Kubernetes-service
目录
- service图解
- 集群内服务发现
- 部署metallb
- 创建网络池
- 创建loadbalancer的svc
-
创建ingress
-
测试访问链接
-
Service
负载均衡器:kube-proxy,通过haproxy实现
trnuser@k8s:~$ kubectl get service -A
NAMESPACE NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
default kubernetes ClusterIP 10.1.0.1 <none> 443/TCP 17d
deployment dc1 ClusterIP 10.1.198.0 <none> 80/TCP 9d
deployment dc2 ClusterIP 10.1.83.114 <none> 80/TCP 9d
helm-mysql mysql LoadBalancer 10.1.52.191 10.250.101.241 3306:30228/TCP 7d4h
helm-mysql mysql-slave ClusterIP 10.1.12.158 <none> 3306/TCP 7d4h
ingress-nginx ingress-nginx LoadBalancer 10.1.215.239 10.250.101.242 80:30224/TCP,443:32573/TCP 9d
kube-system kube-dns ClusterIP 10.1.0.10 <none> 53/UDP,53/TCP,9153/TCP 17d
kube-system metrics-server ClusterIP 10.1.90.3 <none> 443/TCP 16d
kubernetes-dashboard dashboard-metrics-scraper ClusterIP 10.1.252.68 <none> 8000/TCP 16d
kubernetes-dashboard kubernetes-dashboard NodePort 10.1.27.163 <none> 443:30008/TCP 16d
prometheus grafana NodePort 10.1.194.181 <none> 80:32044/TCP 6d20h
prometheus prometheus-alertmanager ClusterIP 10.1.65.96 <none> 80/TCP 6d21h
prometheus prometheus-kube-state-metrics ClusterIP None <none> 80/TCP,81/TCP 6d21h
prometheus prometheus-node-exporter ClusterIP None <none> 9100/TCP 6d21h
prometheus prometheus-pushgateway ClusterIP 10.1.37.152 <none> 9091/TCP 6d21h
prometheus prometheus-server NodePort 10.1.186.79 <none> 80:31824/TCP 6d21h
secret svc1 ClusterIP 10.1.53.54 <none> 80/TCP 10d
secret wordpress-mysql ClusterIP None <none> 3306/TCP 10d
service pod-test ClusterIP 10.1.69.146 <none> 8080/TCP 10d
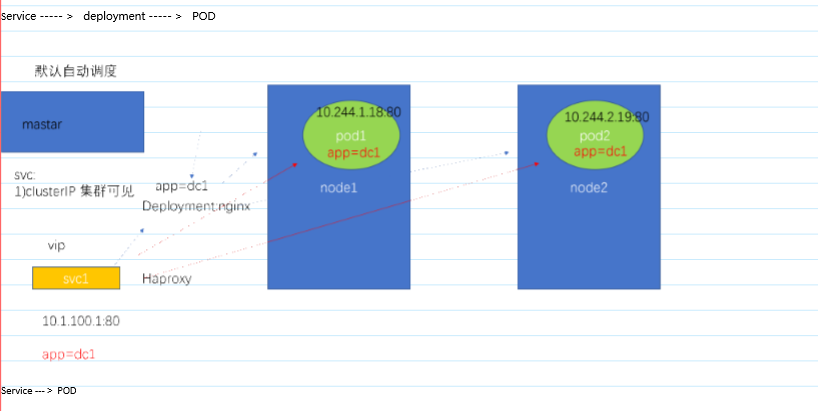
- Service访问图解
![]()
- 暴露POD
kubectl expose pod pod-test --port=80 --target-port=80 --type=ClusterIP
#--port serivce监听的端口
#--target-port pod监听的端口
#--type svc的类
1. ClusterIP # 仅集群内可见
2. NodePort # 生产网可访问,使用NODE端口
3. LoadBalancer # 生产网可访问
----
trnuser@k8s:~/pod/dc$ kubectl describe svc p80
Name: p80
Namespace: service
Labels: run=pod-test
Annotations: <none>
Selector: run=pod-test
Type: ClusterIP
IP: 10.1.76.243
Port: <unset> 8080/TCP # port 为外面访问需指定的端口 curl 10.1.76.243:8080
TargetPort: 80/TCP # targetPort为容器中开放的端口
Endpoints: 10.244.104.39:80
Session Affinity: None
Events: <none>
trnuser@k8s:~/pod/dc$ kubectl describe svc p8080
Name: p8080
Namespace: service
Labels: run=pod-test
Annotations: <none>
Selector: run=pod-test
Type: ClusterIP
IP: 10.1.47.127
Port: <unset> 80/TCP
TargetPort: 8080/TCP
Endpoints: 10.244.104.39:8080
Session Affinity: None
Events: <none>
trnuser@k8s:~/pod/dc$ curl 10.1.76.243:8080
OO
- 集群内实现服务发现
服务发现:各个POD之间怎么实现通讯
1)可以通过 ClusterIP访问 #不建议,IP会变
2)service名字 # 同一个NAMESPACE中的POD之间通讯
3)通过变量 # 不建议
#:不同NAMESPACE间通信
不同NAMESPACE中的POD,可以通过POD IP通讯
不同NAMESPACE中的POD,可以通过Cluster IP通讯
不同NAMESPACE中的POD,不可以通过服务名通讯
不同NAMESPACE中的POD,可以通过FQDN通讯
FQDN:服务名(svc名).命名空间.svc.cluster.local 前提:不同NAMESPACE中需要通过svc才能访问
-
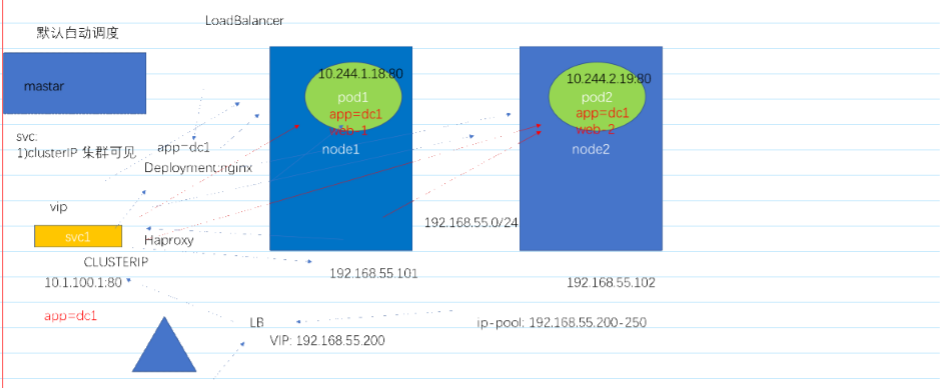
服务发布
![]()
-
部署LoadBalancer
![]()
- 创建namespace--> metallb-system
kubectl create ns metallb-system
