(五)容器网络 -上
一 Linux路由机制打通网络
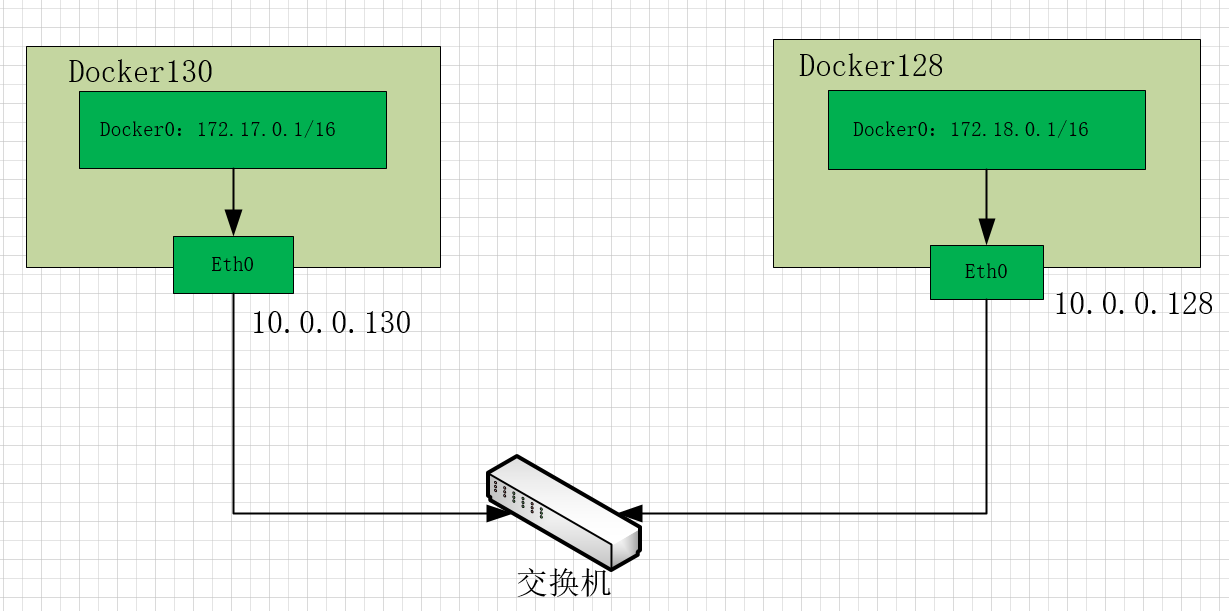
docker128上修改Docker0的网络地址,与docker130不冲突
[root@docker128 ~]# cat /etc/docker/daemon.json {"bip":"172.18.0.1/16"}
[root@docker128 ~]# systemctl restart docker
[root@docker128 ~]# ip addr|grep docker0
5: docker0: <NO-CARRIER,BROADCAST,MULTICAST,UP> mtu 1500 qdisc noqueue state DOWN
inet 172.18.0.1/16 scope global docker0
docker130 上执行 route add -net 172.18.0.0/16 gw 192.168.18.128
docker128 上执行 route add -net 172.17.0.0/16 gw 192.168.18.130
[root@docker128 ~]# ip route default via 10.0.0.2 dev eth0 proto static metric 100 10.0.0.0/8 dev eth0 proto kernel scope link src 10.0.0.128 metric 100 172.17.0.0/16 via 10.0.0.130 dev eth0 172.18.0.0/16 dev docker0 proto kernel scope link src 172.18.0.1 192.168.122.0/24 dev virbr0 proto kernel scope link src 192.168.122.1
在130主机上运行一个容器
[root@docker130 ~]# docker run -it --name=mycentos centos
[root@3b04d1d28796 /]# yum install net-tools -y
[root@3b04d1d28796 /]# ifconfig
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 172.17.0.2 netmask 255.255.0.0 broadcast 0.0.0.0
inet6 fe80::42:acff:fe11:2 prefixlen 64 scopeid 0x20<link>
ether 02:42:ac:11:00:02 txqueuelen 0 (Ethernet)
RX packets 1747 bytes 9192520 (8.7 MiB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 1112 bytes 63744 (62.2 KiB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
[root@docker130 ~]# docker ps -a
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
3b04d1d28796 centos "/bin/bash" 8 minutes ago Exited (0) 2 minutes ago mycentos
[root@docker130 ~]# docker start 3b04d1d28796
3b04d1d28796
[root@docker130 ~]# ping 172.17.0.2
PING 172.17.0.2 (172.17.0.2) 56(84) bytes of data.
64 bytes from 172.17.0.2: icmp_seq=1 ttl=64 time=0.121 ms
64 bytes from 172.17.0.2: icmp_seq=2 ttl=64 time=0.050 ms
64 bytes from 172.17.0.2: icmp_seq=3 ttl=64 time=0.042 ms
^C
--- 172.17.0.2 ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 2000ms
rtt min/avg/max/mdev = 0.042/0.071/0.121/0.035 ms
在130上ping128的一个容器
[root@docker128 ~]# docker exec -it 381e488278b6 /bin/bash [root@381e488278b6 /]# ifconfig eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500 inet 172.18.0.2 netmask 255.255.0.0 broadcast 0.0.0.0 inet6 fe80::42:acff:fe12:2 prefixlen 64 scopeid 0x20<link> ether 02:42:ac:12:00:02 txqueuelen 0 (Ethernet) RX packets 13 bytes 1026 (1.0 KiB) RX errors 0 dropped 0 overruns 0 frame 0 TX packets 13 bytes 1026 (1.0 KiB) TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0
[root@docker130 ~]# ping 172.18.0.2
PING 172.18.0.2 (172.18.0.2) 56(84) bytes of data.
