DASCTF 2025下半年|矩阵博弈,零度突围 Misc详解
DASCTF 2025下半年|矩阵博弈,零度突围 Misc详解
DigitalSignature
Find out the signer. Maybe you need EIP-191. Flag is account address that wrapped by DASCTF{}.
思路:利用以太坊签名的可恢复特性,通过公开的签名和原始消息,还原出签名者的地址
exp:
from web3 import Web3
from eth_account.messages import encode_defunct
# 已知数据
message_text = "Find out the signer. Flag is account address that wrapped by DASCTF{}."
signature_hex = "0x019c4c2968032373cb8e19f13450e93a1abf8658097405cda5489ea22d3779b57815a7e27498057a8c29bcd38f9678b917a887665c1f0d970761cacdd8c41fb61b"
# 重建消息结构(与签名时一致)
message = encode_defunct(text=message_text)
# 恢复 signer 地址
signer = Web3().eth.account.recover_message(message, signature=signature_hex)
print("Recovered address:", signer)
print("Flag:", f"DASCTF{{{signer}}}")
DASCTF{0x2b2D44D5325F0d3550296686BE2a7b5Fecb952cB}
stegh小鬼
010查看快乐小鬼,发现是jpg图片的逆序
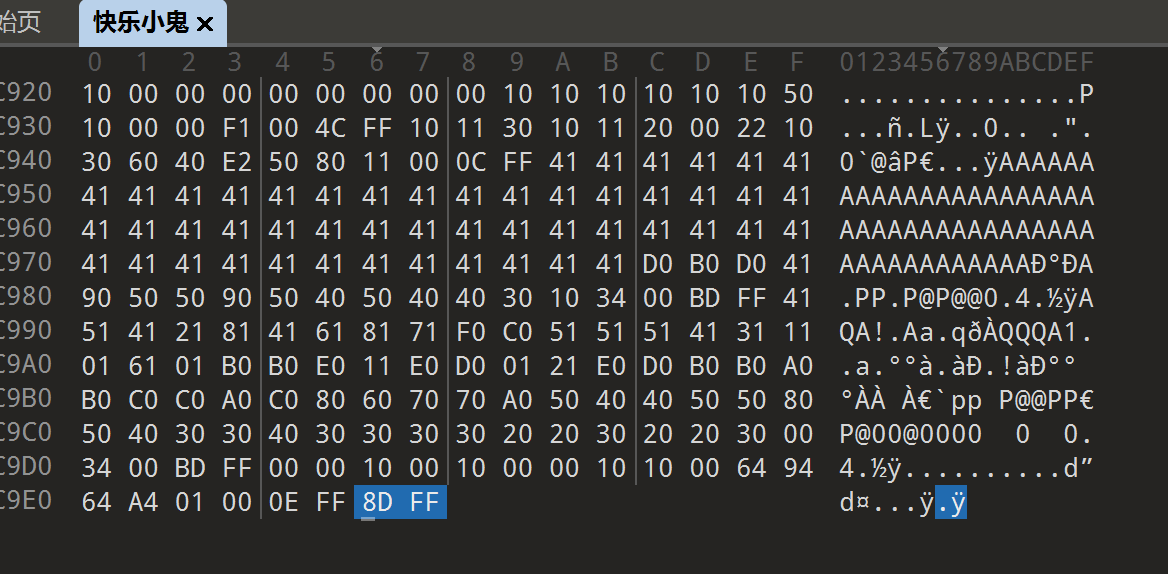
倒置导出
再次查看图片尾部
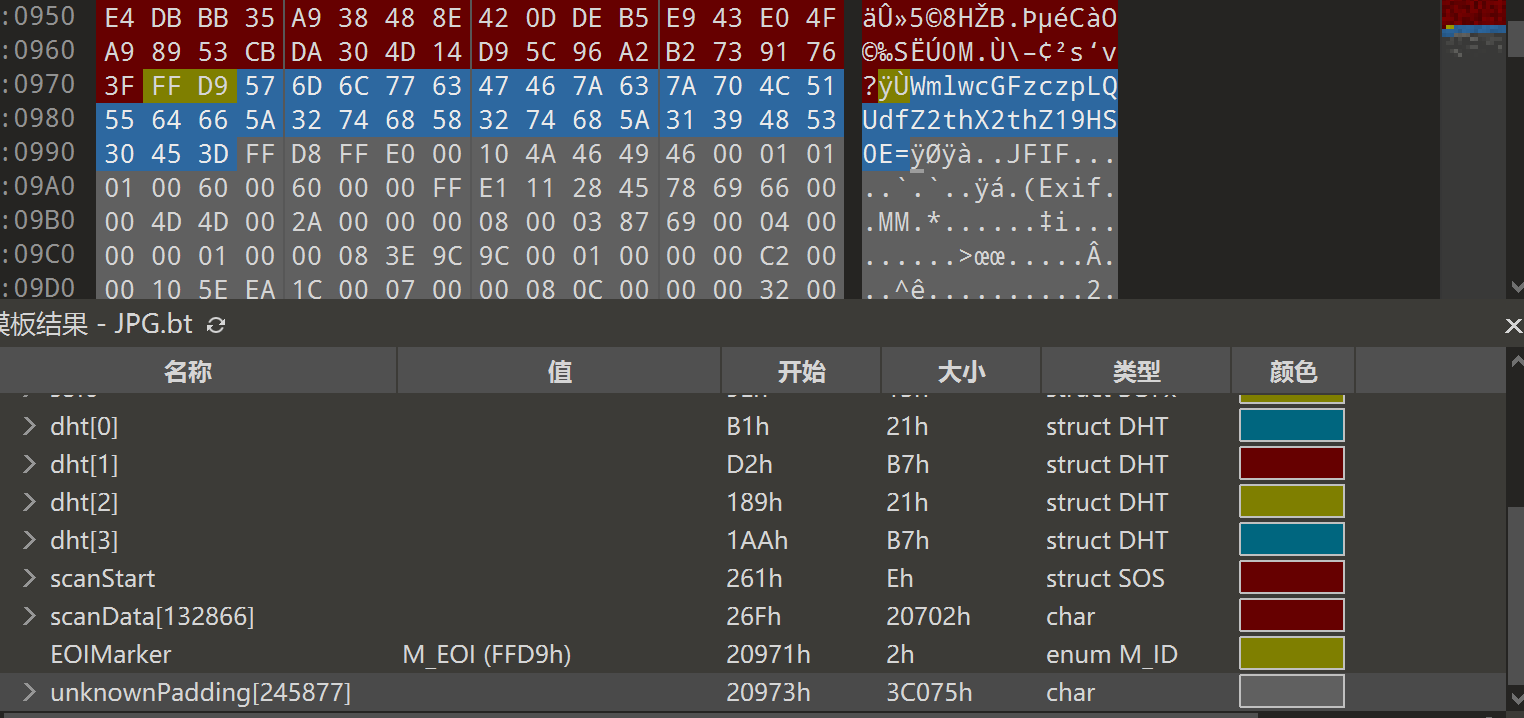
文件尾部存在unknownPadding块,是一串base64加一个jpg图片
WmlwcGFzczpLQUdfZ2thX2thZ19HS0E=
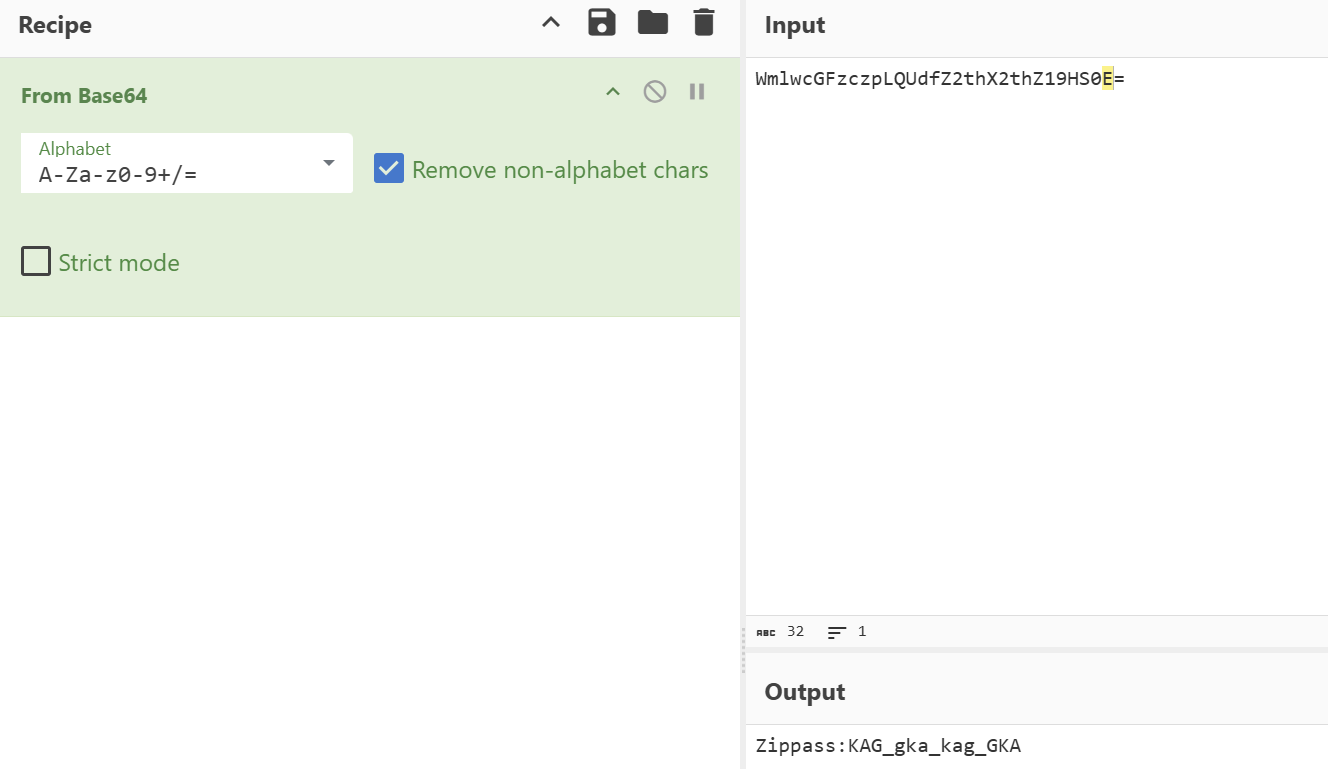
Zippass:KAG_gka_kag_GKA
剩下的图片用foremost分离出来
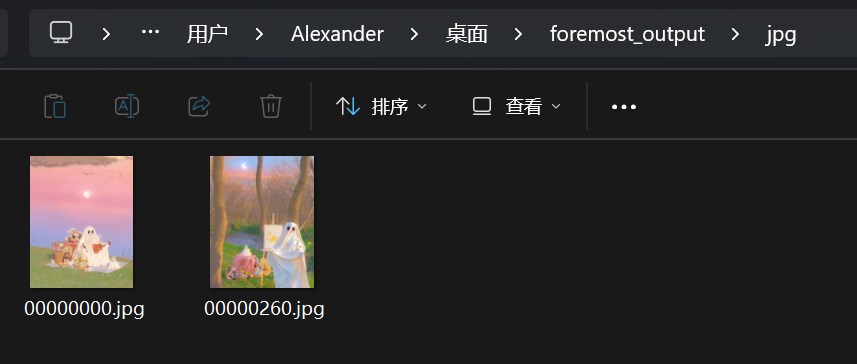
先用KAG_gka_kag_GKA打开zip压缩包
