esp加密
IPsec ESP AES-GCM_ipsec中esp加密算法aes-gcm-CSDN博客
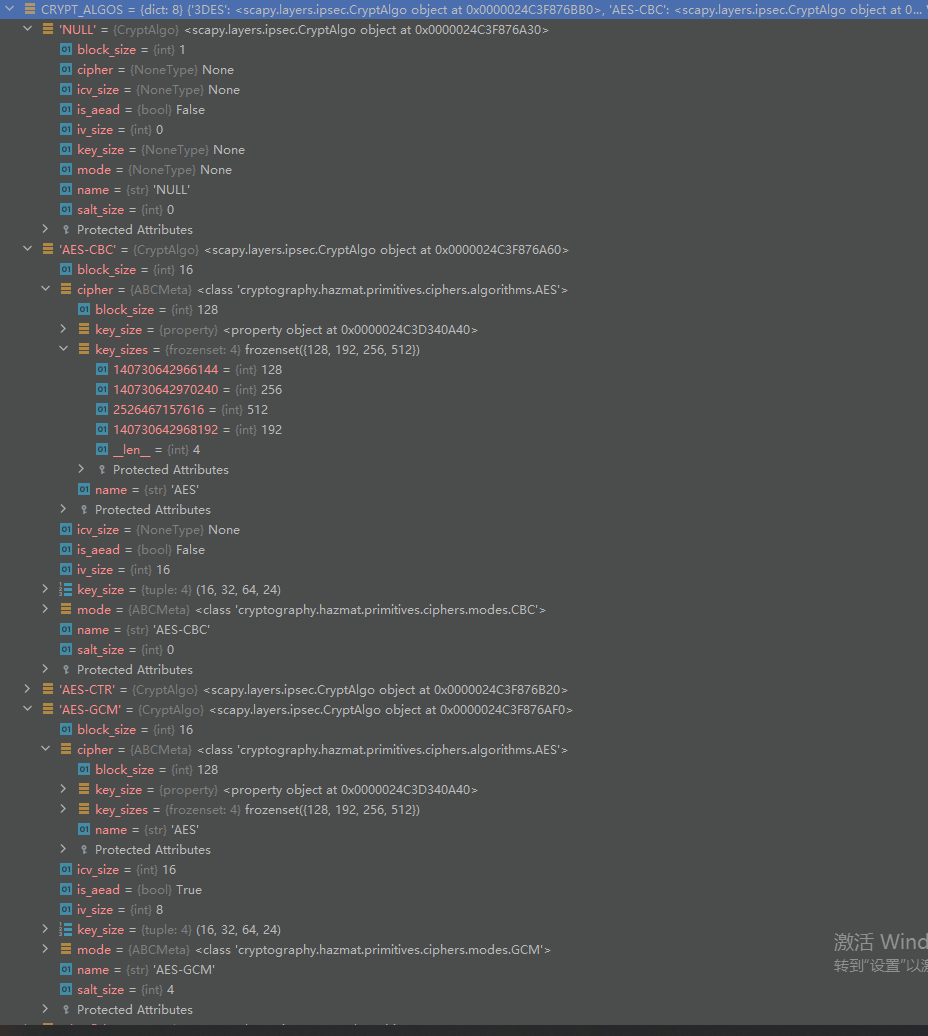
比如这里原始data有
<IP version=4 ihl=5 tos=0x0 len=20 id=1 flags= frag=0 ttl=64 proto=ip chksum=0x2784 src=192.168.105.10 dst=192.168.105.10 |>
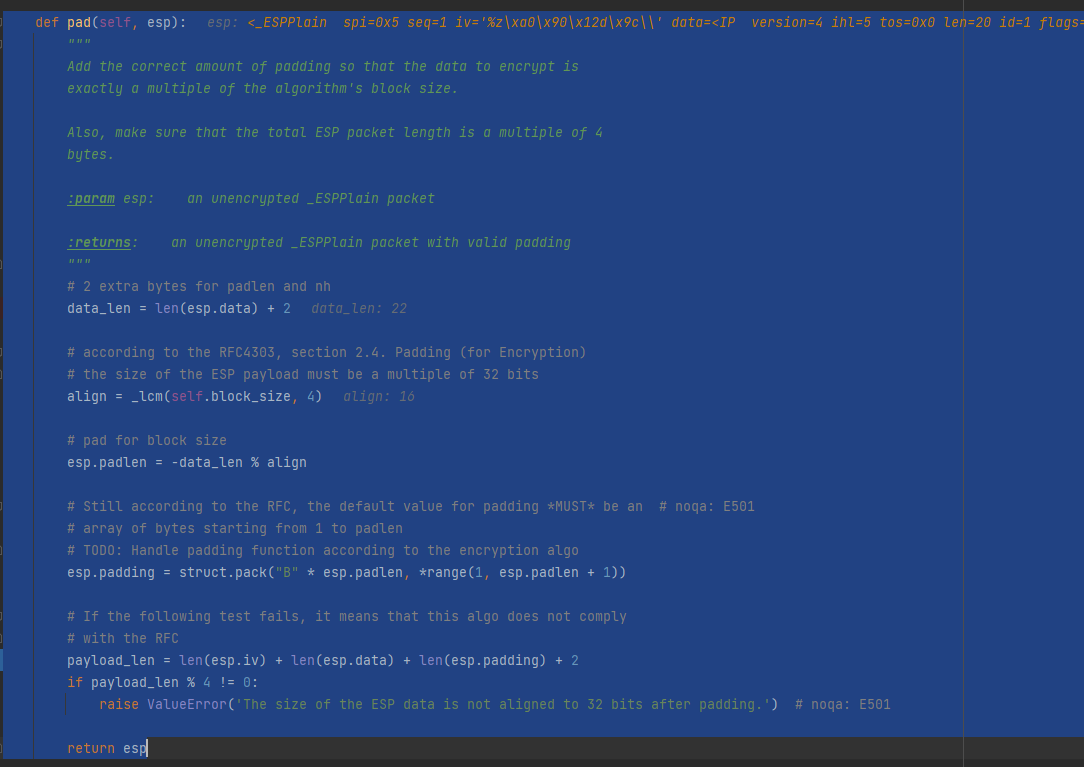
有20个数据 因为payload为空
data_len = len(esp.data) + 2 加两个就是22
# according to the RFC4303, section 2.4. Padding (for Encryption)
# the size of the ESP payload must be a multiple of 32 bits
align = _lcm(self.block_size, 4) 这里求16跟4的最小公倍数 就是16
# pad for block size
esp.padlen = -data_len % align 算出 padlen等于16*2-22=10
# according to the RFC4303, section 2.4. Padding (for Encryption)
# the size of the ESP payload must be a multiple of 32 bits
align = _lcm(self.block_size, 4) 这里求16跟4的最小公倍数 就是16
