整理密码学的系统性地基础知识(图解、密码原理、常用算法、openssl) - part3 命令式实践(openssl)
1. 命令式实践(openssl)
原明文数据
$ echo "hello world!" > raw.txt $ cat raw.txt hello world!
1.1. 对称密码
说明:对称加密算法一般要和分组模式组合使用,输入参数有加密算法的KEY和分组模式需要的IV,这两个值可以通过参数指定,也可以利用password和salt让openssl自动计算。
1.1.1. AES-256-CBC
步骤1:将明文转为密文
$ openssl enc -e -aes-256-cbc -base64 -S 00112233 -pass pass:"a1b2c3" -p -in raw.txt -out cipher.txt salt=0011223300000000 key=30C61CECD25703E18CDEE3535ECC51F78B717329F44FE1760401675F14B83FFE iv =28DEA68CEE4B9FA3CB7458BA44202DA6 $ cat cipher.txt U2FsdGVkX18AESIzAAAAANf7kfQvVsT2sLYhhEXwA2o=
步骤2:对密文转为明文
$ openssl enc -d -aes-256-cbc -base64 -S 00112233 -pass pass:"a1b2c3" -p -in cipher.txt -out plaintext.txt salt=0011223300000000 key=30C61CECD25703E18CDEE3535ECC51F78B717329F44FE1760401675F14B83FFE iv =28DEA68CEE4B9FA3CB7458BA44202DA6 $ cat plaintext.txt hello world!
1.1.2. DES-EDE3-OFB
步骤1 将明文转为密文
$ openssl enc -e -des-ede3-ofb -base64 -K 11111111000000FFFFFFFF -iv FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF -p -nosalt -in raw.txt -out cipher.txt key=11111111000000FFFFFFFF00000000000000000000000000 iv =FFFFFFFFFFFFFFFF $ cat cipher.txt itpQYlxwgzUZeU1FMw==
步骤2 将密文转为明文
$ openssl enc -d -des-ede3-ofb -base64 -K 11111111000000FFFFFFFF -iv FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF -p -nosalt -in cipher.txt -out plaintext.txt key=11111111000000FFFFFFFF00000000000000000000000000 iv =FFFFFFFFFFFFFFFF $ cat plaintext.txt hello world!
1.2. 公钥密码(RSA)
步骤1:创建私钥文件
$ openssl genrsa -out key.private 512 Generating RSA private key, 512 bit long modulus .....................++++++++++++ ..........++++++++++++ e is 65537 (0x10001) $ cat key.private -----BEGIN RSA PRIVATE KEY----- MIIBOgIBAAJBALxpipy7xY8y3ZhjPBHfiE07ZO6grZLpMOP3uhNLO8B97VP9bylE GuJYD4GqMKK5EiokxLIbAuqItb0Q4wZVbKMCAwEAAQJACv/WWcQUioGbsjPI4/o6 yNd40v2KZJM8iXKC6HFx8ZDOxvldTSONaSbBbut+cjcZkh8vFpr7dOYHvRKreASV 0QIhAOcdIoVCoEjh3zKV+m1zvgu9GHLkd+Quwx2RnujcW67vAiEA0LNMpK6C/1H1 RxAGHppV5254O3ge5olbB7PqYUtLHY0CIC3KhwFyTwHBxxBlyOWQzjHTOJnjDKIo Zb5hEORAbOX/AiEApHfYe6Nnasxs7l6rY+yerC67o6oLOASg71YS7C/I93UCICdS 15CkVpQxDr7eQvJQY4ynGag1S/ICHt/YRRjdVr4e -----END RSA PRIVATE KEY-----
步骤2:根据私钥文件创建公钥文件
$ openssl rsa -pubout -in key.private -out key.public writing RSA key $ cat key.public -----BEGIN PUBLIC KEY----- MFwwDQYJKoZIhvcNAQEBBQADSwAwSAJBALxpipy7xY8y3ZhjPBHfiE07ZO6grZLp MOP3uhNLO8B97VP9bylEGuJYD4GqMKK5EiokxLIbAuqItb0Q4wZVbKMCAwEAAQ== -----END PUBLIC KEY-----
步骤3:用公钥文件将原明文进行加密
$ openssl rsautl -encrypt -inkey key.public -pubin -in raw.txt -out cipher.txt
步骤4:用私钥文件对加密后的密文进行解密,还原明文数据文件
$ openssl rsautl -decrypt -inkey key.private -in cipher.txt -out plaintext.txt $ cat plaintext.txt hello world!