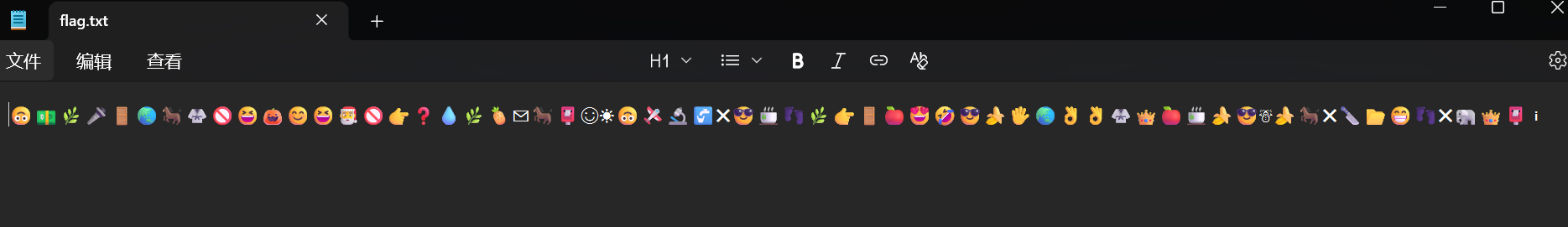
得到flag.txt,emoji图像,猜测可能base100或者emoji-aes
经过尝试发现base100不行,那么就是emoji-aes,这个需要密码
我们回到分离的图片
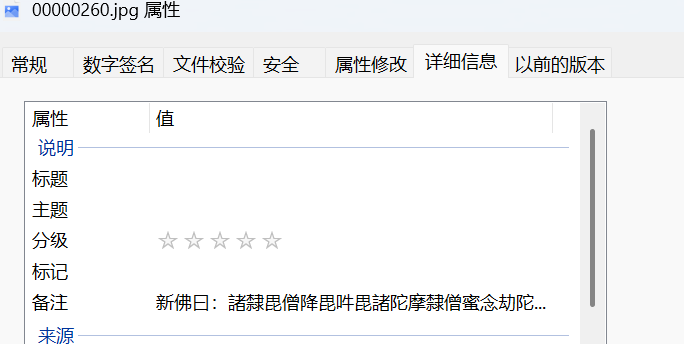
备注有新佛曰加密,但是网站挂了,后面根据hint,直接把密码给我们了
新佛曰挂了,解码出来--pass:2333333
根据附件名字stegh小鬼,猜测为steghide隐写,密码为2333333
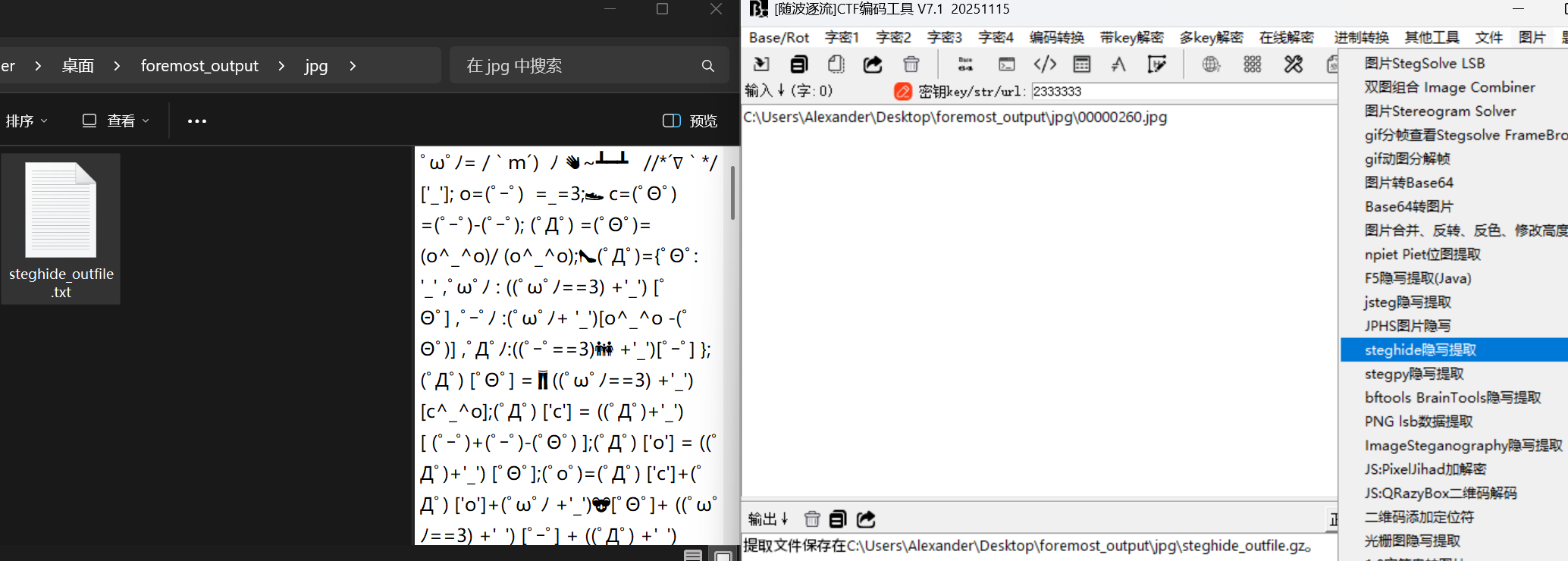
゚ω゚ノ= /`m´)ノ 👋~┻━┻ //*´∇`*/ ['_']; o=(゚ー゚) =_=3;👟 c=(゚Θ゚) =(゚ー゚)-(゚ー゚); (゚Д゚) =(゚Θ゚)= (o^_^o)/ (o^_^o);👠(゚Д゚)={゚Θ゚: '_' ,゚ω゚ノ : ((゚ω゚ノ==3) +'_') [゚Θ゚] ,゚ー゚ノ :(゚ω゚ノ+ '_')[o^_^o -(゚Θ゚)] ,゚Д゚ノ:((゚ー゚==3)👪 +'_')[゚ー゚] }; (゚Д゚) [゚Θ゚] =👖((゚ω゚ノ==3) +'_') [c^_^o];(゚Д゚) ['c'] = ((゚Д゚)+'_') [ (゚ー゚)+(゚ー゚)-(゚Θ゚) ];(゚Д゚) ['o'] = ((゚Д゚)+'_') [゚Θ゚];(゚o゚)=(゚Д゚) ['c']+(゚Д゚) ['o']+(゚ω゚ノ +'_')🐨[゚Θ゚]+ ((゚ω゚ノ==3) +'_') [゚ー゚] + ((゚Д゚) +'_') [(゚ー゚)+(゚ー゚)]+ ((゚ー゚==3) +'_') [゚Θ゚]+((゚ー゚==3) +'_') [(゚ー゚) - (゚Θ゚)]+(゚Д゚) ['c']+((゚Д゚)+'_') [(゚ー゚)+(゚ー゚)]+ (゚Д゚) ['o']+((゚ー゚==3) +'_') [゚Θ゚];(゚Д゚) ['_'] =(o^_^o) [゚o゚] [゚o゚];(゚ε゚)=((゚ー゚==3) +'_') [゚Θ゚]+ (゚Д゚) .゚Д゚ノ+((゚Д゚)+'_')👪 [(゚ー゚) + (゚ー゚)]+((゚ー゚==3) +'_') [o^_^o -゚Θ゚]+((゚ー゚==3) +'_') [゚Θ゚]+ (゚ω゚ノ +'_') [゚Θ゚]; (゚ー゚)+=(゚Θ゚); (゚Д゚)[゚ε゚]='\\'; (゚Д゚).