQnB2bzdZVlQrVVk0L1FkRnJ4WmtpZHJmdwpXRlhsSllIampZSEhzaTVWY2V0bERaTkpoVmkreUxCTHRJWktPdTI5d1llRjhEU3R1M0Y2djFib2o4RFdvZWM0CmNVVU9UeWdCM05qbDY2a3ovamxxNXhoK1l6a3BhSkhTVFlqbkdjbnF4TFJHZngxQWJ2TTVyc3FZaFpZZkY2WkoKdkI2RVJKelhXeVZZekZDOTNoMGFXZUZ2VEtwMkF3OFovRHRZTHROTkZXVXE0am1URmd3UGxwQkdNOVFwaDZiTApkS3pjZFFJREFRQUJvQUF3RFFZSktvWklodmNOQVFFTEJRQURnZ0VCQUdCMWRsb2JDK2diSHRxYUE1TE03Sm1SCjVBV0s0eFBySmNKNHZDbVhkclJHeTN6MFBEMDgwZWZ5Rk9ZMzVqVVkwYVY1U21HZ0xSMFZNNkJtU29EWVovdTQKRzd3Z1htQU1aQkRydS9uZ3NlRElad0syMlhjN0pMd25HR21MdGpGRzZyNDRoYUZGZmFlMy9WRjRKR2RQR2gxNgpSalJhZmhjS0IvMUVFMU5vc3d4TDJDV1QzTkRvcWVkOGtXRHlHQ2Z3bjNNTmdEYTlWTEFKSTY0eUFqcmF0bUs5CnE2cmkyTk01NXcvWWNuNG1mQTZSRjgzeFFjQk15ZDNtbmdDYnIrMzI2VkZ4UmU4L3JYcTN6SnNMeERFUU8zd1YKa29aY0lWUlVFUnJ6YU9nYnJ6eU56Y2x0RXowbXNDbUg3TFJFc0J5dDRzVDkxZ1FBOXpxeS9EN3dzOFI4Rno0PQotLS0tLUVORCBDRVJUSUZJQ0FURSBSRVFVRVNULS0tLS0K[
[root@k8s-master01 x509cert]# kubectl apply -f certificatesignrequest-winnie.yaml
certificatesigningrequest.certificates.k8s.io/winnie created
#此时没有同意 所以是Pending
[root@k8s-master01 x509cert]# kubectl get csr
NAME AGE SIGNERNAME REQUESTOR REQUESTEDDURATION CONDITION
winnie 12s kubernetes.io/kube-apiserver-client kubernetes-admin 10d Pending
[root@k8s-master01 x509cert]# kubectl certificate approve winnie
certificatesigningrequest.certificates.k8s.io/winnie approved
[root@k8s-master01 x509cert]# kubectl get csr
NAME AGE SIGNERNAME REQUESTOR REQUESTEDDURATION CONDITION
winnie 44s kubernetes.io/kube-apiserver-client kubernetes-admin 10d Approved,Issued1.3 获取签发的证书,测试
#certificate 字段
[root@k8s-master01 x509cert]# kubectl get csr winnie -o yaml
apiVersion: certificates.k8s.io/v1
kind: CertificateSigningRequest
metadata:
annotations:
kubectl.kubernetes.io/last-applied-configuration: |
{"apiVersion":"certificates.k8s.io/v1","kind":"CertificateSigningRequest","metadata":{"annotations":{},"name":"winnie"},"spec":{"expirationSeconds":864000,"request":"LS0tLS1CRUdJTiBDRVJUSUZJQ0FURSBSRVFVRVNULS0tLS0KTUlJQ2F6Q0NBVk1DQVFBd0pqRVBNQTBHQTFVRUF3d0dkMmx1Ym1sbE1STXdFUVlEVlFRS0RBcGtaWFpsYkc5dwpaWEp6TUlJQklqQU5CZ2txaGtpRzl3MEJBUUVGQUFPQ0FROEFNSUlCQ2dLQ0FRRUFxNGk2Q3JDU1A3VzRwYVpOCjNSRlcySnJSWFlRZEhrQkZ1V2krV0tVb250c1VlaSsrR05BR3Nhcm9rRFF5alpKYXByeUpwTjd6dERzVUxBRDUKbzVGQ24vVWxSVmxGM3hUTzVFQ1FTM243WUw3U3BSNHNnZ2tFdCtMQnB2bzdZVlQrVVk0L1FkRnJ4WmtpZHJmdwpXRlhsSllIampZSEhzaTVWY2V0bERaTkpoVmkreUxCTHRJWktPdTI5d1llRjhEU3R1M0Y2djFib2o4RFdvZWM0CmNVVU9UeWdCM05qbDY2a3ovamxxNXhoK1l6a3BhSkhTVFlqbkdjbnF4TFJHZngxQWJ2TTVyc3FZaFpZZkY2WkoKdkI2RVJKelhXeVZZekZDOTNoMGFXZUZ2VEtwMkF3OFovRHRZTHROTkZXVXE0am1URmd3UGxwQkdNOVFwaDZiTApkS3pjZFFJREFRQUJvQUF3RFFZSktvWklodmNOQVFFTEJRQURnZ0VCQUdCMWRsb2JDK2diSHRxYUE1TE03Sm1SCjVBV0s0eFBySmNKNHZDbVhkclJHeTN6MFBEMDgwZWZ5Rk9ZMzVqVVkwYVY1U21HZ0xSMFZNNkJtU29EWVovdTQKRzd3Z1htQU1aQkRydS9uZ3NlRElad0syMlhjN0pMd25HR21MdGpGRzZyNDRoYUZGZmFlMy9WRjRKR2RQR2gxNgpSalJhZmhjS0IvMUVFMU5vc3d4TDJDV1QzTkRvcWVkOGtXRHlHQ2Z3bjNNTmdEYTlWTEFKSTY0eUFqcmF0bUs5CnE2cmkyTk01NXcvWWNuNG1mQTZSRjgzeFFjQk15ZDNtbmdDYnIrMzI2VkZ4UmU4L3JYcTN6SnNMeERFUU8zd1YKa29aY0lWUlVFUnJ6YU9nYnJ6eU56Y2x0RXowbXNDbUg3TFJFc0J5dDRzVDkxZ1FBOXpxeS9EN3dzOFI4Rno0PQotLS0tLUVORCBDRVJUSUZJQ0FURSBSRVFVRVNULS0tLS0K","signerName":"kubernetes.io/kube-apiserver-client","usages":["client auth"]}}
creationTimestamp: "2024-01-09T08:21:17Z"
name: winnie
resourceVersion: "537100"
uid: cf8cd2e9-7894-4404-9bfe-4b8c764bd5b3
spec:
expirationSeconds: 864000
groups:
- system:masters
- system:authenticated
request: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURSBSRVFVRVNULS0tLS0KTUlJQ2F6Q0NBVk1DQVFBd0pqRVBNQTBHQTFVRUF3d0dkMmx1Ym1sbE1STXdFUVlEVlFRS0RBcGtaWFpsYkc5dwpaWEp6TUlJQklqQU5CZ2txaGtpRzl3MEJBUUVGQUFPQ0FROEFNSUlCQ2dLQ0FRRUFxNGk2Q3JDU1A3VzRwYVpOCjNSRlcySnJSWFlRZEhrQkZ1V2krV0tVb250c1VlaSsrR05BR3Nhcm9rRFF5alpKYXByeUpwTjd6dERzVUxBRDUKbzVGQ24vVWxSVmxGM3hUTzVFQ1FTM243WUw3U3BSNHNnZ2tFdCtMQnB2bzdZVlQrVVk0L1FkRnJ4WmtpZHJmdwpXRlhsSllIampZSEhzaTVWY2V0bERaTkpoVmkreUxCTHRJWktPdTI5d1llRjhEU3R1M0Y2djFib2o4RFdvZWM0CmNVVU9UeWdCM05qbDY2a3ovamxxNXhoK1l6a3BhSkhTVFlqbkdjbnF4TFJHZngxQWJ2TTVyc3FZaFpZZkY2WkoKdkI2RVJKelhXeVZZekZDOTNoMGFXZUZ2VEtwMkF3OFovRHRZTHROTkZXVXE0am1URmd3UGxwQkdNOVFwaDZiTApkS3pjZFFJREFRQUJvQUF3RFFZSktvWklodmNOQVFFTEJRQURnZ0VCQUdCMWRsb2JDK2diSHRxYUE1TE03Sm1SCjVBV0s0eFBySmNKNHZDbVhkclJHeTN6MFBEMDgwZWZ5Rk9ZMzVqVVkwYVY1U21HZ0xSMFZNNkJtU29EWVovdTQKRzd3Z1htQU1aQkRydS9uZ3NlRElad0syMlhjN0pMd25HR21MdGpGRzZyNDRoYUZGZmFlMy9WRjRKR2RQR2gxNgpSalJhZmhjS0IvMUVFMU5vc3d4TDJDV1QzTkRvcWVkOGtXRHlHQ2Z3bjNNTmdEYTlWTEFKSTY0eUFqcmF0bUs5CnE2cmkyTk01NXcvWWNuNG1mQTZSRjgzeFFjQk15ZDNtbmdDYnIrMzI2VkZ4UmU4L3JYcTN6SnNMeERFUU8zd1YKa29aY0lWUlVFUnJ6YU9nYnJ6eU56Y2x0RXowbXNDbUg3TFJFc0J5dDRzVDkxZ1FBOXpxeS9EN3dzOFI4Rno0PQotLS0tLUVORCBDRVJUSUZJQ0FURSBSRVFVRVNULS0tLS0K
signerName: kubernetes.io/kube-apiserver-client
usages:
- client auth
username: kubernetes-admin
status:
certificate: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSURERENDQWZTZ0F3SUJBZ0lSQVA4dXhQeXVWUWFCN2dVY1BYNUlKMEV3RFFZSktvWklodmNOQVFFTEJRQXcKRlRFVE1CRUdBMVVFQXhNS2EzVmlaWEp1WlhSbGN6QWVGdzB5TkRBeE1Ea3dPREUyTlRaYUZ3MHlOREF4TVRrdwpPREUyTlRaYU1DWXhFekFSQmdOVkJBb1RDbVJsZG1Wc2IzQmxjbk14RHpBTkJnTlZCQU1UQm5kcGJtNXBaVENDCkFTSXdEUVlKS29aSWh2Y05BUUVCQlFBRGdnRVBBRENDQVFvQ2dnRUJBS3VJdWdxd2tqKzF1S1dtVGQwUlZ0aWEKMFYyRUhSNUFSYmxvdmxpbEtKN2JGSG92dmhqUUJyR3E2SkEwTW8yU1dxYThpYVRlODdRN0ZDd0ErYU9SUXAvMQpKVVZaUmQ4VXp1UkFrRXQ1KzJDKzBxVWVMSUlKQkxmaXdhYjZPMkZVL2xHT1AwSFJhOFdaSW5hMzhGaFY1U1dCCjQ0MkJ4N0l1VlhIclpRMlRTWVZZdnNpd1M3U0dTanJ0dmNHSGhmQTByYnR4ZXI5VzZJL0ExcUhuT0hGRkRrOG8KQWR6WTVldXBNLzQ1YXVjWWZtTTVLV2lSMGsySTV4bko2c1MwUm44ZFFHN3pPYTdLbUlXV0h4ZW1TYndlaEVTYwoxMXNsV014UXZkNGRHbG5oYjB5cWRnTVBHZnc3V0M3VFRSVmxLdUk1a3hZTUQ1YVFSalBVS1llbXkzU3MzSFVDCkF3RUFBYU5HTUVRd0V3WURWUjBsQkF3d0NnWUlLd1lCQlFVSEF3SXdEQVlEVlIwVEFRSC9CQUl3QURBZkJnTlYKSFNNRUdEQVdnQlNUeW04TUdJVWJOQmxtMlhYYWRRdmc0bzh0V0RBTkJna3Foa2lHOXcwQkFRc0ZBQU9DQVFFQQpkV01aMnJ5eStoUzVBYk00UFEzaElrTDA1U3kwMzRidHFLNTkva1lVVWVoWk1Rd2gxQUF5TW5BN1pBS0ZVYnA4CnBGSW12VWthMFZTMUFTSFdtbUdqYmgxYmRpRCtQVUlPa0NwLzVzUjlZWHVUbzFZWWs5Z1hxSTg4dDN6SkoxSUgKQm1wR0x1bzFsc2RVaExrTjQ0R0x0OEpkWXR6NldwVlVNMGY4ZDRkaXM4UmY4djYvZEMrM0VTS3FLK080clBPegp1Zk5pRUd5K2xpS3FsZW9Nb2lTUWhDOEgrbk5tZ1BzUUljSHkvNHRRWGEyVGlZcWdKSFJqNC9YeWk0OVpsOFA3ClhOWUNUNitnTG1nV0UyMjA3djlqa0FnbzdhdW9HTHIvUkZPNmEzU0pBQmpoN2tLWUxCYzRNdjJwbHpjR2p3dWIKVjFuSFdRTzA5ZWp6eWU1bm1XOG1Edz09Ci0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K
conditions:
- lastTransitionTime: "2024-01-09T08:21:56Z"
lastUpdateTime: "2024-01-09T08:21:56Z"
message: This CSR was approved by kubectl certificate approve.
