挖矿病毒分析
挖矿病毒
现象
CPU利用率占满了,或者占50%
工具【sysdig】和【unhide】来搜寻被隐藏的进程,这些工具被替换了,运行会出现段错误。
解决
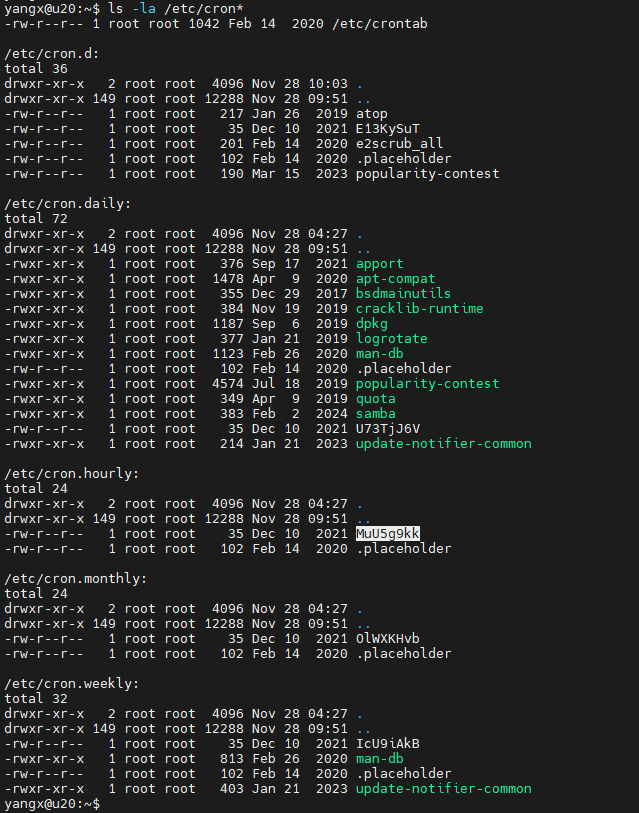
ls -la /etc/cron* # 检查系统级定时任务
ls -la /var/spool/cron/crontabs/ # 检查所有用户的 crontab 文件
# 里面就可以找到执行的程序
cat /etc/cron.hourly/MuU5g9kk
ls -la /etc/cron*
sudo tail -f /var/log/auth.log # 实时监控登录日志
sudo grep -i "fail|error|attack" /var/log/syslog # 搜索攻击痕迹
病毒的可执行文件:
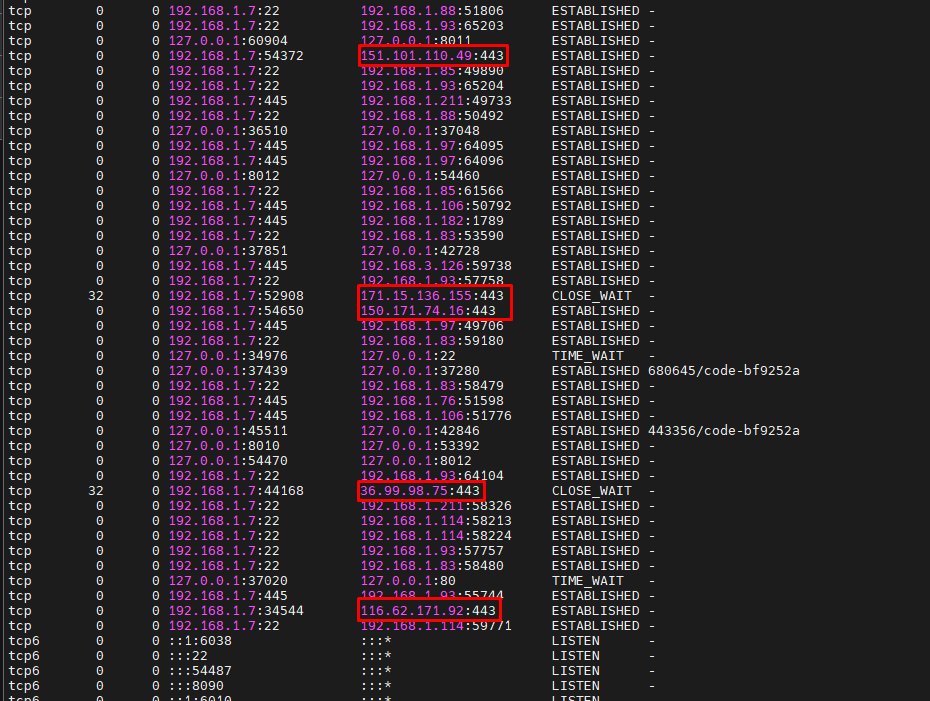
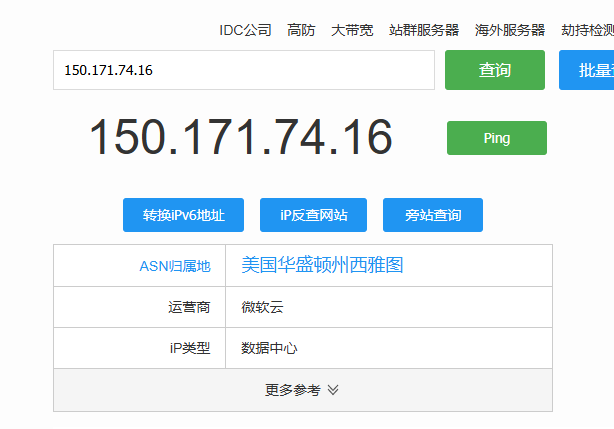
可疑IP:
# 检查服务器的常用程序有没有被替换
sudo apt install rkhunter
sudo rkhunter --check
登陆用户爆破
日志查看
sudo tail -f /var/log/auth.log # 实时监控登录日志
病毒进行字典爆破日志:
Nov 28 11:10:08 u20 sshd[184701]: Invalid user .hlifanuang from 127.0.0.1 port 42542
Nov 28 11:10:08 u20 sshd[184701]: pam_unix(sshd:auth): check pass; user unknown
Nov 28 11:10:08 u20 sshd[184701]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=127.0.0.1
Nov 28 11:10:10 u20 sshd[184701]: Failed password for invalid user lifan.huang from 127.0.0.1 port 42542 ssh2
Nov 28 11:10:11 u20 sshd[184701]: Connection closed by invalid user lifan.huang 127.0.0.1 port 42542 [preauth]
Nov 28 11:10:15 u20 sshd[184749]: Invalid user jin.wu from 127.0.0.1 port 38136
Nov 28 11:10:15 u20 sshd[184749]: pam_unix(sshd:auth): check pass; user unknown