゚Θ゚ノ=👖(゚Д゚+ ゚ー゚)[o^_^o -(゚Θ゚)];(o゚ー゚o)=(゚ω゚ノ +'_')[c^_^o];(゚Д゚) [゚o゚]='\"';(゚Д゚) ['_'] ( (゚Д゚) ['_'] (゚ε゚+/*´∇`*/(゚Д゚)[゚o゚]+ (゚Д゚)👇[゚ε゚]+(゚Θ゚)+(゚Θ゚)+(゚ー゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+((゚ー゚) + 🐫(o^_^o))+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+((゚ー゚) + (o^_^o))+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+(o^_^o)+(゚Д゚)[゚ε゚]+(゚ー゚)+(c^_^o)+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+(o^_^o)+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+👪(゚Θ゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((o^_^o) +(o^_^o))+((o^_^o) - (゚Θ゚))+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+((゚ー゚) + (゚Θ゚))+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+((o^_^o) +(o^_^o))+(゚Д゚)[゚ε゚]+(゚Θ゚)+((o^_^o) +(o^_^o))+👪((゚ー゚) + (゚Θ゚))+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+(゚ー゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+(゚ー゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (o^_^o))+(゚Θ゚)+(゚Д゚)[゚ε゚]+(゚ー゚)+(c^_^o)+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+(゚Θ゚)👮+(゚Д゚)[゚ε゚]+(゚Θ゚)+((o^_^o) +(o^_^o))+(゚ー゚)+(゚Д゚)[゚ε゚]+(゚ー゚)+(c^_^o)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((o^_^o) +(o^_^o))+(゚ー゚)🐧+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+(c^_