64 bytes from 172.18.0.2: icmp_seq=1 ttl=63 time=0.287 ms
64 bytes from 172.18.0.2: icmp_seq=2 ttl=63 time=0.203 ms
64 bytes from 172.18.0.2: icmp_seq=3 ttl=63 time=0.189 ms
64 bytes from 172.18.0.2: icmp_seq=4 ttl=63 time=0.195 ms
^C
--- 172.18.0.2 ping statistics ---
4 packets transmitted, 4 received, 0% packet loss, time 3000ms
rtt min/avg/max/mdev = 0.189/0.218/0.287/0.042 ms
在128主机上 抓包
[root@docker128 ~]# yum install -y wireshark
#在130的容器中ping 128 容器的ip
[root@3b04d1d28796 /]# ping 172.18.0.2
PING 172.18.0.2 (172.18.0.2) 56(84) bytes of data.
64 bytes from 172.18.0.2: icmp_seq=1 ttl=62 time=0.575 ms
64 bytes from 172.18.0.2: icmp_seq=2 ttl=62 time=0.239 ms
64 bytes from 172.18.0.2: icmp_seq=3 ttl=62 time=0.233 ms
64 bytes from 172.18.0.2: icmp_seq=4 ttl=62 time=0.233 ms
64 bytes from 172.18.0.2: icmp_seq=5 ttl=62 time=0.342 ms
64 bytes from 172.18.0.2: icmp_seq=6 ttl=62 time=0.237 ms
64 bytes from 172.18.0.2: icmp_seq=7 ttl=62 time=0.214 ms
64 bytes from 172.18.0.2: icmp_seq=8 ttl=62 time=0.231 ms
64 bytes from 172.18.0.2: icmp_seq=9 ttl=62 time=0.244 ms
[root@docker128 ~]# tshark -f icmp Running as user "root" and group "root". This could be dangerous. Capturing on 'eth0' 1 0.000000000 10.0.0.130 -> 172.18.0.2 ICMP 98 Echo (ping) request id=0x1753, seq=1/256, ttl=64 2 0.000103946 172.18.0.2 -> 10.0.0.130 ICMP 98 Echo (ping) reply id=0x1753, seq=1/256, ttl=63 (request in 1) 3 1.000691927 10.0.0.130 -> 172.18.0.2 ICMP 98 Echo (ping) request id=0x1753, seq=2/512, ttl=64 4 1.000746593 172.18.0.2 -> 10.0.0.130 ICMP 98 Echo (ping) reply id=0x1753, seq=2/512, ttl=63 (request in 3) 5 2.000378026 10.0.0.130 -> 172.18.0.2 ICMP 98 Echo (ping) request id=0x1753, seq=3/768, ttl=64
[root@docker128 ~]# tshark -i docker0 -f icmp Running as user "root" and group "root". This could be dangerous. Capturing on 'docker0' 1 0.000000000 10.0.0.130 -> 172.18.0.2 ICMP 98 Echo (ping) request id=0x0019, seq=9/2304, ttl=62 2 0.000026941 172.18.0.2 -> 10.0.0.130 ICMP 98 Echo (ping) reply id=0x0019, seq=9/2304, ttl=64 (request in 1) 3 1.000678788 10.0.0.130 -> 172.18.0.2 ICMP 98 Echo (ping) request id=0x0019, seq=10/2560, ttl=62 4 1.000711113 172.18.0.2 -> 10.0.0.130 ICMP 98 Echo (ping) reply id=0x0019, seq=10/2560, ttl=64 (request in 3) 5 2.001349102 10.0.0.130 -> 172.18.0.2 ICMP 98 Echo (ping) request id=0x0019, seq=11/2816, ttl=62 6 2.001382828 172.18.0.2 -> 10.0.0.130 ICMP 98 Echo (ping) reply id=0x0019, seq=11/2816, ttl=64 (request in 5) 7 3.001029334 10.0.0.130 -> 172.18.0.2 ICMP 98 Echo (ping) request id=0x0019, seq=12/3072, ttl=62 8 3.001063332 172.18.0.2 -> 10.0.0.130 ICMP 98 Echo (ping) reply id=0x0019, seq=12/3072, ttl=64 (request in 7) 9 4.001703754 10.0.0.130 -> 172.18.0.2 ICMP 98 Echo (ping) request id=0x0019, seq=13/3328, ttl=62 10 4.001731139 172.18.0.2 -> 10.0.0.130 ICMP 98 Echo (ping) reply id=0x0019, seq=13/3328, ttl=64 (request in 9) 11 5.002387065 10.0.0.130 -> 172.18.0.2 ICMP 98 Echo (ping) request id=0x0019, seq
Docker130上的容器 c1:172.17.0.2ping 128上的容器c2:172.18.0.2时,c1发现这个地址不是自己子网的,于是发 给docker0网关
经过路由计算,这个报文被发往下一跳的路由器端口:eth0,所以ttl减一
报文到达128主机的eth0网卡,经过路由计算,被发往下一跳的端口dock0:
回来的时候,数据包流程:c2--》28 docker0 --》128 eth0 --》130 eth0 --》130 docker0 ---》c1


 浙公网安备 33010602011771号
浙公网安备 33010602011771号