- 生成secret,随机的key
kubectl create secret generic -n metallb-system memberlist --from-literal=secretkey="$(openssl rand -base64 128)"
- 部署metallb
trnuser@k8s:~/pod/metallb$ cat namespace.yaml
apiVersion: v1
kind: Namespace
metadata:
name: metallb-system
labels:
app: metallb
trnuser@k8s:~/pod/metallb$ ls
create-network.yaml metallb.yaml namespace.yaml
trnuser@k8s:~/pod/metallb$ cat create-network.yaml
apiVersion: v1
kind: ConfigMap
metadata:
namespace: metallb-system
name: config
data:
config: |
address-pools:
- name: default
protocol: layer2
addresses:
- 10.250.101.241-10.250.101.249
trnuser@k8s:~/pod/metallb$ ls
create-network.yaml metallb.yaml namespace.yaml
trnuser@k8s:~/pod/metallb$ cat metallb.yaml
apiVersion: policy/v1beta1
kind: PodSecurityPolicy
metadata:
labels:
app: metallb
name: controller
namespace: metallb-system
spec:
allowPrivilegeEscalation: false
allowedCapabilities: []
allowedHostPaths: []
defaultAddCapabilities: []
defaultAllowPrivilegeEscalation: false
fsGroup:
ranges:
- max: 65535
min: 1
rule: MustRunAs
hostIPC: false
hostNetwork: false
hostPID: false
privileged: false
readOnlyRootFilesystem: true
requiredDropCapabilities:
- ALL
runAsUser:
ranges:
- max: 65535
min: 1
rule: MustRunAs
seLinux:
rule: RunAsAny
supplementalGroups:
ranges:
- max: 65535
min: 1
rule: MustRunAs
volumes:
- configMap
- secret
- emptyDir
---
apiVersion: policy/v1beta1
kind: PodSecurityPolicy
metadata:
labels:
app: metallb
name: speaker
namespace: metallb-system
spec:
allowPrivilegeEscalation: false
allowedCapabilities:
- NET_ADMIN
- NET_RAW
- SYS_ADMIN
allowedHostPaths: []
defaultAddCapabilities: []
defaultAllowPrivilegeEscalation: false
fsGroup:
rule: RunAsAny
hostIPC: false
hostNetwork: true
hostPID: false
hostPorts:
- max: 7472
min: 7472
privileged: true
readOnlyRootFilesystem: true
requiredDropCapabilities:
- ALL
runAsUser:
rule: RunAsAny
seLinux:
rule: RunAsAny
supplementalGroups:
rule: RunAsAny
volumes:
- configMap
- secret
- emptyDir
---
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
app: metallb
name: controller
namespace: metallb-system
---
apiVersion: v1
kind: ServiceAccount
metadata:
labels:
app: metallb
name: speaker
namespace: metallb-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
labels:
app: metallb
name: metallb-system:controller
rules:
- apiGroups:
- ''
resources:
- services
verbs:
- get
- list
- watch
- update
- apiGroups:
- ''
resources:
- services/status
verbs:
- update
- apiGroups:
- ''
resources:
- events
verbs:
- create
- patch
- apiGroups:
- policy
resourceNames:
- controller
resources:
- podsecuritypolicies
verbs:
- use
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRole
metadata:
labels:
app: metallb
name: metallb-system:speaker
rules:
- apiGroups:
- ''
resources:
- services
- endpoints
- nodes
verbs:
- get
- list
- watch
- apiGroups:
- ''
resources:
- events
verbs:
- create
- patch
- apiGroups:
- policy
resourceNames:
- speaker
resources:
- podsecuritypolicies
verbs:
- use