^o)+(゚Д゚)[゚ε゚]+(゚👩Θ゚)+(゚ー゚)+((゚ー゚) + (゚Θ゚))+(゚Д゚)[゚ε゚]+(゚ー゚)+(c^_^o)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+((゚ー゚) + (゚Θ゚))+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+(゚Θ゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+(゚ー゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+(゚ー゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+(゚ー゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+((゚ー゚) + (゚Θ゚))+(゚Д゚)[゚ε゚]+(゚ー゚)+(c^_^o)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+((゚ー゚) + (o^_^o))+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+((o^_^o) +(o^_^o))+(゚Д゚)[゚ε゚]+(゚ー゚)+(c^_^o)👛+(゚Д゚)[゚ε゚]+(゚Θ゚)+((o^_^o) +(o^_^o))+(゚ー゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+(c^_^o)+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+((゚ー゚) + (゚Θ゚))+(゚Д゚)[゚ε゚]+(゚ー゚)+(c^_^o)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((o^_^o) +(o^_^o))+(c^_^o)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((゚ー゚) + (゚Θ゚))+(゚Θ゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+(o^_^o)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((o^_^o) +(o^_^o))+(゚ー゚)+(゚Д゚)[゚ε゚]+(゚Θ゚)+((o^_^o) +(o^_^o))+((゚ー゚) + (゚Θ゚))+(゚Д゚)[゚ε゚]+(゚Θ゚)+((o^_^o) +(o^_^o))+((o^_^o) - (゚Θ゚))+(゚Д゚)[゚ε゚]+(゚Θ゚)+(゚ー゚)+((゚ー゚) + (゚Θ゚))+(゚Д゚)[゚o゚]) (゚Θ゚)) ('_');