reason: KubectlApprove
status: "True"
type: Approved
# 直接获取 certificate 字段
[root@k8s-master01 x509cert]# kubectl get csr winnie -o jsonpath={.status.certificate} | base64 -d
-----BEGIN CERTIFICATE-----
MIIDDDCCAfSgAwIBAgIRAP8uxPyuVQaB7gUcPX5IJ0EwDQYJKoZIhvcNAQELBQAw
FTETMBEGA1UEAxMKa3ViZXJuZXRlczAeFw0yNDAxMDkwODE2NTZaFw0yNDAxMTkw
ODE2NTZaMCYxEzARBgNVBAoTCmRldmVsb3BlcnMxDzANBgNVBAMTBndpbm5pZTCC
ASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEBAKuIugqwkj+1uKWmTd0RVtia
0V2EHR5ARblovlilKJ7bFHovvhjQBrGq6JA0Mo2SWqa8iaTe87Q7FCwA+aORQp/1
JUVZRd8UzuRAkEt5+2C+0qUeLIIJBLfiwab6O2FU/lGOP0HRa8WZIna38FhV5SWB
442Bx7IuVXHrZQ2TSYVYvsiwS7SGSjrtvcGHhfA0rbtxer9W6I/A1qHnOHFFDk8o
AdzY5eupM/45aucYfmM5KWiR0k2I5xnJ6sS0Rn8dQG7zOa7KmIWWHxemSbwehESc
11slWMxQvd4dGlnhb0yqdgMPGfw7WC7TTRVlKuI5kxYMD5aQRjPUKYemy3Ss3HUC
AwEAAaNGMEQwEwYDVR0lBAwwCgYIKwYBBQUHAwIwDAYDVR0TAQH/BAIwADAfBgNV
HSMEGDAWgBSTym8MGIUbNBlm2XXadQvg4o8tWDANBgkqhkiG9w0BAQsFAAOCAQEA
dWMZ2ryy+hS5AbM4PQ3hIkL05Sy034btqK59/kYUUehZMQwh1AAyMnA7ZAKFUbp8
pFImvUka0VS1ASHWmmGjbh1bdiD+PUIOkCp/5sR9YXuTo1YYk9gXqI88t3zJJ1IH
BmpGLuo1lsdUhLkN44GLt8JdYtz6WpVUM0f8d4dis8Rf8v6/dC+3ESKqK+O4rPOz
ufNiEGy+liKqleoMoiSQhC8H+nNmgPsQIcHy/4tQXa2TiYqgJHRj4/Xyi49Zl8P7
XNYCT6+gLmgWE2207v9jkAgo7auoGLr/RFO6a3SJABjh7kKYLBc4Mv2plzcGjwub
V1nHWQO09ejzye5nmW8mDw==
-----END CERTIFICATE-----
[root@k8s-master01 x509cert]# kubectl get csr winnie -o jsonpath={.status.certificate} | base64 -d > winnie.crt
[root@k8s-master01 x509cert]# ll
total 16
-rw-r--r-- 1 root root 1446 Jan 9 16:21 certificatesignrequest-winnie.yaml
-rw-r--r-- 1 root root 1119 Jan 9 16:27 winnie.crt
-rw-r--r-- 1 root root 915 Jan 9 16:12 winnie.csr
-rw-r--r-- 1 root root 1679 Jan 9 16:12 winnie.key
[root@k8s-master01 x509cert]# curl -k -E ./winnie.crt --key ./winnie.key https://192.168.40.101:6443
{
"kind": "Status",
"apiVersion": "v1",
"metadata": {},
"status": "Failure",
"message": "forbidden: User \"winnie\" cannot get path \"/\"",
"reason": "Forbidden",
"details": {},
"code": 403
}2、使用openssl-x509签发证书
2.1 签发普通用户
[root@k8s-master01 x509cert]# openssl genrsa -out birkhoff.key 2048
[root@k8s-master01 x509cert]# openssl req -new -key birkhoff.key -out birkhoff.csr -subj "/CN=birkhoff/O=developers"
[root@k8s-master01 x509cert]# openssl x509 -req -days 365 -CA /etc/kubernetes/pki/ca.crt -CAkey /etc/kubernetes/pki/ca.key -CAcreateserial -in birkhoff.csr -out birkhoff.crt
Signature ok
subject=/CN=birkhoff/O=developers
Getting CA Private Key
[root@k8s-master01 x509cert]# curl -k -E ./birkhoff.crt --key ./birkhoff.key https://192.168.40.101:6443
{
"kind": "Status",
"apiVersion": "v1",
"metadata": {},
"status": "Failure",
"message": "forbidden: User \"birkhoff\" cannot get path \"/\"",
"reason": "Forbidden",
"details": {},
"code": 403
}
#将 证书和 ca证书发到node1上 进行测试
[root@k8s-master01 x509cert]# scp birkhoff.* 192.168.40.111:/root/x509
[root@k8s-master01 x509cert]# scp /etc/kubernetes/pki/ca.crt 192.168.40.111:/root/x509
#此时无法访问 因为没有RBAC授权
[root@k8s-node01 ~]# kubectl get pods --client-certificate=/root/x509/birkhoff.crt --client-key=/root/x509/birkhoff.key --server=https://192.168.40.101:6443 --certificate-authority=/root/x509/ca.crt