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
labels:
app: metallb
name: config-watcher
namespace: metallb-system
rules:
- apiGroups:
- ''
resources:
- configmaps
verbs:
- get
- list
- watch
---
apiVersion: rbac.authorization.k8s.io/v1
kind: Role
metadata:
labels:
app: metallb
name: pod-lister
namespace: metallb-system
rules:
- apiGroups:
- ''
resources:
- pods
verbs:
- list
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
labels:
app: metallb
name: metallb-system:controller
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: metallb-system:controller
subjects:
- kind: ServiceAccount
name: controller
namespace: metallb-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: ClusterRoleBinding
metadata:
labels:
app: metallb
name: metallb-system:speaker
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: metallb-system:speaker
subjects:
- kind: ServiceAccount
name: speaker
namespace: metallb-system
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
labels:
app: metallb
name: config-watcher
namespace: metallb-system
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: config-watcher
subjects:
- kind: ServiceAccount
name: controller
- kind: ServiceAccount
name: speaker
---
apiVersion: rbac.authorization.k8s.io/v1
kind: RoleBinding
metadata:
labels:
app: metallb
name: pod-lister
namespace: metallb-system
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: pod-lister
subjects:
- kind: ServiceAccount
name: speaker
---
apiVersion: apps/v1
kind: DaemonSet
metadata:
labels:
app: metallb
component: speaker
name: speaker
namespace: metallb-system
spec:
selector:
matchLabels:
app: metallb
component: speaker
template:
metadata:
annotations:
prometheus.io/port: '7472'
prometheus.io/scrape: 'true'
labels:
app: metallb
component: speaker
spec:
containers:
- args:
- --port=7472
- --config=config
env:
- name: METALLB_NODE_NAME
valueFrom:
fieldRef:
fieldPath: spec.nodeName
- name: METALLB_HOST
valueFrom:
fieldRef:
fieldPath: status.hostIP
- name: METALLB_ML_BIND_ADDR
valueFrom:
fieldRef:
fieldPath: status.podIP
# needed when another software is also using memberlist / port 7946
#- name: METALLB_ML_BIND_PORT
# value: "7946"
- name: METALLB_ML_LABELS
value: "app=metallb,component=speaker"
- name: METALLB_ML_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.namespace
- name: METALLB_ML_SECRET_KEY
valueFrom:
secretKeyRef:
name: memberlist
key: secretkey
image: metallb/speaker:main
imagePullPolicy: IfNotPresent
name: speaker
ports:
- containerPort: 7472
name: monitoring
resources:
limits:
cpu: 100m
memory: 100Mi
securityContext:
allowPrivilegeEscalation: false
capabilities:
add:
- NET_ADMIN
- NET_RAW
- SYS_ADMIN
drop:
- ALL
readOnlyRootFilesystem: true
hostNetwork: true
nodeSelector:
beta.kubernetes.io/os: linux
serviceAccountName: speaker
terminationGracePeriodSeconds: 2
tolerations:
- effect: NoSchedule
key: node-role.kubernetes.io/master
---
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
app: metallb
component: controller
name: controller