分离emoji和特殊字符
特殊字符为AAencode颜文字解密,不知道为啥随波逐流为啥没反应
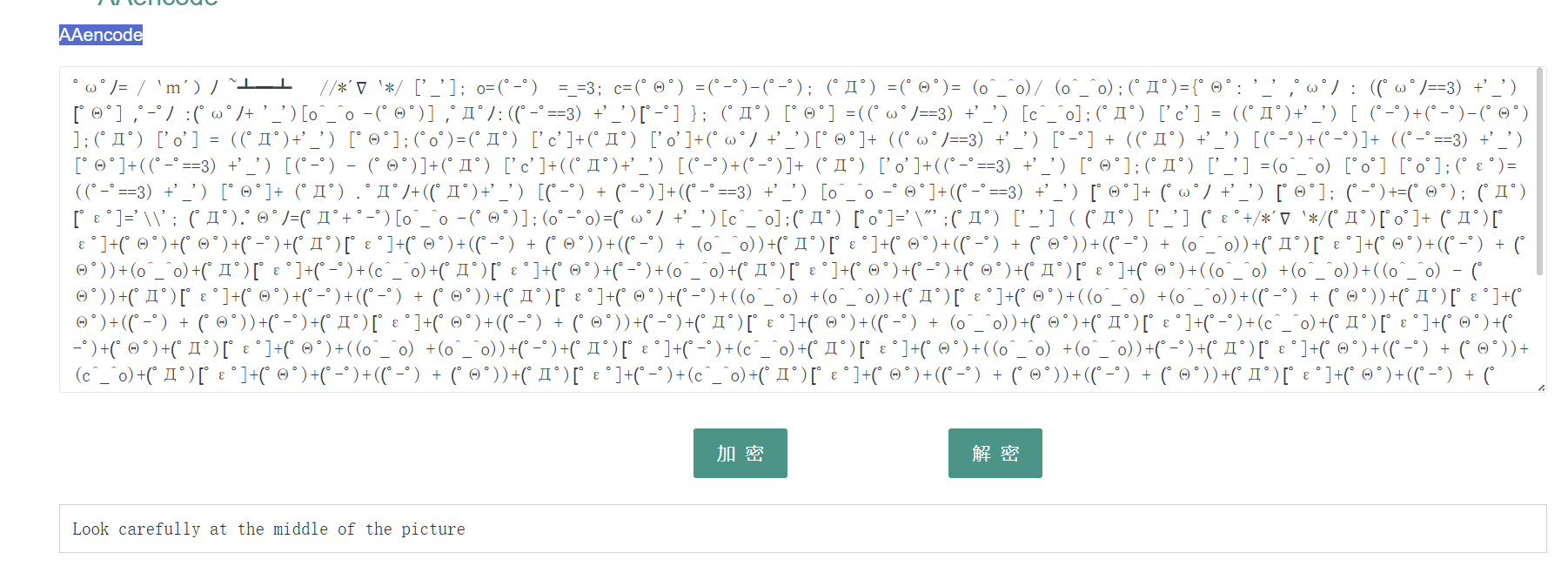
Look carefully at the middle of the picture
这个意思是让我们仔细看图片中间,我们foremost时候已经发现图片中间的zip密码了,所以可以忽略
emoji为base100
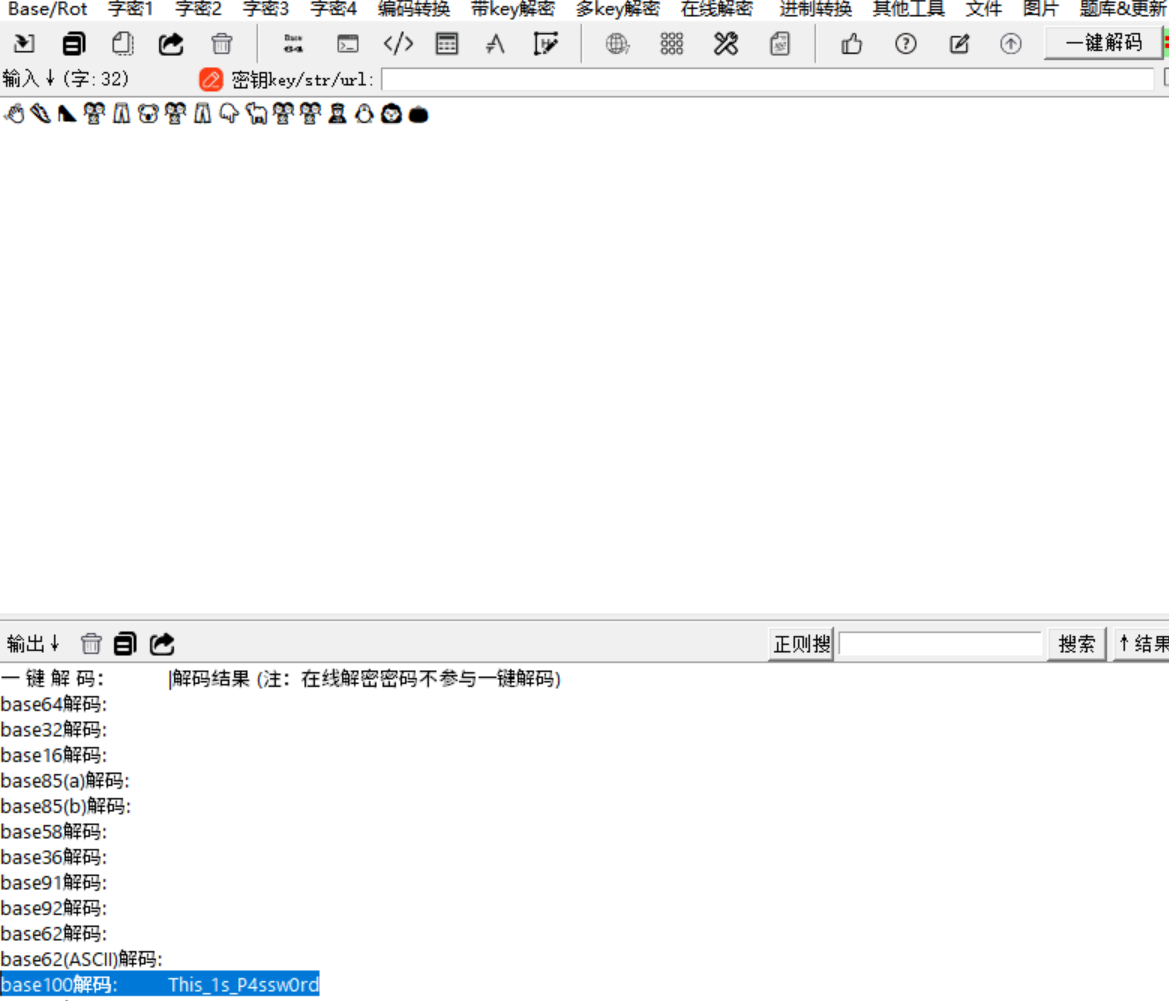
This_1s_P4ssw0rd
最后emoji-aes解密
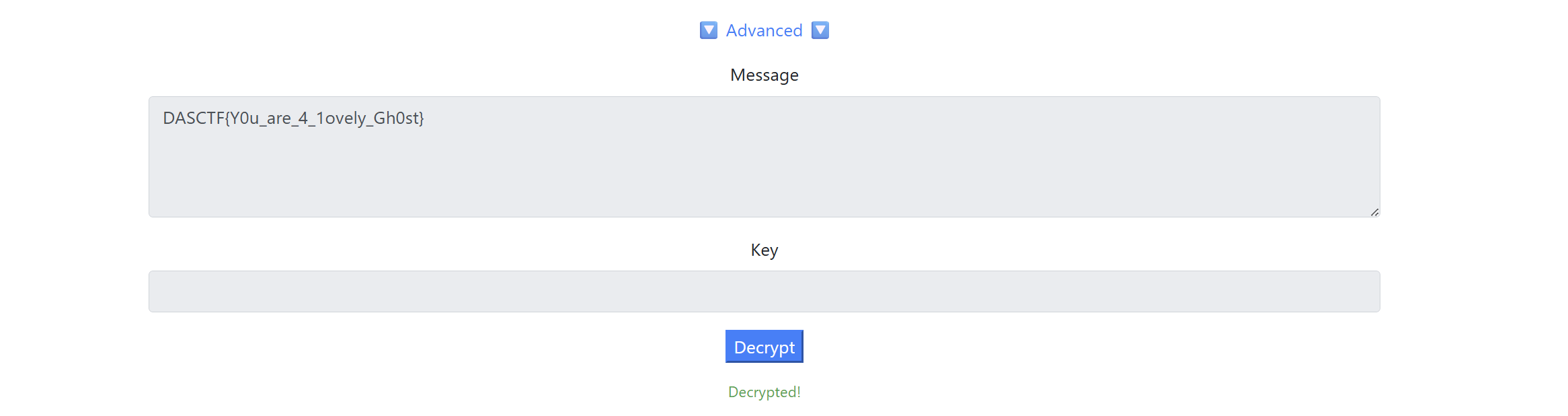
DASCTF{Y0u_are_4_1ovely_Gh0st}
Steganography_challenges0.2
010模板报错
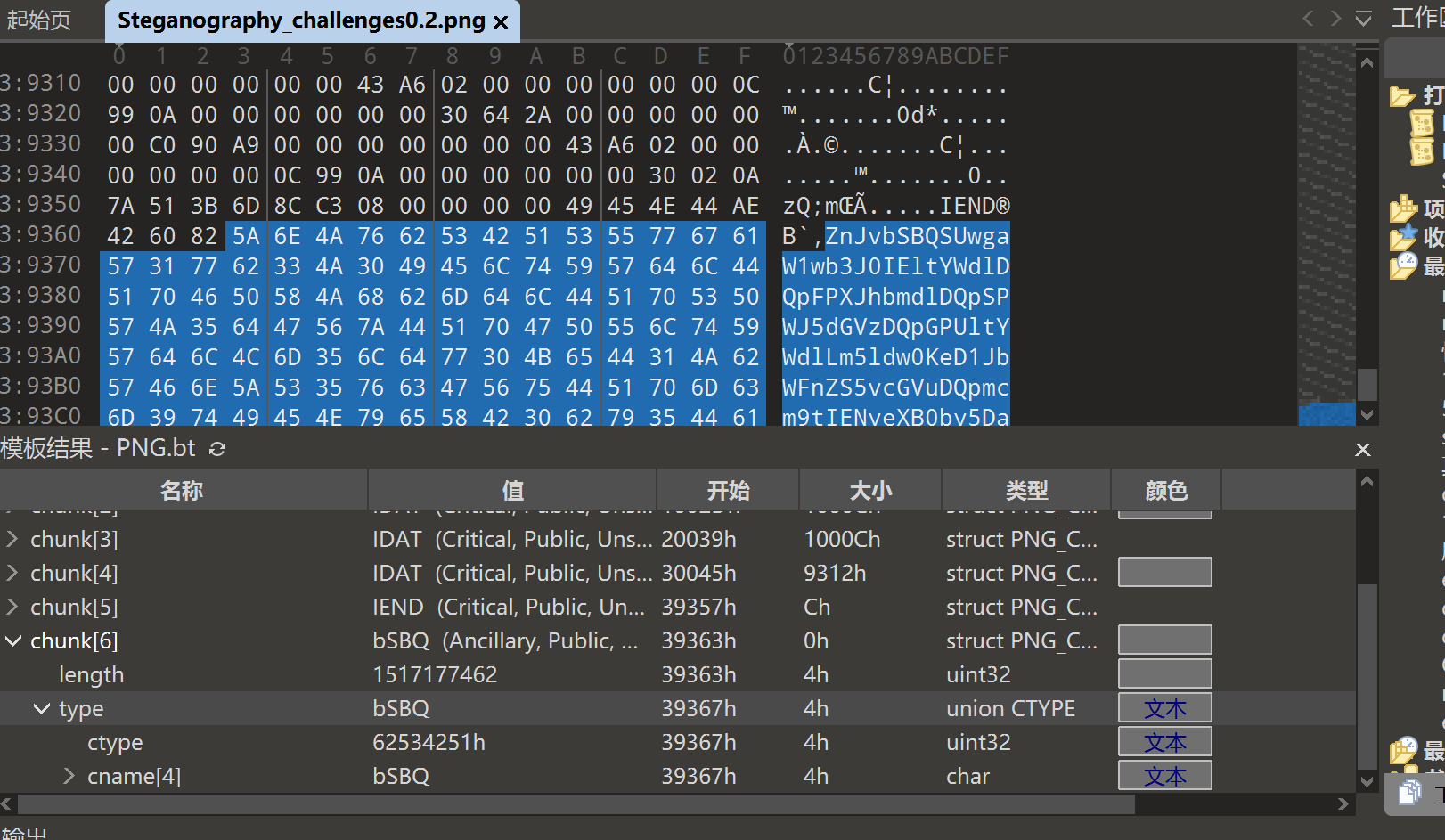
文件尾部出现base64文本
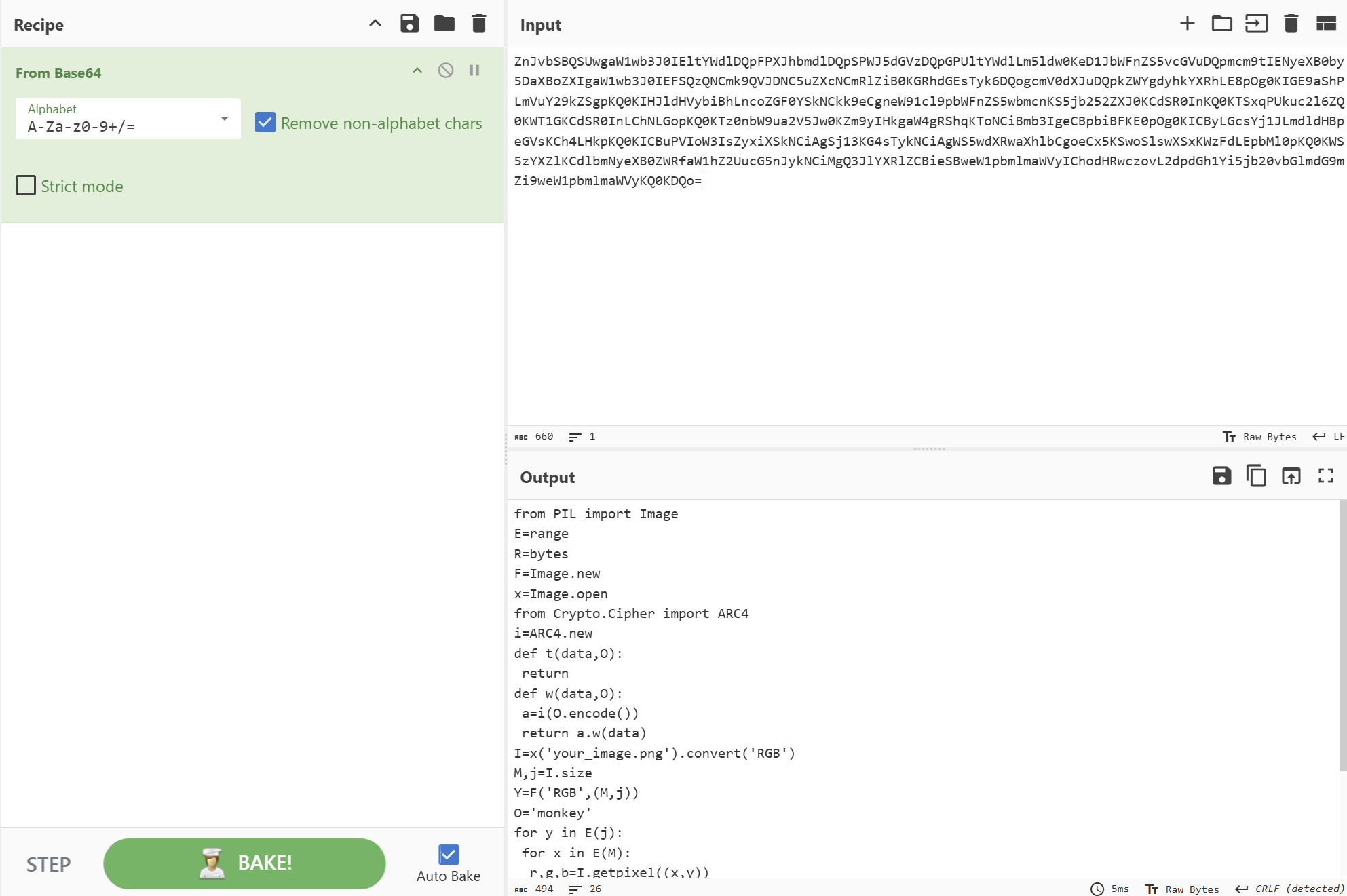
from PIL import Image
E=range
R=bytes
F=Image.new
x=Image.open
from Crypto.Cipher import ARC4
i=ARC4.new
def t(data,O):
return
def w(data,O):
a=i(O.encode())
return a.w(data)
I=x('your_image.png').convert('RGB')
M,j=I.size
Y=F('RGB',(M,j))
O='monkey'
for y in E(j):
for x in E(M):
r,g,b=I.getpixel((x,y))
n=R([r,g,b])
J=w(n,O)
Y.putpixel((x,y),(J[0],J[1],J[2]))
Y.save('encrypted_image.png')
# Created by pyminifier (https://github.com/liftoff/pyminifier)
一个使用RC4加密算法对图像像素进行加密的程序,我们反向解密
from PIL import Image
from Crypto.Cipher import ARC4
import os
def decrypt_image(input_path, output_path):