Error from server (Forbidden): pods is forbidden: User "birkhoff" cannot list resource "pods" in API group "" in the namespace "default"2.2 签发system用户
system:masters用户可以有权限看到很多资源
[root@k8s-master01 x509cert]# openssl genrsa -out superadmin.key 2048
#/O改为system:masters
[root@k8s-master01 x509cert]# openssl req -new -key superadmin.key -out superadmin.csr -subj "/CN=superadmin/O=system:masters"
[root@k8s-master01 x509cert]# openssl x509 -req -days 365 -CA /etc/kubernetes/pki/ca.crt -CAkey /etc/kubernetes/pki/ca.key -CAcreateserial -in superadmin.csr -out superadmin.crt
[root@k8s-master01 x509cert]# curl -k -E ./superadmin.crt --key ./superadmin.key https://192.168.40.101:6443
{
"paths": [
"/.well-known/openid-configuration",
"/api",
"/api/v1",
"/apis",
"/apis/",
"/apis/admissionregistration.k8s.io",
"/apis/admissionregistration.k8s.io/v1",
"/apis/agent.k8s.elastic.co",
"/apis/agent.k8s.elastic.co/v1alpha1",
"/apis/apiextensions.k8s.io",
"/apis/apiextensions.k8s.io/v1",
"/apis/apiregistration.k8s.io",
"/apis/apiregistration.k8s.io/v1",
"/apis/apm.k8s.elastic.co",
"/apis/apm.k8s.elastic.co/v1",
"/apis/apm.k8s.elastic.co/v1beta1",
"/apis/apps",
"/apis/apps/v1",
"/apis/authentication.k8s.io",
"/apis/authentication.k8s.io/v1",
"/apis/authorization.k8s.io",
"/apis/authorization.k8s.io/v1",
"/apis/autoscaling",
"/apis/autoscaling.k8s.elastic.co",
"/apis/autoscaling.k8s.elastic.co/v1alpha1",
"/apis/autoscaling/v1",
"/apis/autoscaling/v2",
"/apis/batch",
"/apis/batch/v1",
"/apis/beat.k8s.elastic.co",
"/apis/beat.k8s.elastic.co/v1beta1",
"/apis/certificates.k8s.io",
"/apis/certificates.k8s.io/v1",
"/apis/coordination.k8s.io",
"/apis/coordination.k8s.io/v1",
"/apis/crd.projectcalico.org",
"/apis/crd.projectcalico.org/v1",
"/apis/discovery.k8s.io",
"/apis/discovery.k8s.io/v1",
"/apis/elasticsearch.k8s.elastic.co",
"/apis/elasticsearch.k8s.elastic.co/v1",
"/apis/elasticsearch.k8s.elastic.co/v1beta1",
"/apis/enterprisesearch.k8s.elastic.co",
"/apis/enterprisesearch.k8s.elastic.co/v1",
"/apis/enterprisesearch.k8s.elastic.co/v1beta1",
"/apis/events.k8s.io",
"/apis/events.k8s.io/v1",
"/apis/flowcontrol.apiserver.k8s.io",
"/apis/flowcontrol.apiserver.k8s.io/v1beta2",
"/apis/flowcontrol.apiserver.k8s.io/v1beta3",
"/apis/kibana.k8s.elastic.co",
"/apis/kibana.k8s.elastic.co/v1",
"/apis/kibana.k8s.elastic.co/v1beta1",
"/apis/logstash.k8s.elastic.co",
"/apis/logstash.k8s.elastic.co/v1alpha1",
"/apis/maps.k8s.elastic.co",
"/apis/maps.k8s.elastic.co/v1alpha1",
"/apis/metallb.io",
"/apis/metallb.io/v1alpha1",
"/apis/metallb.io/v1beta1",
"/apis/metallb.io/v1beta2",
"/apis/networking.k8s.io",
"/apis/networking.k8s.io/v1",
"/apis/node.k8s.io",
"/apis/node.k8s.io/v1",
"/apis/openebs.io",
"/apis/openebs.io/v1",
"/apis/openebs.io/v1alpha1",
"/apis/policy",
"/apis/policy/v1",
"/apis/rbac.authorization.k8s.io",
"/apis/rbac.authorization.k8s.io/v1",
"/apis/scheduling.k8s.io",
"/apis/scheduling.k8s.io/v1",
"/apis/stackconfigpolicy.k8s.elastic.co",
"/apis/stackconfigpolicy.k8s.elastic.co/v1alpha1",