Nov 28 11:10:15 u20 sshd[184749]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=127.0.0.1
Nov 28 11:10:17 u20 sshd[184749]: Failed password for invalid user jin.wu from 127.0.0.1 port 38136 ssh2
Nov 28 11:10:19 u20 sshd[184749]: Connection closed by invalid user jin.wu 127.0.0.1 port 38136 [preauth]
Nov 28 11:10:23 u20 sshd[184886]: Invalid user qing.li from 127.0.0.1 port 34480
Nov 28 11:10:23 u20 sshd[184886]: pam_unix(sshd:auth): check pass; user unknown
Nov 28 11:10:23 u20 sshd[184886]: pam_unix(sshd:auth): authentication failure; logname= uid=0 euid=0 tty=ssh ruser= rhost=127.0.0.1
Nov 28 11:10:24 u20 sshd[184886]: Failed password for invalid user qing.li from 127.0.0.1 port 34480 ssh2
Nov 28 11:10:25 u20 sshd[184886]: Connection closed by invalid user qing.li 127.0.0.1 port 34480 [preauth]
Nov 28 11:10:30 u20 sshd[184936]: Invalid user wenliu.zhu from 127.0.0.1 port 59566
可以看到有常用的用户名进行不停的尝试
解决
# 安装 Fail2Ban 自动封禁爆破 IP
sudo apt install fail2ban
sudo systemctl enable fail2ban
sudo systemctl start fail2ban
参考
https://zhuanlan.zhihu.com/p/1916912786694439328
https://blog.csdn.net/wananxuexihu/article/details/145681912
本文来自博客园,作者:杨旭0324,转载请注明原文链接:https://www.cnblogs.com/allalonewithyou/p/19313424,个人邮箱:yaonie4444@foxmail.com





 浙公网安备 33010602011771号
浙公网安备 33010602011771号