if not os.path.exists(input_path):
print(f"Error: {input_path} not found.")
return
try:
img = Image.open(input_path).convert('RGB')
width, height = img.size
new_img = Image.new('RGB', (width, height))
key = 'monkey'
cipher_temp = ARC4.new(key.encode('utf-8'))
keystream = cipher_temp.encrypt(b'\x00' * 3)
print(f"Keystream for first 3 bytes: {list(keystream)}")
pixels = img.load()
new_pixels = new_img.load()
for y in range(height):
for x in range(width):
r, g, b = pixels[x, y]
dr = r ^ keystream[0]
dg = g ^ keystream[1]
db = b ^ keystream[2]
new_pixels[x, y] = (dr, dg, db)
new_img.save(output_path)
print(f"Success: Decrypted image saved to {output_path}")
except Exception as e:
print(f"Error processing image: {str(e)}")
if __name__ == "__main__":
INPUT_IMAGE_PATH = r"Steganography_challenges0.2.png"
OUTPUT_IMAGE_PATH = "decrypted_image.png"
decrypt_image(INPUT_IMAGE_PATH, OUTPUT_IMAGE_PATH)
lsb隐写通道并行,每个通道有独立存储信息,然后按顺序组合: 然后连续拼凑
from PIL import Image
# 输入图片路径
input_image = r"decrypted_image.png"
try:
# 打开图片并转换为RGB模式
img = Image.open(input_image).convert('RGB')
width, height = img.size
print(f"图片尺寸: {width} x {height}")
# 加载像素数据
pixels = img.load()