"/apis/storage.k8s.io",
"/apis/storage.k8s.io/v1",
"/healthz",
"/healthz/autoregister-completion",
"/healthz/etcd",
"/healthz/log",
"/healthz/ping",
"/healthz/poststarthook/aggregator-reload-proxy-client-cert",
"/healthz/poststarthook/apiservice-discovery-controller",
"/healthz/poststarthook/apiservice-openapi-controller",
"/healthz/poststarthook/apiservice-openapiv3-controller",
"/healthz/poststarthook/apiservice-registration-controller",
"/healthz/poststarthook/apiservice-status-available-controller",
"/healthz/poststarthook/bootstrap-controller",
"/healthz/poststarthook/crd-informer-synced",
"/healthz/poststarthook/generic-apiserver-start-informers",
"/healthz/poststarthook/kube-apiserver-autoregistration",
"/healthz/poststarthook/priority-and-fairness-config-consumer",
"/healthz/poststarthook/priority-and-fairness-config-producer",
"/healthz/poststarthook/priority-and-fairness-filter",
"/healthz/poststarthook/rbac/bootstrap-roles",
"/healthz/poststarthook/scheduling/bootstrap-system-priority-classes",
"/healthz/poststarthook/start-apiextensions-controllers",
"/healthz/poststarthook/start-apiextensions-informers",
"/healthz/poststarthook/start-cluster-authentication-info-controller",
"/healthz/poststarthook/start-deprecated-kube-apiserver-identity-lease-garbage-collector",
"/healthz/poststarthook/start-kube-aggregator-informers",
"/healthz/poststarthook/start-kube-apiserver-admission-initializer",
"/healthz/poststarthook/start-kube-apiserver-identity-lease-controller",
"/healthz/poststarthook/start-kube-apiserver-identity-lease-garbage-collector",
"/healthz/poststarthook/start-legacy-token-tracking-controller",
"/healthz/poststarthook/start-service-ip-repair-controllers",
"/healthz/poststarthook/start-system-namespaces-controller",
"/healthz/poststarthook/storage-object-count-tracker-hook",
"/livez",
"/livez/autoregister-completion",
"/livez/etcd",
"/livez/log",
"/livez/ping",
"/livez/poststarthook/aggregator-reload-proxy-client-cert",
"/livez/poststarthook/apiservice-discovery-controller",
"/livez/poststarthook/apiservice-openapi-controller",
"/livez/poststarthook/apiservice-openapiv3-controller",
"/livez/poststarthook/apiservice-registration-controller",
"/livez/poststarthook/apiservice-status-available-controller",
"/livez/poststarthook/bootstrap-controller",
"/livez/poststarthook/crd-informer-synced",
"/livez/poststarthook/generic-apiserver-start-informers",
"/livez/poststarthook/kube-apiserver-autoregistration",
"/livez/poststarthook/priority-and-fairness-config-consumer",
"/livez/poststarthook/priority-and-fairness-config-producer",
"/livez/poststarthook/priority-and-fairness-filter",
"/livez/poststarthook/rbac/bootstrap-roles",
"/livez/poststarthook/scheduling/bootstrap-system-priority-classes",
"/livez/poststarthook/start-apiextensions-controllers",
"/livez/poststarthook/start-apiextensions-informers",
"/livez/poststarthook/start-cluster-authentication-info-controller",
"/livez/poststarthook/start-deprecated-kube-apiserver-identity-lease-garbage-collector",
"/livez/poststarthook/start-kube-aggregator-informers",