namespace: metallb-system
spec:
revisionHistoryLimit: 3
selector:
matchLabels:
app: metallb
component: controller
template:
metadata:
annotations:
prometheus.io/port: '7472'
prometheus.io/scrape: 'true'
labels:
app: metallb
component: controller
spec:
containers:
- args:
- --port=7472
- --config=config
image: metallb/controller:main
imagePullPolicy: IfNotPresent
name: controller
ports:
- containerPort: 7472
name: monitoring
resources:
limits:
cpu: 100m
memory: 100Mi
securityContext:
allowPrivilegeEscalation: false
capabilities:
drop:
- all
readOnlyRootFilesystem: true
nodeSelector:
beta.kubernetes.io/os: linux
securityContext:
runAsNonRoot: true
runAsUser: 65534
serviceAccountName: controller
terminationGracePeriodSeconds: 0
- 创建网络池
trnuser@k8s:~/pod/metallb$ cat create-network.yaml
apiVersion: v1
kind: ConfigMap
metadata:
namespace: metallb-system
name: config
data:
config: |
address-pools:
- name: default
protocol: layer2
addresses:
- 10.250.101.241-10.250.101.249
- 验证部署
trnuser@k8s:~/pod/metallb$ kubectl get pods -n metallb-system
NAME READY STATUS RESTARTS AGE
controller-648db4b75-b7tz5 1/1 Running 0 10d
speaker-blbwt 1/1 Running 0 10d
speaker-gl9wt 1/1 Running 0 10d
speaker-jrd4d 1/1 Running 0 10d
speaker-zkhts 1/1 Running 0 10d
trnuser@k8s:~/pod/metallb$
- 部署LoadBalancer的SVC
kubectl expose deployment dc1 --port=80 --target-port=80 --type LoadBalancer
- 部署ingress
注:ingress主要用于http,https,结合loadbalancer使用,节约生产ip
原理:nginx的反向代理
- 图解说明
![]()
- 部署ingress
trnuser@k8s:~/pod/ingress$ cat ingress-nginx-V0.24.1.yaml
apiVersion: v1
kind: Namespace
metadata:
name: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
---
kind: ConfigMap
apiVersion: v1
metadata:
name: nginx-configuration
namespace: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
---
kind: ConfigMap
apiVersion: v1
metadata:
name: tcp-services
namespace: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
---
kind: ConfigMap
apiVersion: v1
metadata:
name: udp-services
namespace: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: nginx-ingress-serviceaccount
namespace: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: ClusterRole
metadata:
name: nginx-ingress-clusterrole
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
rules:
- apiGroups:
- ""
resources:
- configmaps
- endpoints
- nodes
- pods
- secrets
verbs:
- list
- watch
- apiGroups:
- ""
resources:
- nodes
verbs:
- get
- apiGroups:
- ""
resources:
- services
verbs:
- get
- list
- watch
- apiGroups:
- "extensions"
resources:
- ingresses
verbs:
- get
- list
- watch
- apiGroups:
- ""
resources:
- events
verbs:
- create
- patch
- apiGroups:
- "extensions"
resources:
- ingresses/status
verbs:
- update
---
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: Role
metadata:
name: nginx-ingress-role
namespace: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
rules:
- apiGroups:
- ""
resources:
- configmaps
- pods
- secrets
- namespaces
verbs:
- get
- apiGroups:
- ""
resources:
- configmaps
resourceNames:
# Defaults to "<election-id>-<ingress-class>"
# Here: "<ingress-controller-leader>-<nginx>"
# This has to be adapted if you change either parameter
# when launching the nginx-ingress-controller.
- "ingress-controller-leader-nginx"
verbs:
- get
- update
- apiGroups:
- ""
resources:
- configmaps
verbs:
- create
- apiGroups:
- ""
resources:
- endpoints
verbs:
- get
---
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: RoleBinding
metadata:
name: nginx-ingress-role-nisa-binding
namespace: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: Role
name: nginx-ingress-role
subjects:
- kind: ServiceAccount
name: nginx-ingress-serviceaccount
namespace: ingress-nginx
---
apiVersion: rbac.authorization.k8s.io/v1beta1
kind: ClusterRoleBinding
metadata:
name: nginx-ingress-clusterrole-nisa-binding
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
roleRef:
apiGroup: rbac.authorization.k8s.io
kind: ClusterRole
name: nginx-ingress-clusterrole
subjects:
- kind: ServiceAccount
name: nginx-ingress-serviceaccount
namespace: ingress-nginx
---
apiVersion: apps/v1
kind: Deployment
metadata:
name: nginx-ingress-controller
namespace: ingress-nginx
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
spec:
replicas: 1
selector:
matchLabels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
template:
metadata:
labels:
app.kubernetes.io/name: ingress-nginx
app.kubernetes.io/part-of: ingress-nginx
annotations:
prometheus.io/port: "10254"
prometheus.io/scrape: "true"
spec:
serviceAccountName: nginx-ingress-serviceaccount
containers:
- name: nginx-ingress-controller
image: registry.cn-shenzhen.aliyuncs.com/sanjinjin/ingress-nginx:0.24.1
imagePullPolicy: IfNotPresent
args:
- /nginx-ingress-controller
- --configmap=$(POD_NAMESPACE)/nginx-configuration
- --tcp-services-configmap=$(POD_NAMESPACE)/tcp-services
- --udp-services-configmap=$(POD_NAMESPACE)/udp-services
- --publish-service=$(POD_NAMESPACE)/ingress-nginx
- --annotations-prefix=nginx.ingress.kubernetes.io
securityContext:
allowPrivilegeEscalation: true
capabilities:
drop:
- ALL
add:
- NET_BIND_SERVICE
# www-data -> 33
runAsUser: 33
env:
- name: POD_NAME
valueFrom:
fieldRef:
fieldPath: metadata.name
- name: POD_NAMESPACE
valueFrom:
fieldRef:
fieldPath: metadata.namespace
ports:
- name: http
containerPort: 80
- name: https
containerPort: 443
livenessProbe:
failureThreshold: 3
httpGet:
path: /healthz
port: 10254
scheme: HTTP
initialDelaySeconds: 10
periodSeconds: 10
successThreshold: 1
timeoutSeconds: 10
readinessProbe:
failureThreshold: 3
httpGet:
path: /healthz
port: 10254
scheme: HTTP
periodSeconds: 10
successThreshold: 1
timeoutSeconds: 10
kubectl create -f ingress-nginx-V0.24.1.yaml
- 查看ingress
# kubectl expose deployment nginx-ingress-controller --name=ingress-nginx -type=NodePort -n ingress-nginx
trnuser@k8s:~/pod/ingress$ kubectl get svc -n ingress-nginx
NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) AGE
ingress-nginx LoadBalancer 10.1.215.239 10.250.101.242 80:30224/TCP,443:32573/TCP 10d
trnuser@k8s:~/pod/ingress$ kubectl get deployments.apps -n ingress-nginx
NAME READY UP-TO-DATE AVAILABLE AGE
nginx-ingress-controller 1/1 1 1 10d
trnuser@k8s:~/pod/ingress$ kubectl get pod -n ingress-nginx
NAME READY STATUS RESTARTS AGE
nginx-ingress-controller-9cb7c48cd-v6bmz 1/1 Running 0 10d
- 创建一个ingress
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: myingress
spec:
rules:
- host: www.example.com
http:
paths:
- path: /
backend:
serviceName: dc1
servicePort: 80
- path: /cka
backend:
serviceName: dc2
servicePort: 80
---
apiVersion: extensions/v1beta1
kind: Ingress
metadata:
name: myingress-2
spec:
rules:
- host: blog.example.com
http:
paths:
- path: /
backend:
serviceName: dc2
servicePort: 80
- ingress访问
trnuser@k8s:~/pod/ingress$ kubectl get ingress -A
NAMESPACE NAME CLASS HOSTS ADDRESS PORTS AGE
deployment myingress <none> www.example.com 10.250.101.242 80 9d
deployment myingress-2 <none> blog.example.com 10.250.101.242 80 9d






 浙公网安备 33010602011771号
浙公网安备 33010602011771号