# 提取区域:x从1243到1257,y从1243到1254
start_x, end_x = 1243, 1257 # 列范围
start_y, end_y = 1243, 1254 # 行范围
# 存储三个通道的LSB位
lsb = [[], [], []] # [R通道, G通道, B通道]
# 提取LSB位
for channel in range(3): # 0:R, 1:G, 2:B
for i in range(start_y, end_y + 1): # y坐标
for j in range(start_x, end_x + 1): # x坐标
# 获取像素的RGB值,提取指定通道的最低位
bit = pixels[j, i][channel] & 1
lsb[channel].append(bit)
print("\n=== LSB位提取结果 ===")
print(f"每个通道提取的位数: {len(lsb[0])}")
print(f"R通道前10位: {lsb[0][:10]}")
print(f"G通道前10位: {lsb[1][:10]}")
print(f"B通道前10位: {lsb[2][:10]}")
# 将三个通道的LSB位交错组合
tmp = ""
for i in range(len(lsb[0])):
for channel in range(3):
tmp += str(lsb[channel][i])
print(f"\n=== 组合后的二进制串 ===")
print(f"二进制串长度: {len(tmp)} bits")
print(f"前60位: {tmp[:60]}")
# 每8位二进制转换为一个字符
key = ""
for i in range(0, len(tmp), 8):
if i + 8 <= len(tmp): # 确保有完整的8位
byte_str = tmp[i:i+8]
char_code = int(byte_str, 2)
key += chr(char_code)
print(f"\n=== 解码结果 ===")
print(f"解码出的字符串: {key}")
print(f"字符串长度: {len(key)} 字符")
# 尝试以不同方式显示结果
print(f"\n=== 十六进制表示 ===")
hex_str = ""
for i in range(0, len(tmp), 8):
if i + 8 <= len(tmp):
hex_str += hex(int(tmp[i:i+8], 2))[2:].zfill(2) + " "
print(f"十六进制: {hex_str[:100]}...")