# pad for block size
esp.padlen = -data_len % align 算出 padlen等于16*2-22=10
那填充就有
b'\x01\x02\x03\x04\x05\x06\x07\x08\t\n'
最后变成
<_ESPPlain spi=0x5 seq=1 iv='%z\xa0\x90\x12d\x9c\\' data=<IP version=4 ihl=5 tos=0x0 len=20 id=1 flags= frag=0 ttl=64 proto=ip chksum=0x2784 src=192.168.105.10 dst=192.168.105.10 |> padding='\x01\x02\x03\x04\x05\x06\x07\x08\t\n' padlen=10 nh=4 |>
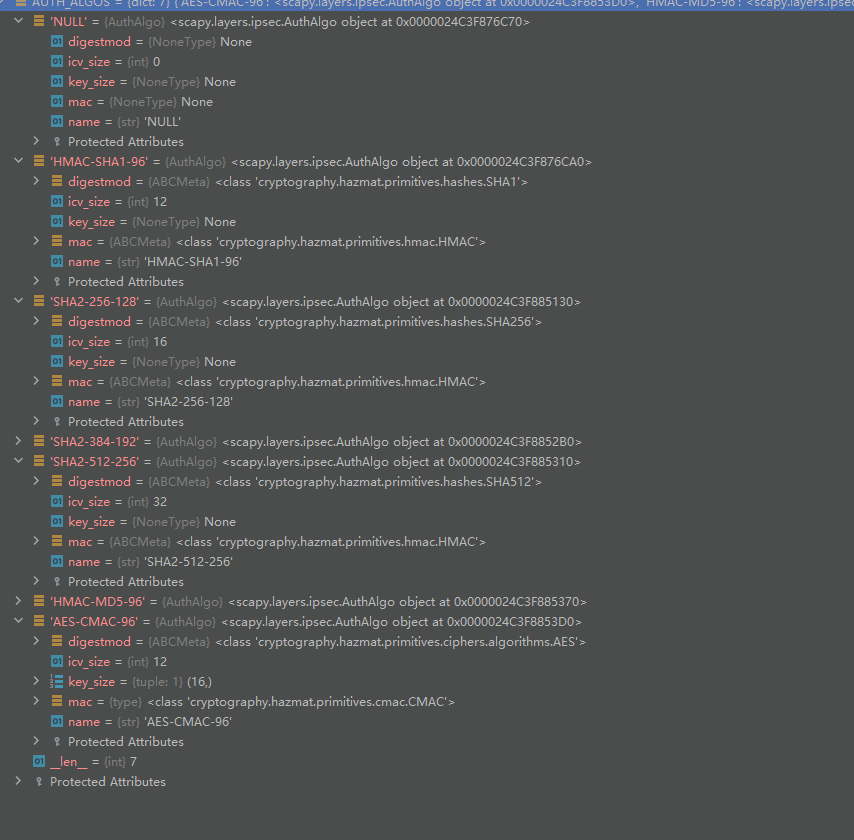
from scapy.all import *
from scapy.layers.ipsec import *
from scapy.layers.l2 import *
def main(argv):
payload = 'test-' * 2000
sa = SecurityAssociation(ESP, spi=5, crypt_algo='AES-GCM',
crypt_key=b'\x49\x2e\x8f\xfe\x71\x8a\x95\xa0\x0c\x18\x93\xea\x61\xaf\xc6\x49\x97\xf4\x73\x28\x48\xcc\xfe\x6e\xa0\x7d\xb4\x83\x17\x5c\xb1\x8d\xe9\xae\x41\x1a',
auth_algo='NULL', auth_key=None,)
sa.crypt_algo.icv_size = 16
p = IP(src='192.168.105.10', dst='192.168.105.10')
e = sa.encrypt(p,iv=b'\xad\xf73g\x80\xea\xbb\xa1')
if __name__ == "__main__":
exit(main(sys.argv[1:]))
from scapy.layers.ipsec import *
from scapy.layers.l2 import *
def main(argv):
payload = 'test-' * 2000
sa = SecurityAssociation(ESP, spi=5, crypt_algo='AES-GCM',
crypt_key=b'\x49\x2e\x8f\xfe\x71\x8a\x95\xa0\x0c\x18\x93\xea\x61\xaf\xc6\x49\x97\xf4\x73\x28\x48\xcc\xfe\x6e\xa0\x7d\xb4\x83\x17\x5c\xb1\x8d\xe9\xae\x41\x1a',
auth_algo='NULL', auth_key=None,)
sa.crypt_algo.icv_size = 16
p = IP(src='192.168.105.10', dst='192.168.105.10')
e = sa.encrypt(p,iv=b'\xad\xf73g\x80\xea\xbb\xa1')
if __name__ == "__main__":
exit(main(sys.argv[1:]))



 浙公网安备 33010602011771号
浙公网安备 33010602011771号