1.3. 单向散列函数
说明:使用sha256散列函数根据原明文数据产生一组hex表示的固定长度字串。
$ openssl dgst -hex -sha256 raw.txt SHA256(raw.txt)= ecf701f727d9e2d77c4aa49ac6fbbcc997278aca010bddeeb961c10cf54d435a
1.4. 消息认证码– HMAC
说明:应用HMAC-SHA256函数根据原明文数据产生一组hex表示的固定长度字串,它和单纯的SHA256比,多了一个hmac参数指定key值。
$ openssl dgst -hex -hmac a1b2c3 -sha256 raw.txt HMAC-SHA256(raw.txt)= b6259883d554b8c6fcc9b07d34b55182ff966459f0dcaa07604a5c55832aff06 $ openssl dgst -hex -hmac A1B2C3 -sha256 raw.txt HMAC-SHA256(raw.txt)= 16df5a2e80e74b37d0ae1bb90a97b70e869e7a9f4a33636cf87562816e13f9fe
1.5. 数字签名
步骤1:创建私钥对,创建的方法之前介绍过。
步骤2:用散列函数SHA256把明文生成固定长度的字串,然后用私钥对该字串加密,生成原明文的签名文件。
$ openssl dgst -sign key.private -sha256 -out sign.txt raw.txt
步骤3:用公钥对签名文件解密;用SHA-256算法计算明文文件数据的HASH值;若解密后的签名文件和HASH值相同等验证成功
$ openssl dgst -verify key.public -sha256 -signature sign.txt raw.txt Verified OK
1.6. 证书
说明:接收者Bob的公钥要被包含在证书中,一般接收者Bob和颁发证书的机构不应该是同一个对象,但是为了实验方便,可以假定接收者Bob和颁发证书的机构为同一个对象,然后Bob自己给自己颁发包含自己公钥的证书。
步骤:
$ openssl req -new -newkey rsa:512 -days 30 -SHA1 -nodes -x509 -subj "/C=CH/ST=Sichuan/L=Chengdu" -keyout key.private -out certifate.cer Generating a 512 bit RSA private key ......++++++++++++ ...++++++++++++ writing new private key to 'key.private' ----- $ cat key.private -----BEGIN PRIVATE KEY----- MIIBVAIBADANBgkqhkiG9w0BAQEFAASCAT4wggE6AgEAAkEA3D4oOCvg2jC42OgA o1oANnnXUllokdWZr5jzRnHUT5LRKFxl/bm8HBh7njT4eoiFgbAyCR756WKRKnxB tKAA9wIDAQABAkAXFXi3snmlxNeK/H4coPFGxGx6GB7qsh2ilwBgkMu07zevw1R8 L6l9RDOGcexACz1DmCeZbkERgtKoAQ7aqLmRAiEA79zswWEtC1YlJcIID/BsQ0Wr fLrCEs0kgoZwuuxQwRkCIQDrD1Id5wtqtdylesZuJlLFifgkMk4NGJgXtB5aQbXE jwIhAI3sISXWkqlngjlSEiUkM1qmiW4WrqgjO1wDogXnt2xZAiBaU6jalM5uUzRW 4rcd3NwxzLLuNeaIYcsQUMbZKCcRQQIgT8g9zqQX4IFwFxXzQw7LWUqXbCugAyuq w95vFSyQUbQ= -----END PRIVATE KEY----- $ cat certifate.cer -----BEGIN CERTIFICATE----- MIIBqzCCAVWgAwIBAgIJAK3IyqteqlZKMA0GCSqGSIb3DQEBBQUAMDExCzAJBgNV BAYTAkNIMRAwDgYDVQQIDAdTaWNodWFuMRAwDgYDVQQHDAdDaGVuZ2R1MB4XDTIw MDYyMDA4MDg0N1oXDTIwMDcyMDA4MDg0N1owMTELMAkGA1UEBhMCQ0gxEDAOBgNV BAgMB1NpY2h1YW4xEDAOBgNVBAcMB0NoZW5nZHUwXDANBgkqhkiG9w0BAQEFAANL ADBIAkEA3D4oOCvg2jC42OgAo1oANnnXUllokdWZr5jzRnHUT5LRKFxl/bm8HBh7 njT4eoiFgbAyCR756WKRKnxBtKAA9wIDAQABo1AwTjAdBgNVHQ4EFgQUTWDjEsyN h6vLONUT6w1fEpT0WT8wHwYDVR0jBBgwFoAUTWDjEsyNh6vLONUT6w1fEpT0WT8w DAYDVR0TBAUwAwEB/zANBgkqhkiG9w0BAQUFAANBAM0mJXRJ2yAVMuyqloIdYctY ME8MRWq+uQfBbU2E0kv6SJ4U38vtBroc9ENGZv4fJs6dLu6BIDXlht/CegmgEqE= -----END CERTIFICATE-----
备注:上述命令之后,输出如下两个文件:
文件key.private: 为接收者Bob的私钥
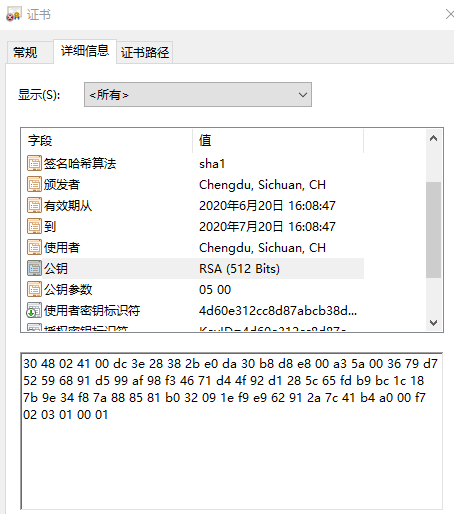
文件certificate.cer:为接收者Bob为自己的公钥颁发的证书。这个证书可以在windows系统上直接鼠标双击打开。内容如下图
posted on 2020-06-24 14:24 LiveWithACat 阅读(995) 评论(0) 收藏 举报


 浙公网安备 33010602011771号
浙公网安备 33010602011771号