except FileNotFoundError:
print(f"错误: 找不到文件 {input_image}")
print("请确保 'decrypted_image.png' 文件在当前目录")
except Exception as e:
print(f"运行时错误: {e}")
It seems that you are really a steg_master,key is Oversized_chips
得到key
剩下的是lsb另一种隐写,aes+lsb的加密隐写方式:clockedpixels
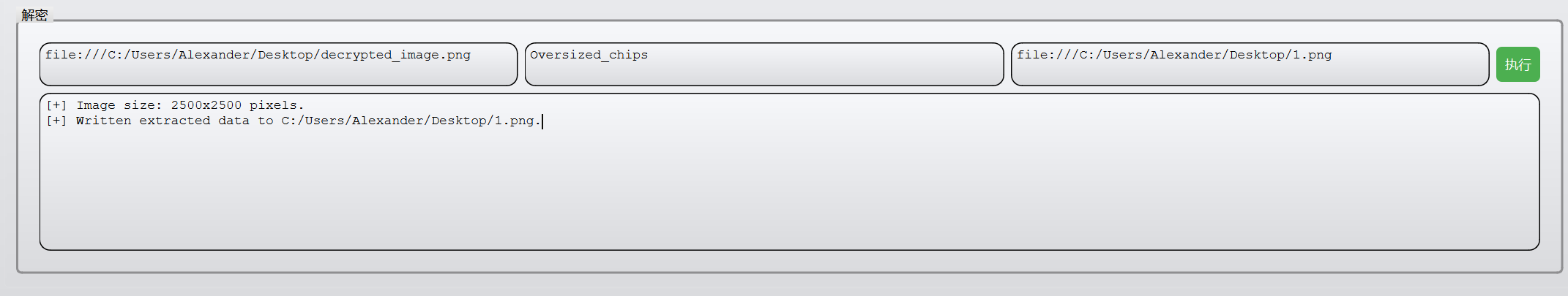
得到一个水的图片

猜测为盲水印
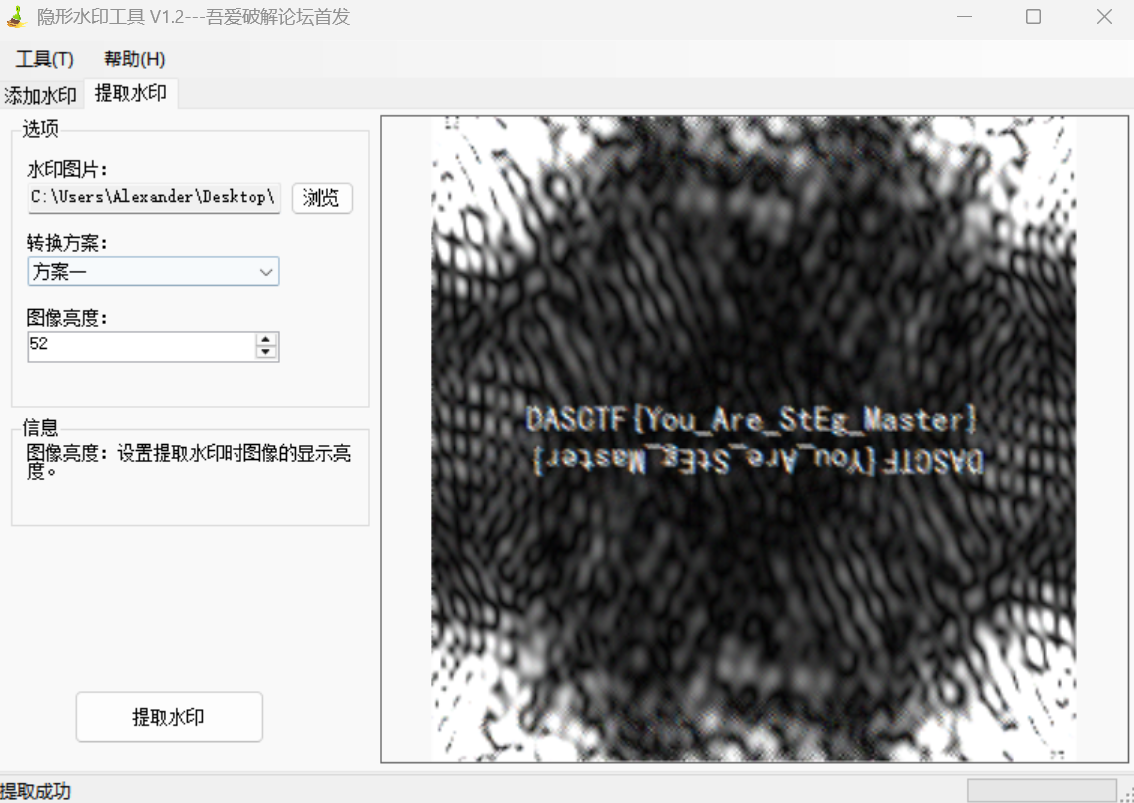
得到flag
DASCTF{You_Are_StEg_Master}
本文来自博客园,作者:{Alexander17},转载请注明原文链接:{https://home.cnblogs.com/u/alexander17}


 浙公网安备 33010602011771号
浙公网安备 33010602011771号