"/livez/poststarthook/start-kube-apiserver-admission-initializer",
"/livez/poststarthook/start-kube-apiserver-identity-lease-controller",
"/livez/poststarthook/start-kube-apiserver-identity-lease-garbage-collector",
"/livez/poststarthook/start-legacy-token-tracking-controller",
"/livez/poststarthook/start-service-ip-repair-controllers",
"/livez/poststarthook/start-system-namespaces-controller",
"/livez/poststarthook/storage-object-count-tracker-hook",
"/logs",
"/metrics",
"/metrics/slis",
"/openapi/v2",
"/openapi/v3",
"/openapi/v3/",
"/openid/v1/jwks",
"/readyz",
"/readyz/autoregister-completion",
"/readyz/etcd",
"/readyz/etcd-readiness",
"/readyz/informer-sync",
"/readyz/log",
"/readyz/ping",
"/readyz/poststarthook/aggregator-reload-proxy-client-cert",
"/readyz/poststarthook/apiservice-discovery-controller",
"/readyz/poststarthook/apiservice-openapi-controller",
"/readyz/poststarthook/apiservice-openapiv3-controller",
"/readyz/poststarthook/apiservice-registration-controller",
"/readyz/poststarthook/apiservice-status-available-controller",
"/readyz/poststarthook/bootstrap-controller",
"/readyz/poststarthook/crd-informer-synced",
"/readyz/poststarthook/generic-apiserver-start-informers",
"/readyz/poststarthook/kube-apiserver-autoregistration",
"/readyz/poststarthook/priority-and-fairness-config-consumer",
"/readyz/poststarthook/priority-and-fairness-config-producer",
"/readyz/poststarthook/priority-and-fairness-filter",
"/readyz/poststarthook/rbac/bootstrap-roles",
"/readyz/poststarthook/scheduling/bootstrap-system-priority-classes",
"/readyz/poststarthook/start-apiextensions-controllers",
"/readyz/poststarthook/start-apiextensions-informers",
"/readyz/poststarthook/start-cluster-authentication-info-controller",
"/readyz/poststarthook/start-deprecated-kube-apiserver-identity-lease-garbage-collector",
"/readyz/poststarthook/start-kube-aggregator-informers",
"/readyz/poststarthook/start-kube-apiserver-admission-initializer",
"/readyz/poststarthook/start-kube-apiserver-identity-lease-controller",
"/readyz/poststarthook/start-kube-apiserver-identity-lease-garbage-collector",
"/readyz/poststarthook/start-legacy-token-tracking-controller",
"/readyz/poststarthook/start-service-ip-repair-controllers",
"/readyz/poststarthook/start-system-namespaces-controller",
"/readyz/poststarthook/storage-object-count-tracker-hook",
"/readyz/shutdown",
"/version"
]
}
#查看node1
[root@k8s-master01 x509cert]# scp superadmin.* 192.168.40.111:/root/x509
[root@k8s-node01 ~]# kubectl get pods --client-certificate=/root/x509/superadmin.crt --client-key=/root/x509/superadmin.key --server=https://192.168.40.101:6443 --certificate-authority=/root/x509/ca.crt
NAME READY STATUS RESTARTS AGE
adminbox-5ccff58646-vclm2 0/1 CrashLoopBackOff 360 (3m15s ago) 30h
client-10961 0/1 Error 0 26h
client-2933 0/1 Error 0 2d3h
dowardapi-pod 1/1 Running 2 (31h ago) 4d1h
nginx-test-566dbd78d4-dk2h9 1/1 Running 1 (31h ago) 2d21h
nginx-test-566dbd78d4-ht5sf 1/1 Running 1 (31h ago) 2d21h
nginx-test-566dbd78d4-jb5zx 1/1 Running 1 (31h ago) 2d21h 

 浙公网安备 33010602011771号
浙公网安备 33010602011771号